FortiGate SSL VPN RADIUS integration
Multi-Factor Authentication (MFA) is an extra layer of security used when logging into websites or apps. Individuals are authenticated through more than one required security and validation procedure that only they know or have access to.
Remote Authentication Dial-In User Service (RADIUS) is a protocol commonly used to authenticate, authorize, and account for user access and actions.
Arculix by SecureAuth offers a simple solution for adding MFA to FortiGate SSL VPN via its RADIUS solution.
Prerequisites
Arculix RADIUS Agent that is configured and connected to your user directory. For example, Microsoft Active Directory (AD).
For more information, see the Arculix RADIUS Agent deployment guide.
FortiGate UTM user account with administrative access
Arculix RADIUS Agent configuration
To integrate Arculix with your FortiGate UTM, you will need to install an Arculix RADIUS Agent on a machine within your network. This server will receive RADIUS requests from your FortiGate UTM, check with the LDAP server to perform primary authentication, and then contact Arculix cloud service for secondary authentication.
Follow these steps to configure the Arculix RADIUS Agent.
Log in to the Arculix RADIUS Agent as an administrator.
Open the radius-agent-config.env file with an editor.
The file is located in the installed directory of RADIUS Agent. RADIUS clients are configured in this setting.
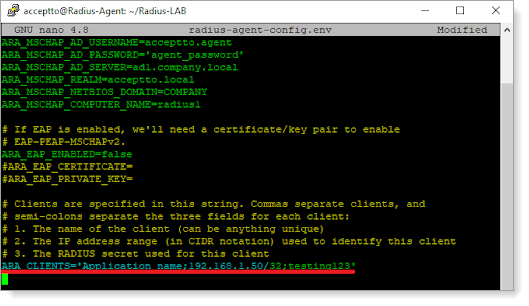
At the end of the radius-agent-config.env file, set the following configuration for the ARA_CLIENTS attribute:
Note
The values should be separated by semicolons (;).
ARA_CLIENTS = <An optional name for your FortiGate UTM>; <Internal IP address of your FortiGate UTM>; <a shared secret>
For example, set:
ARA_CLIENTS = FortiGate;192.168.1.50/32;testing12345
Save the file.
Run the following command to apply the changes:
docker-compose down && docker-compose up -d
FortiGate UTM configuration
In this section, you'll configure FortiGate as a service provider.
Log in to your FortiGate UTM as an administrator.
Go to User & Authentication > RADIUS Servers.
Click Create New, and enter your Arculux RADIUS Agent information following the image below:
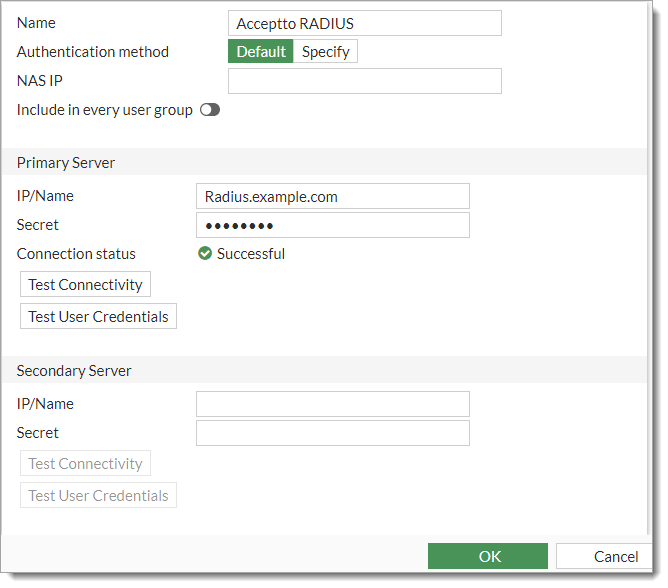
Click OK.
In the FortiGate console, change the authentication timeout to 60 seconds using the following commands:
config system global set remoteauthtimeout 60 endGo to User & Authentication > User Groups.
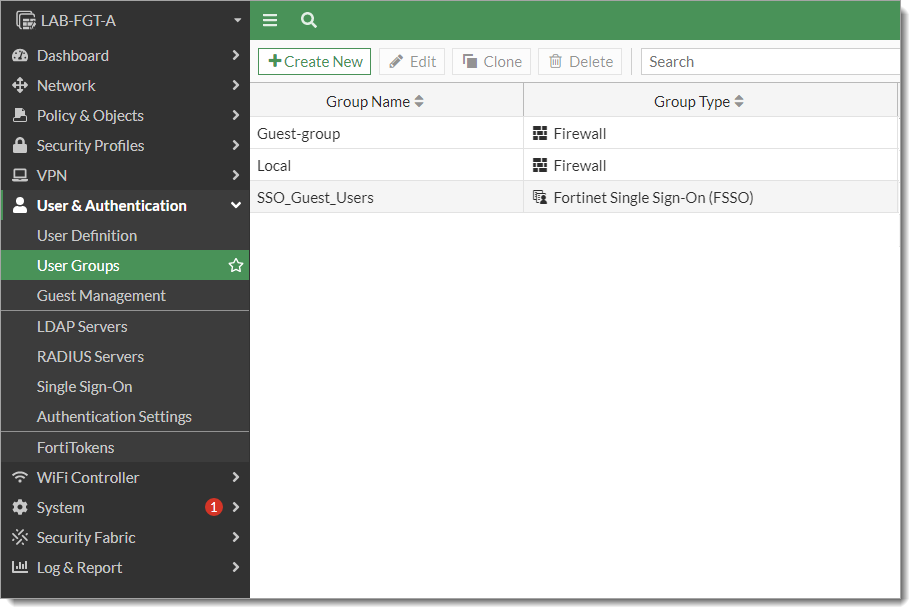
Click Create New and set the following configurations:
Name
Enter a unique name.
For example, Arculix MFA.
Type
Set to Firewall.
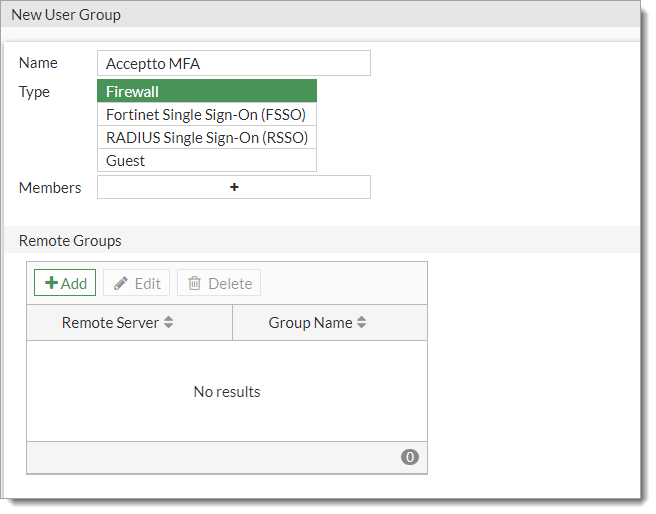
Click Add to define a new Group Match.
In the Add Group Match section, select Arculix RADIUS.
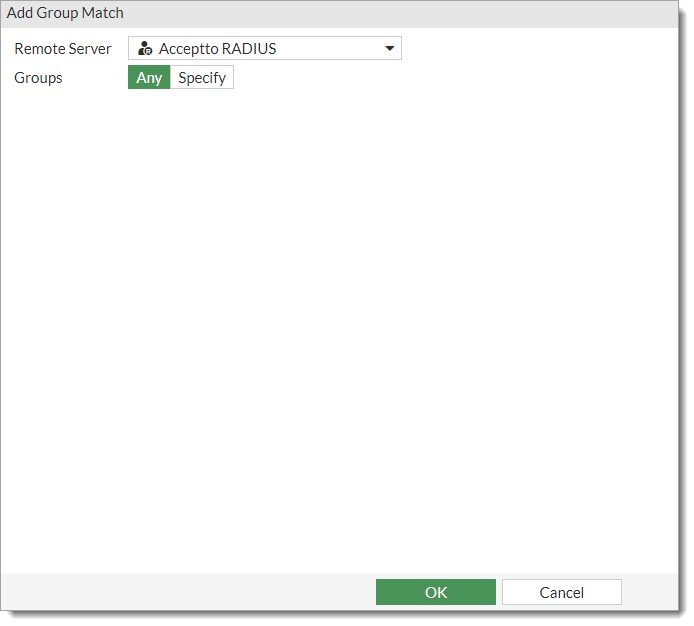
Click OK.
Go to Policy & Object > Firewall Policy and edit the policy related to your SSL-VPN.
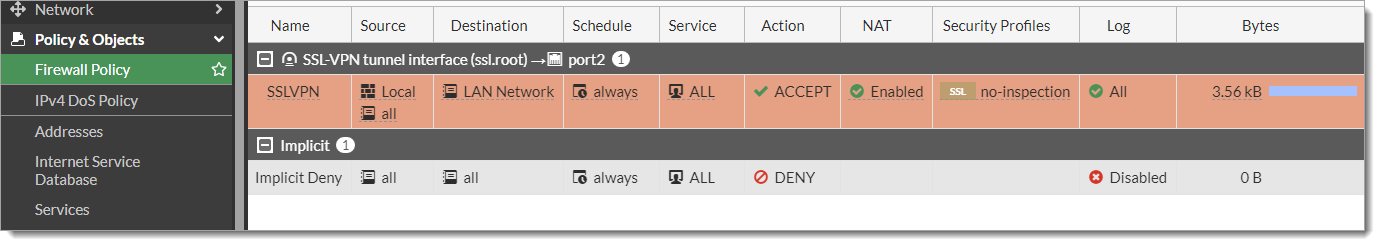
Edit the Source field and add the User Group created in Step 7.
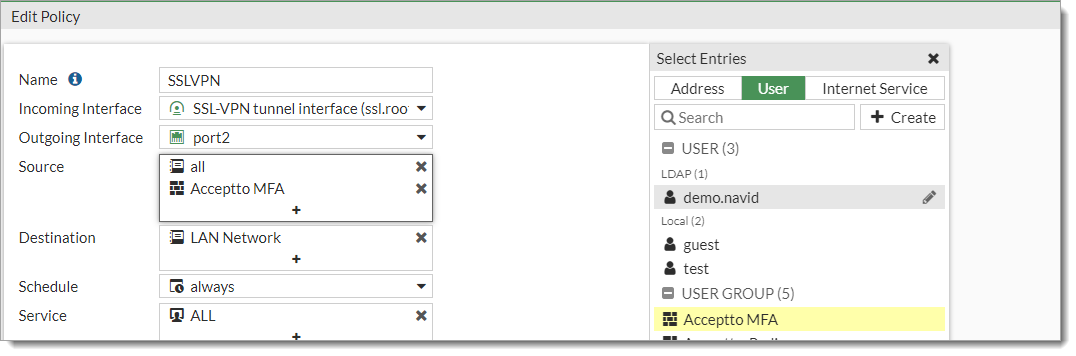
Click OK to save the configuration.
Go to VPN > SSL-VPN Settings.
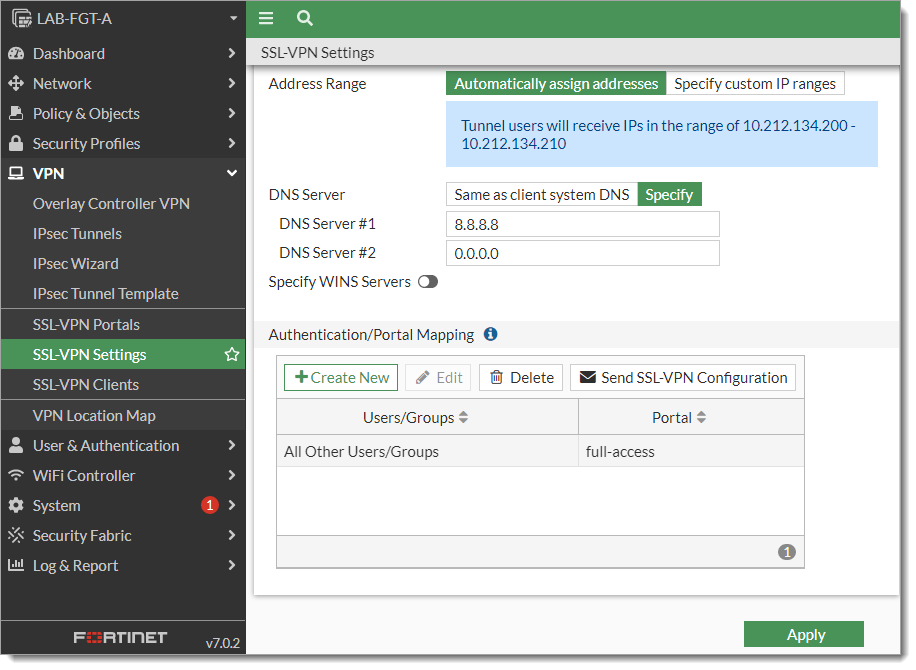
In the Authentication/Portal Mapping section, click Create New.
In the New Authentication/Portal Mapping section, set the following configurations:
User/Groups
Select the User Group created in Step 7
Portal
Select the type of portal you are going to provide.
The options are: full-access, tunnel access, or web access.
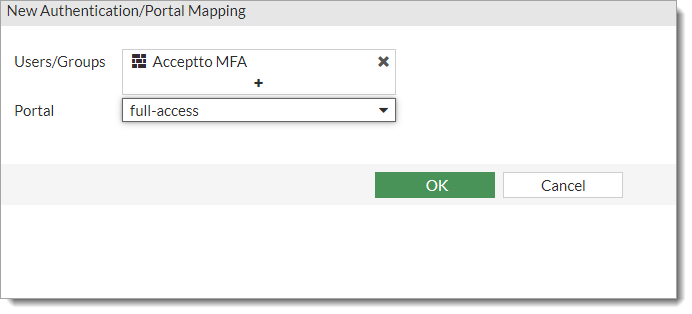
Click OK.
Click Apply to save the configuration.
Test your application integration
On the FortiClient VPN, create your SSL VPN connection and click Save.
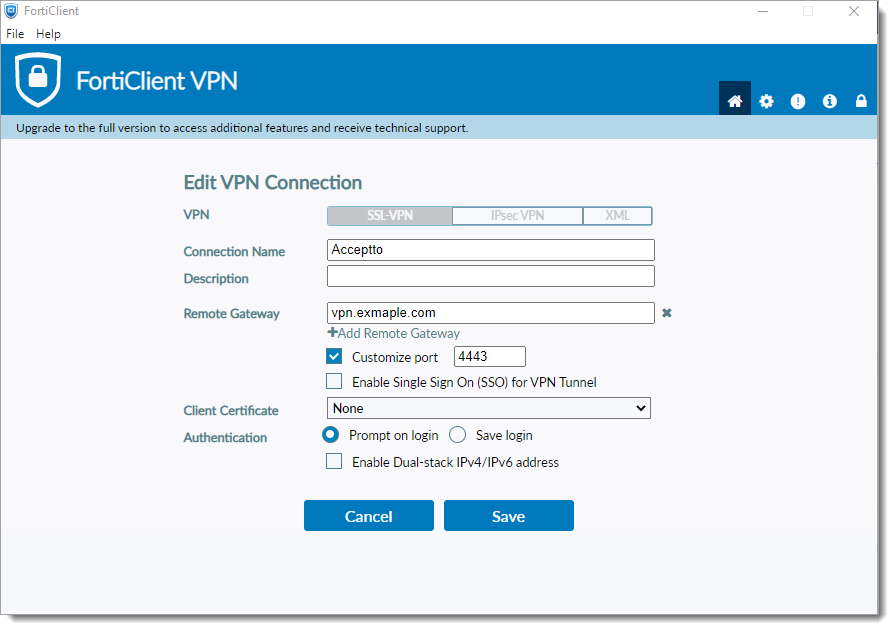
Enter your credentials and click Connect.
The Arculix Mobile app receives a push notification for your approval to log in.
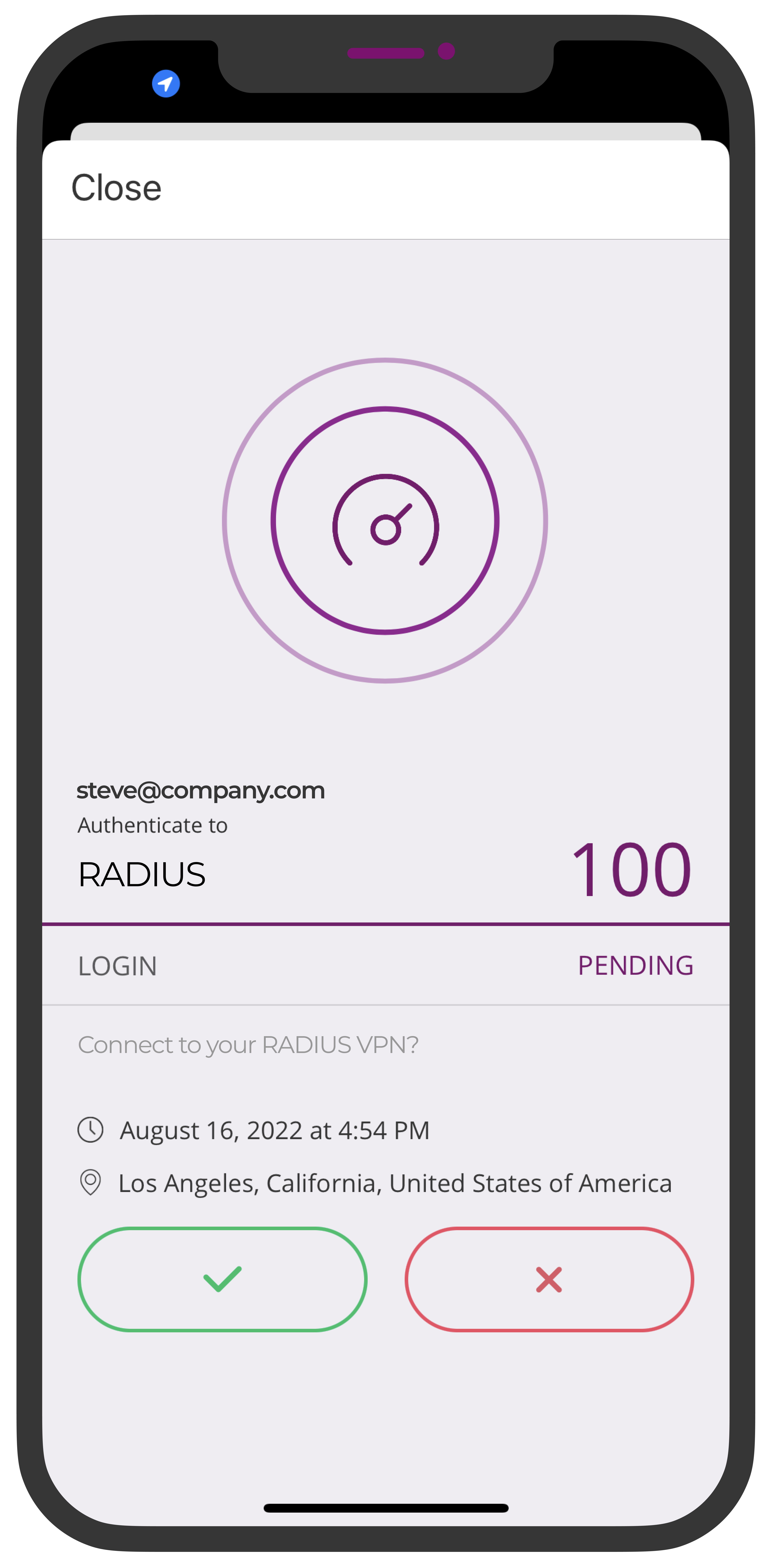
After approval, your connection will be established.
Support
If you have questions or need assistance, contact SecureAuth Support.
Sales
Want to learn more about our MFA solutions? Contact our Professional Services for a demo today.
Disclaimer
All product names, trademarks, and registered trademarks are the property of their respective owners.
All company, product, and service names used in this document are for identification purposes only. The use of these names, trademarks, and brands do not constitute an endorsement by the SecureAuth Corporation.