Using Arculix Device Trust - MFA methods
This section provides an overview of the available MFA methods, which include push, SMS, email, phone biometric and workstation biometric.
Push
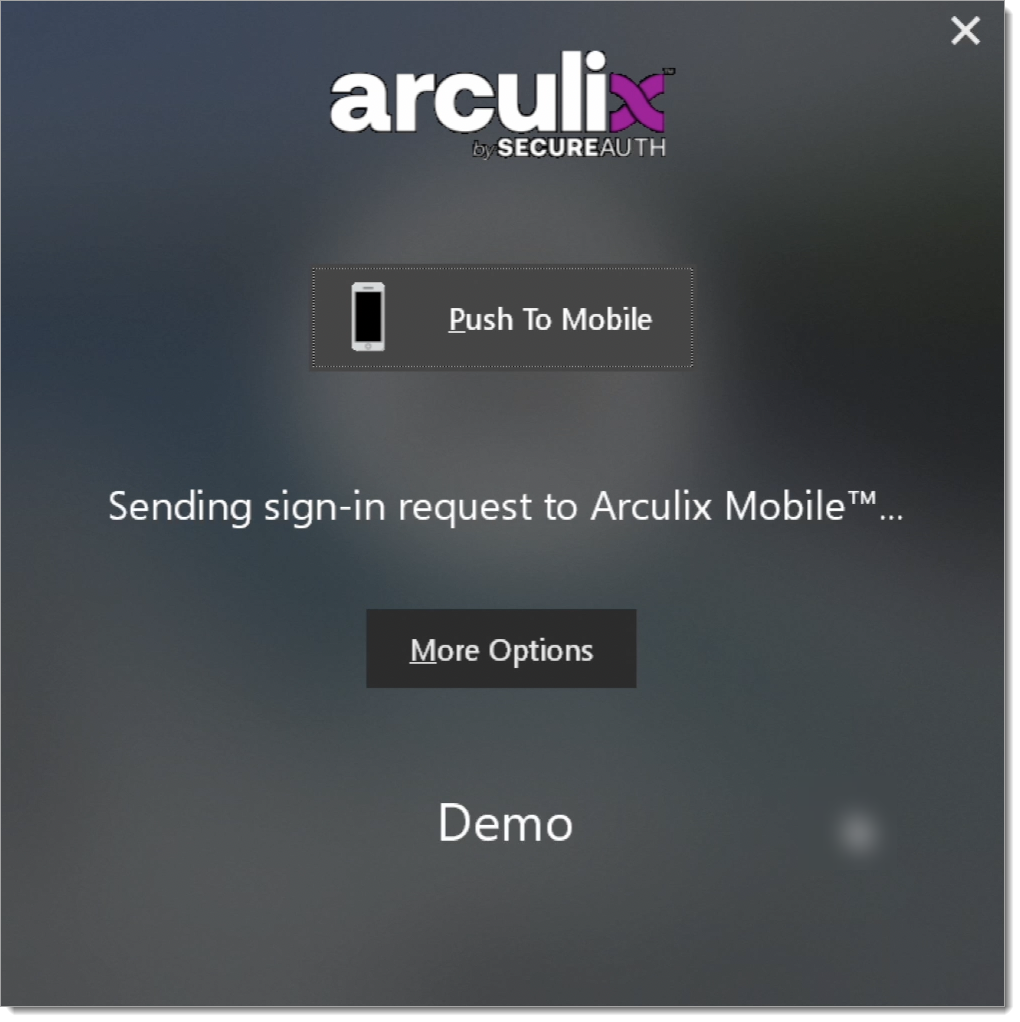
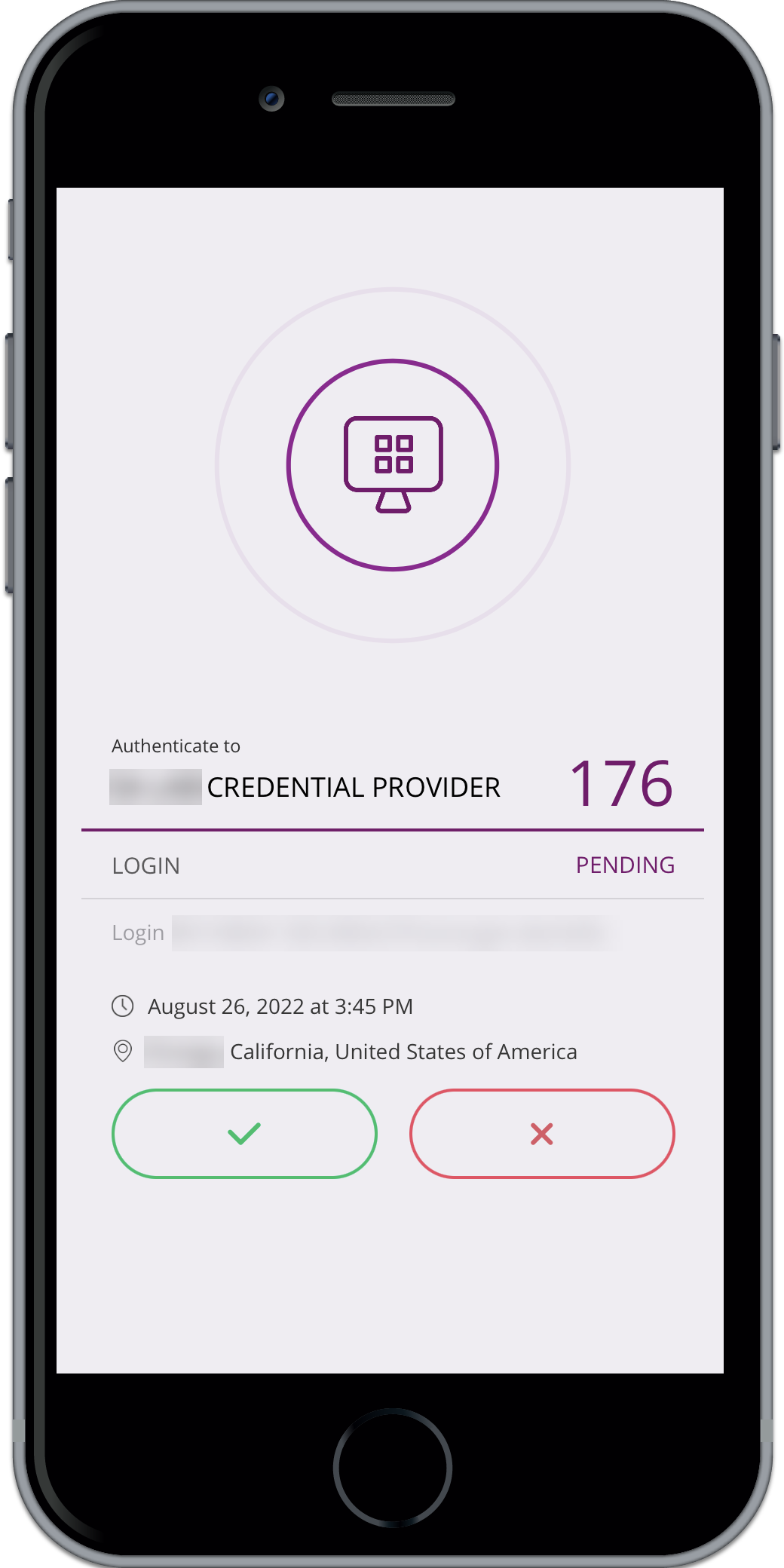
Push notification using the Arculix Mobile app is the default MFA method for all logins. Each workstation login automatically sends a push to the user’s registered Arculix Mobile app. Tap Accept to log in, and Deny to block the login.
 |
 |
Email and SMS
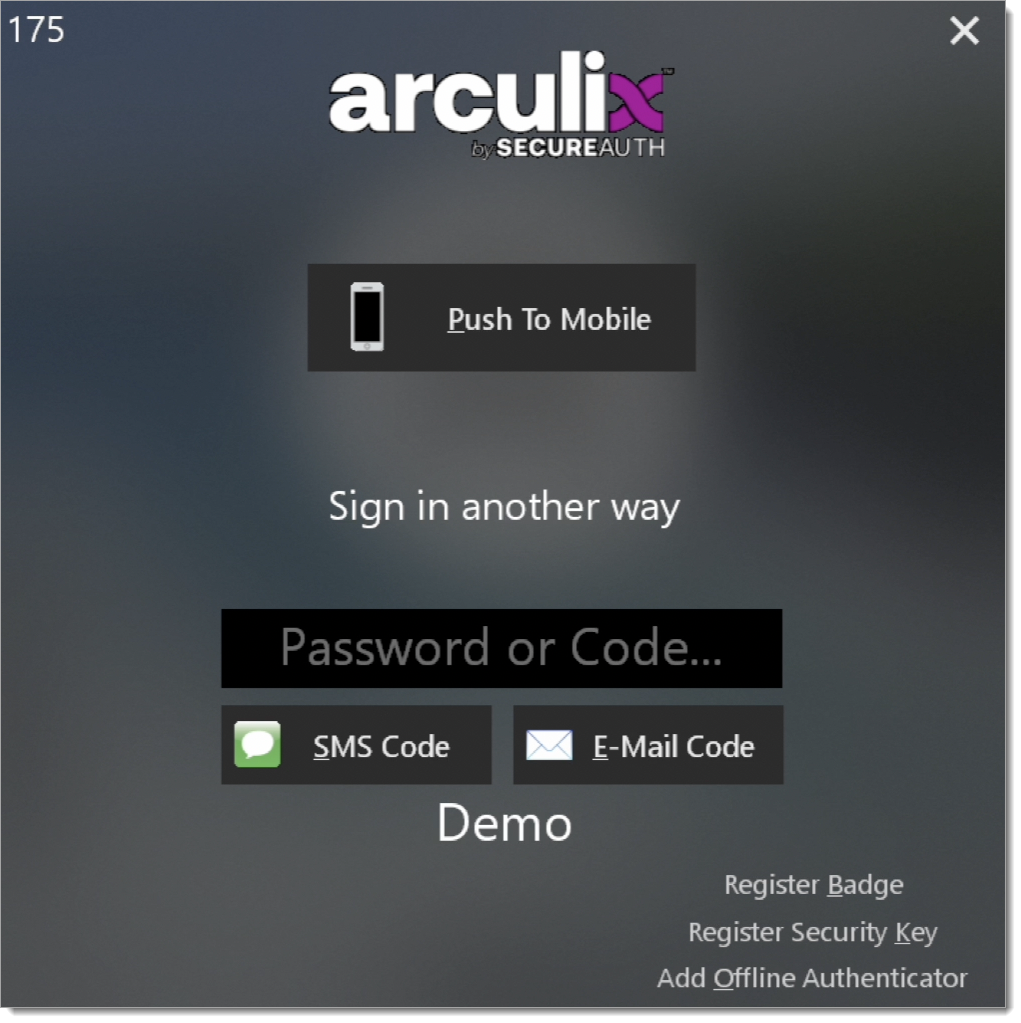
If an authentication method other than push is needed or desired, clicking More Options after entering the username and password present additional MFA options. A one-time passcode can be sent via SMS or email by clicking the corresponding button in the dialogue box (note that the phone number must be registered on the user’s account to receive SMS). Enter the provided 6-digit authentication code in the Offline code entry field.
 |
TOTP
When registering a Windows or macOS workstation with Arculix, a time-based one-time temporary passcode (TOTP) is created that enables access when the system doesn’t have an internet connection (e.g. on an airplane or outside an internet service area).
The TOTP changes every 30 seconds and is accessible from two locations within Arculix Mobile app:
Offline authenticators
Workstation
To gain access to the workstation, enter code in the Offline Code field before the number expires (a countdown clock is provided right above the code in Arculix Mobile.
To add the ability to use a TOTP from a second device, click Add Offline Authenticator. Then, you will receive a push notification in Arculix Mobile app on your device to approve the reset. After approving, you will see a QR code. Scan this QR code using your second device in order to add the new TOTP to your list of Offline Authenticators. Be sure to click OK in order to complete the reset.
Security keys
To log in with a security key, you must first register your security key using the bottom-right Register Security Key. This will send you a push that you must accept through the Arculix Mobile app. Once you register by accepting this push, you can use the security key by tapping once you enter the login screen.
Biometric - Windows Hello
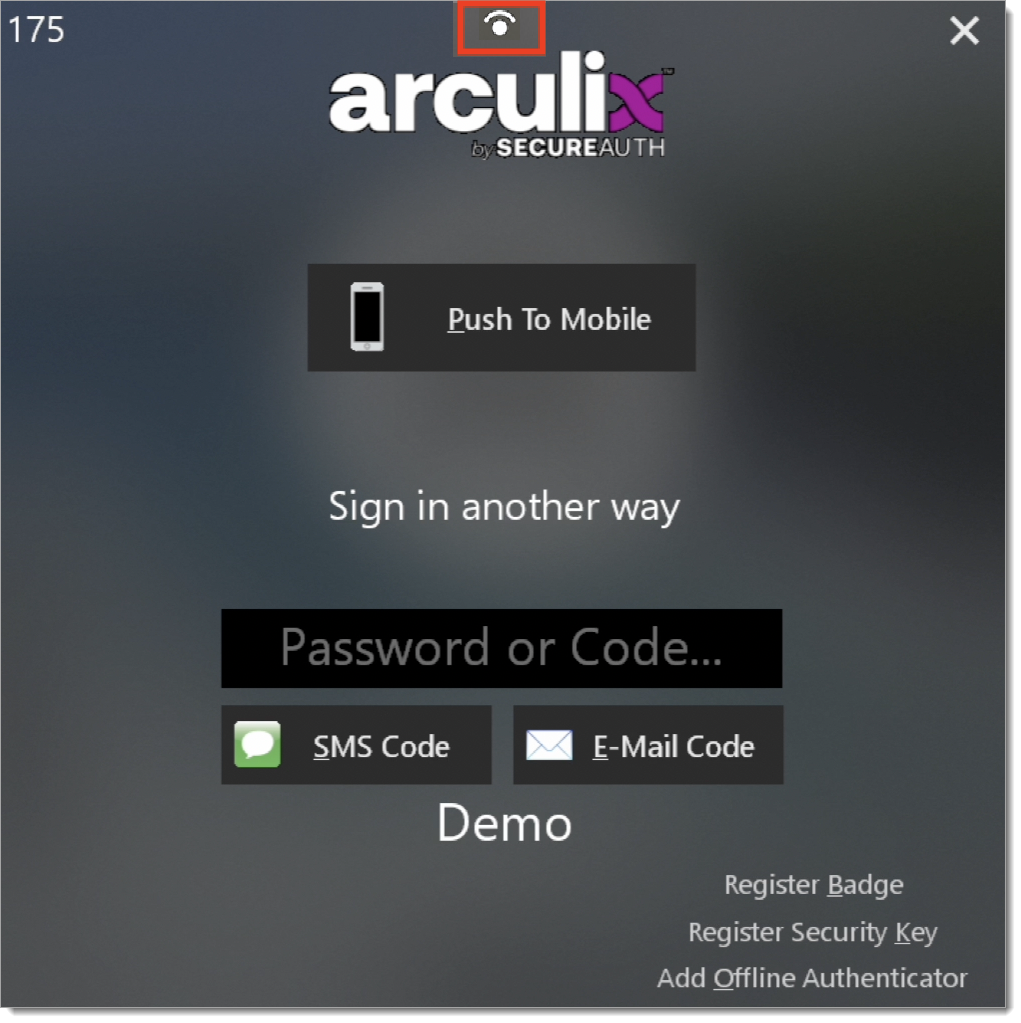
The biometric login for Windows Hello is evident by the icon on the top of the Arculix login screen. This option is available once your face or fingerprint has been registered with the system through Windows settings.
 |
Two-way SMS
Two-way SMS can be used by selecting More options from the Arculix login screen and then selecting SMS code. You will receive a code, which you can then reply back with in the chat.
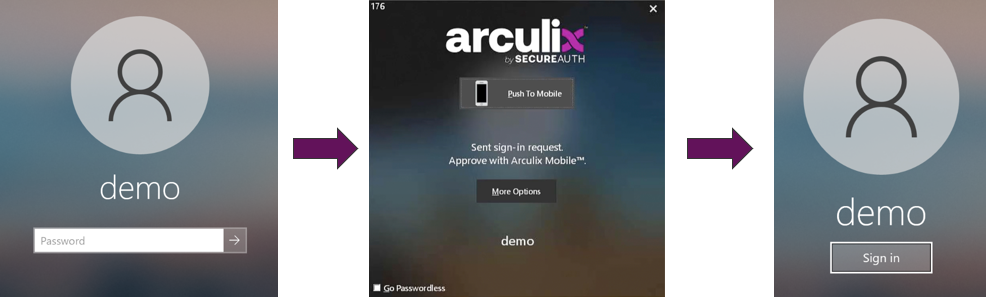
Enabling passwordless
End users can use passwordless authentication by selecting the Go Passwordless check box during login to their workstation. On the next login, they will see a Sign in button to receive an automatic push notification without entering a password.
Note: As an administrator, you can show or hide the Go Passwordless check box in the Arculix Core configuation settings.
 |
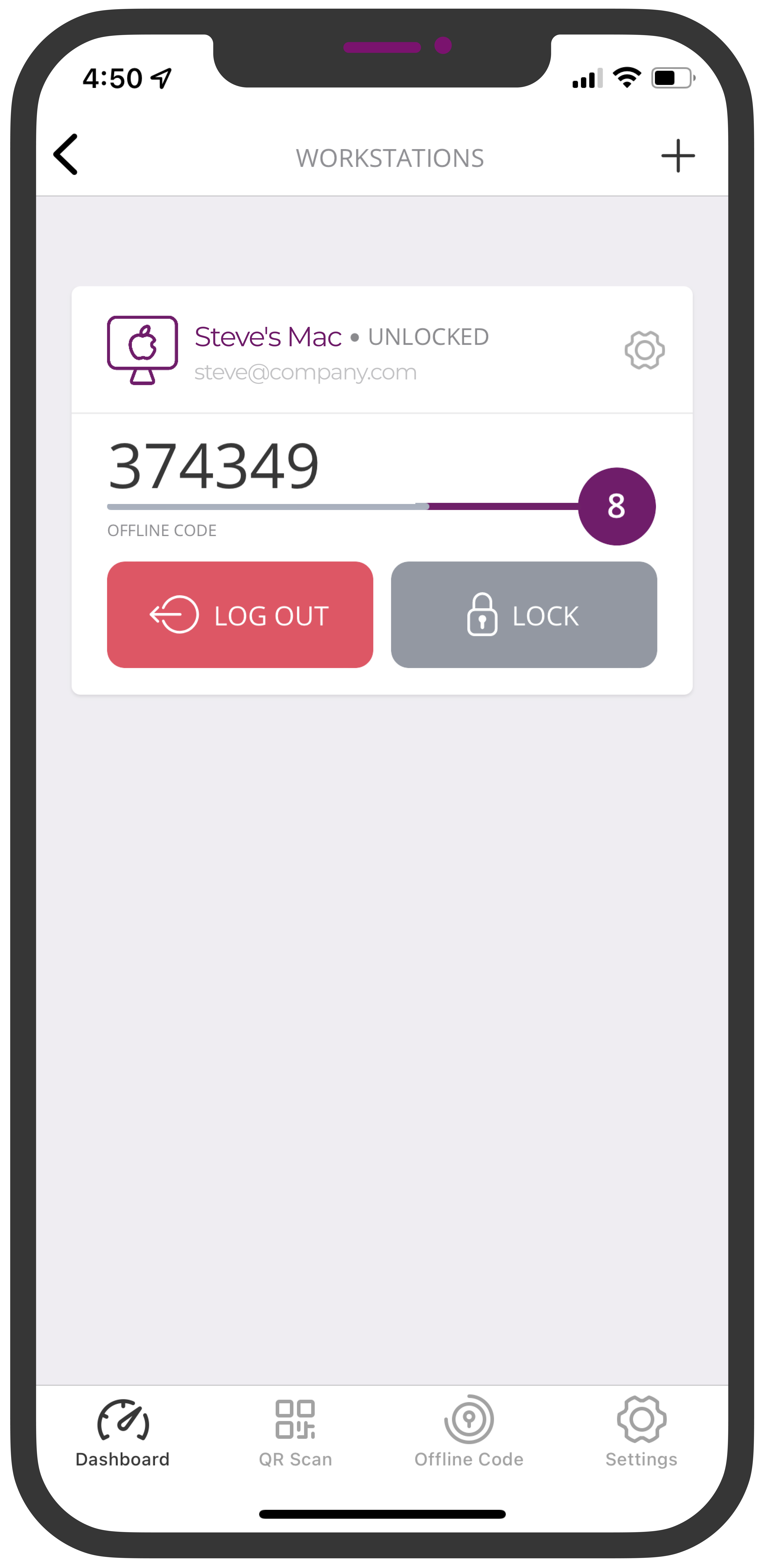
Remote workstation lock and logout
Arculix Mobile has the ability for users to lock and log out of protected workstations remotely.
While logged into the workstation, open the Arculix Mobile app and click Workstations in the upper right left corner of the Dashboard screen to open the Workstations page.
Clicking Lock locks the current session, requiring re-authentication to gain access. Clicking Logout logs the user out of your active session.
Clicking Logout logs the user out of your active session.
Allow TouchID on macOS lock screen
In order to login using TouchID when Arculix Device Trust is installed on a macOS workstation, the setting MFALockEnabled must be set to false. This setting is false by default for macOS devices that have biometric and true for those that do not. When false, the setting allows you to login with TouchID or Password at the lock screen and if the network connection drops then the setting forces the user to a lock screen which requires MFA.
To change the setting run the following commands:
sudo atagent stopsudo atagent set mfalockenabled true/falsesudo atagent installLog off the workstation
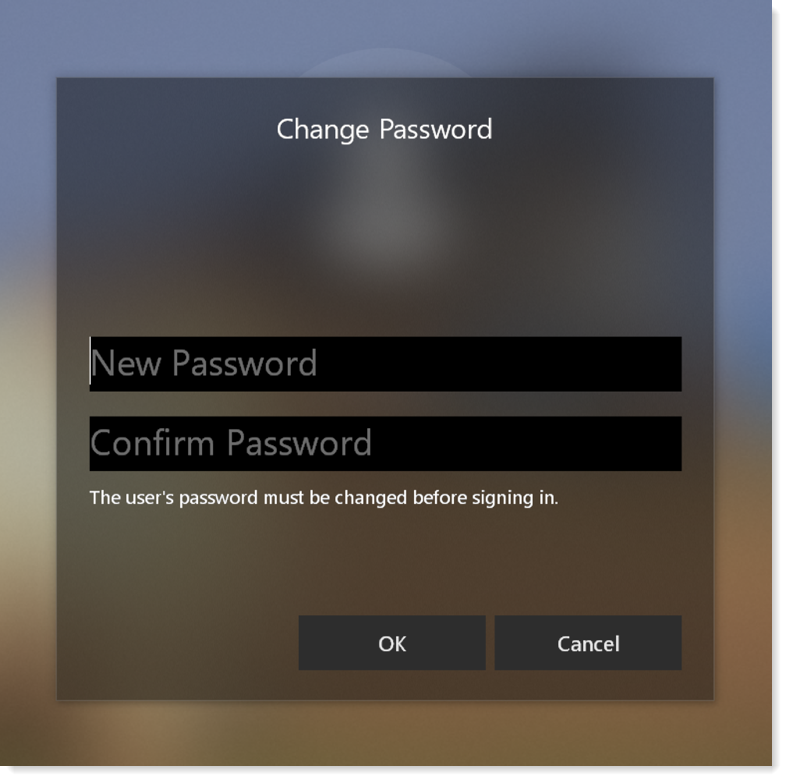
Force password change
As an administrator, you might have a setting in the Active Directory to force end users to change their password on the next login to their workstation. Device Trust will send a prompt to end users to change their password.
During the password change, users are guided by password complexity rules set in the Active Directory. Any errors will display below the Confirm Password field.
 |
A user can change their password under these circumstances:
As a local user, they can change their password in online or offline mode.
As a domain user, they must have a connection to the Active Directory to change their password. This requires an internet connection, and possibly a VPN connection.
Device Trust will only prompt a domain user to change their password during an active connection to the Active Directory. If the user decides to cancel the password change prompt and go offline, they will not be able to change their password until they restore their connection to the Active Directory.
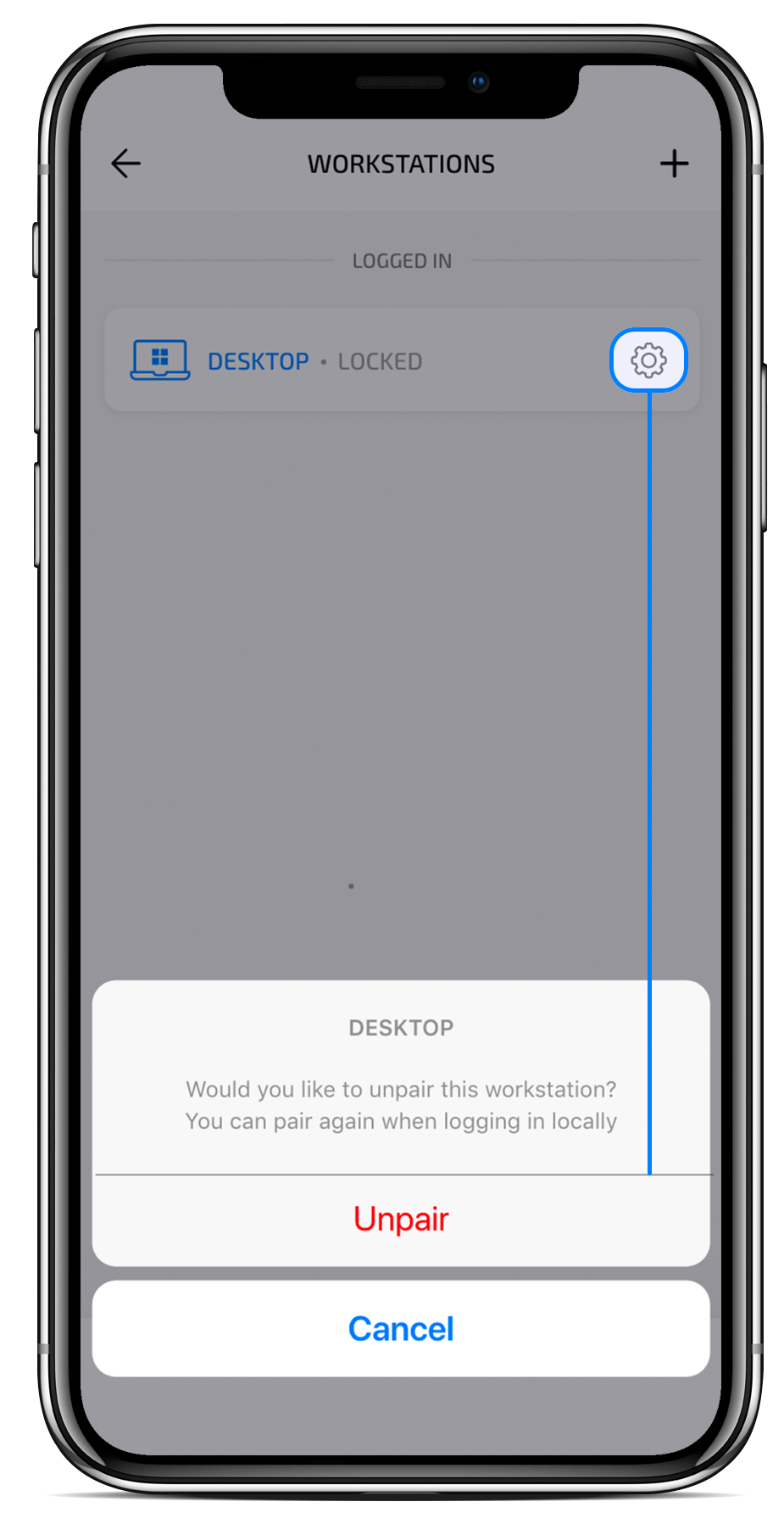
Unpairing a workstation
Open Arculix Mobile and navigate to the Workstation page. On the right side of the workstation’s name, click on the gear icon to bring up the option to unpair the workstation. Click Unpair to unregister the workstation from Arculix. If you are currently logged in to your workstation when you unpair, you will be logged out and forced to pair when logging on again.
 |
 |
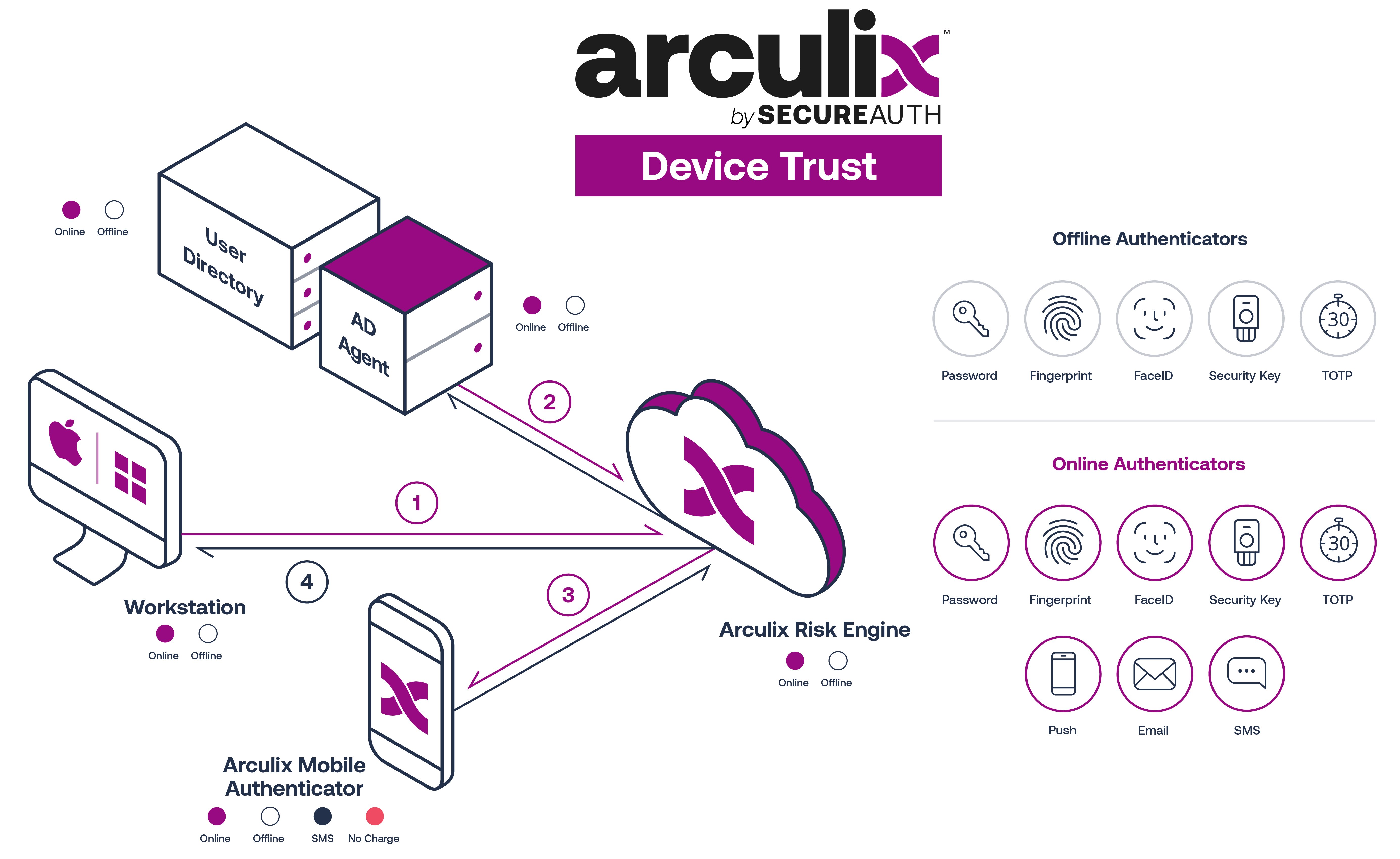
Always access
The architectural diagram below outlines the primary Device Trust subsystems instrumental in delivering the service. The four subsystems involved are as follows.
Enterprise User Directory and the Arculix AD Agent
Arculix Cloud: Policy and Risk Engine
Registered phone with Arculix Mobile app
Workstation (Windows/Mac) Agent
 |
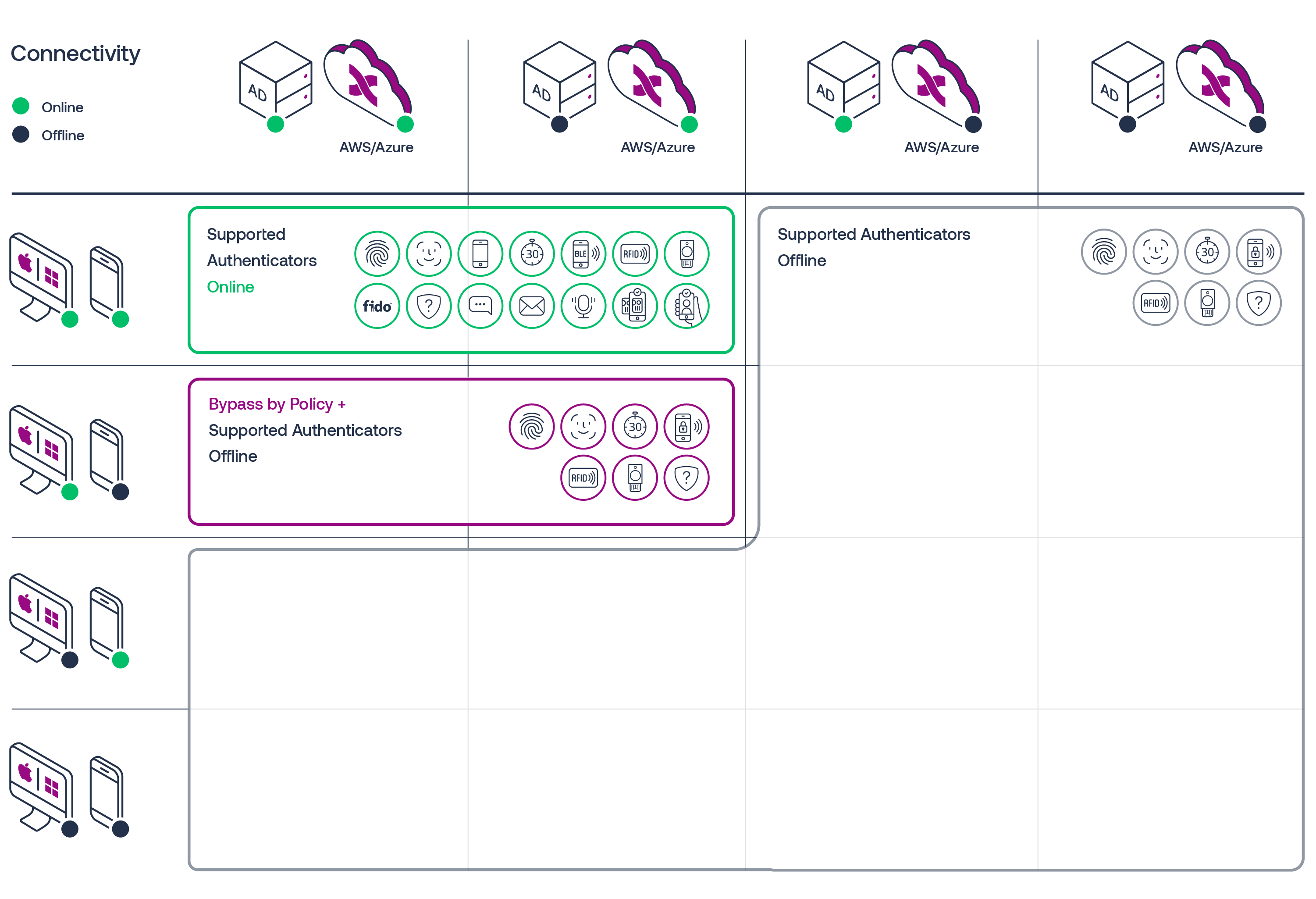
The validation matrix below details the valid authenticators in the different system availability states. All the permutations of this matrix should be tested against the authenticators applicable to the environment being deployed in.
 |
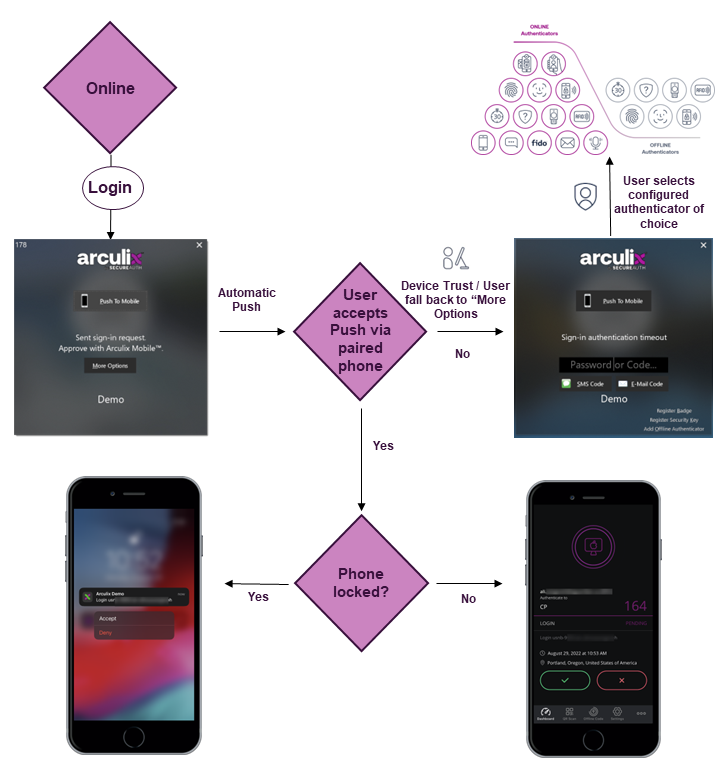
Expected online UX flow
Below is a flow diagram of the expected screen when all systems are online. All enterprise supported authenticators should be tested.
Test approval of Push notification from both a locked and unlocked phone.
Let the Push expire or select More Options to access the secondary MFA screen. Select and test all available online and offline authenticators.
 |
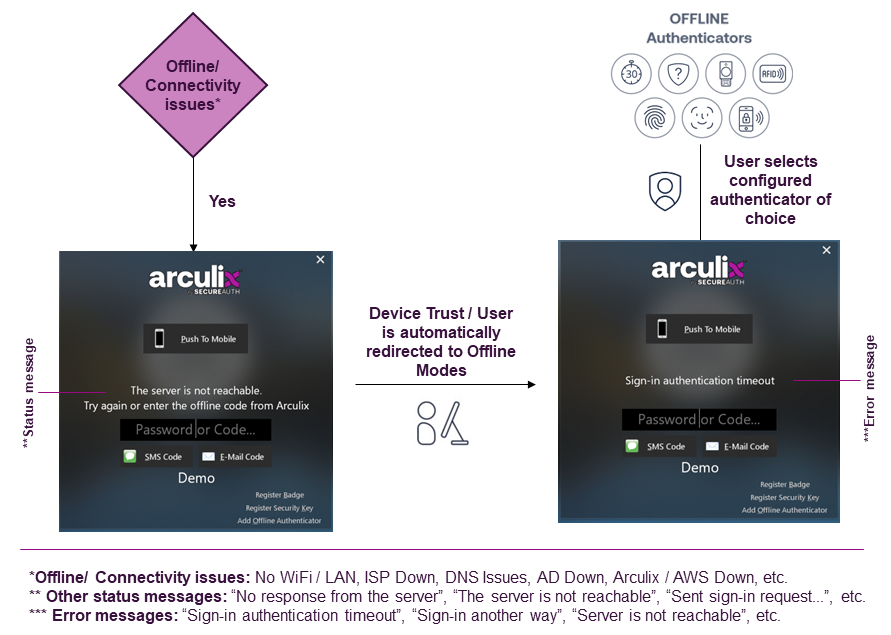
Expected offline UX flow
Below is a flow diagram of the expected screen when one or more subsystems are offline. Test all available offline authenticators for when workstation, phone, AD and Arculix / AWS are offline.
 |