Connect an Active Directory
Connect a Microsoft Active Directory (AD) to Arculix thorugh the admin console. Connecting AD allows you to manage user access to resources through your existing Active Directory.
Prerequisites
Arculix LDAP Agent installed, configured, and online
To enable password management features, use LDAPS and configure appropriate service credentials
Add an AD user directory
In Arculix, click User Directories > Create New Directory.
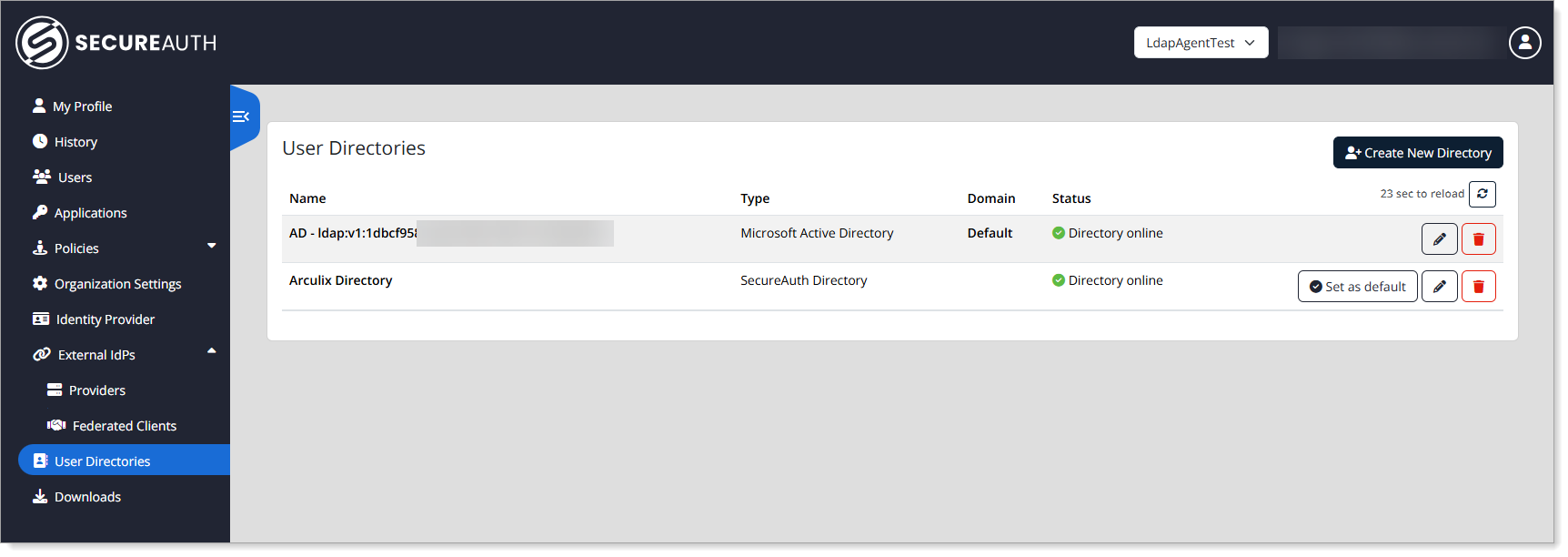
Configure the basic AD settings.
Type
Set to Microsoft Active Directory
Name
Enter a unique name to identify this AD connection.
Domain
Add one or more domains.
Settings
Enable the following based on your requirements:
Inline Factor Provisioning – Assigns authentication factors to users automatically during their first login.
Inline User Provisioning – Creates a user record in Arculix when someone logs in from this directory for the first time.
Search Directory for Groups – Looks up user group membership directly from the directory during authentication for policy enforcement.
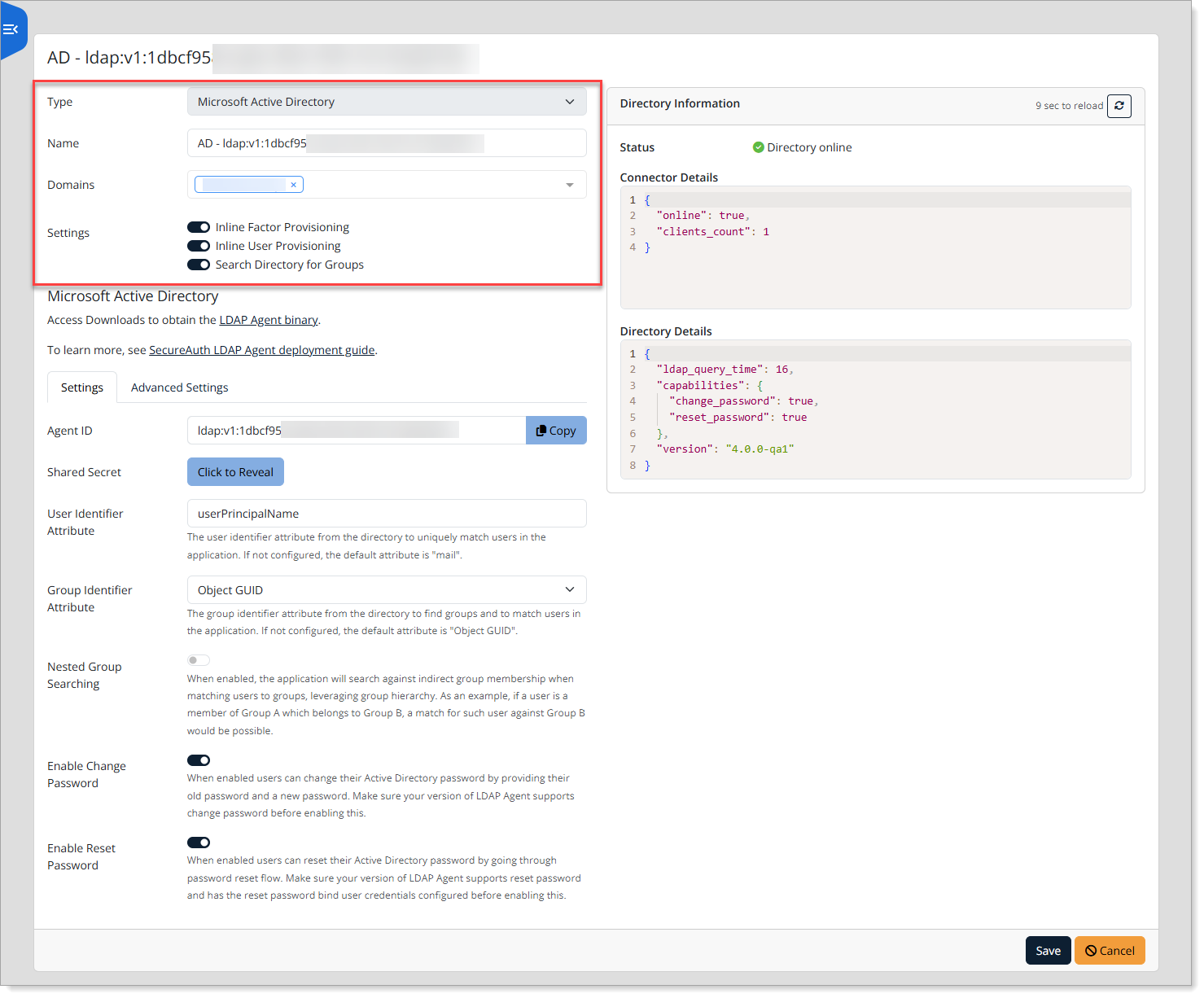
On the Settings tab, configure the following settings.
Agent ID
Auto-filled identifier for this AD connection.
Shared Secret
Used to securely communicate with the LDAP Agent.
User Identifier Attribute
Enter the attribute used to uniquely identify users.
Default:
mailGroup Identifier Attribute
Enter the attribute used to identify groups and match users to groups.
Default:
Object GUIDNested Group Searching
Enable this to match users to groups through nested (indirect) group membership.
For example: If a user is in Group A, and Group A is a member of Group B, the user will match to Group B.
Enable Change Password
Allow users to change their own AD password by entering their current password and a new one.
Note: Requires LDAP Agent with password change support
Enable Reset Password
Allow users to reset their AD password through a password reset flow.
Note: Requires LDAP Agent with password reset support and proper bind credentials configured.
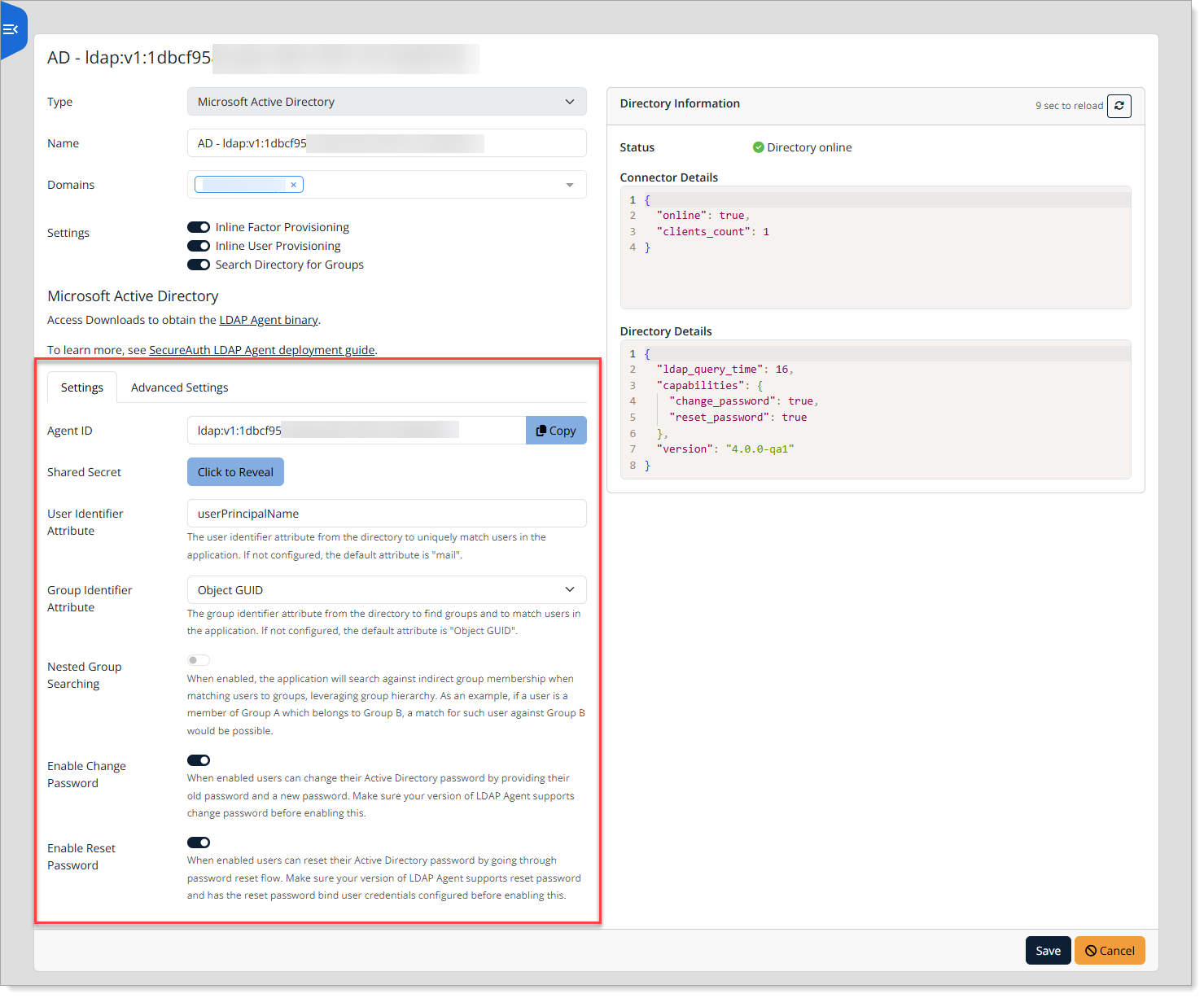
On the Advanced Settings tab, configure the following settings.
Agent heartbeat timeout
Set the interval (in seconds) between heartbeat requests to the LDAP Agent.
Default: 35 seconds
Agent Cache
Enable this to temporarily cache agent service responses. Helps maintain functionality during brief network interruptions.
Agent Cache Duration
Set how long cached responses remain valid.
Enter values in hours and minutes.
Default: 25 hours
Use case: Supports users who login daily, even during service disruptions.
Circuit breaker
Enable this to temporarily stop requests to a target service when repeated errors are detected. Prevents excessive retry attempts when the service is down.
Circuit breaker volume threshold – Minimum number of requests in a time window before the error rate is calculated.
Circuit breaker error threshold – Percentage of failed requests (out of the total volume threshold) that triggers the circuit to open.
Circuit breaker time window – Length of the time window (in seconds) used to evaluate error rates.
Circuit breaker sleep window – Duration (in seconds) the system waits before retrying requests after the circuit opens.
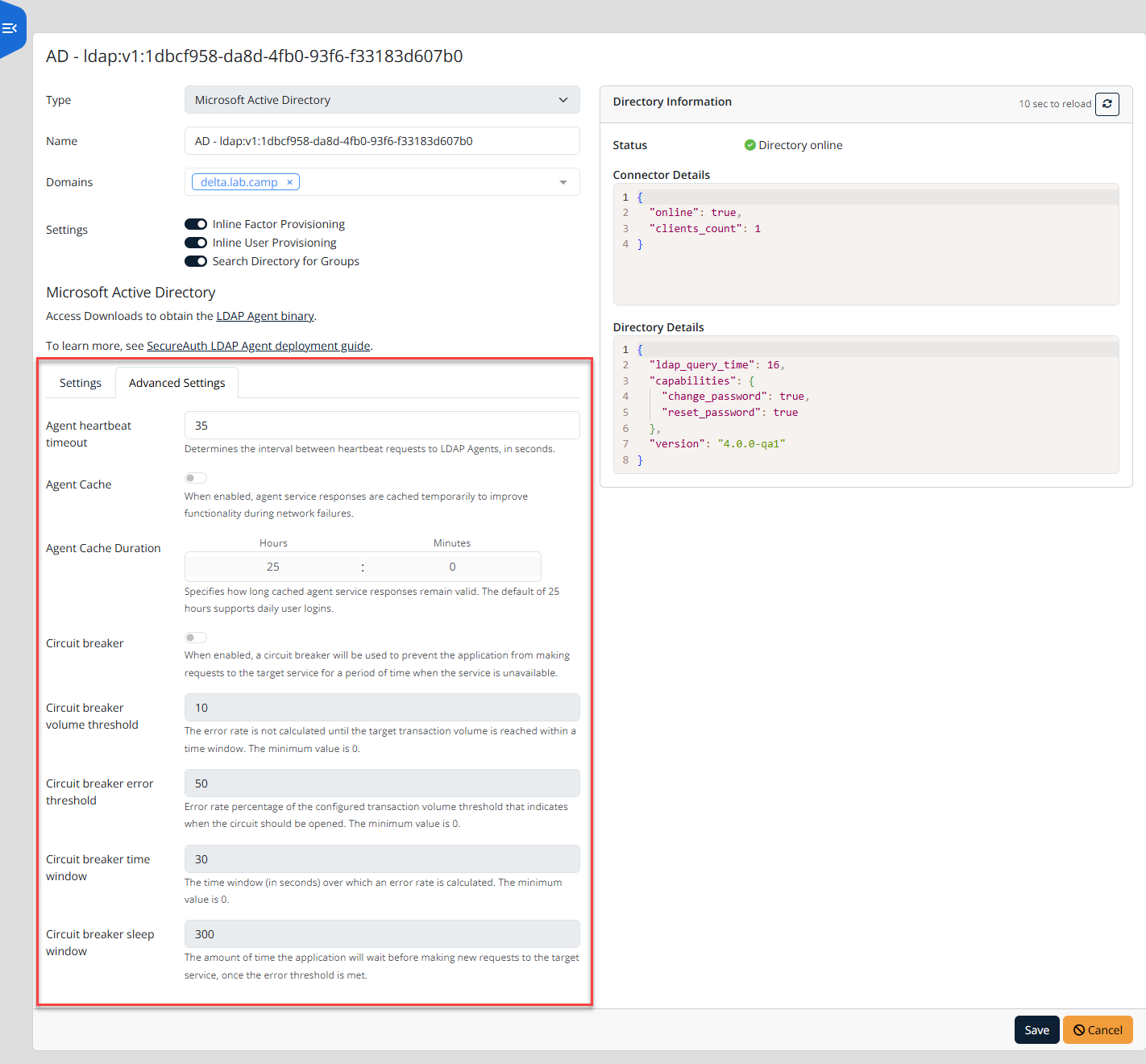
Save your changes.
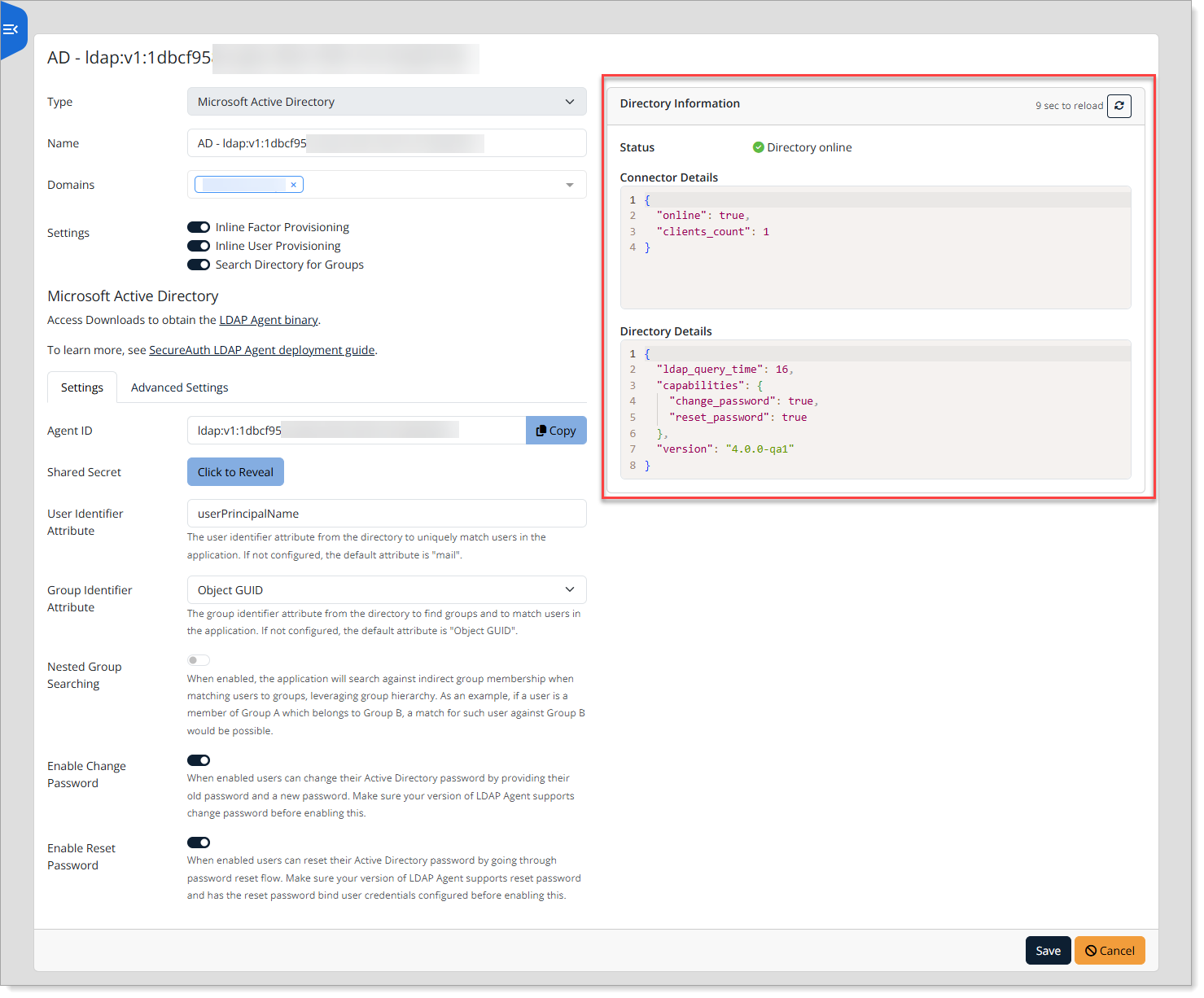
Verify connection and capabilities
After configuration, confirm the Directory Information panel shows the directory as online and check the Directory Details.
 |