Network communication requirements for Identity Platform
This document lists the firewall ports that must be opened to ensure network connectivity of the SecureAuth® Identity Platform appliance, release 19.07 or later.
Refer to How to configure the Windows Server 2019 Firewall for instructions on how to open firewall ports on the appliance's firewall.
Required Connectivity
Note
The following ports are required to be open for SecureAuth Identity Platform to function
Direction | Port | Protocol | Destination | Status | Description | Host-Based FW Rules |
|---|---|---|---|---|---|---|
Inbound | 443 | TCP | All SecureAuth Identity Platform appliances | Required | Provides access to the SecureAuth web interface | World Wide Web Services (HTTPS Traffic-In) |
Outbound | 80 & 443 | TCP | Refer to SecureAuth cloud services for the latest URLs and requirements | Required | Needed for access to SecureAuth cloud infrastructure | SecureAuth - Allow Cloud Services SecureAuth - Allow SecureAuth Activation |
Outbound | 53 | TCP, UDP | To the preferred IPs of your internal Domain Name System servers | Required | DNS | Core Networking - DNS (UDP-Out) SecureAuth - Allow DNS (TCP-Out) |
Outbound | 123 | UDP | The preferred Network Time Provider service | Required | (S)NTP / Windows Time | SecureAuth - Allow NTP |
Outbound | 80 | TCP | www.microsoft.com | Required | For Windows Operation System Activation | SecureAuth - Allow Windows Activation (1) SecureAuth - Allow Windows Activation (2) |
Outbound | 443 | TCP | www.microsoft.com | Required | For Windows Operation System Activation | SecureAuth - Allow Windows Activation (1) SecureAuth - Allow Windows Activation (2) |
Further Connectivity
The following groups of ports are necessary if your deployment uses the services indicated. If your implementation does not use a service, then you are not required to open the corresponding ports.
Notice
Windows Server 2008 R2 and Windows Server 2008, in compliance with Internet Assigned Numbers Authority (IANA) recommendations, increased the dynamic port range for connections. The new default start port is 49152, and the new default end port is 65535. Therefore, you must increase the remote procedure call (RPC) port range in your firewalls.
When you see TCP Dynamic in the Port column, it refers to ports 1025 through 5000, the default port range for Windows Server 2003, and ports 49152 through 65535, the default port range beginning with Windows Server 2008.
For more information, see the Microsoft support document, Active Directory and Active Directory Domain Services Port Requirements.
Direction | Port | Protocol | Destination | Status | Description | Host-Based FW Rules |
|---|---|---|---|---|---|---|
Inbound / Outbound | 445 | TCP | The participating SecureAuth appliances | Required | SMB/CIFS | SecureAuth - Allow SecureAuth Filesync Service (TCP-In) SecureAuth - Allow SecureAuth Filesync Service (UDP-In) SecureAuth - Allow SecureAuth Filesync Service (TCP-Out) SecureAuth - Allow SecureAuth Filesync Service (UDP-Out) |
Inbound / Outbound | 139 | TCP | The participating SecureAuth appliances | Required | NetBIOS-Session | |
Inbound / Outbound | 138 | UDP | The participating SecureAuth appliances | Required | NetBIOS-Datagram | |
Inbound / Outbound | 137 | UDP | The participating SecureAuth appliances | Required | NetBIOS-Name |
Direction | Port | Protocol | Destination | Status | Description | Host-Based FW Rules |
|---|---|---|---|---|---|---|
Outbound | 389 | TCP, UDP | The appropriate Active Directory Domain Controller(s) or LDAP server(s) | Required | LDAP | SecureAuth - Allow Directory-LDAP (TCP-Out) SecureAuth - Allow Directory-LDAP (UDP-Out) |
Outbound | 636 | TCP | The appropriate Active Directory Domain Controller(s) or LDAP server(s) | Optional | LDAP - SSL/TLS | SecureAuth - Allow Directory-LDAP (TCP-Out) SecureAuth - Allow Directory-LDAP (UDP-Out) |
Outbound | 3268 | TCP | The appropriate Active Directory Global Catalog server(s) | Required* | LDAP Global Catalog (*Required if connecting to AD DC) | SecureAuth - Allow Directory-LDAP (TCP-Out) SecureAuth - Allow Directory-LDAP (UDP-Out) |
Outbound | 3269 | TCP | The appropriate Active Directory Global Catalog server(s) | Optional* | LDAP Global Catalog - SSL/TLS (*Required if connecting to AD DC over SSL/TLS) | SecureAuth - Allow Directory-LDAP (TCP-Out) SecureAuth - Allow Directory-LDAP (UDP-Out) |
Outbound | 88 | TCP, UDP | The appropriate Active Directory Domain Controller(s) | Required | Kerberos | SecureAuth - Allow Directory-LDAP (TCP-Out) SecureAuth - Allow Directory-LDAP (UDP-Out) |
Outbound | 389 | TCP, UDP | The appropriate Active Directory Domain Controller(s) | Required | LDAP | SecureAuth - Allow Domain Membership (TCP-Out) SecureAuth - Allow Domain Membership (UDP-Out) |
Outbound | 636 | TCP | The appropriate Active Directory Domain Controller(s) | Optional | LDAP - SSL/TLS | SecureAuth - Allow Domain Membership (TCP-Out) SecureAuth - Allow Domain Membership (UDP-Out) |
Outbound | 3268 | TCP | The appropriate Active Directory Domain Controller(s) | Required | LDAP Global Catalog | SecureAuth - Allow Domain Membership (TCP-Out) SecureAuth - Allow Domain Membership (UDP-Out) |
Outbound | 3269 | TCP | The appropriate Active Directory Domain Controller(s) | Optional | LDAP Global Catalog - SSL/TLS | SecureAuth - Allow Domain Membership (TCP-Out) SecureAuth - Allow Domain Membership (UDP-Out) |
Outbound | 88 | TCP, UDP | The appropriate Active Directory Domain Controller(s) | Required | Kerberos | SecureAuth - Allow Domain Membership (TCP-Out) SecureAuth - Allow Domain Membership (UDP-Out) |
Outbound | 445 | TCP, UDP | The appropriate Active Directory Domain Controller(s) | Required | SMB/CIFS, DFSN, LSARPC, NbtSS, NetLogonR, SamR, SrvSvc | SecureAuth - Allow Domain Membership (TCP-Out) SecureAuth - Allow Domain Membership (UDP-Out) |
Outbound | 135 | TCP | The appropriate Active Directory Domain Controller(s) | Required | RPC, EPM | SecureAuth - Allow Domain Membership (TCP-Out) SecureAuth - Allow Domain Membership (UDP-Out) |
Outbound | 137 | UDP | The appropriate Active Directory Domain Controller(s) | Required | NetLogon, NetBIOS Name Resolution | SecureAuth - Allow Domain Membership (TCP-Out) SecureAuth - Allow Domain Membership (UDP-Out) |
Outbound | 138 | UDP | The appropriate Active Directory Domain Controller(s) | Required | DFSN, NetLogon, NetBIOS Datagram Service | SecureAuth - Allow Domain Membership (TCP-Out) SecureAuth - Allow Domain Membership (UDP-Out) |
Outbound | 139 | TCP | The appropriate Active Directory Domain Controller(s) | Required | DFSN, NetBIOS Session Service, NetLogon | SecureAuth - Allow Domain Membership (TCP-Out) SecureAuth - Allow Domain Membership (UDP-Out) |
Outbound | TCP Dynamic | TCP | The appropriate Active Directory Domain Controller(s) | Optional | Default Dynamic Port Range (see note below) | SecureAuth - Allow Domain Membership (TCP-Out) SecureAuth - Allow Domain Membership (UDP-Out) |
Direction | Port | Protocol | Destination | Status | Description | Host-Based FW Rules |
|---|---|---|---|---|---|---|
Outbound | 389 | TCP, UDP | The appropriate Active Directory Domain Controller(s) | Required | LDAP | SecureAuth - Allow Domain Membership (TCP-Out) SecureAuth - Allow Domain Membership (UDP-Out) |
Outbound | 636 | TCP | The appropriate Active Directory Domain Controller(s) | Optional | LDAP - SSL/TLS | SecureAuth - Allow Domain Membership (TCP-Out) SecureAuth - Allow Domain Membership (UDP-Out) |
Outbound | 3268 | TCP | The appropriate Active Directory Domain Controller(s) | Required | LDAP Global Catalog | SecureAuth - Allow Domain Membership (TCP-Out) SecureAuth - Allow Domain Membership (UDP-Out) |
Outbound | 3269 | TCP | The appropriate Active Directory Domain Controller(s) | Optional | LDAP Global Catalog - SSL/TLS | SecureAuth - Allow Domain Membership (TCP-Out) SecureAuth - Allow Domain Membership (UDP-Out) |
Outbound | 88 | TCP, UDP | The appropriate Active Directory Domain Controller(s) | Required | Kerberos | SecureAuth - Allow Domain Membership (TCP-Out) SecureAuth - Allow Domain Membership (UDP-Out) |
Outbound | 445 | TCP, UDP | The appropriate Active Directory Domain Controller(s) | Required | SMB/CIFS, DFSN, LSARPC, NbtSS, NetLogonR, SamR, SrvSvc | SecureAuth - Allow Domain Membership (TCP-Out) SecureAuth - Allow Domain Membership (UDP-Out) |
Outbound | 135 | TCP | The appropriate Active Directory Domain Controller(s) | Required | RPC, EPM | SecureAuth - Allow Domain Membership (TCP-Out) SecureAuth - Allow Domain Membership (UDP-Out) |
Outbound | 137 | UDP | The appropriate Active Directory Domain Controller(s) | Required | NetLogon, NetBIOS Name Resolution | SecureAuth - Allow Domain Membership (TCP-Out) SecureAuth - Allow Domain Membership (UDP-Out) |
Outbound | 138 | UDP | The appropriate Active Directory Domain Controller(s) | Required | DFSN, NetLogon, NetBIOS Datagram Service | SecureAuth - Allow Domain Membership (TCP-Out) SecureAuth - Allow Domain Membership (UDP-Out) |
Outbound | 139 | TCP | The appropriate Active Directory Domain Controller(s) | Required | DFSN, NetBIOS Session Service, NetLogon | SecureAuth - Allow Domain Membership (TCP-Out) SecureAuth - Allow Domain Membership (UDP-Out) |
Outbound | TCP Dynamic | TCP | The appropriate Active Directory Domain Controller(s) | Optional | Default Dynamic Port Range (see note below) | SecureAuth - Allow Domain Membership (TCP-Out) SecureAuth - Allow Domain Membership (UDP-Out) |
Direction | Port | Protocol | Destination | Status | Description | Host-Based FW Rules |
|---|---|---|---|---|---|---|
Outbound | 139 | TCP | The appropriate Active Directory Domain Controller(s) | Required | DFSN, NetBIOS Session Service, NetLogon | SecureAuth - Allow Active Directory Password Reset (TCP-Out) SecureAuth - Allow Active Directory Password Reset (UDP-Out) |
Outbound | 445 | TCP, UDP | The appropriate Active Directory Domain Controller(s) | Required | SMB/CIFS, DFSN, LSARPC, NbtSS, NetLogonR, SamR, SrvSvc | |
Outbound | 464 | TCP, UDP | The appropriate Active Directory Domain Controller(s) | Required | Kerberos Change\Set Password |
Direction | Port | Protocol | Destination | Status | Description | Host-Based FW Rules |
|---|---|---|---|---|---|---|
Outbound | 1433 | TCP | The appropriate Database Servers | Optional | Required if using ODBC\MSSQL as a Data Store and\or reporting server | SecureAuth - Allow SQL |
Outbound | 514 | UDP | The appropriate Database Servers | Optional | Required if Syslog logging will be used | SecureAuth - Allow Syslog |
RADIUS
Direction | Port | Protocol | Destination | Status | Description | Host-Based FW Rules |
|---|---|---|---|---|---|---|
Inbound | 1812 | UDP | The appropriate Radius Servers | Required | RADIUS Authentication | SecureAuth - Allow RADIUS |
Inbound | 1813 | UDP | The appropriate Radius Servers | Required | RADIUS Accounting | SecureAuth - Allow RADIUS |
Direction | Port | Protocol | Destination | Status | Description | Host-Based FW Rules |
|---|---|---|---|---|---|---|
Outbound | 25 | TCP | The preferred SMTP server | Required | SMTP for One Time Password notification | SecureAuth - Allow SMTP |
Basic Required Service
The SecureAuth Identity Platform appliance will need to resolve DNS addresses. Ensure the appliance is configured with usable DNS IP resolvers and all firewalls are configured to allow the traffic (TCP-UDP/53).
 |
If you intend for users to receive their One Time Password (OTP) code via email, then you will have to allow SMTP (TCP/25) connectivity. If your internal SMTP server requires encryption, see the SecureAuth document Enabling SSL/TLS Support for SMTP.
Warning
SecureAuth Identity Platform appliances come pre-configured to use the mail relay, smtp.merchantsecure.com (64.34.120.34). This relay is intended for testing purposes only and should not be used in your production environment. SecureAuth Corporation offers no SLA for the uptime of the mail relay. We strongly recommended that customers configure the appliance to use their internal mail relay at the earliest possible opportunity.
 |
SecureAuth uses the Kerberos protocol to facilitate secure communications for many of its functions. The Kerberos protocol is sensitive to time drifts and, as such, keeping the clock disciplined on the appliance is important. The SecureAuth appliance should be within a few minutes of the LDAP/Active Directory Server. If the SecureAuth appliance is not joined to a domain and receiving accurate timing from a Domain Controller, we recommend enabling NTP to keep the time accurate.
 |
If your environment uses Microsoft Active Directory or an LDAP based solution, such as OpenLDAP, then you will need to open the applicable ports below:
Active Directory / LDAP | ||
Direction | Port | Protocol |
Outbound | 389 | TCP, UDP |
Outbound | 636 | TCP |
Outbound | 3268 | TCP |
Outbound | 3269 | TCP |
Outbound | 88 | TCP, UDP |
Notice
SSL Certificates are required for Secure LDAP (LDAPS) functionality. Review the following documents for specific information.
See How to enable LDAP over SSL with a third-party certification authority for information regarding the SSL certificates needed for LDAPS.
See How to add a Subject Alternative Name to a secure LDAP certificate for information on using a domain alias with LDAPS.
 |
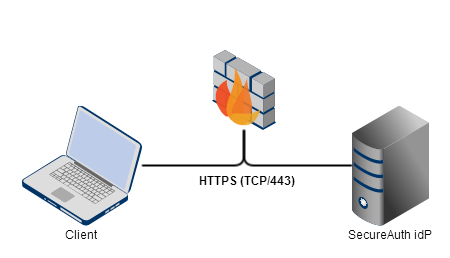
SecureAuth-specific Services
All interaction with the SecureAuth Identity Platform appliance, whether administrative or user facing, occurs over HTTPS for maximum security. HTTPS (TCP/443) access must be allowed or the appliance will be rendered inoperable.
Notice
When using multiple SecureAuth Identity Platform appliances in a load balanced configuration, you need to be aware of how sessions are handled. Normally, a load balancer routes each request independently to a node with the smallest load. While this method works fine for normal (stateless) web applications, it will cause issues with SecureAuth Identity Platform, which is a stateful application.
In this case, the node which first handles the request from a user must continue to answer their requests until the session concludes. To accommodate this use case, most load balancers have a sticky session feature (also known as session affinity) which enables the load balancer to bind a user's session to a specific node. This ensures that all requests coming from the user during the session will be sent to the same node.
 |
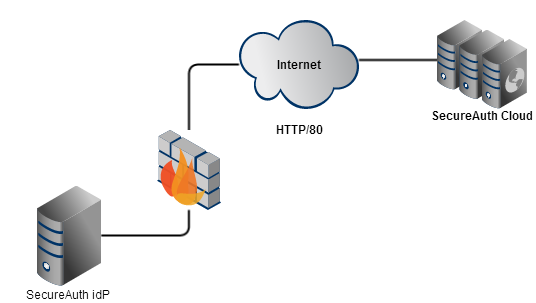
The SecureAuth cloud infrastructure handles many critical services for the SecureAuth Identity Platform product, including but not limited to:
SMS One Time Password (OTP) Notifications
Telephony One Time Password (OTP) Notifications
Issuance of x509 v3 certificates
Licensing
Adaptive Authentication options
To ensure proper operation of the SecureAuth Identity Platform appliance, refer to SecureAuth cloud services for the URLs required to be accessible from the device.
 |
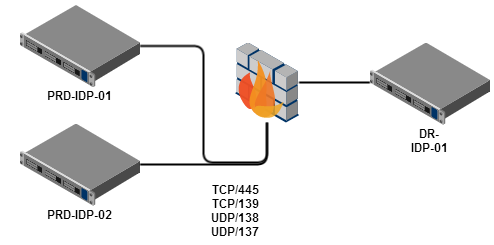
The SecureAuth sync service keeps configuration information synchronized between two or more SecureAuth Identity Platform appliances. If you would like to install the service in your environment, contact SecureAuth support at (949) 777-6959 option 2 or submit a ticket at support.secureauth.com to arrange for the software to be installed. As a prerequisite to deploying the service, ensure the following ports and protocols are allowed between the SecureAuth Identity Platform appliances:
SecureAuth Sync Service | ||
Direction | Port | Protocol |
|---|---|---|
Inbound\outbound | 445 | TCP |
Inbound\outbound | 139 | TCP |
Inbound\outbound | 138 | UDP |
Inbound\outbound | 137 | UDP |
 |
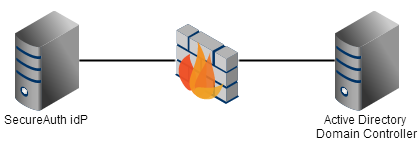
Client-based Services
If the SecureAuth Identity Platform appliance will be joined to a domain, then you will need to ensure that the ports listed in the Domain Membership table above are allowed between the SecureAuth appliance and applicable Domain Controllers.
 |
If the SecureAuth Identity Platform appliance is used to reset passwords, then you need to ensure the port listed below are open between the appliance and applicable domain controllers:
Password Reset | ||
Direction | Port | Protocol |
Outbound | 139 | TCP |
Outbound | 445 | TCP, UDP |
Outbound | 464 | TCP, UDP |
 |
If the SecureAuth Identity Platform appliance is writing logging data to an external ODBC, Microsoft SQL or Syslog server, then you need to ensure that the ports listed below are open between the appliance and the DB/Syslog server:
Reporting / Database | |||
Direction | Port | Protocol | Description |
Outbound | 1433 | TCP | MS SQL / ODBC |
Outbound | 514 | UDP | Syslog |
 |
If SecureAuth Identity Platform communicates with a RADIUS server, then you need to ensure the ports listed below are open:
RADIUS | ||
Direction | Port | Protocol |
Outbound | 1812 | UDP |
Outbound | 1813 | UDP |
Notice
Early deployments of RADIUS were done using UDP port number 1645, which conflicts with the datametrics service. The officially assigned port number for RADIUS is 1812.
 |
Additional Information
Active Directory and Active Directory Domain Services Port Requirements
RFC 2865: Remote Authentication Dial In User Service (RADIUS)
How to enable LDAP over SSL with a third-party certification authority
http://tools.ietf.org/html/rfc2865
How to add a Subject Alternative Name to a secure LDAP certificate