Dynamic IP Blocking settings
Dynamic IP Blocking is a feature that protects your resources by blocking IP addresses from password spraying and other online password attacks. Password spraying is a login attack using a single password against a large number of users. Attackers use common passwords with this method.
SecureAuth blocks the source IP address after failed login attempts using different usernames for a specified amount of time. Instead of locking user accounts, it blocks login attempts coming from that source IP address.
There are two parts to setting up Dynamic IP Blocking:
Use IP Filtering rule to set the length of time to block the source IP address after a set number of failed attempts, and add allowed IP addresses. This setting applies to all policies.
Add the Dynamic IP Blocking rule or condition in each policy in the Authentication Rules tab.
Defining the Dynamic IP Blocking rule
When you define the IP blocking rule here, it applies to all policies.
In the left navigation of the Identity Platform, click IP Filtering.
The settings you define here will be available in all policies. You can add more trusted IP addresses in a specific policy.
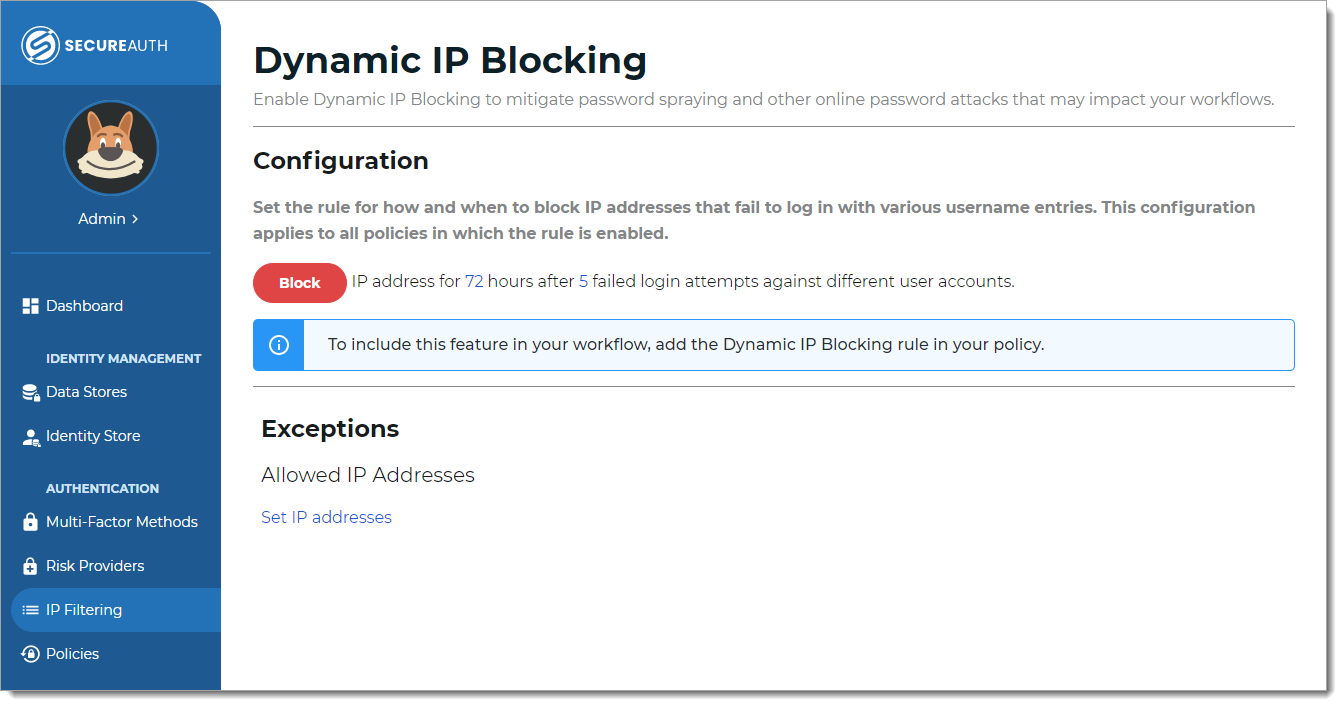
Set the length of time to block the source IP address after a specified number of failed login attempts.
The numbers in the line after the Block button are clickable links. Options are:
Length of time – 12, 24, 36, 48, or 72 hours
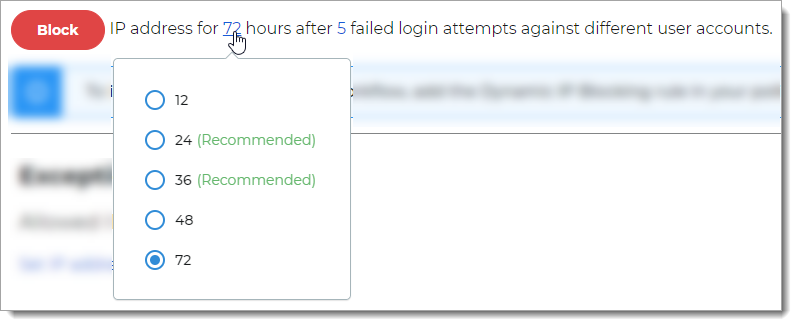
Number of failed login attempts – 5, 10, 15, 20, and 25
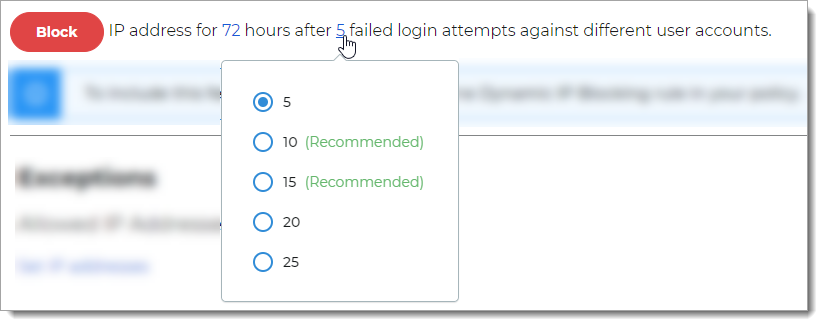
To allow trusted IP addresses, click the Set IP addresses link and enter IP addresses, separated by a comma.
IP addresses can only be in IPv4 format. The Identity Platform applies the trusted IP addresses in all policies that use the Dynamic IP Blocking rule.
Save your changes.
Next steps
Open a policy and go to the Authentication Rules tab and add Dynamic IP Blocking as a new rule or condition.