Troubleshooting Login for Mac
This topic contains information about logs and troubleshooting Login for Mac.
Error logs
You can find Login for Mac error logs in the following locations.
Installation logs
Information related to installation is written in the install.log file:
/var/tmp
Login logs
Login information writes to the login.log file:
/Library/Application Support/com.secureauth.saap
The login.log file displays system information, such as the type and version of the operating system, the version of Login for Mac your organization is running, and more as shown in the following image:
 |
After you view the login.log file, then connect later through RDP, you might notice what look like inconsistencies because the log file will have new start lines and threads. This is expected behavior because connecting through RDP causes new instances of the credential provider to be created, which causes the new start lines and threads.
Installer issue
Login for Mac installer requires Python 3 on macOS version 12.3 (Monterey) or later.
If Python 3 does not exist on the Mac, the Login for Mac installer will launch the Python 3 installer.
Prevent and troubleshoot end user lockouts
End users can be locked out of their Mac workstations because of network setup issues, misconfigured Login for Mac install, or end user Mac configuration issues.
Network setup issues
"Matching Active Directory profiles required". Active Directory must include an account profile for each end user, and that profile must match the AD profile set up on the Mac in order for the Mac endpoint to retrieve the AD profile.
Login for Endpoints installer misconfigured
"Edits made in config.json file". If the configured config.json file is edited, ensure that Unicode characters, instead of UTF-8 characters, are not entered and saved in the file. This scenario might occur if text is copied from another source and pasted into the file, and could result in an end user being locked out of the Mac due to a misconfigured endpoint.
End user Mac configuration issues
"Misconfigured Active Directory profile on Mac". If the end user's new Mac has a misconfigured Active Directory account profile, the endpoint will not be able to retrieve the end user's AD profile to complete the login process.
"Lockout with secure, automatic enterprise WiFi endpoint connection". If the endpoint is set to automatically connect to a secure, enterprise WiFi, and has not yet been configured to connect to the SecureAuth Identity Platform, then the end user will be locked out of logging on the Mac. In this scenario, the Mac may need to be reset by the administrative user who can bypass the login endpoint to reset the machine.
"Lockout without OATH seed for YubiKey HOTP device or network connectivity". If a YubiKey HOTP device is used for logging on the Mac, but the machine does not have an OATH seed stored on it or network connectivity, then the endpoint must wait for an available network connection
No WiFi or wired connection. If the end user is attempting to log on for the first time, and the Mac does not have WiFi configured or is not using a wired connection, then the end user will be locked out of logging on the Mac.
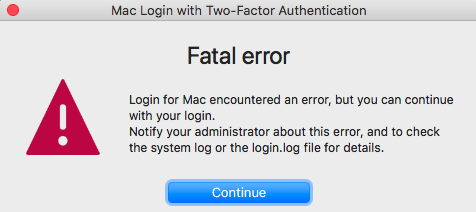
Admin needs to view log information
End users receive the following message that Login for Mac encountered an error and are guided to continue with their login. Admins are guided to check the system log or the login.log file for details.
 |
To find more information about the error, you can do the following -- in Login for Mac, open the login.log file, located in /Library/Application Support/com.secureauth.saap.
Enter the following command:
log show --last [number] --predicate 'subsystem = "com.secureauth.saap"'
If running a PAM product, enter the following command:
log show --last [number] --predicate 'subsystem = "com.secureauth.pam"'
where
--last [number][m|h|d]enables you to set a time period to limit the captured events from the present to the previous minutes, hours, or days. If [m|h|d] is not specified, the specified time is rendered in seconds.
Example 1: To limit the output in the log file to the last 5 minutes, use the following value: --last 5m
Example 2: To limit the output in the log file to the last 45 seconds, use the following value: --last 45