Audit logs
In Arculix, you can view and access real-time audit logs, which include detailed data on the context and results of authentication and workstation events.
Audit log summary
Log in to Arculix and from the left navigation, click Home.
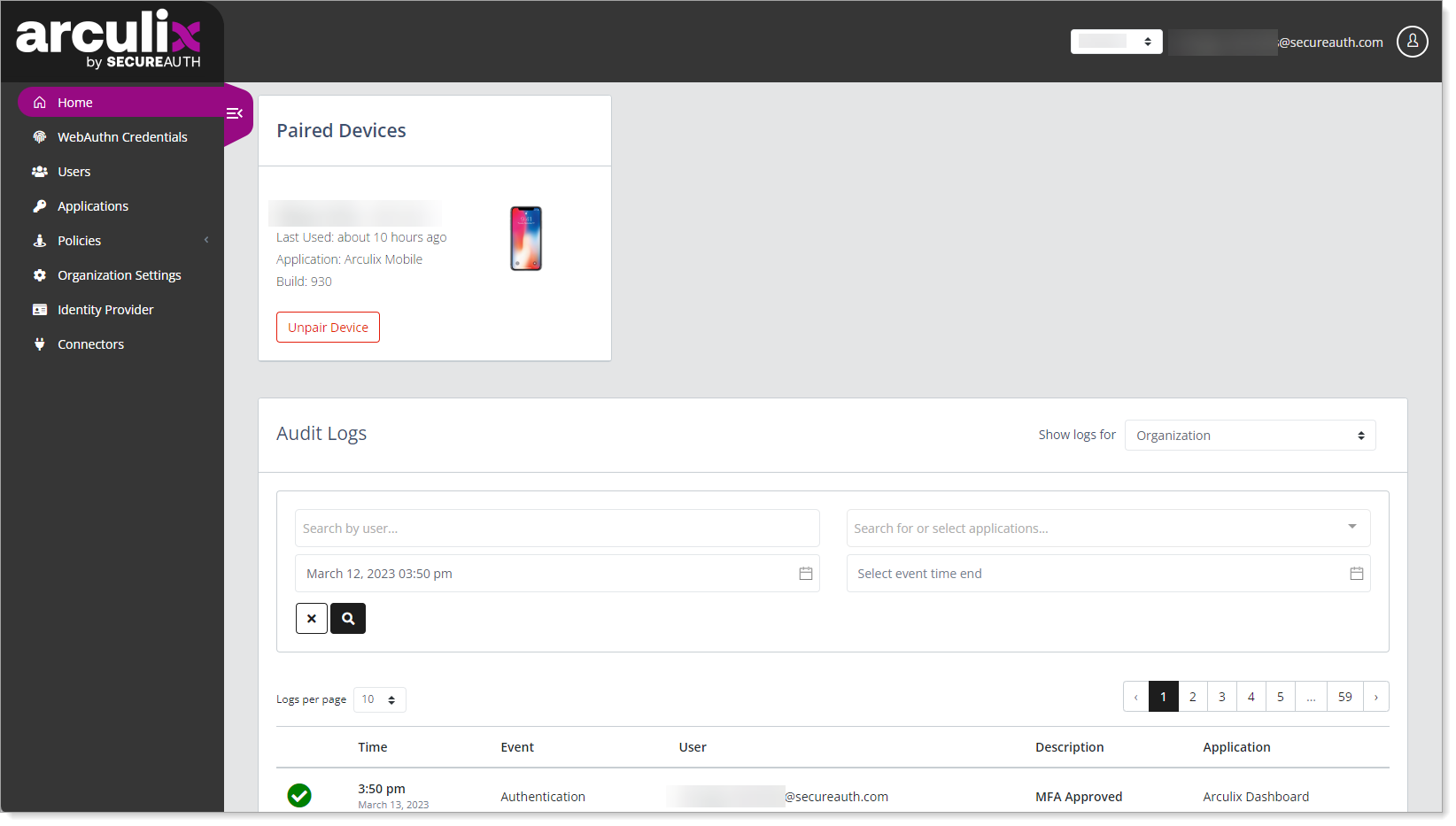
In the Show Logs for field, select whether you want to view authentication events by Organization or Current User.
Organization
View all events within a specific organization.
You must be an administrator to view logs by organization.
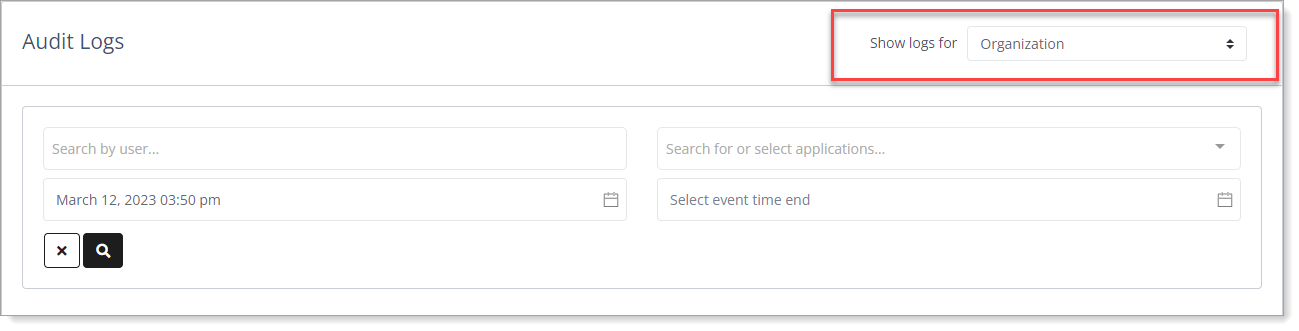 Search filters
Search filtersSearch by user – Filter your search by user email. You can enter any part of an email address in the search.
Search for or select applications – Filter your search by application.
Select event time start – Filter your search by the starting date and time of the data event.
Select event time end – Filter your search by the ending date and time of the data event.
Current User
View events for yourself as the current user logged in to Arculix.
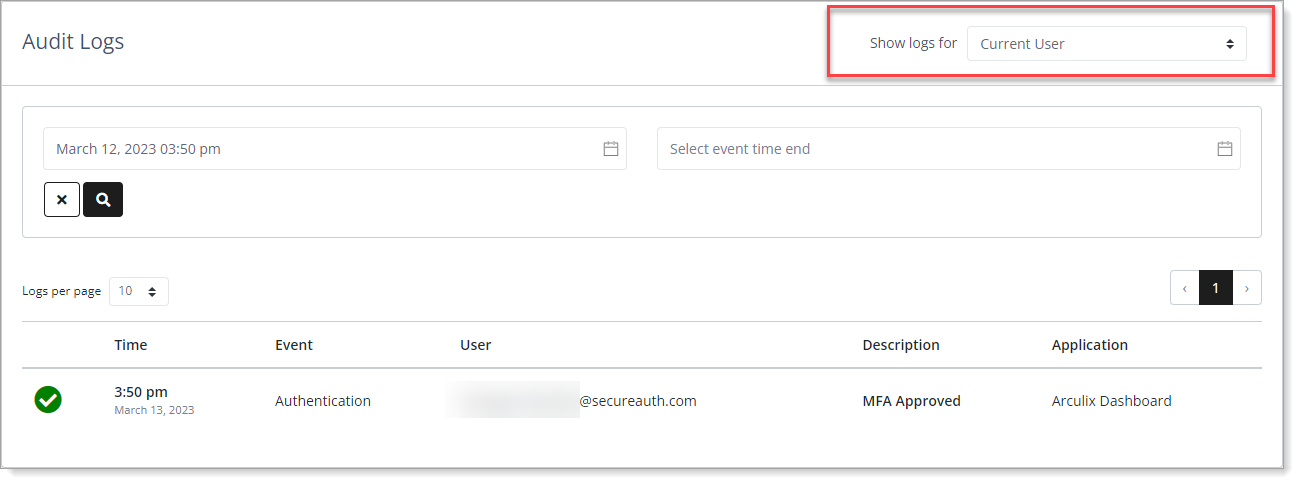 Search filters
Search filtersSelect event time start – Filter your search by the starting date and time of the data event.
Select event time end – Filter your search by the ending date and time of the data event.
View the audit logs.
For an explanation of the event and description types, see Event types and Description types.
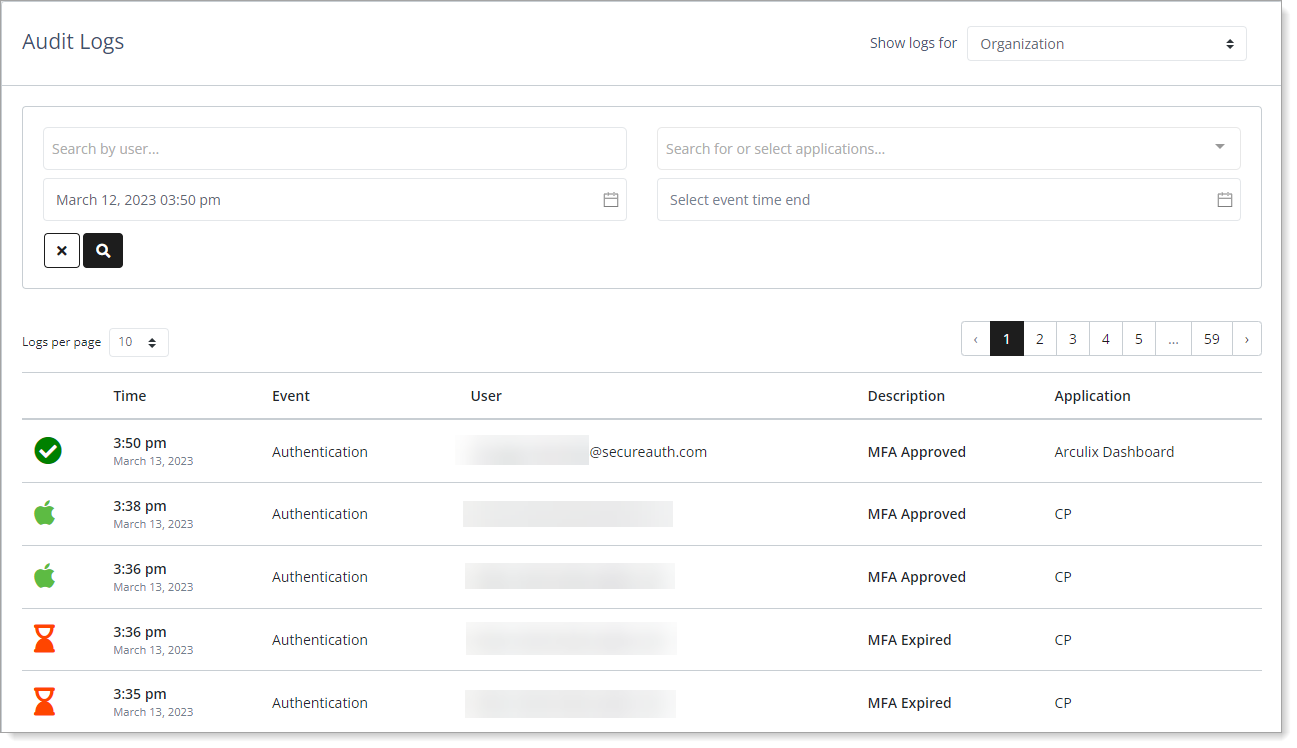
Audit logs by Organization
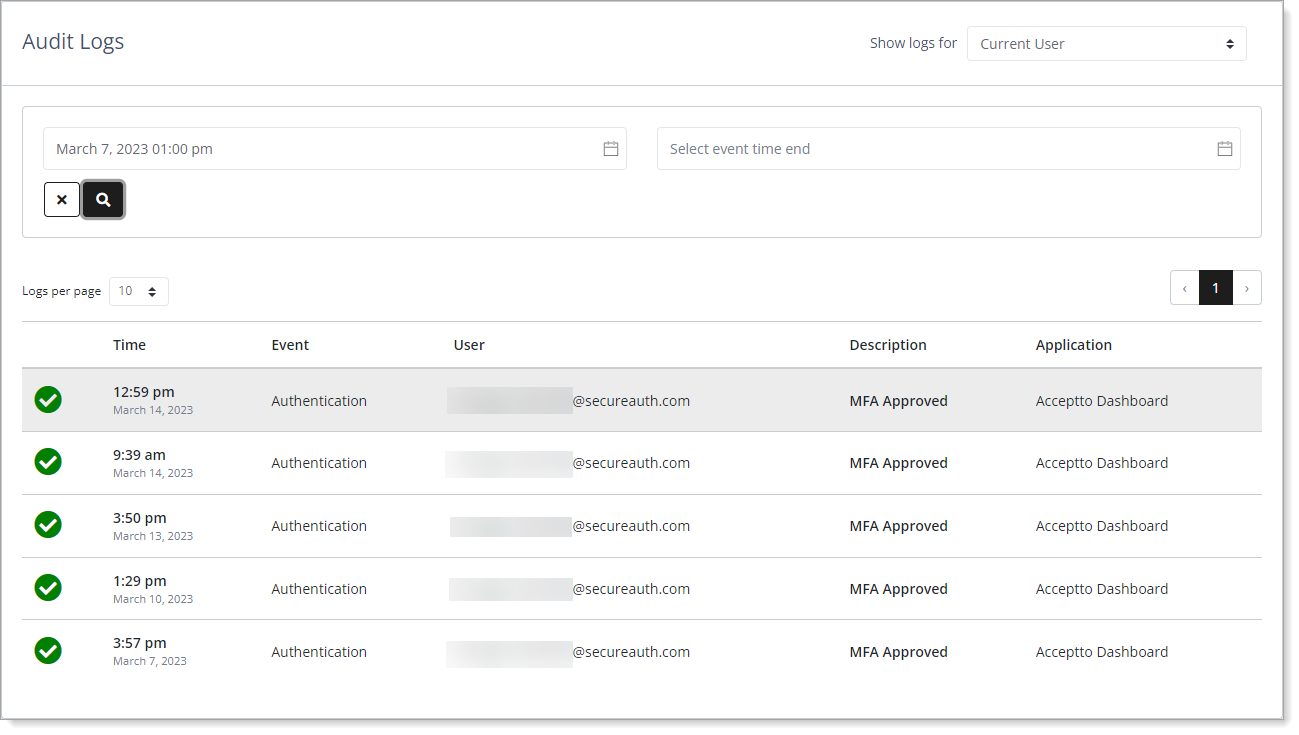
Audit logs by Current User
To view more details of an authentication event, click the log entry in the summary list.
For an explanation of log details, see Audit log details.
Event types
In the Events column of the audit logs summary list, it displays the following event types.
Authentication – Login requests to web apps, Credential Provider, RADIUS, and others.
Continuous Authentication – Logins to additional resources during an authenticated SSO session.
Data Event – Log entry of a data event like the creation or removal of user permissions.
Workstation Log – Workstation events such as locked, unlocked, paired, and logged out.
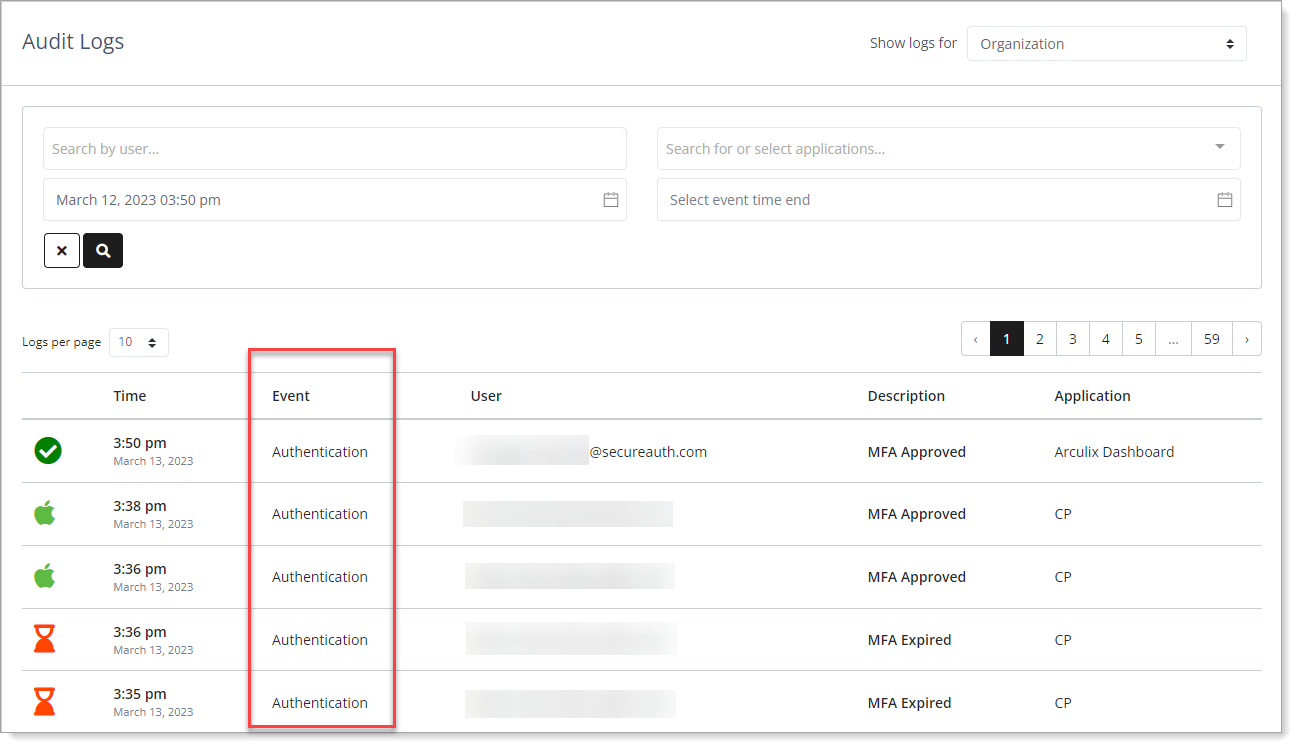
Organization audit logs - Event types
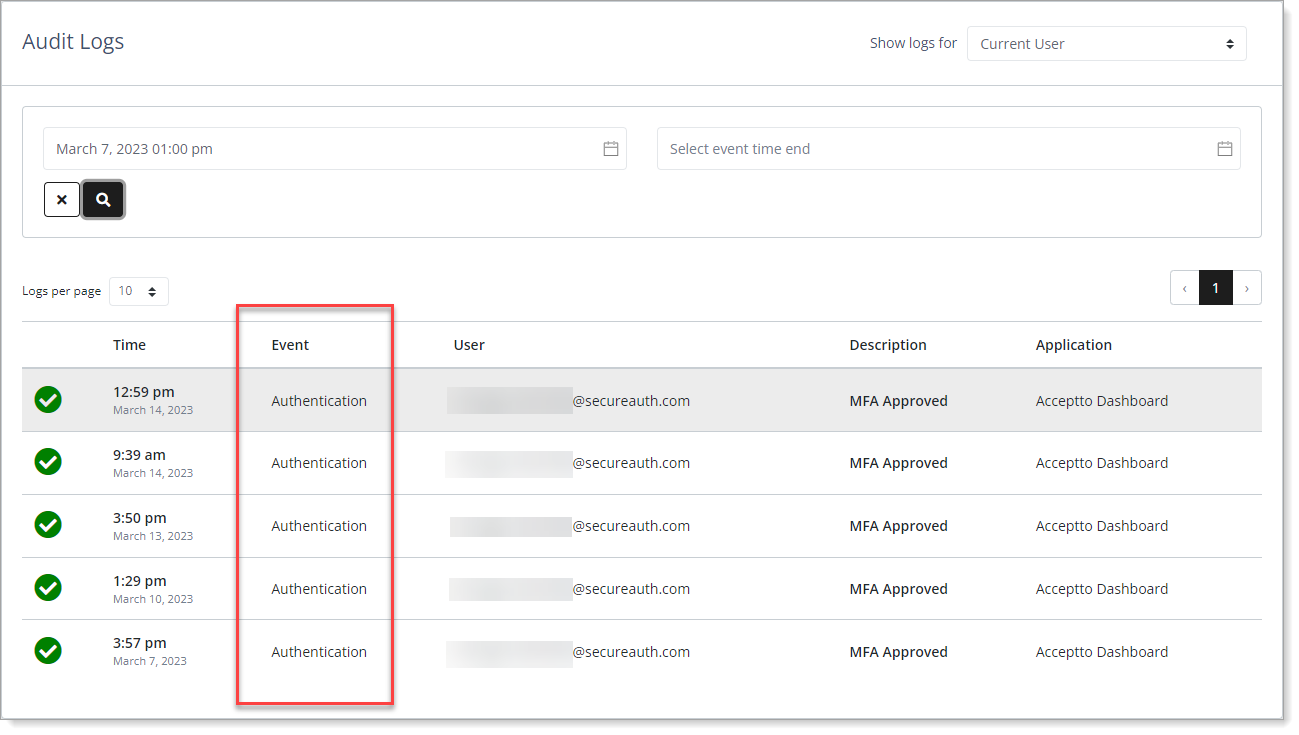
Current User audit logs - Event types
Description types
In the Description column, it displays a description associated with the event type.
MFA Approved – Successful login, approved by the user or automatically via policy.
Automatically Approve – Continuous authentication approved by the policy engine.
MFA Expired – Login request expired without being approved.
MFA Rejected – Login request rejected by the user or due to policy.
Pending – Login request pending approval.
Logged In – User is logged in to workstation.
Logged Out – User is logged out of workstation.
Locked – Workstation locked by user, administrator, or policy.
Unlocked – Workstation unlocked by user, administrator, or policy.
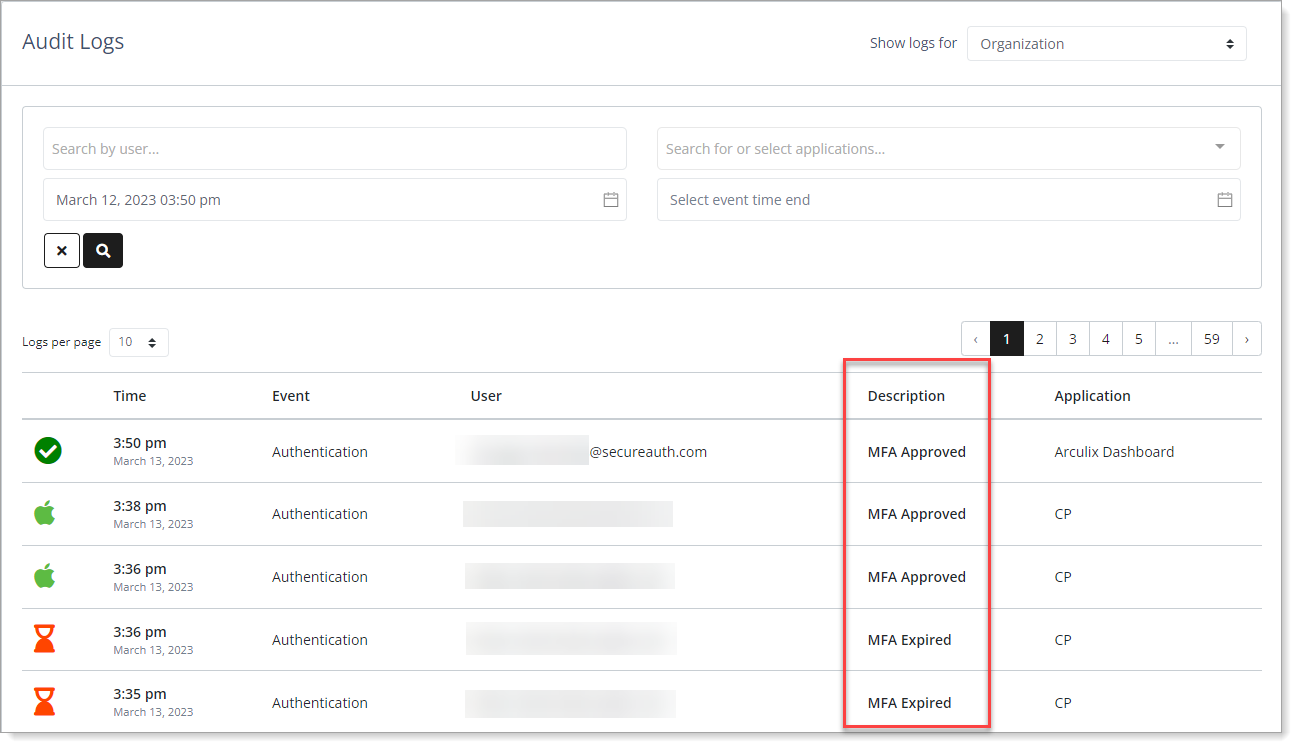
Organization audit logs - Description types
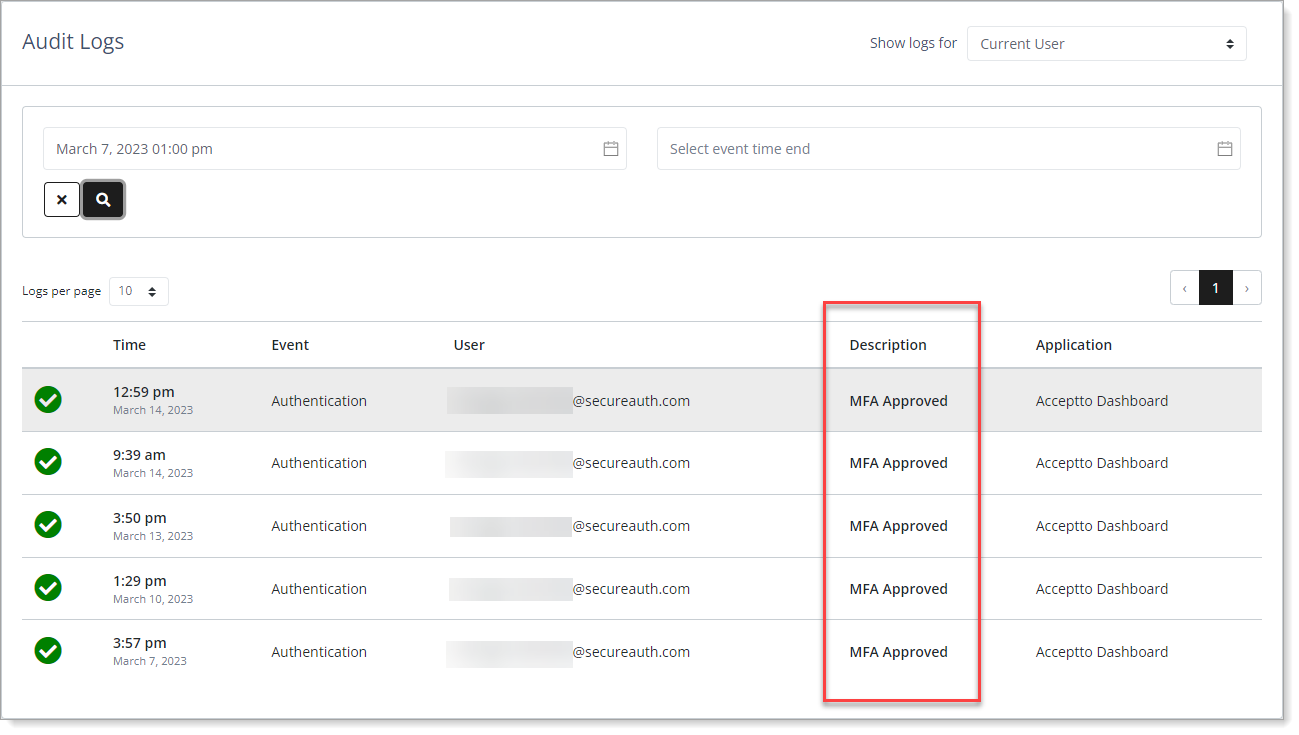
Current User audit logs - Description types
Audit log details
In the Audit Logs summary list, click a log entry.
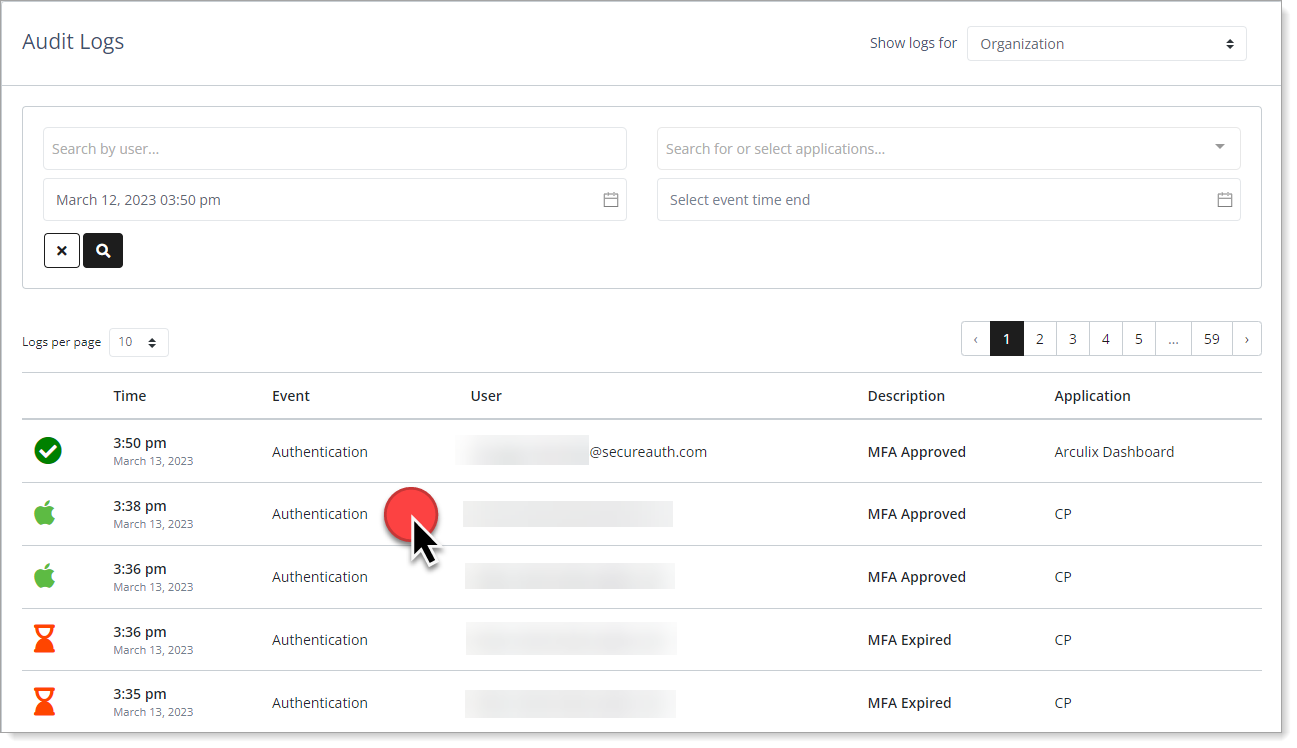
Click anywhere on a log entry to view details
View details about an authentication event.
Different types of information are displayed for different events.
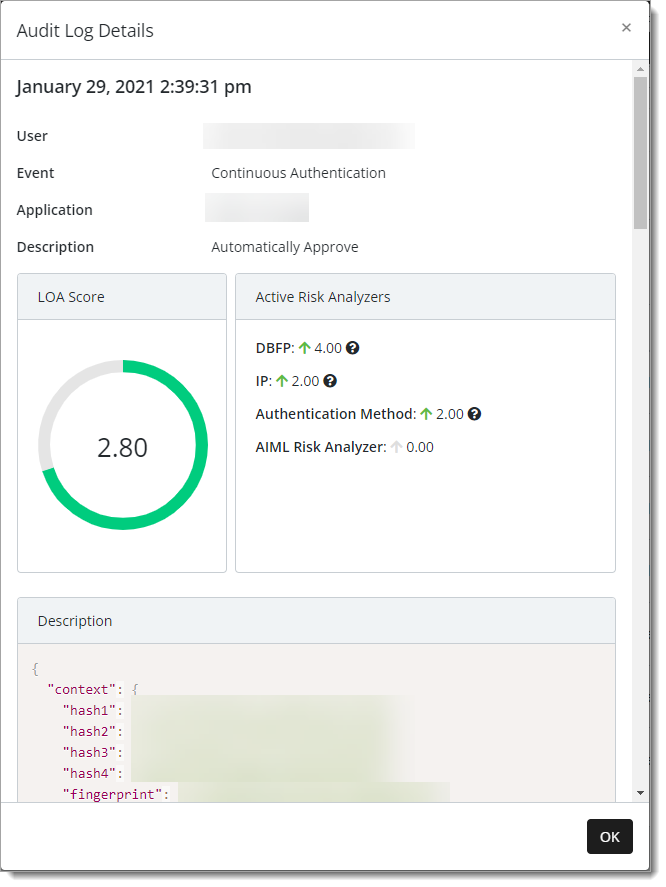
Continuous Authentication event details
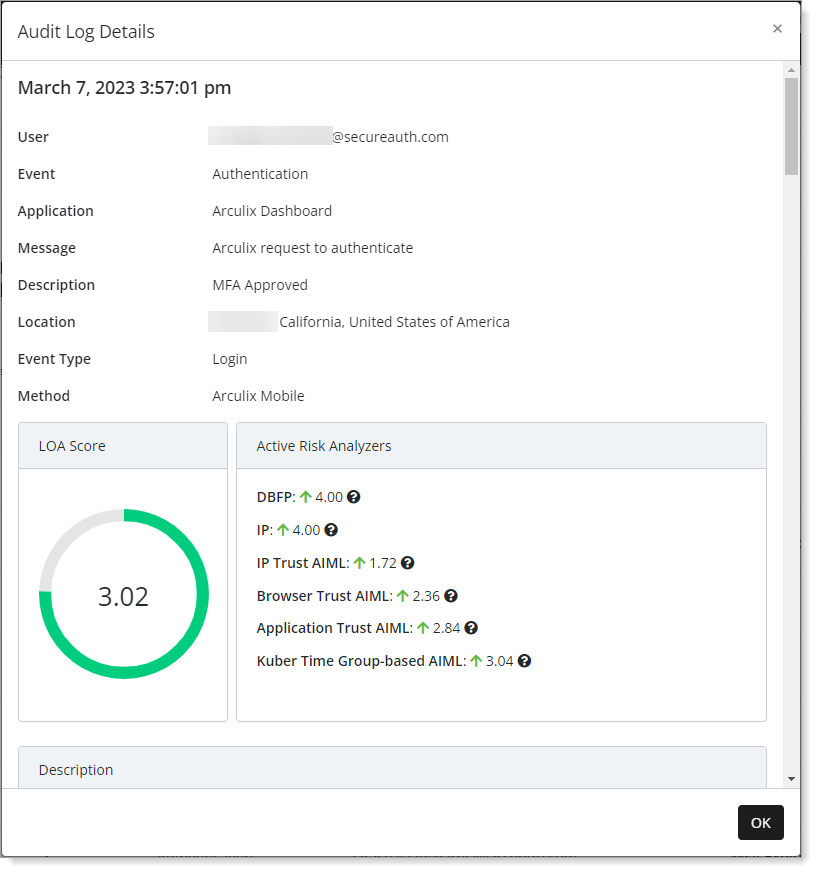
Authentication event details
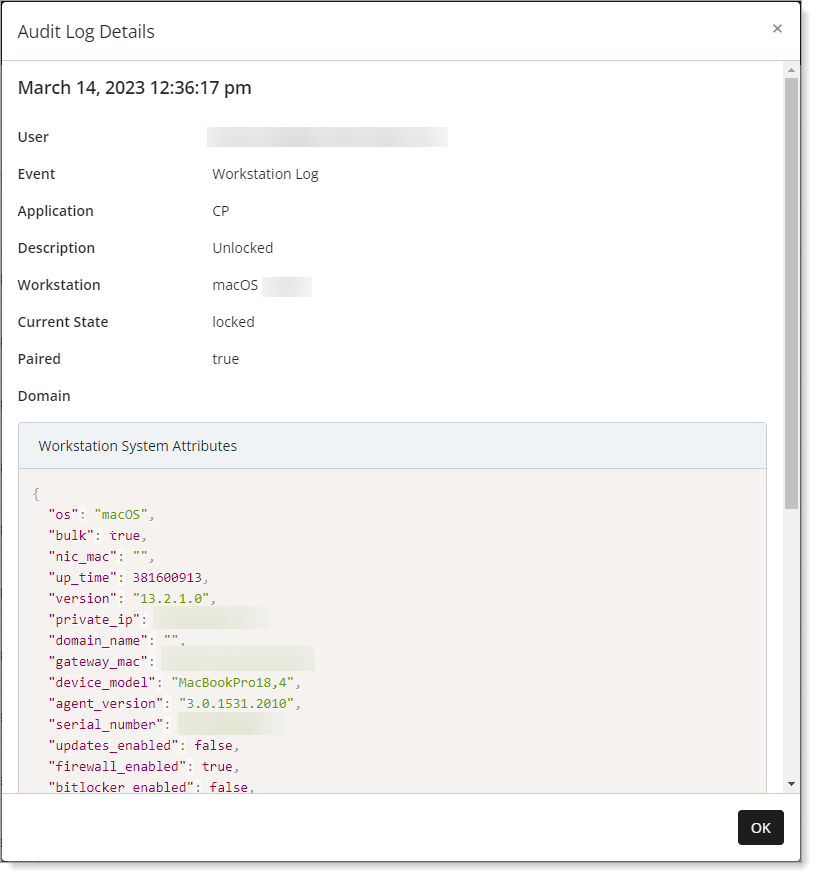
Workstation Log event details
Event details
The log details for events can include any of the following:
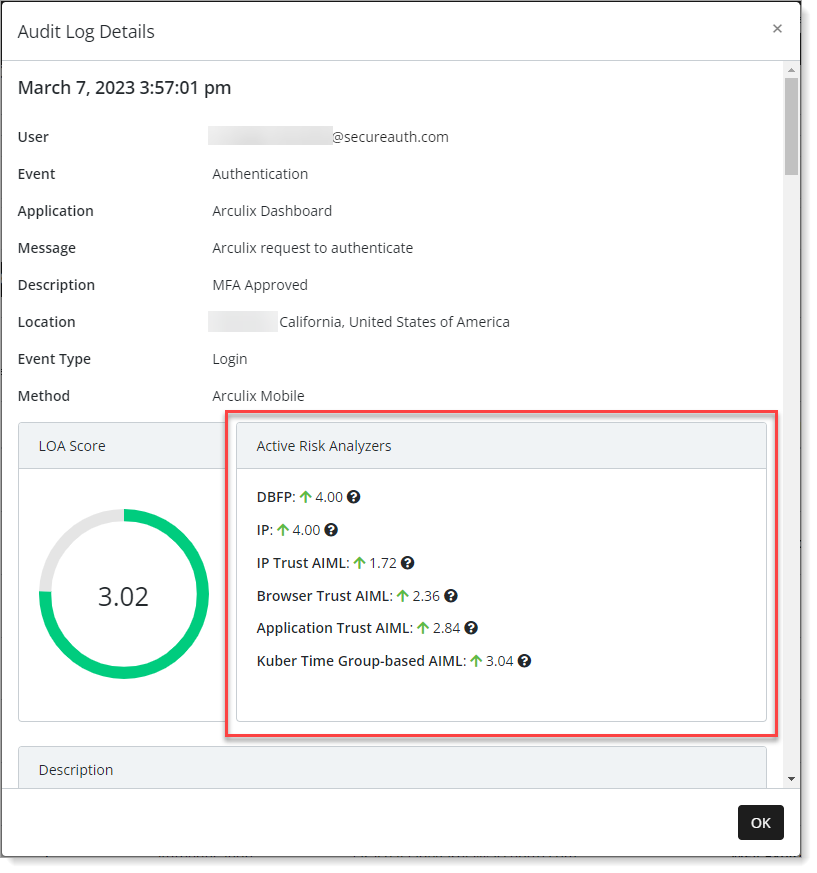
User – User email account that triggered this event.
Event – Type of event that occurred. For example, an authentication event to log in to Arculix.
Application – Name of application associated with this event. For example, Arculix Dashboard or SSO portal.
Message – Message associated with this event.
Description – Description associated with event type. For example, MFA Approved for login to Arculix.
Location – Obtained user location where this event occurred.
Event type – Result associated with the event, like login, logout and so on.
Method – The method associated with the event. For example. Arculix Mobile was used to authenticate and approve log in to the event.
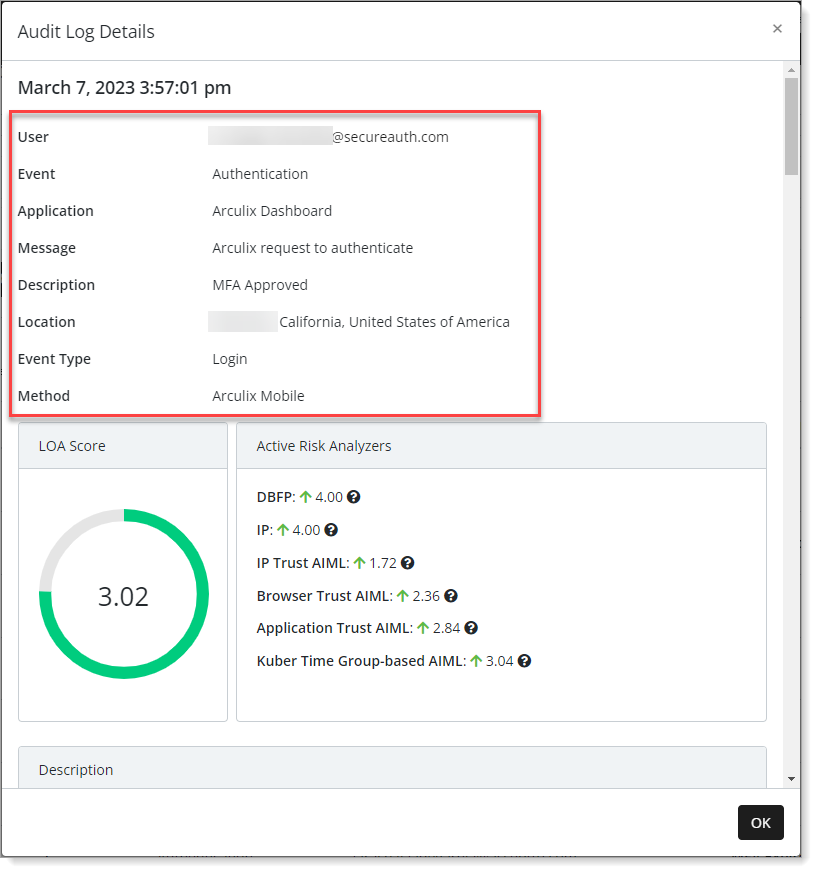
LOA Score
The LOA score is a number between 0.0 to 4.0. The higher the LOA the more likely the user is who they claim to be. The overall LOA score is calculated out of the confidence and risk scores generated by the risk analyzers.
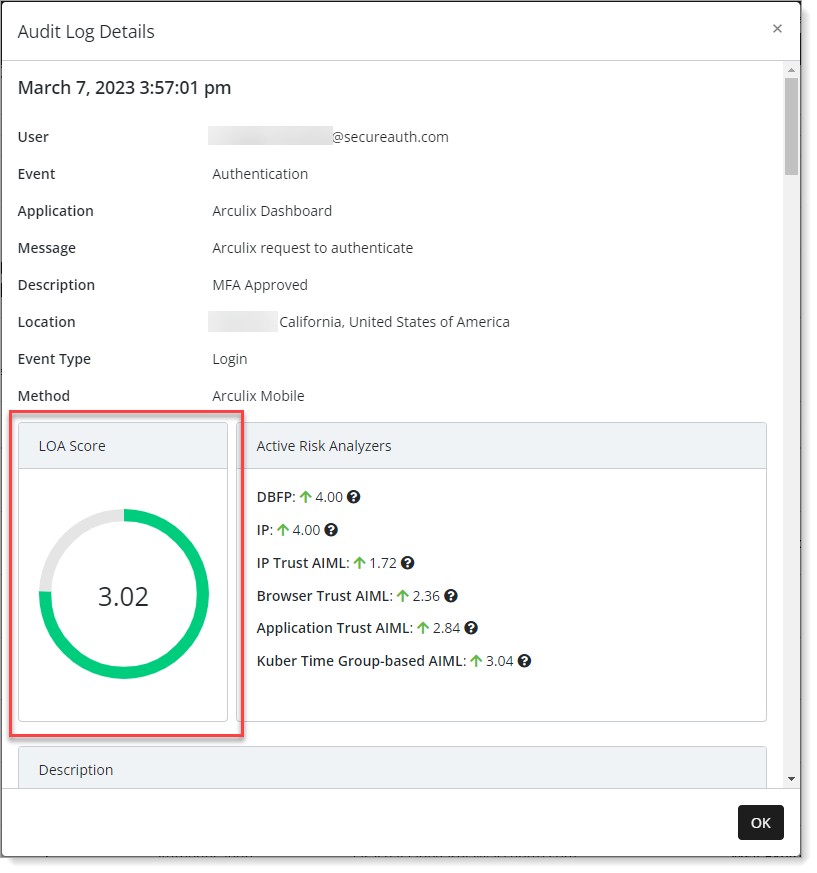
Active Risk Analyzers
Risk analyzers are responsible for fetching data from different sources and calculating a final score based on the collected information. Each risk analyzer focuses on a specific area and gets a specific kind of data. For example, the IP risk analyzer gets some information about the IP address of the user and generates a score based on that address.
This is a non-inclusive list of built-in risk analyzers:
AIML: Provides a score based on the user contextual information provided to the AI/ML engine in Arculix.
Auth method: Provides a score based on the authenticator used for the last MFA.
DBFP: Provides a score based on the user's browser fingerprint.
IP: Provides a score based on the user's IP address.
Location: Provides a score based on the user's obtained location. The location will be obtained from the phone or browser and if not provided, falls back to the IP-based location.
Tip
You can click the question mark icon next to each risk analyzer for more information.
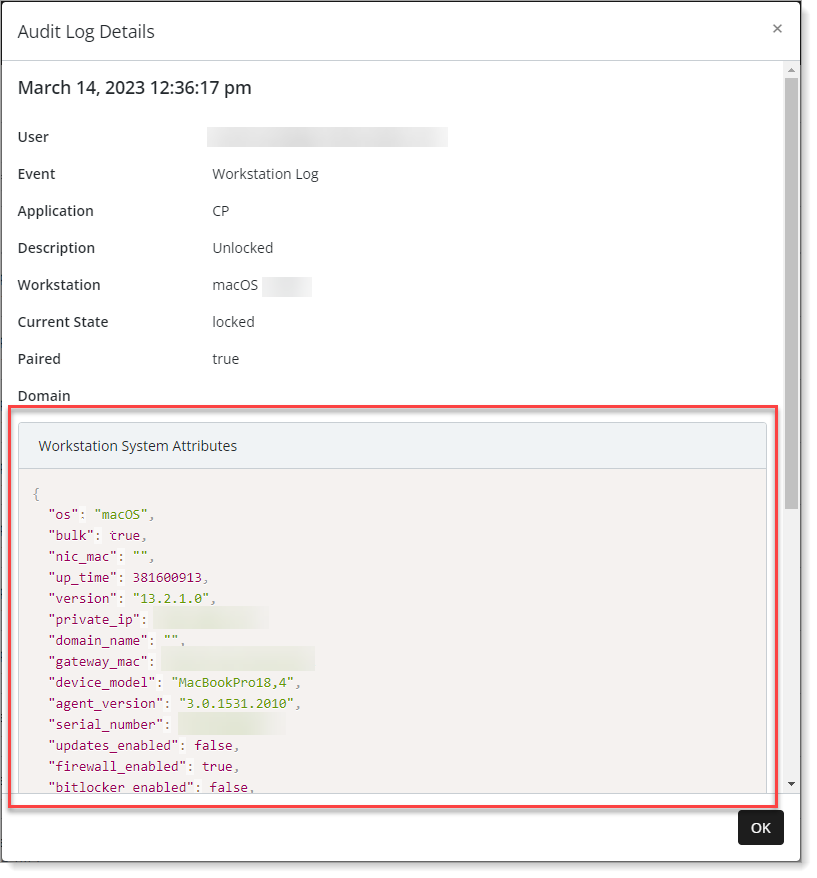
Description / Workstation System Attributes
Detailed context information in code about about the audit log entry that includes risk analyzer results and workstation configuration.