Multi-factor app enrollment URL configuration
Use this guide to create an app enrollment page with a URL workflow for end users to connect to their profile in the following ways to enroll and provision any of the following:
SecureAuth Passcode app to receive one-time passcodes (OTPs) on their desktop
SecureAuth Authenticate app to receive time-based one-time passcodes (TOTPs), push notification one-time passcodes (OTPs), Push-to-Accept, and Symbol-to-Accept login requests on their mobile device
Once provisioned to use SecureAuth Passcode and SecureAuth Authenticate, the passcode and login requests from the app is used to validate the end user attempting to log in to a protected resource.
For supported versions of mobile apps, OTP clients, desktop browsers, and paired smartwatches, see the SecureAuth compatibility guide.
Prerequisites
SecureAuth® Identity Platform release 22.02 or later
Data store added to the Identity Platform
Configured user authentication policy
Identity Platform configuration
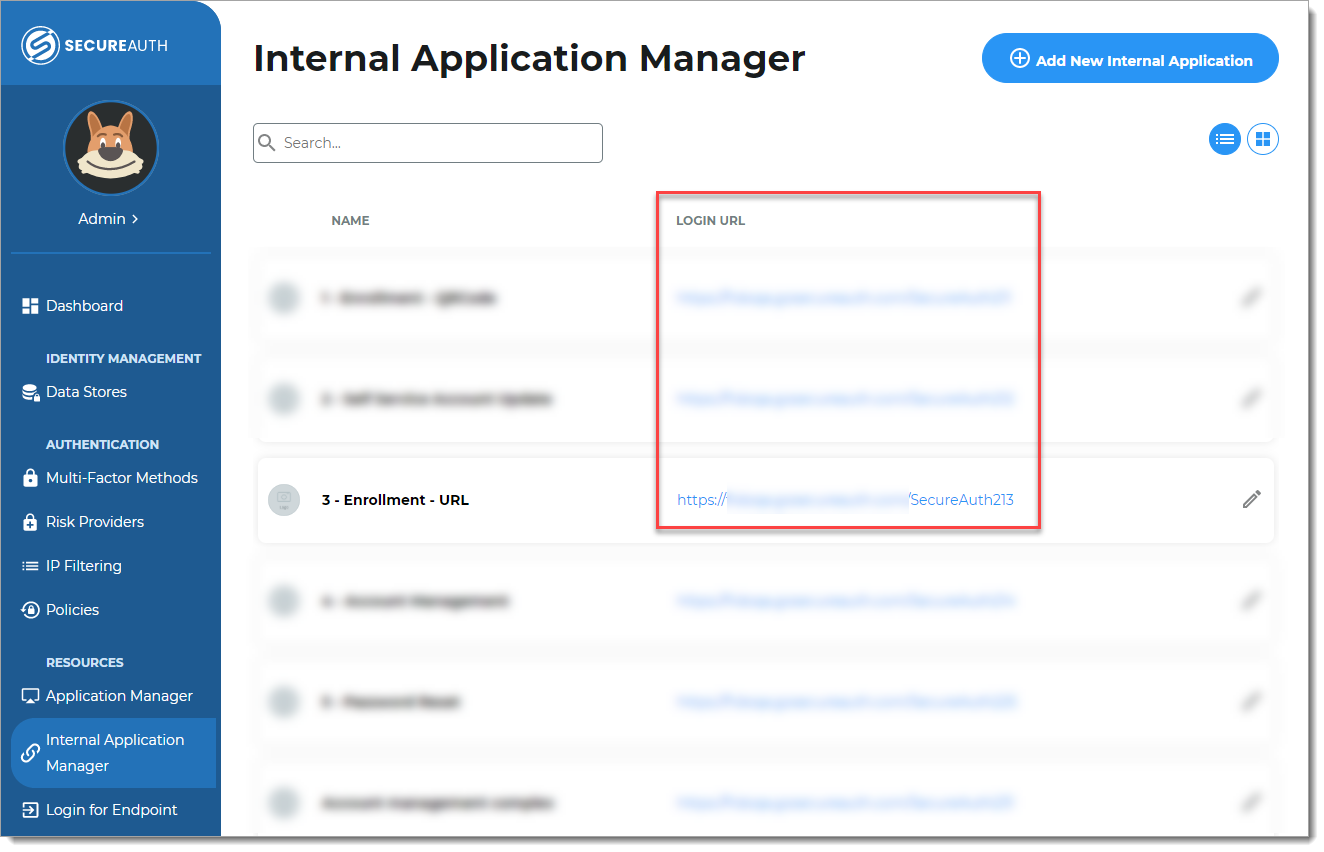
On the left side of the Identity Platform, click Internal Application Manager.
Click Add New Internal Application.
The New Internal Application page displays.
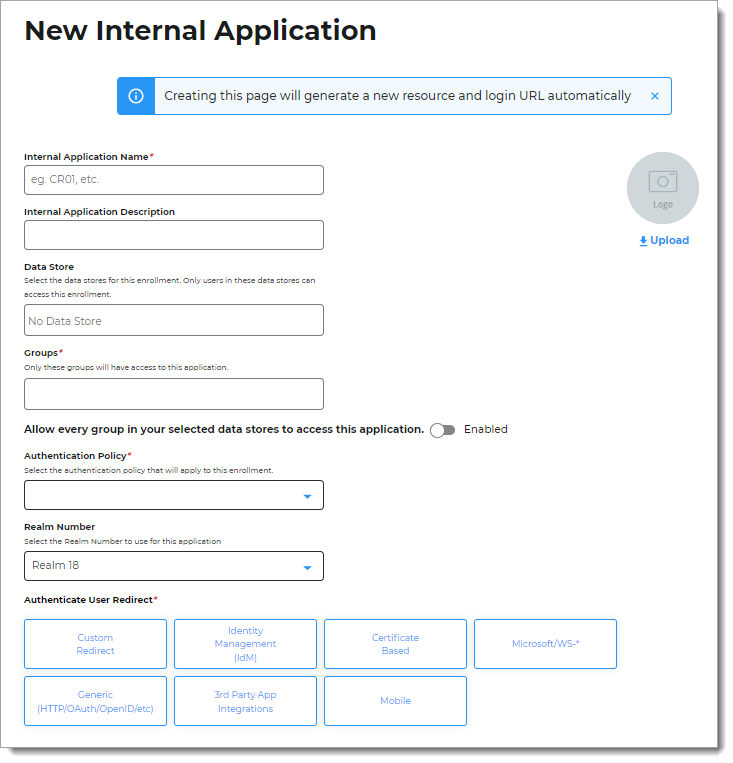
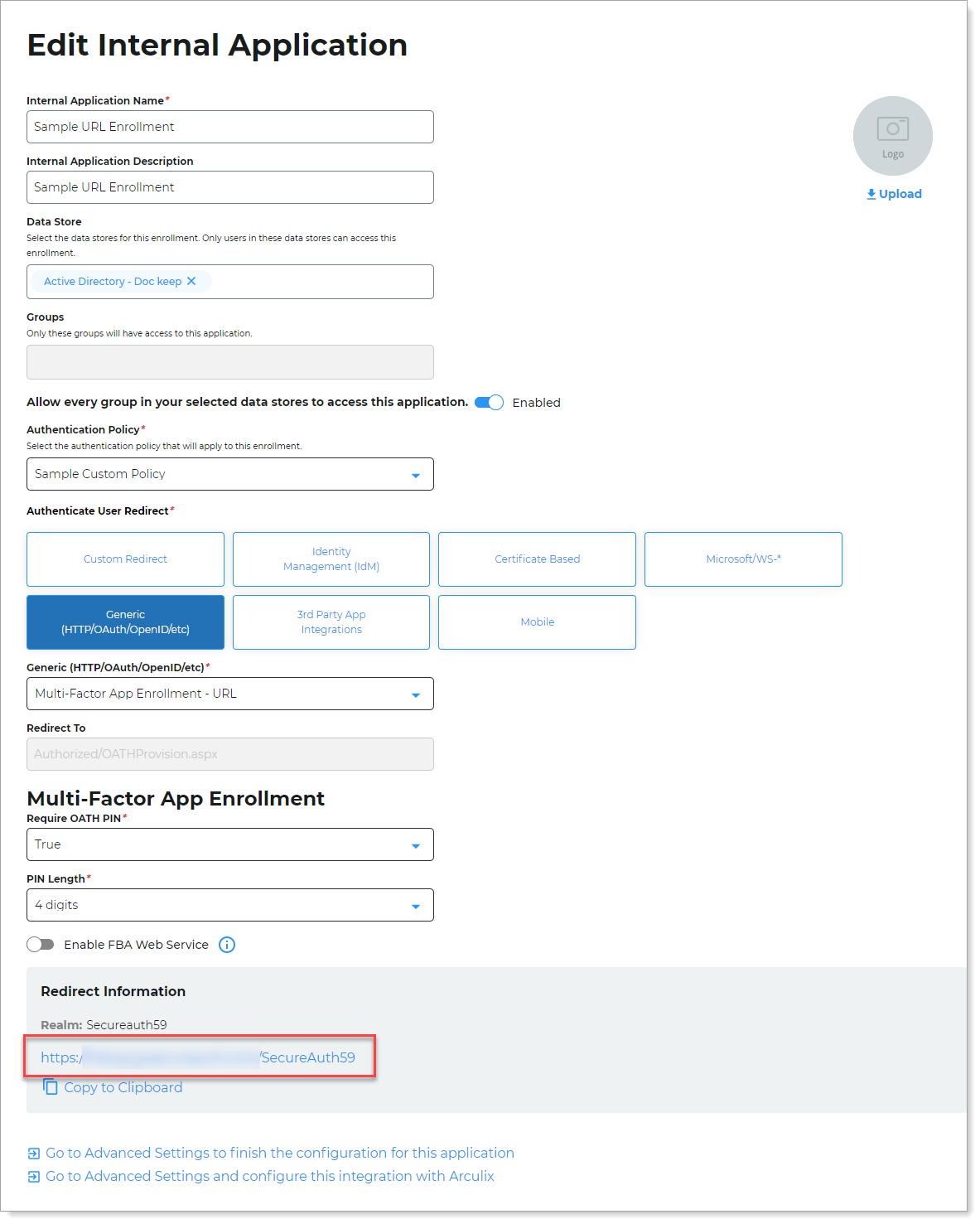
Set the following configurations:
Internal Application Name
Set the name of the URL enrollment application.
This name is shown on the page header and document title of the end user login pages.
Note
If you change this name, it will overwrite any value that is set on the Overview tab in the Advanced Settings.
Internal Application Description
Enter an internal description. Not visible to end users.
Data Store
Enter the data store to authenticate and allow user access to the URL enrollment application.
Groups
Use one of the following options:
Slider in the On position (enabled): Allow users from every group in your selected data stores access to the URL enrollment application.
Slider in the Off position (disabled): Enter the specific groups who are allowed access to the URL enrollment application.
Authentication Policy
Select the user authentication policy for the QR enrollment application.
Realm Number
Select the Realm Number to use for this application.
Authenticate User Redirect
Select the Generic (HTTP/OAuth/OpenID/etc) category.
Generic (HTTP/OAuth/OpenID/etc)
Select Multi-Factor App Enrollment - URL.
Redirect To
This field is automatically populated by the selection of the Multi-Factor App Enrollment - URL as an internal application.
This is the URL enrollment page the end user lands on after login.
Multi-Factor App Enrollment section
Require OATH PIN
Set to one of the following options:
True – To view the time-based one-time passcode (TOTP) on the Authenticate app, require users to provide a PIN or biometric ID (fingerpint)
False – PIN is not required to view the TOTP on the Authenticate app
PIN Length
Set the number of digits in the PIN (4, 6, 8, or 10 digits).
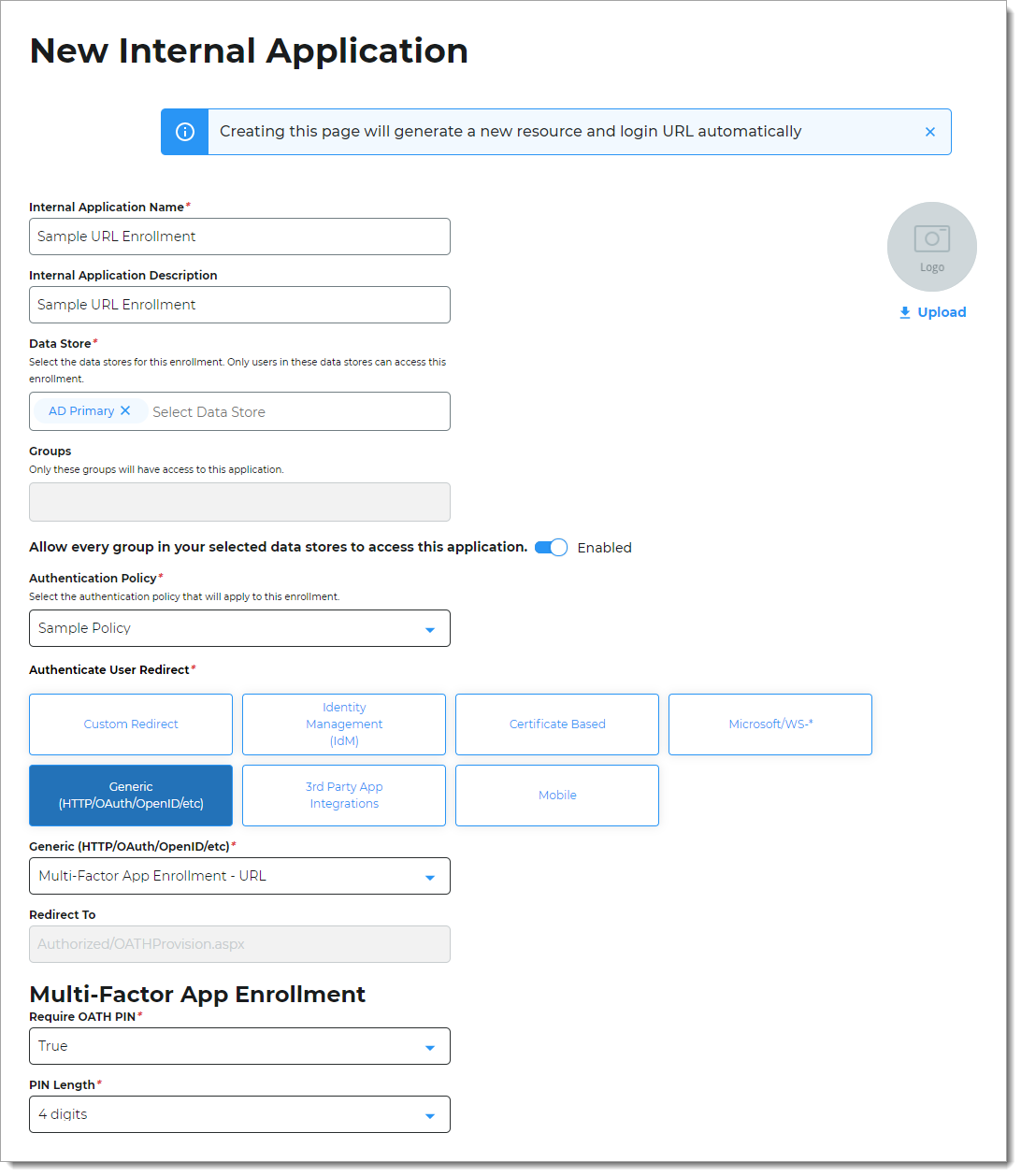
Click Create Connection.
This creates a new URL enrollment application with an attached user authentication policy.
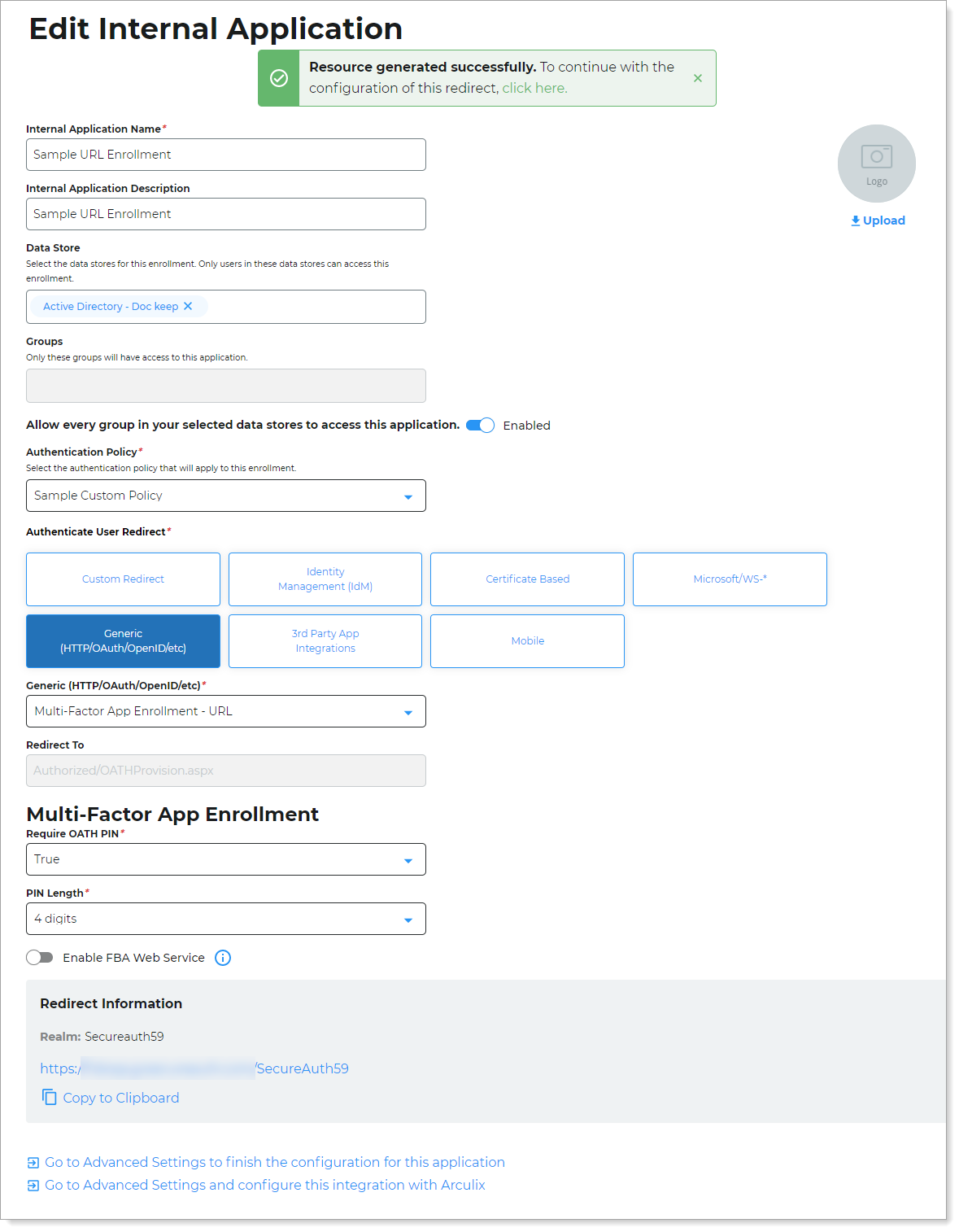
Optional: You only need to complete the configuration in Advanced Settings if you want to do any of the following:
Change User ID Mapping to something else other than Authenticated User ID.
Configure token or cookie settings for the URL enrollment application.
To go to Advanced Settings, click either link at the top or bottom of the Edit Internal Application page.
Use the login URL for your end users to access the URL enrollment page.
You can find this on the main Internal Application Manager page or when you edit the URL enrollment application in the Redirect Information section.