PingOne OIDC integration
Multi-Factor Authentication (MFA) is an extra layer of security used when logging into websites or apps. Individuals are authenticated through more than one required security and validation procedure that only they know or have access to.
OIDC (OpenID Connect) is an open standard protocol that provides a way to authenticate and authorize access to applications without giving the application your login credentials.
Arculix by SecureAuth, offers a simple method for adding single sign-on (SSO) MFA to PingOne through its OIDC solution.
Prerequisites
Configured Arculix instance and user account with administrative privileges for Arculix.
Configured Arculix LDAP Agent.
For more information, see the Arculix LDAP Agent deployment guide.
User account with administrative privileges for PingOne.
Task A: Start PingOne configuration
In this section, you will configure the PingOne application that supports OIDC.
Log in to PingOne with an administrator account.
From the left navigation, expand Connections and click External IDPs in the Identity Providers section.
Click Add Provider.
On the Add a Social or Custom Identity Provider page, click OPENID CONNECT.

On the Create Profile page, enter a unique Name and Description, and click Continue.
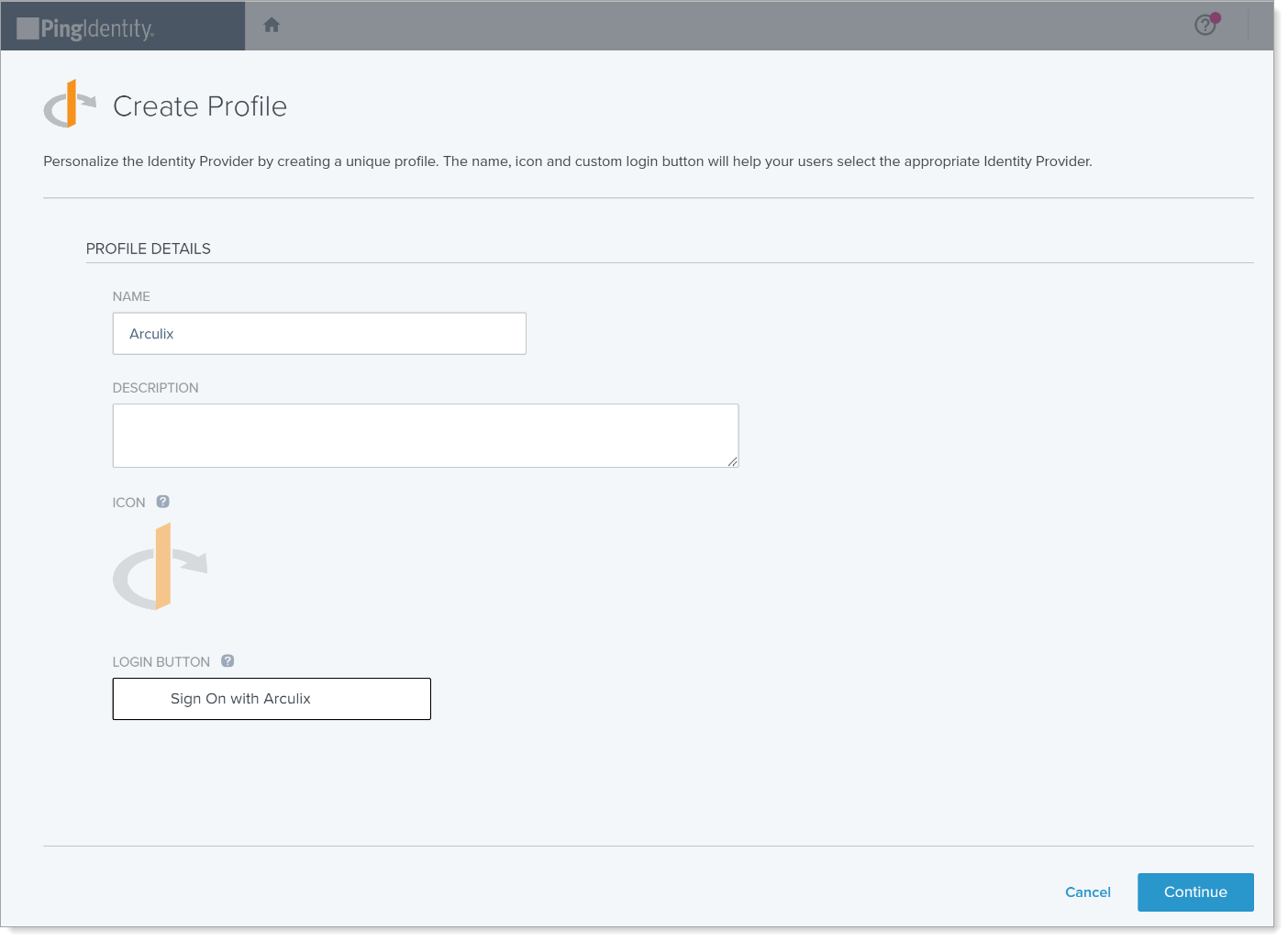
In the Connection Details section, copy the CALLBACK URL.
You will need this for the Arculix configuration when you open Arculix in another browser tab in Task B: Add OIDC application in Arculix
Task B: Add OIDC application in Arculix
In this section, you'll configure Arculix to act as an OIDC provider to authenticate the user and grant access to PingOne.
Log in to Arculix with an administrative account and go to Applications.
Click Create New Application.
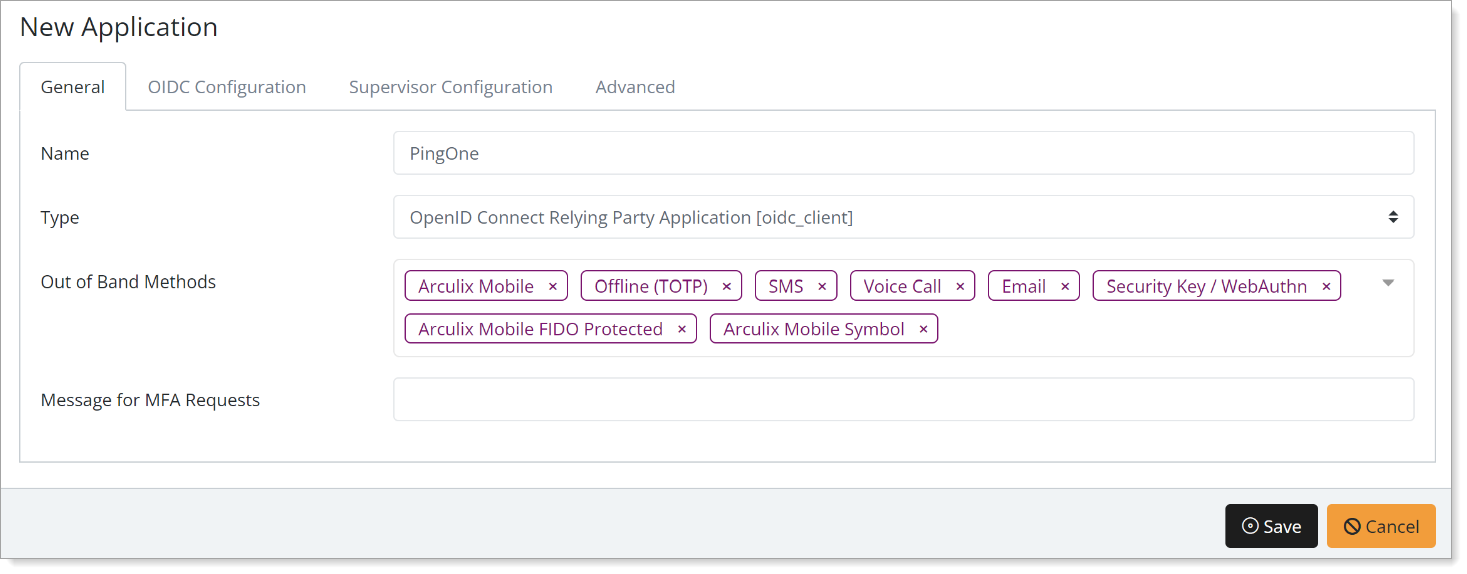
In the New Application form, on the General tab, set the following configurations:
Name
Set the name of the application. This is the name to display for push notifications, in the Admin panel, Application portal, and audit logs.
For example, PingOne.
Type
Set to OpenID Connect Relying Party Application [oidc_client].
Out of Band Methods
Select the allowed methods end users can choose to approve MFA requests.
For example, Arculix Mobile app (push notifications), SMS, or Security Key.
Message for MFA Requests
Optional. Type a message displayed to end users when sending an MFA request via push notification, SMS, or email.
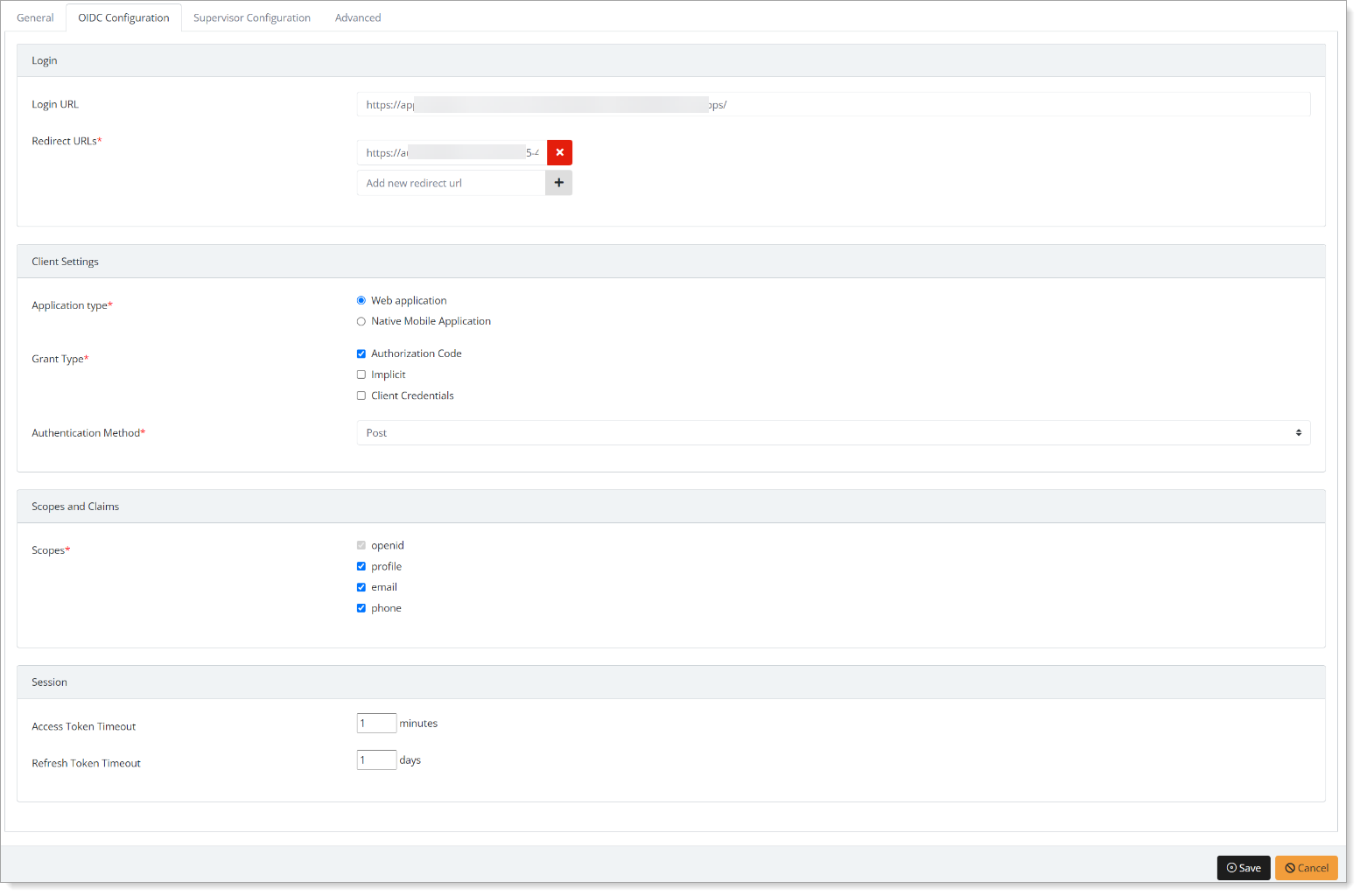
Select the OIDC Configuration tab, and set the following configurations:
Login
Login URL
(Optional) Enter the login home page URL for your PingOne application portal.
Redirect URLs
Paste the CALLBACK URL you copied earlier.
This is the redirect URL (Redirect_uri) that Arculix will use to send back the authorization code.
You can register more than one redirect URL (Redirect_uri).
Client Settings
Application Type
Set to Web application.
Grant Type
Set to Authorization code – User logs in to the application, then the application redirects the flow to Arculix for authentication. After authentication, Arculix returns an authorization code to the application, then exchanges the code for an access token and an identity token.
Authentication Method
Set to Post – Authenticates using the HTTP POST method, also known as the forms post response mode.
Scopes and Claims
Scopes
Select the following scopes:
profile – Allow access to user's profile information like postal address and phone number.
email – Allow access to user's email address.
phone – Allow access to user's phone number.
Session
Access Token Timeout
Set how long the access token is valid for before it times out. By default this set to 1 minute.
Refresh Token Timeout
Set how long the refresh token is valid for before it times out and requires the user to reauthenticate. By default this is set to 1 day.
Save your changes.
Edit the configured OIDC application and select the Advanced tab.
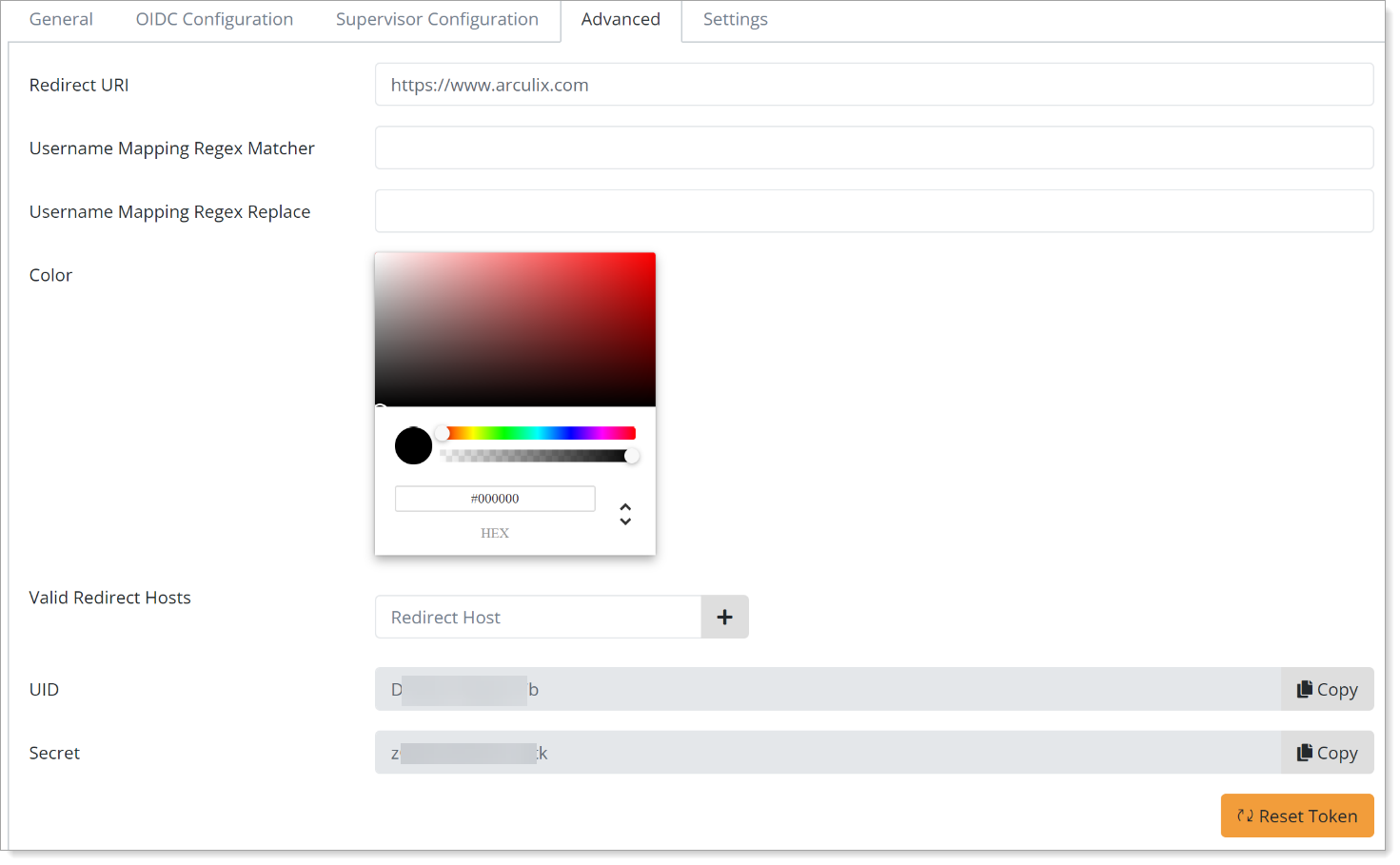
Copy the UID and Secret values.
You will need these to continue the PingOne configuration in Task C: Complete PingOne configuration.
Task C: Complete PingOne configuration
In this section, you will complete the PingOne configuration.
Switch back to the PingOne configuration page.
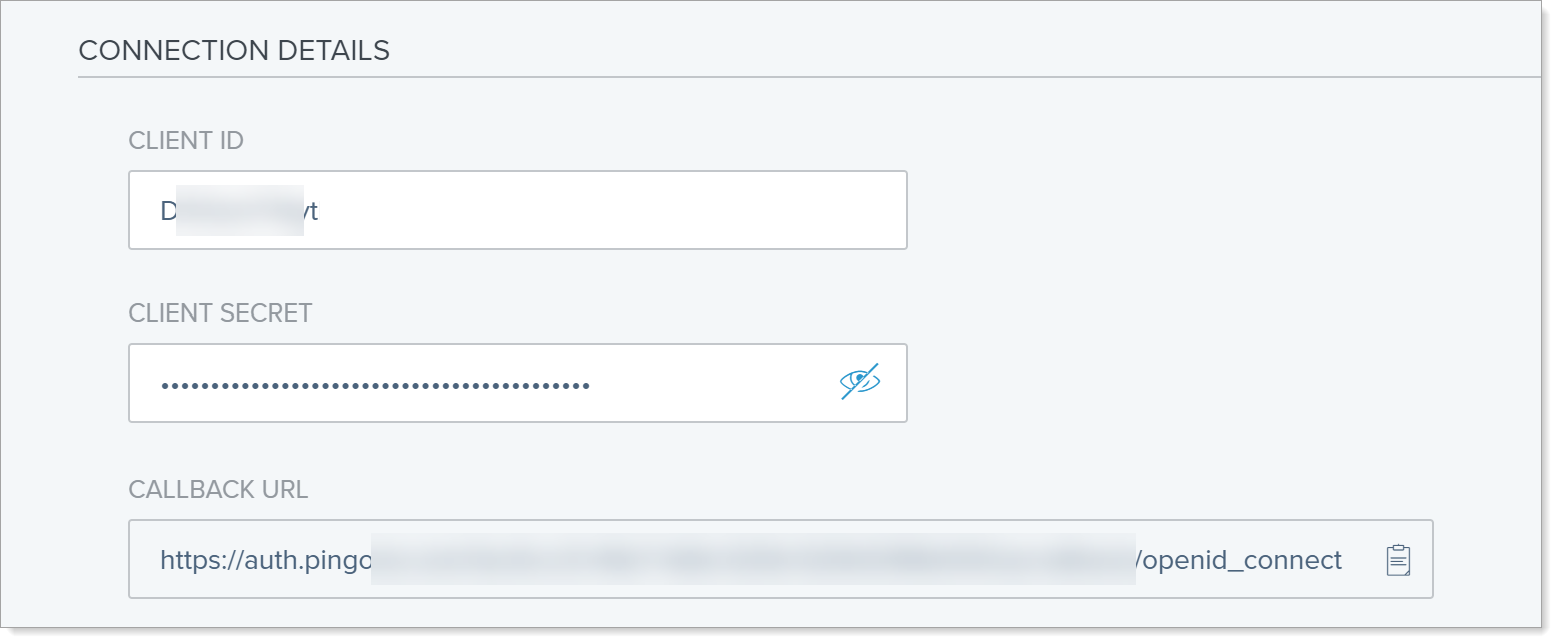
In the CONNECTION DETAILS section, set the following configurations:
Client ID
Paste the UID value copied from the PingOne OIDC application in Arculix.
Client Secret
Paste the Secret value copied from the PingOne OIDC application in Arculix.
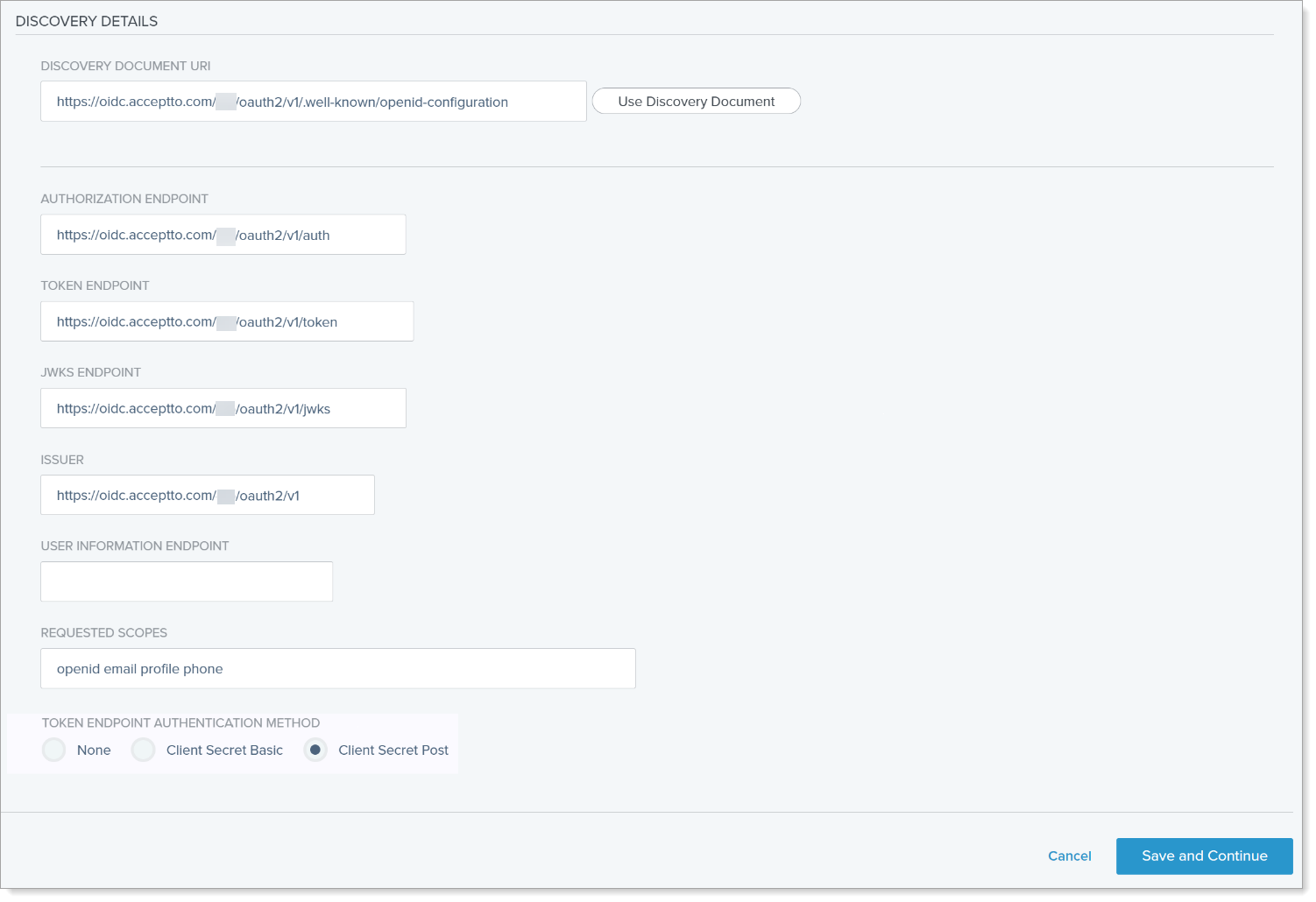
Scroll down to DISCOVERY DETAILS and set the following configurations:
Discovery Document URI
Enter the well-known endpoint URL in this format:
https://oidc.acceptto.com/<organization>/oauth2/v1/.well-known/openid-configurationClick Use Discovery Document.
Authorization Endpoint
Enter the authorization endpoint URL in this format:
https://oidc.acceptto.com/<organization>/oauth2/v1/authToken Endpoint
Enter the token endpoint URL in this format:
https://oidc.acceptto.com/<organization>/oauth2/v1/tokenJWKS Endpoint
Enter any required JSON Web Key Set (JWKS) endpoints in the format:
https://oidc.acceptto.com/<organization>/oauth2/v1/jwksThis endpoint will contain the JWK used to verify all Auth0-issued JWTs for this tenant.
Issuer
Enter the URL identifying the issuer of this endpoint in the format:
https://oidc.acceptto.com/<organization>/oauth2/v1User Information Endpoint
Remove any value that appears in this field.
Requested Scopes
Define the requested scopes in the PingOne application; this is similar to the scopes you selected in the Arculix OIDC application.
For example, set to
openid email profile phoneToken Endpoint Authentication Method
Set to Client Secret Post.
In the Map Attributes section, click Add Attribute and set the following configurations:
PingOne User Profile Attribute
Set to Email Address.
OIDC Attribute
Set to providerAttributes.email.
Click Save and Finish.
From the left navigation, go back to Connections > External IDPs.
Move the slider to enable Arculix as the newly added Provider and then click the pencil icon to make edits.
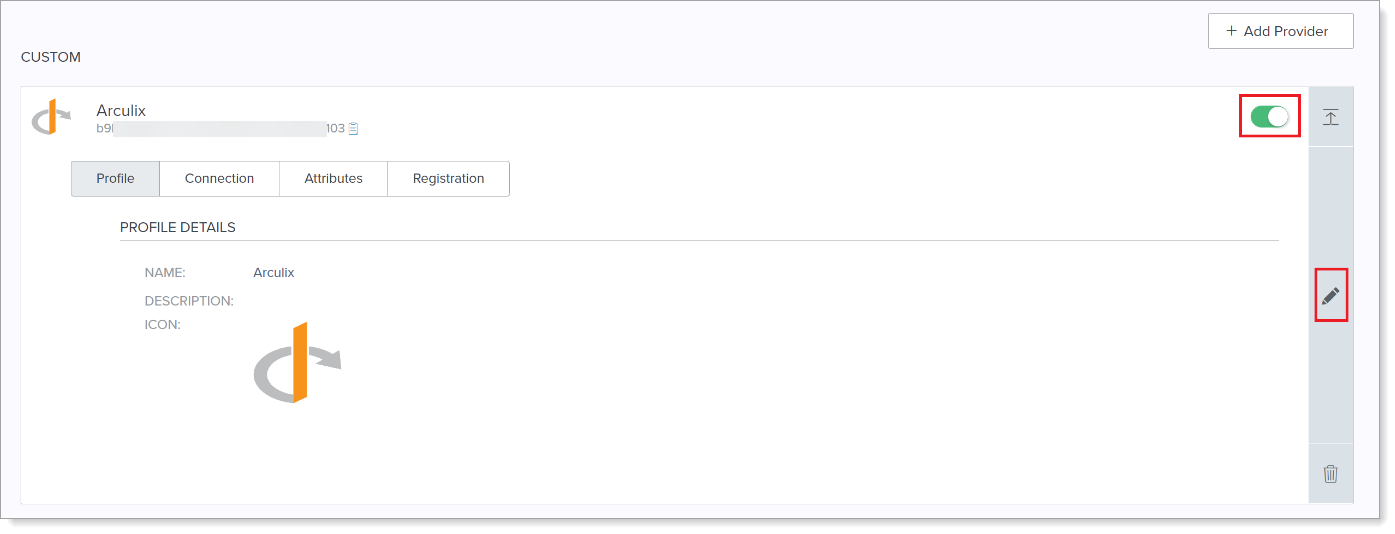
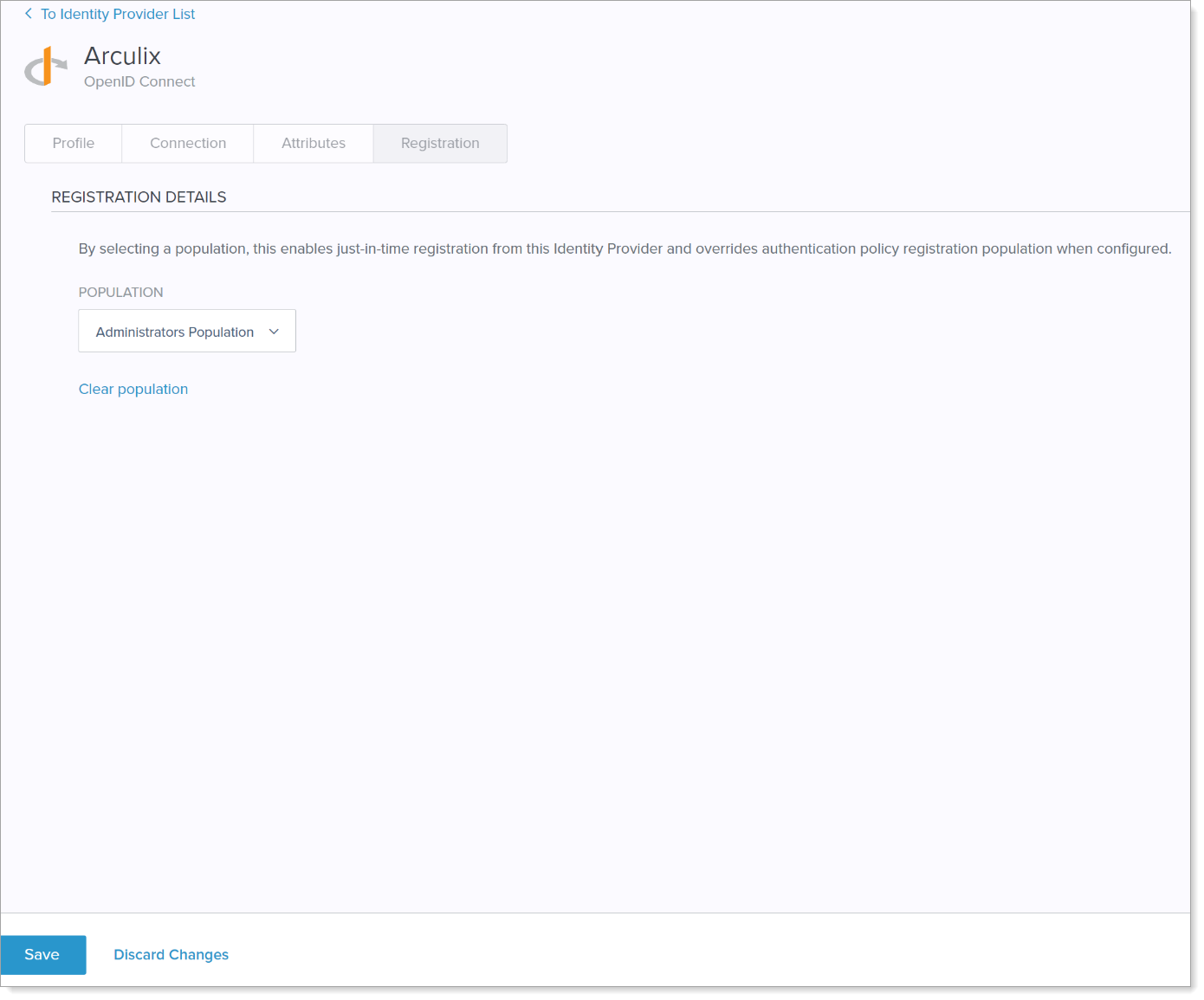
Select the Registration tab.
Scroll down to the Registration Details section and from the Population list, select the population group. Save your changes.
In the left navigation, select Experiences > Authentication.
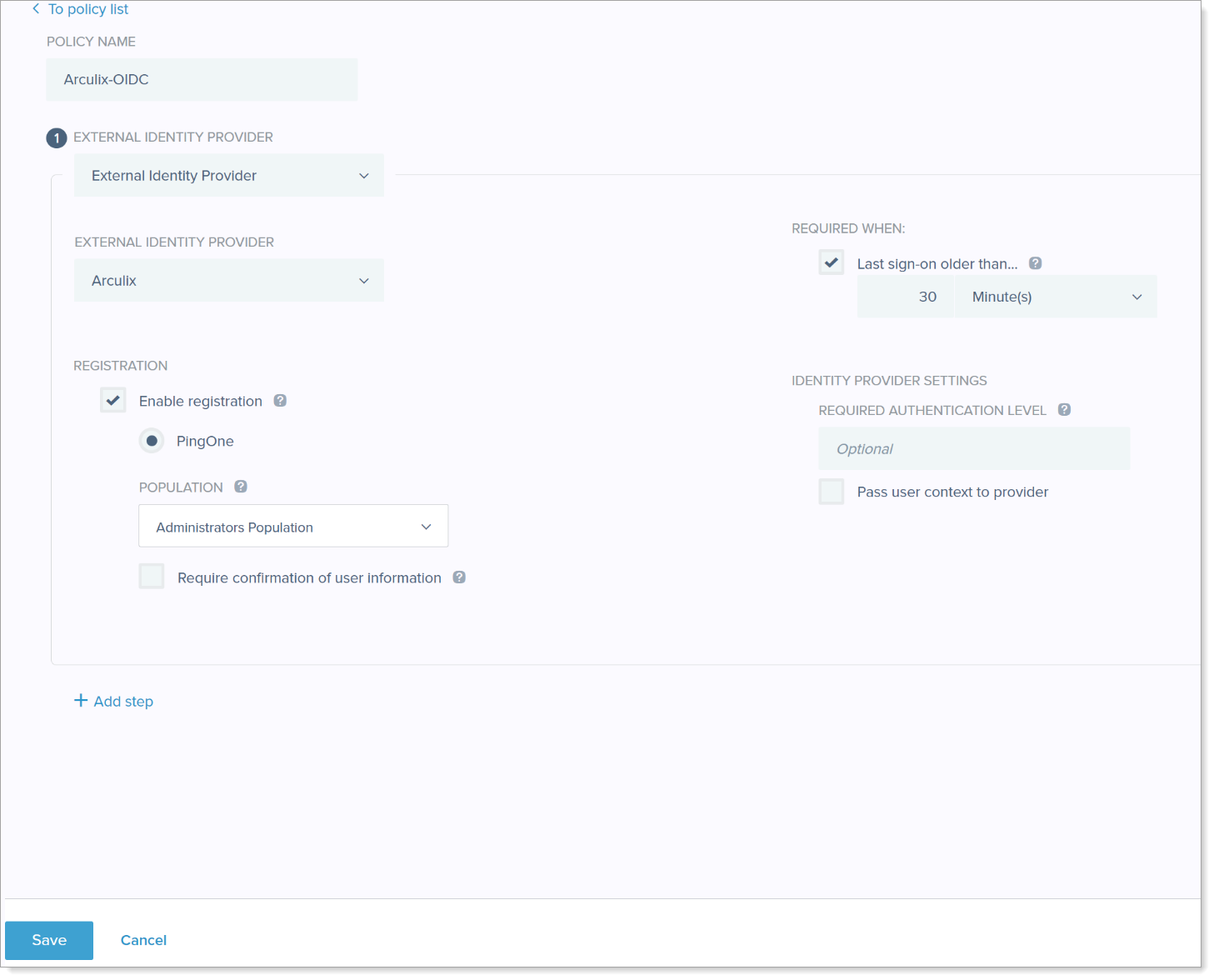
In the Authentication Policies section, click Add Policy.
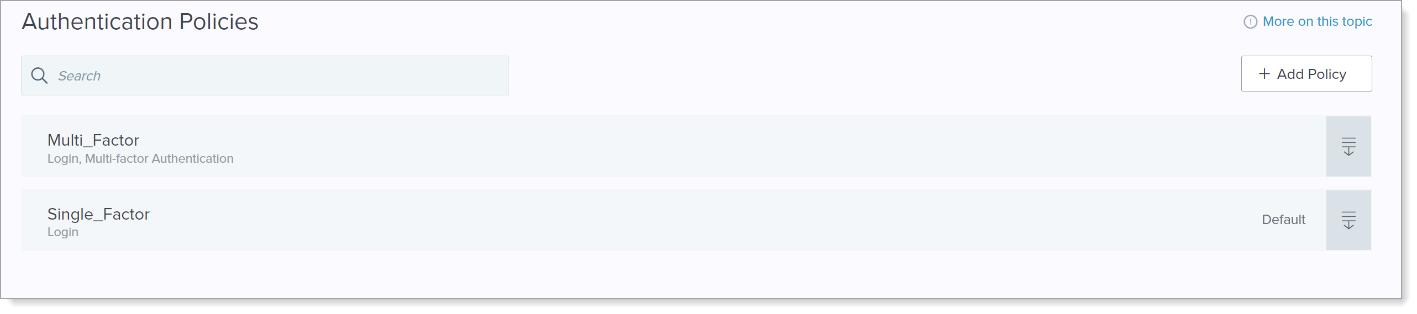
Set the following configurations.
Set a name for the policy.
In the step type list, select External Identity Provider.
In the next list, select Arculix.
Select the Enable registration check box.
Select the population to which the policy applies.
Save your changes.
In the left navigation, select Connections > Applications.
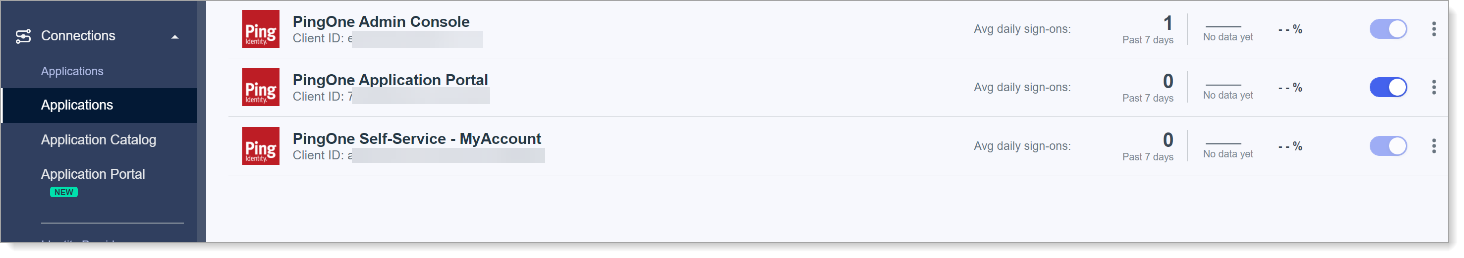
Configure the policies for the application in the following steps for each application as needed.
Note
Make sure to add the home page URL of each application to the Redirect URL field in the Arculix OIDC application.
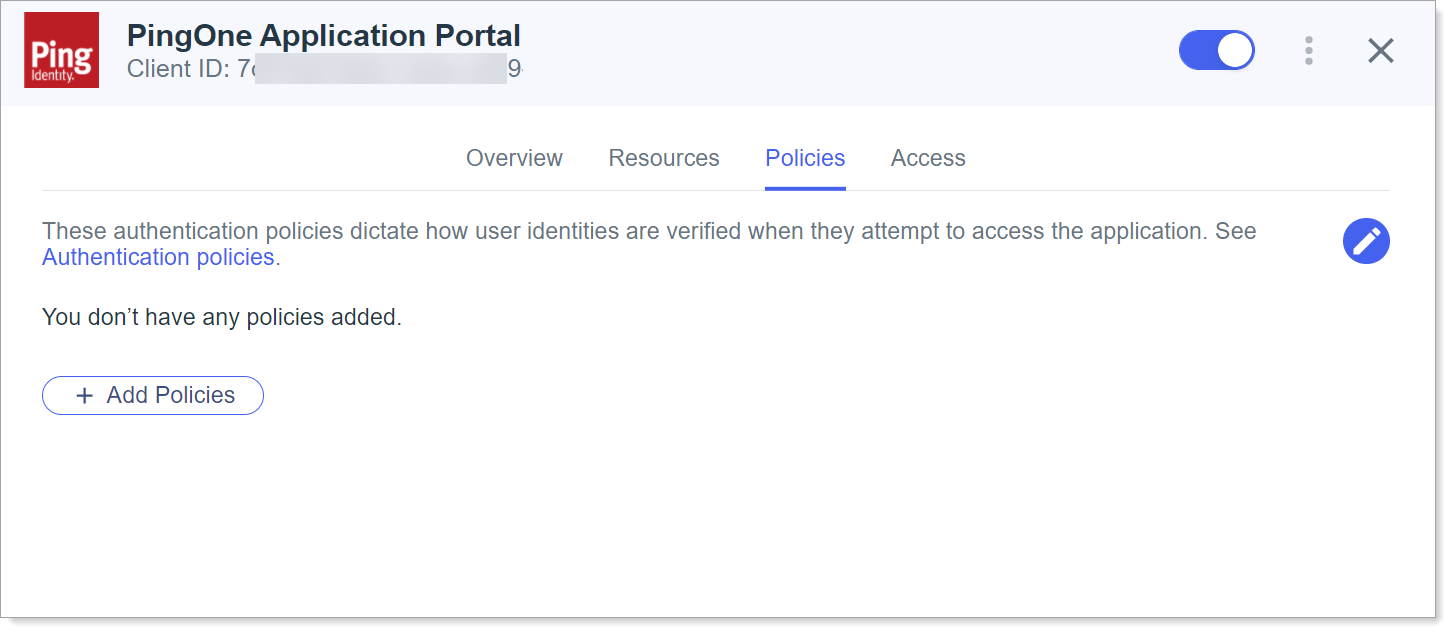
On the PingOne Application Portal page, select the Policies tab then click Add Policies.
Select the check box for the newly created policy and click Add.
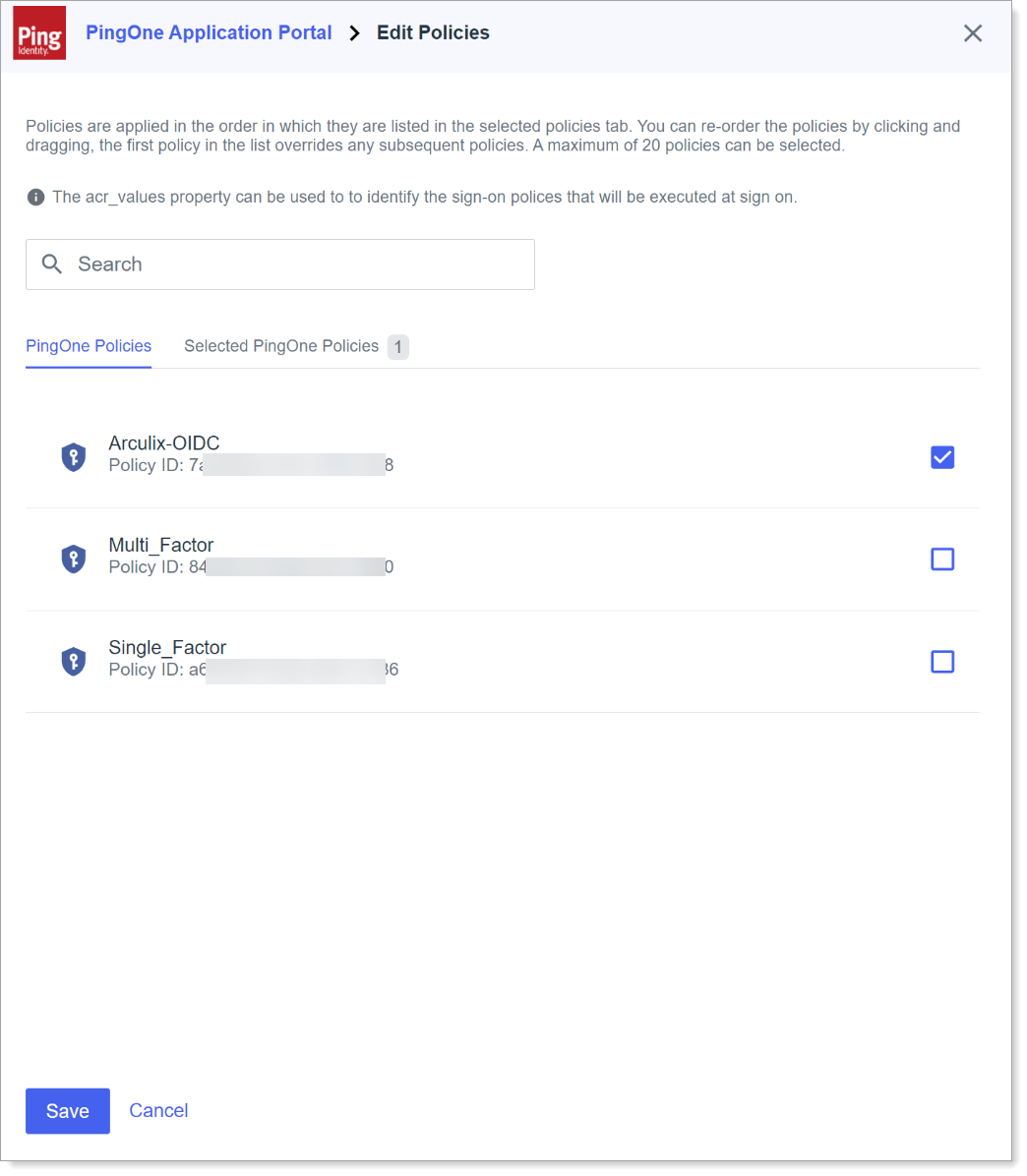
Save your changes.
Repeat step Step 14 as needed for each application.
Test your OIDC application integration
Go to the PingOne Application Portal and log in.
You will be redirected to the Arculix SSO page.

After successful authentication, select your preferred MFA method to approve access to the PingOne application.
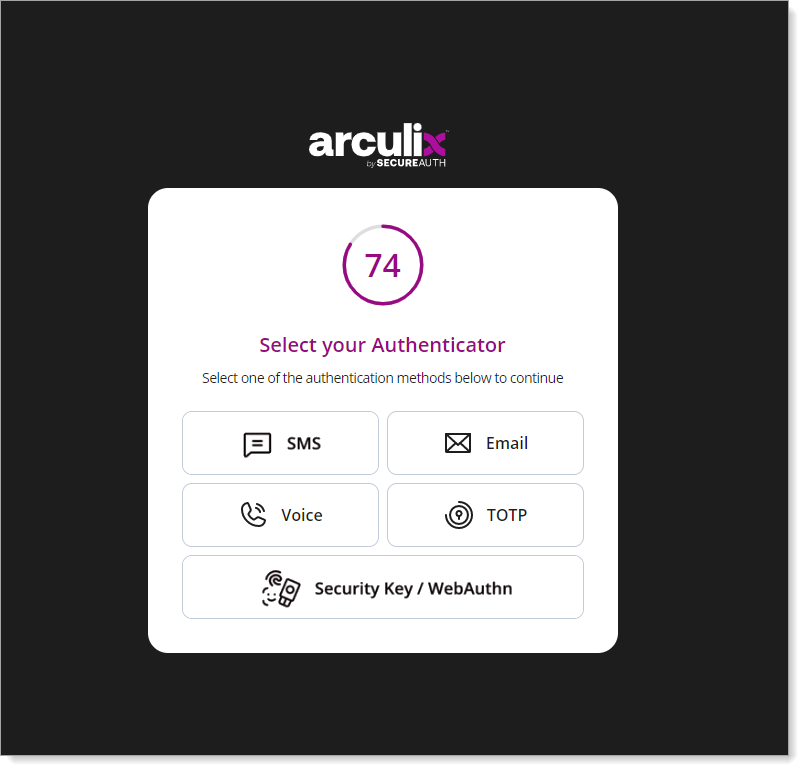
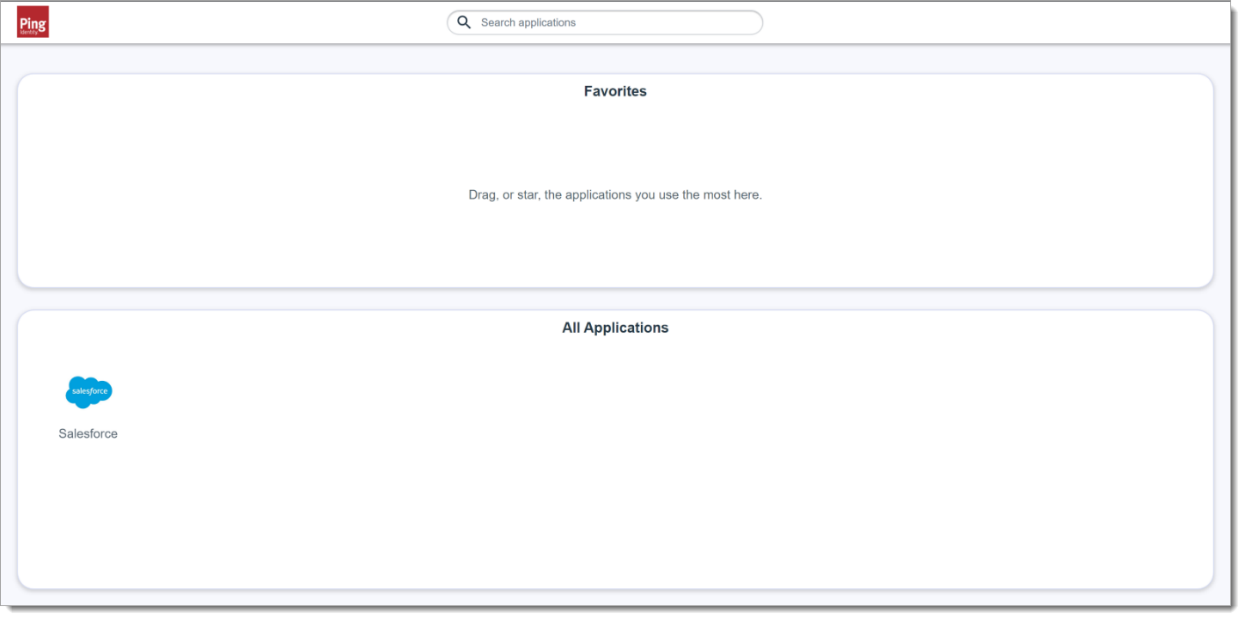
Finally, you'll be redirected to the PingOne application home page.
Support
If you have questions or need assistance, contact SecureAuth Support.
Sales
Want to learn more about our MFA solutions? Contact our Professional Services for a demo today.
Disclaimer
All product names, trademarks, and registered trademarks are the property of their respective owners.
All company, product, and service names used in this document are for identification purposes only. The use of these names, trademarks, and brands do not constitute an endorsement by the SecureAuth Corporation.