15Five SAML integration
Multi-Factor Authentication (MFA) is an extra layer of security used when logging into websites or apps. Individuals are authenticated through more than one required security and validation procedure that only they know or have access to.
Security Assertion Markup Language (SAML) is a protocol for authenticating to web applications. SAML allows federated apps and organizations to communicate and trust one another’s users.
Arculix, as a SAML provider, improves the user login experience for 15Five users with smart and convenient single sign-on (SSO) MFA.
Prerequisites
Configured Arculix instance and user account with administrative privileges for Arculix.
Configured Arculix LDAP Agent.
For more information, see the Arculix LDAP Agent deployment guide.
User account with administrative privileges for 15Five.
Registered 15Five tenant; which is known as your "subdomain".
15Five configuration
In this section, you will configure 15Five as a service provider (SP).
Download the SAML metadata and certificate for your organization from Arculix.
Metadata download:
https://sso.acceptto.com/<myorganization>/saml/download/metadataView metadata:
https://sso.acceptto.com/<myorganization>/saml/metadataCertificate download:
https://sso.acceptto.com/<myorganization>/saml/download/certLog in to 15Five as an administrator with your registered 15Five tenant name and password.
Go to ACCOUNT SETTINGS > Company settings > SSO.
The Single Sign-On welcome screen appears.
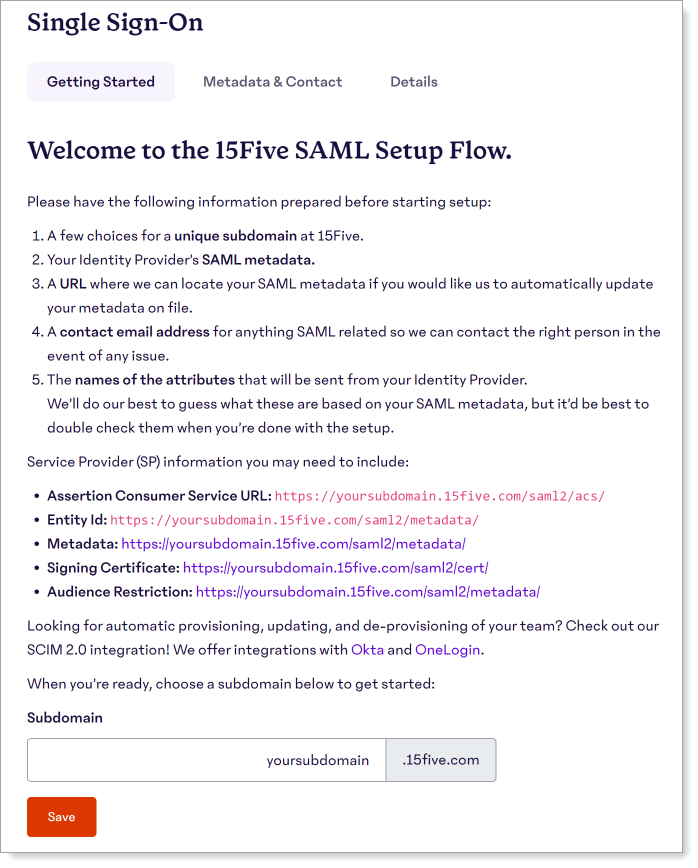
On the Getting Started tab, set a unique subdomain in the Subdomain text box,
For example, yoursubdomain.
On the Metadata & Contact tab, set the following configurations.
Contact Email
Your email or the IT support email for your organization.
Automatically update metadata
Leave this check box cleared.
XML metadata
Copy and paste the Arculix metadata you downloaded earlier.
For example, this is the metadata in
https://sso.acceptto.com/<myorganization>/saml/metadata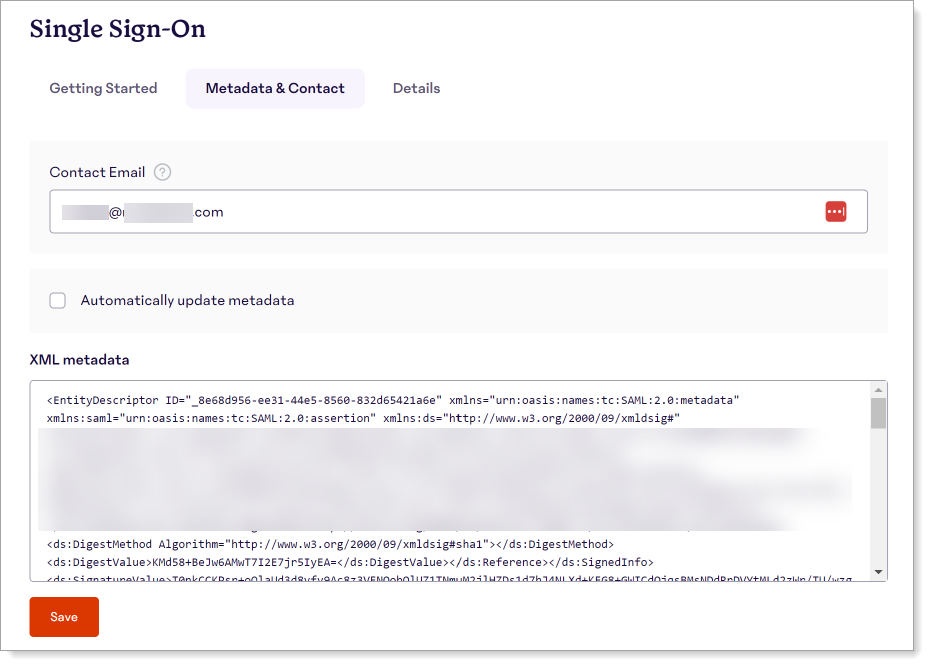
Save your changes.
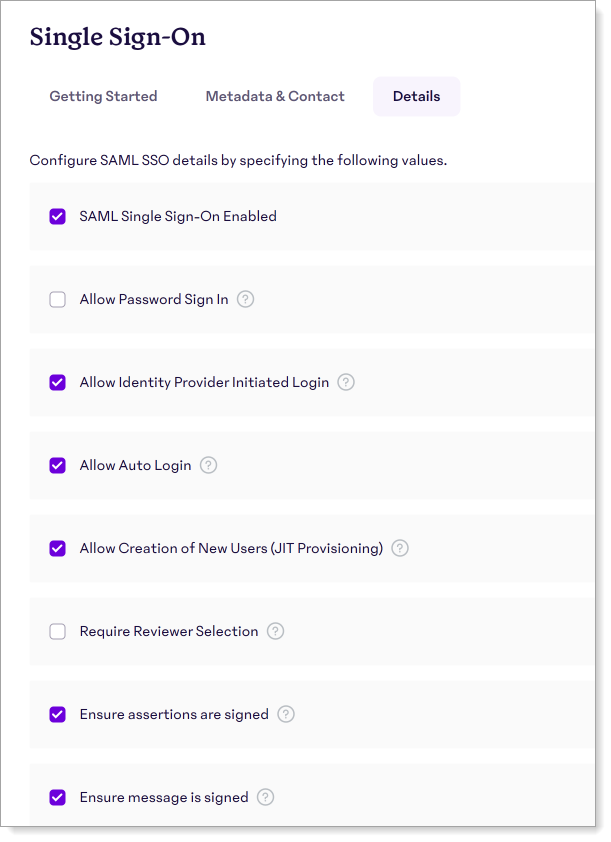
On the Details tab, set the following configurations as needed.
For more information about these fields, see the 15Five support article on Single Sign-on (SSO).
In the Single Sign-on section, select the check boxes as needed for your organization.
SAML Single Sign-on Enabled
Select this to enable SAML SSO.
Allow Password Sign In
To allow users the ability to log in using their email and password, instead of through SSO. You can select this check box during testing and then clear it later.
Allow Identity Provider Initiated Login
Select this check box to allow your users to log in from the SSO dashboard when they log in through your organization's IdP.
Allow Auto Login
Select this check box to allow your end users to automatically login through their IdP without having to re-authenticate.
This option works only when the Allow Password Sign In check box is cleared.
Allow Creation of New Users (JIT Provisioning)
Select this check box to allow the creation of new users via JIT provisioning.
Require Reviewer Selection
Requires an end user to choose their reviewer during their first time log in. This occurs only when the reviewer information is not sent in the SAML response. Most organizations do not use this option..
If you select this option, you will need to specify the Reviewer Attributes in Step 6c.
Ensure assertions are signed
Select this check box to send signed SAML assertions to 15Five.
Ensure message is signed
Select this check box to send a signed SAML message to 15Five.
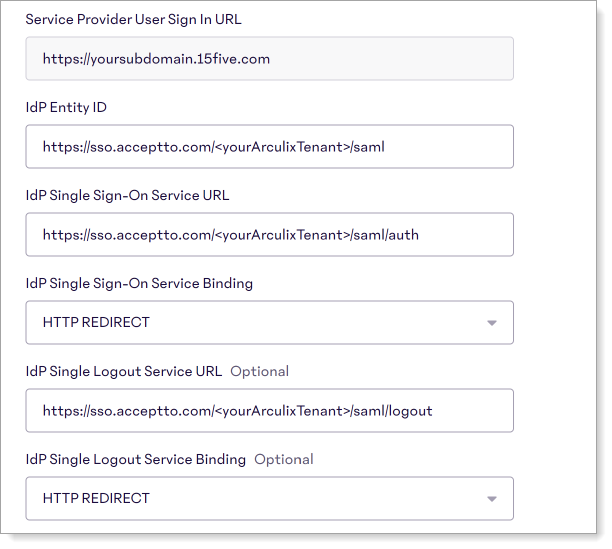
In the next set of configurations, the first four fields are auto-populated by the Arculix XML metadata that was entered earlier. Make sure to review these configurations.
Service Provider User Sign in URL
The login URL for your organization to 15Five. This is your subdomain.
For example,
https://yoursubdomain.15five.com.IdP Entity ID
The Entity ID URL found in the Arculix metadata.
For example,
https://sso.acceptto.com/<yourArculixTenant>/samlIdP Single Sign-On Service URL
The login URL found in the Arculix metadata.
For example,
https://sso.acceptto.com/<yourArculixTenant>/saml/authIdP Single Sign-On Service Binding
Set to HTTP REDIRECT.
IdP Single Logout Service URL
Optional. Enter the logout URL found in the Arculix metadata.
In this example, it is
https://sso.acceptto.com/<yourArculixTenant>/saml/logoutIdP Single Logout Service Binding
Optional. Set the service binding for user logouts from applications in the same SSO session through the Arculix.
In the User Attributes section, set the relevant attributes.
Name ID Contents
Set to Email.
Email attribute name
Leave blank or set to an email attribute like
mail.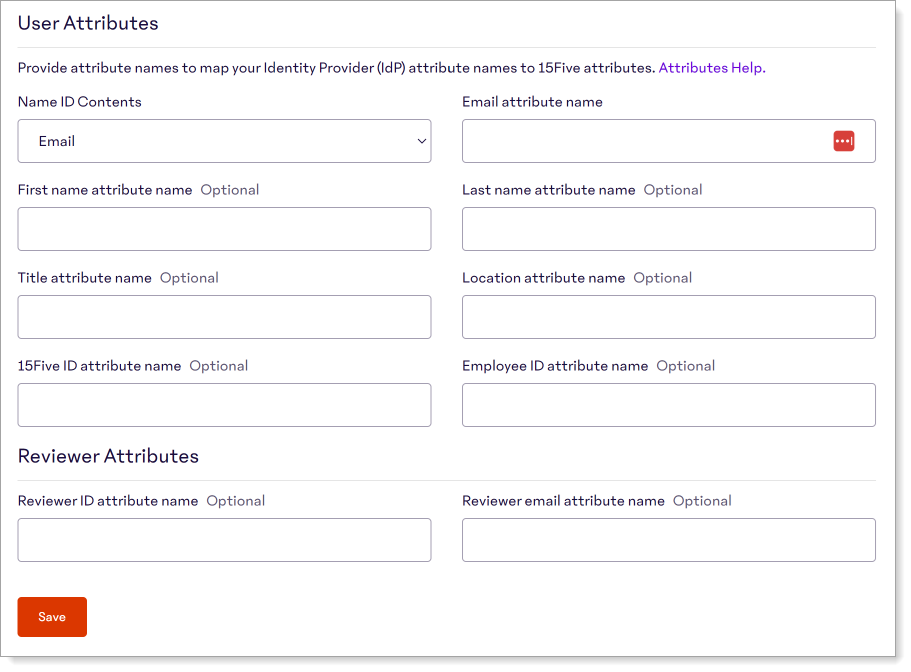
Save your changes.
Arculix SAML configuration as an Identity Provider (IdP)
In this section, you'll add an application for 15Five and set the SAML configuration settings. This will be the Identity Provider (IdP) side of the configuration.
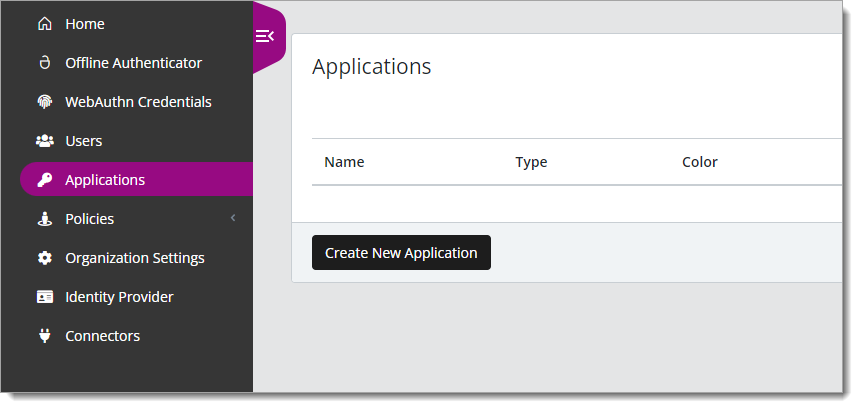
Log in to Arculix with an administrative account and go to Applications.
Click Create New Application.
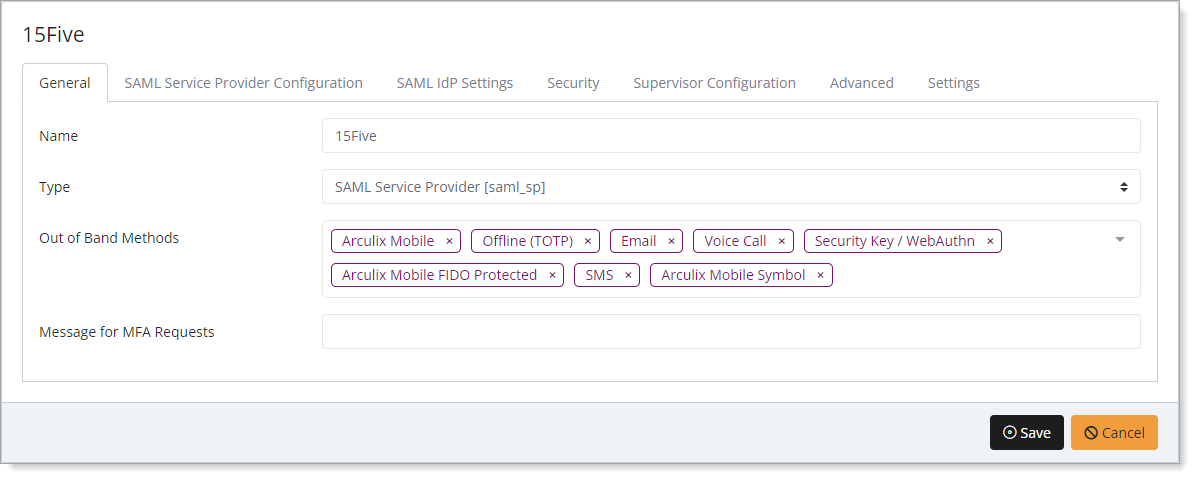
In the New Application form, on the General tab, set the following configurations:
Name
Set the name of the application. This is the name to display for push notifications, in the Admin panel, Application portal, and audit logs.
For example, 15Five.
Type
Set to SAML Service Provider.
Out of Band Methods
Select the allowed methods end users can choose to approve MFA requests.
For example, Arculix Mobile app (push notifications), SMS, or Security Key.
Message for MFA Requests
Optional. Type a message displayed to end users when sending an MFA request via push notification, SMS, or email.
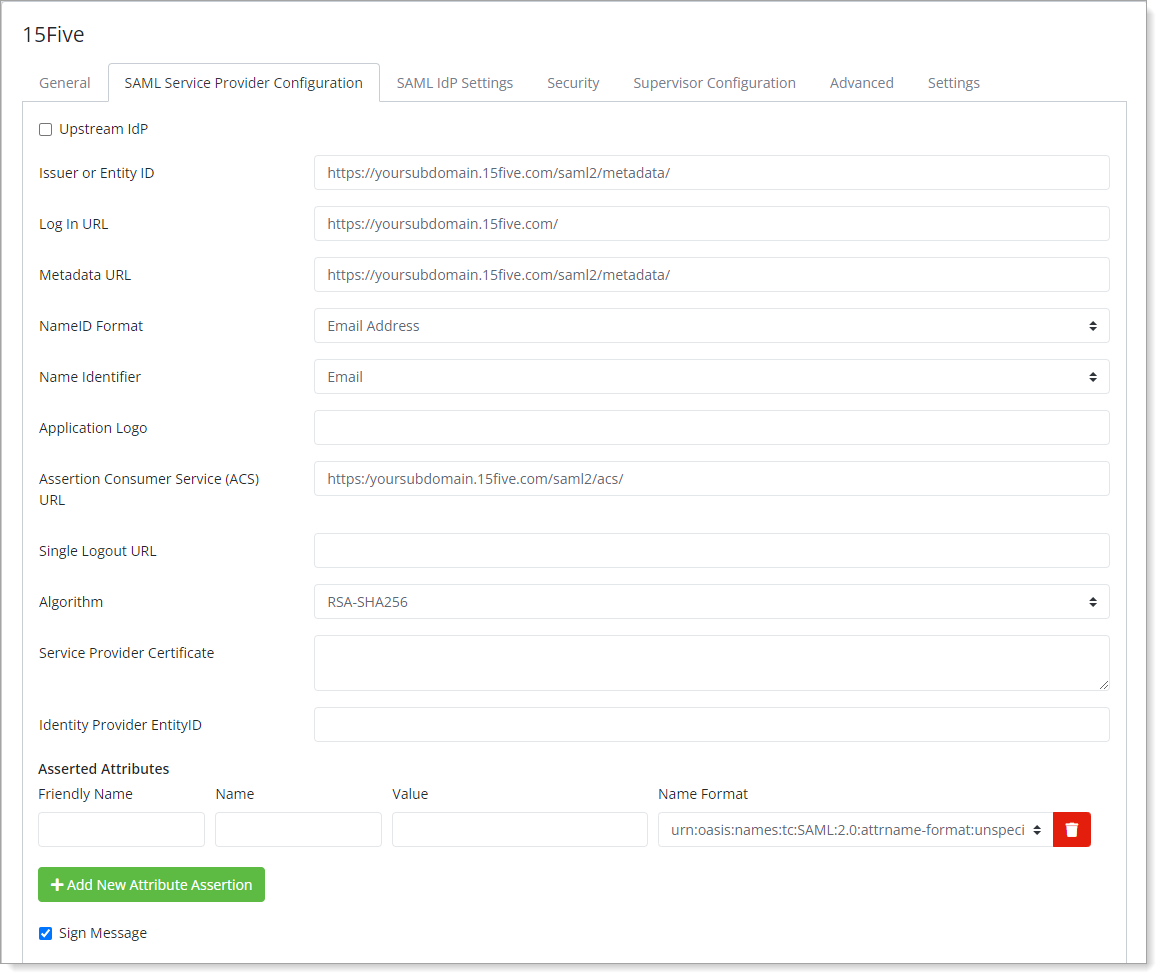
Select the SAML Service Provider Configuration tab, and set the following configurations:
Issuer or Entity ID
Enter the issuer or entity ID for this configuration.
For example,
https://yoursubdomain.15five.com/saml2/metadata/Log in URL
Enter the URL for log in to this configuration.
For example,
https://yoursubdomain.15five.com/.Metadata URL
Enter the metadata URL for 15Five.
For example,
https://yoursubdomain.15five.com/saml2/metadata/NameID Format
Set to Email Address.
Name Identifier
Set to Email.
ACS URL
The Assertion Consumer Servcie URL of your 15Five instance.
For example,
https:/yoursubdomain.15five.com/saml2/acs/Algorithm
Set to RSA-SHA256.
Certificate
Copy and paste the 15Five certificate downloaded from
https://yoursubdomain.15five.com/saml2/cert/Sign Message
Select this check box if you selected this in the 15Five configuration.
At the bottom of the page, add an entry in the Response Hosts section.
For example,
yoursubdomain.15five.com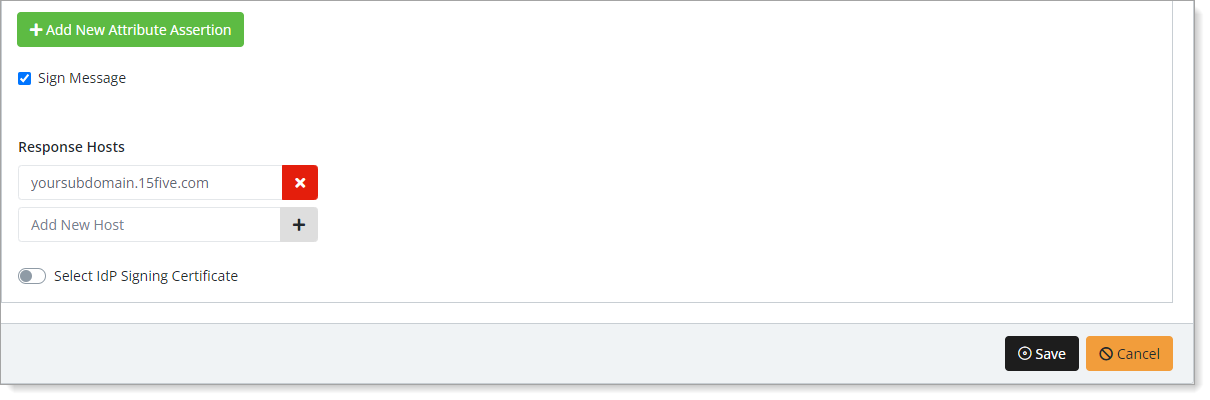
Save your changes.
Test your application integration
Go to your 15Five login instance at https://yoursubdomain.15five.com/ and choose Sign in using Single Sign-on.
You will be redirected to the Arculix SSO page.

After successful authentication, select your preferred MFA method to approve access to the 15Five application.
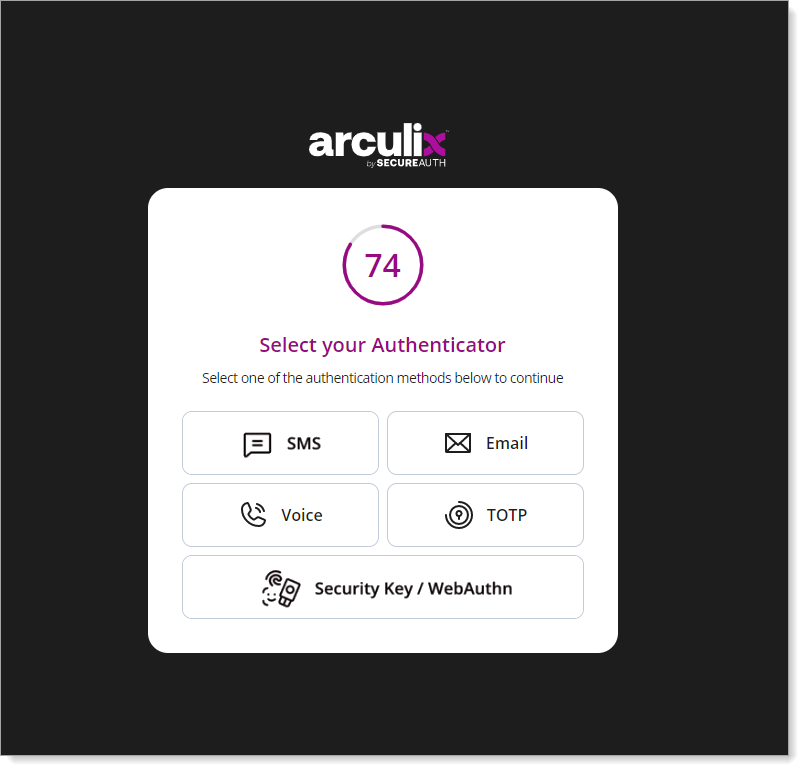
If your configuration is correct, you are logged in to 15Five.com.