Multi-screen login workflows
With the multi-screen login workflow, end users authenticate by entering their username on a VPN login screen followed by at least one other code. This can be a password, passcode, symbol, link, PIN, or YubiKey passcode. Once end users have entered their username and code, the login button is enabled on a second VPN login screen or the SecureAuth Authenticate mobile app.
Considerations
If end users will use YubiKey devices to obtain an HMAC-based One-Time Password (HOTP) or Time-Based One-Time Passcode (TOTP), ensure that the YubiKey devices are supported. See the Supported third-party login devices section of the SecureAuth compatibility guide.
If end users will use face or fingerprint recognition, ensure that they set up their mobile device for face or fingerprint recognition before enrollment. Features will then work automatically with the SecureAuth Authenticate mobile app.
End users who already use the Authenticate mobile app and want to add the ability to accept biometric push notifications to use face or fingerprint recognition must first reconnect the account for their mobile device.
If end users want to use face or fingerprint recognition, but did not set up their mobile device to use the features before enrollment, they must turn on face or fingerprint recognition on their mobile device, then set up the SecureAuth mobile app again. To learn more, see the Prerequisites section in the SecureAuth Authenticate App documentation for iOS and Android.
Second-factor authentication methods
The list of available second-factor authentication methods is dynamic and based on the multi-factor authentication options provisioned by the administrator.
See the chart below for the full list of second-factor authentication methods and their workflows.
Second-factor method | Workflow | |
|---|---|---|
SMS / Text Message Phone | If the SMS / Text Message Phone option is selected, the following occurs:
| |
SMS / Text Link (Link-to-Accept) | If the SMS Link-to-Accept option is selected, the following occurs:
| |
If the Email option is selected, the following occurs:
| ||
Email Link (Link-to-Accept) | If the Email Link-to-Accept option is selected, the following occurs:
| |
Send Passcode to Phone (Push Notification) | If the Send Passcode to Phone (Push Notification) option is selected, the following occurs:
| |
Send Login Request to Phone (Push-to-Accept) | If the Push-to-Accept option is selected, the following occurs:
| |
Yubico OTP Token | If the Yubico OTP Token option is selected, the following occurs:
| |
PIN | If the PIN option is selected, the following occurs:
| |
Help Desk OTP | If the Help Desk OTP option is selected, the following occurs:
The following image is an example of the VPN screen end users see with this workflow:
| |
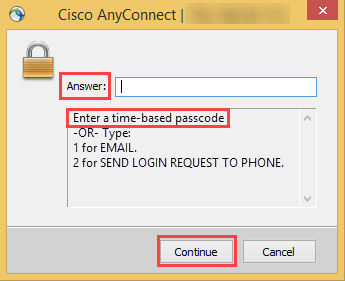
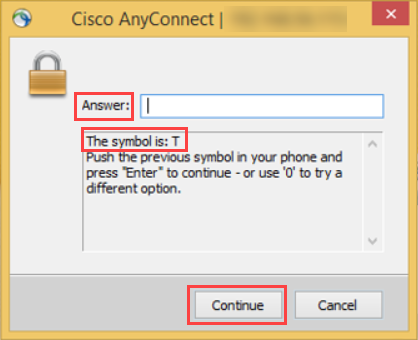
Symbol-to-Accept | If the Symbol-to-Accept option is selected, the following occurs:
The following image is an example of the VPN screen end users see with this workflow:
| |
Fingerprint | If the Fingerprint or Face Recognition options are selected, the following occurs:
| |
Face Recognition |
End user experience
The following sections detail the end user instructions for logging in with the available multi-screen login workflow options.
Note
If the Send Passcode to Phone (Push Notification), PIN, Symbol-to-Accept or Link-to-Accept workflow is initially selected, end users can enter 0 (zero) in the Response field to return to the screen where they can select a different second-factor authentication option.
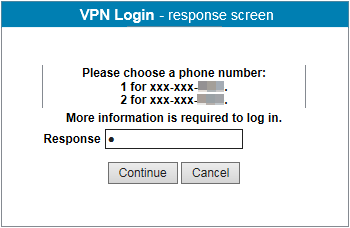
If end users have more than one registered mobile device, each with more than one phone number or email address registered, a prompt appears to select which mobile device, phone number, or email address to use in the second-factor authentication workflow. See sample image below.
End users must first select the phone number to use before seeing the second-factor authentication screen.
Password | One-Time Passcode (TOTP/HOTP)
On the initial VPN login screen, enter your username.
Enter your password.
Get the one-time passcode from the SecureAuth Authenticate App or other SecureAuth TOTP application.
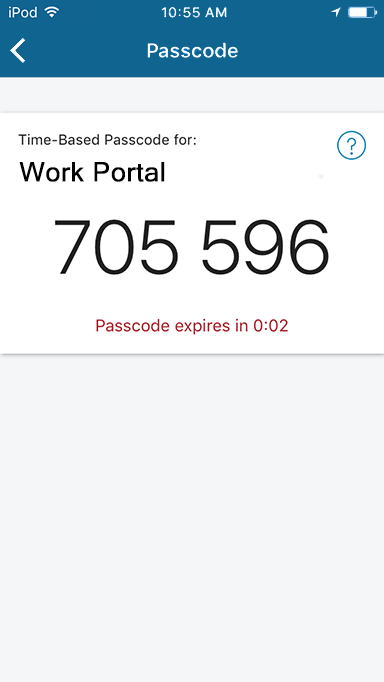
On the second VPN login screen, enter your passcode.
Password & Mobile Login Request (Approve / Deny)
On the initial VPN login screen, enter your username.
Enter your password.
The VPN waits for SecureAuth RADIUS to respond.
On the mobile app Login Request screen, tap Approve or Deny request.
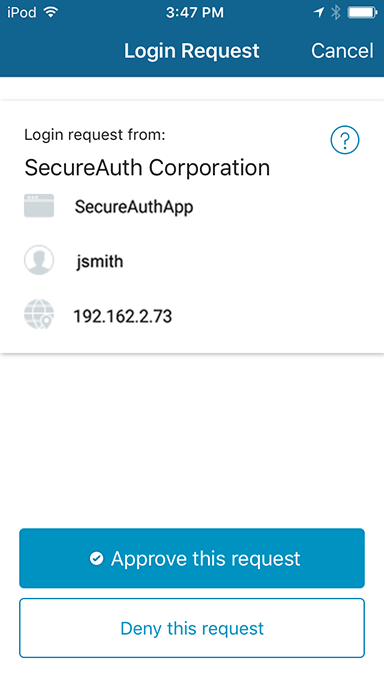
Password | Second Factor
On the initial VPN login screen, enter your username.
Enter your password.
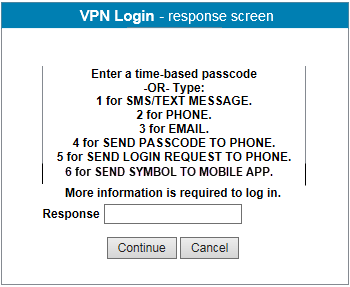
The response screen prompts you for one of two options:
Enter an HOTP one-time passcode (from a YubiKey) or a TOTP one-time passcode (from SecureAuth Authenticate, SecureAuth Passcode, or Yubico Authenticator) to authenticate.
Enter the number corresponding to an available second-factor authentication method and proceed with the workflow. See Second-factor authentication methods.
One-Time Passcode (TOTP/HOTP) | Password
On the initial VPN login screen, enter your username.
Get the one-time passcode from the SecureAuth Authenticate App (or other SecureAuth TOTP application, such as SecureAuth Passcode), HOTP from YubiKey, or TOTP from a Yubico Authenticator app by using a YubiKey.
Enter your password on the second VPN login screen.
Username | Second Factor
On the initial VPN login screen, enter your username.
A password entry is not required.
On the response screen, enter the number corresponding to an available second-factor authentication method and proceed with the workflow. See Second-factor authentication methods.
Username | Second Factor | Password
On the VPN login screen, enter your username.
A password entry is not required at this step.
On the response screen, enter the number corresponding to an available second-factor authentication method and proceed with the workflow. See Second-factor authentication methods.
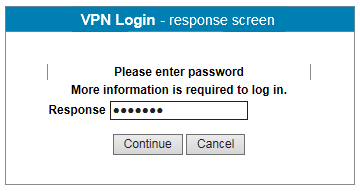
On the response screen, enter your password.
Username | Fingerprint
On the initial VPN login screen, enter your username.
A password entry is not required.
If more than one mobile phone is registered, select the phone to use.
You need to do this once only as the selection is persistent.
Enter the number that corresponds with Fingerprint to send a request to the SecureAuth mobile app.
Provide a fingerprint on the SecureAuth mobile app to approve the request.
The VPN receives the fingerprint information and you are authenticated.
Username | Face Recognition
On the initial VPN login screen, enter your username.
A password entry is not required.
If more than one mobile phone is registered, select the phone to use.
You need to do this once only as the selection is persistent.
Enter the number that corresponds with Face Recognition to send a request to the SecureAuth mobile app.
Show your face on the SecureAuth mobile app to approve the request.
The VPN receives the face information and you are authenticated.
Password & One-Time Passcode (TOTP/HOTP)
On the initial VPN login screen, enter your username.
Enter your password.
Get the one-time passcode from the SecureAuth mobile app (or other SecureAuth TOTP application, such as SecureAuth Passcode), HOTP from YubiKey, or TOTP from a Yubico Authenticator app by using a YubiKey.
Enter your passcode.
Password & Yubico One-Time Passcode (OTP)
On the initial VPN login screen, enter your username.
Enter your password.
Get the Yubico one-time passcode by pressing your YubiKey.
The Yubico OTP is automatically sent to the login app, the login app receives the OTP, and you are connected to your network.