Support biometric options in login workflow with Authenticate app
SecureAuth® Identity Platform supports end user login workflow options using biometric-to-accept (B2A) with the SecureAuth Authenticate app. End users can log in using biometric options if their iOS or Android phone supports biometrics.
It requires the Identity Platform appsettings value: tryBiometric=true.
This setting enforces biometric options by default, in the Authenticate app on mobile devices that support biometric.Otherwise, end users get the standard push-to-accept (P2A) on mobile devices that do not support biometric.
Push-to-accept delivery options on the Authenticate app display as login request, fingerprint recognition, or facial recognition like the following image:
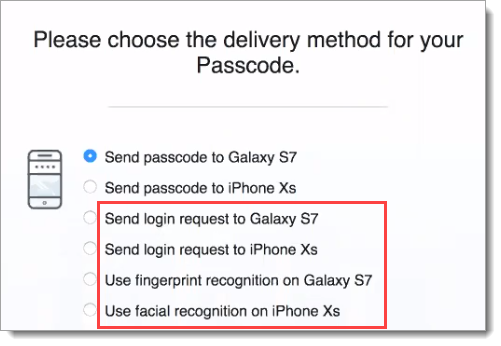 |
Requirements
Applicable on the following product versions:
Identity Platform version 20.06-5 or later
Identity Platform version 19.07.01-25 or later
Identity Platform must have the appsettings value set to:
tryBiometric=trueRequires the use of SecureAuth Authenticate app version 20.03.01 or later
End users must have at least one biometric option enabled on their mobile phone (fingerprint or facial recognition)
Supported devices
Android and iOS devices that support biometrics (Android supports fingerprint recognition; iOS supports fingerprint recognition and facial recognition)
Authenticate app on Android and iOS watches redirect end users to their phone for each biometric request
Tablets are included in this feature
Identity Platform configuration
Contact Support to ensure the Identity Platform appsettings value is set to: tryBiometric=true.
End user process
Direct end users to download or update to the latest SecureAuth Authenticate app version 20.03.01 from the Google Play or Apple App Store:
End users can choose their preferred login method like any of the following:
Login using passcode option, like "Send passcode to <phone name>".
Login using push-to-accept option, like "Send login request to <phone name> option.
Login using biometric option, like "Use fingerprint recognition on <phone name>" or "Use facial recognition on <phone name>".

Result
For iOS phones, end users receive a biometric prompt from the Authenticate app like the following, to use facial recognition:
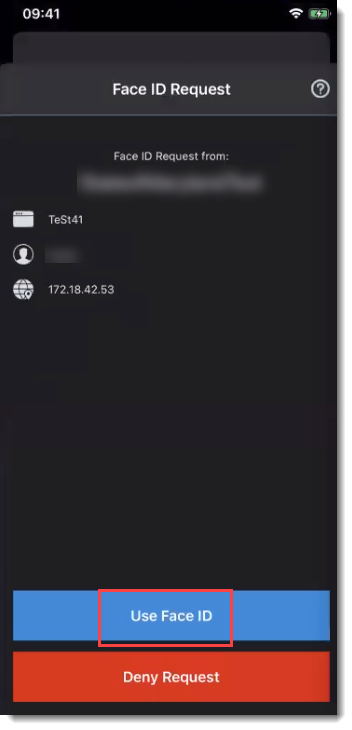 |
The tryBiometric=true causes biometrics-to-accept (B2A) to be the default action. So, this requires end users to unlock their phone to use fingerprint or facial recognition.
In this case, when the lock screen is on, iPhone users cannot use a long press action to accept push-to-accept notifications.
When biometrics is not available on a mobile phone, the fallback method for end users is push-to-accept; even if they select a biometric option. They get a prompt to use push-to-accept like the following:
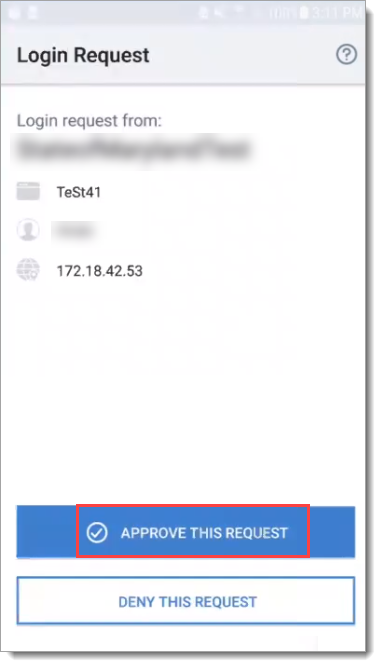 |
For Android phones, end users receive a prompt from the Authenticate app like the following, to use fingerprint recognition (it reads as "Use Biometric"):
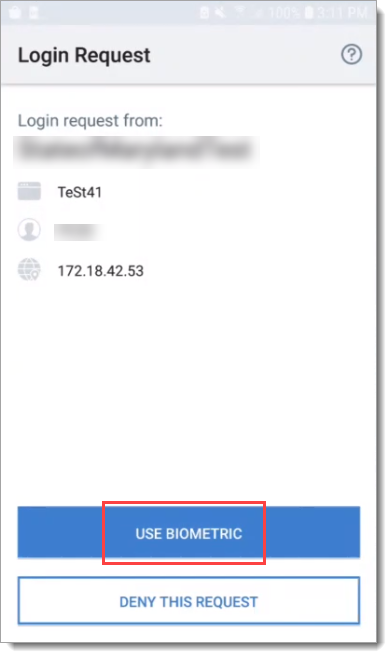 |