VMware Horizon and UAG SAML integration
Multi-Factor Authentication (MFA) is an extra layer of security used when logging into websites or apps. Individuals are authenticated through more than one required security and validation procedure that only they know or have access to.
Security Assertion Markup Language (SAML) is a protocol for authenticating to web applications. SAML allows federated apps and organizations to communicate and trust one another’s users.
VMware Horizon enables IT departments to run virtual machine (VM) desktops and applications in the data center or cloud and remotely deliver these desktops and applications to employees as a managed service. In a normal mode, the Unified Access Gateway (UAG) is an appliance used to ensure incoming traffic comes from a strongly authenticated remote user. Unified Access Gateway directs authentication users to the appropriate server and only to desktop and application resources to which the user is actually entitled.
Arculix, as a SAML provider, improves the user login experience for Horizon users with convenient MFA. This manual illustrates how to configure both VMware Horizon and UAG with Arculix’s single sign-on solution. Arculix’s solution for VMware Horizon and UAG eliminates the second logon on the Horizon Agent machine using True SSO, which generates certificates for each user and then uses those certificates to automatically sign into the Horizon Agent machine.
Prerequisites
Configured Arculix instance and user account with administrative privileges for Arculix.
Configured Arculix LDAP Agent.
For more information, see the Arculix LDAP Agent deployment guide.
Configured VMware Horizon Enrollment server which has a trust relationship with Horizon Connection server.
Configured Certificate Authority server.
User account with administrative privileges for VMware Connection server and UAG.
Arculix SAML configuration as an Identity Provider (IdP)
In this section, you'll add an application for VMware Horizon and UAG and set the SAML configuration settings. This will be the Identity Provider (IdP) side of the configuration.
Log in to Arculix with an administrative account and go to Applications.
Click Create New Application.
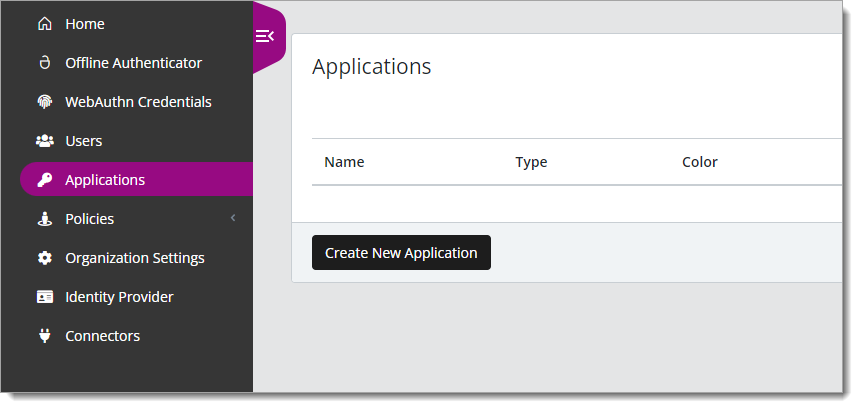
In the New Application form, on the General tab, set the following configurations:
Name
Set the name of the application. This is the name to display for push notifications, in the Admin panel, Application portal, and audit logs.
For example, UAG.
Type
Set to SAML Service Provider.
Out of Band Methods
Select the allowed methods end users can choose to approve MFA requests.
For example, Arculix Mobile app (push notifications), SMS, or Security Key.
Message for MFA Requests
Optional. Type a message displayed to end users when sending an MFA request via push notification, SMS, or email.
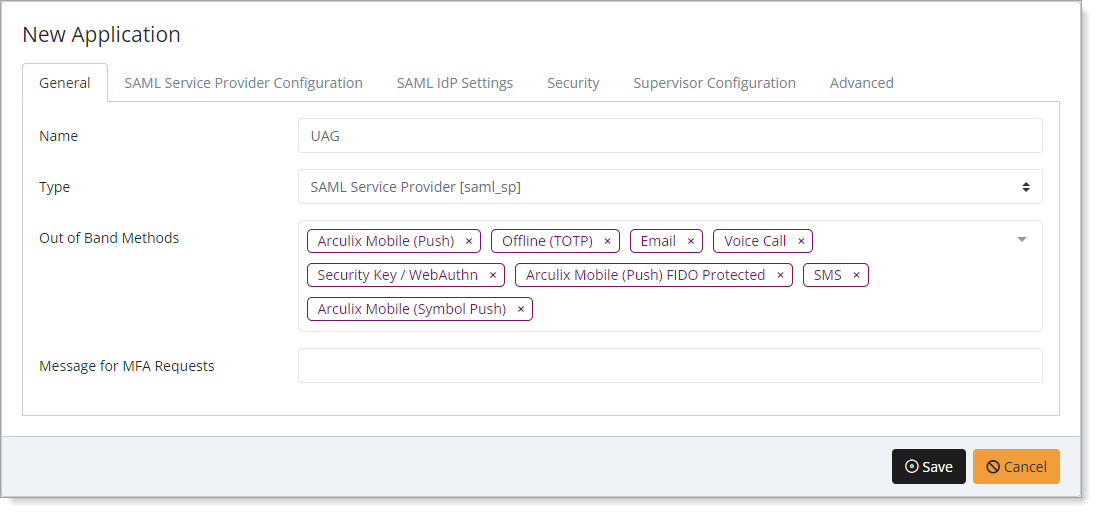
Select the SAML Service Provider Configuration tab, and set the following configurations:
Issuer or Entity ID
Enter the Issuer/EntityID of your UAG instance.
For example,
https://<HORIZON_UAG_FQDN/portal.Log in URL
The login URL for UAG.
For example,
https://HORIZON_UAG_FQDN/portal.NameID Format
Set to Email Address.
Name Identifier
Set to Email.
Save your changes.
UAG configuration
In this section, you'll configure UAG as a service provider (SP).
Download the SAML metadata and certificate for your organization from Arculix.
Metadata download:
https://sso.acceptto.com/<myorganization>/saml/download/metadataView metadata:
https://sso.acceptto.com/<myorganization>/saml/metadataCertificate download:
https://sso.acceptto.com/<myorganization>/saml/download/certLog in to your UAG admin page with an admin account.
For example, your login URL might be
https://<HORIZON_UAG_FQDN>:9443/admin.
Select Configure Manually.
Scroll down to the Identity Bridging Settings section and click the gear icon for Upload Identity Provider Metadata.
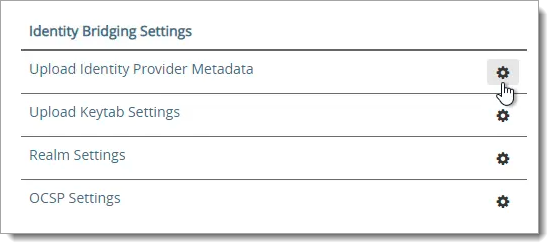
Next to IDP Metadata, click the Select link.
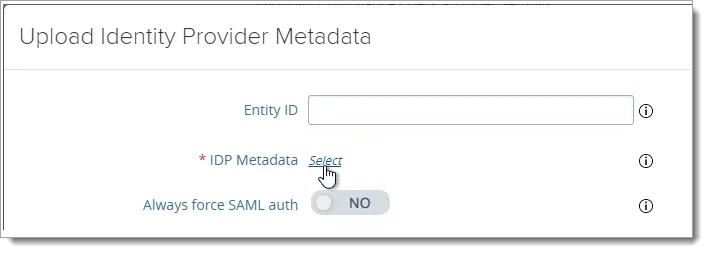
Find the xml metadata file you downloaded earlier from Arculix. Click Save.
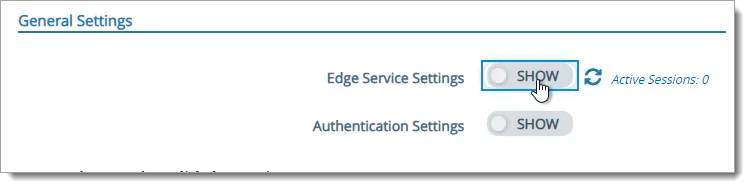
At the top of the page, next to Edge Service Settings, click SHOW.
Next to Horizon Settings, click the gear icon.
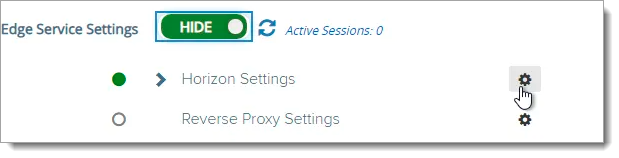
At the bottom of the page, click the More link.
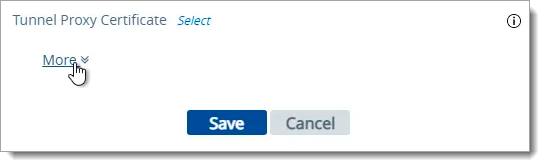
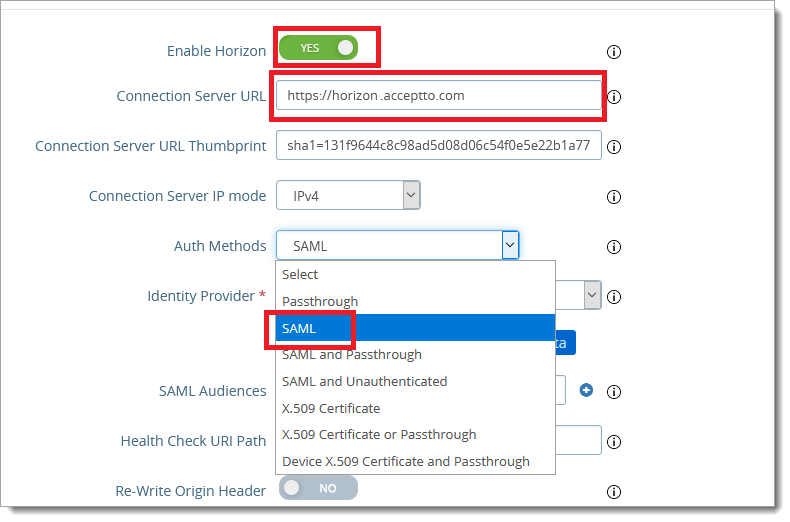
In the middle of the page, change the Auth Methods setting to SAML.
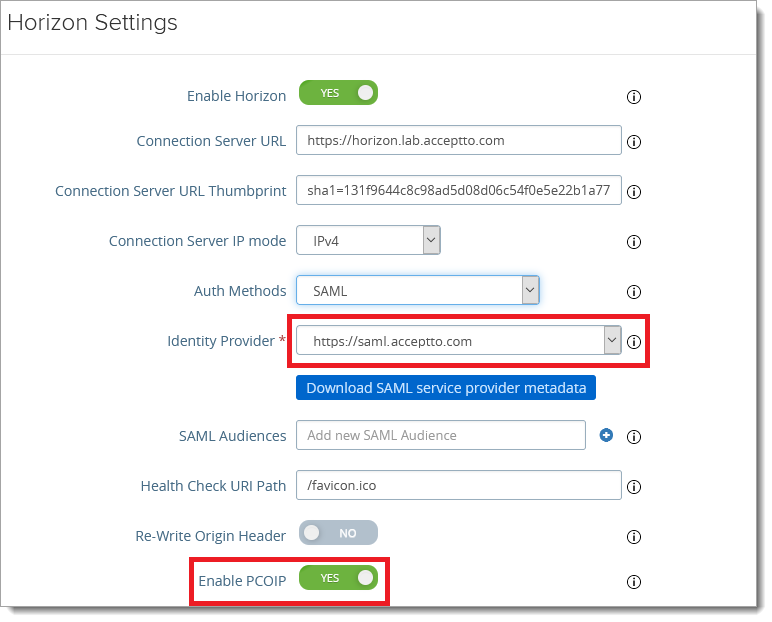
Change the Identity Provider setting to the one for Arculix (formerly Acceptto). Then, click Download SAML service provider metadata to download the file. We will need this file to configure the Horizon Connection server.
At the bottom of the page, click Save.
Horizon Connection Server configuration
To integrate the VMware Horizon connection server with Arculix and enable SAML authentication, follow these steps.
Log in to Horizon Console.
In the left menu, go to Settings > Servers.
On the right, select the Connection Servers tab.
Highlight a Connection Server to which UAG talks and click Edit.
Select the Authentication tab.
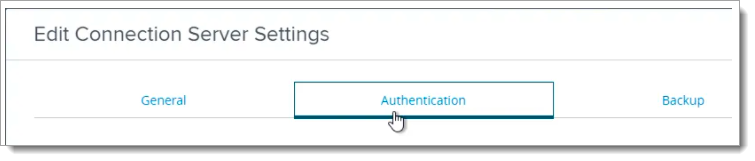
Set Delegation of authentication to VMware Horizon (SAML 2.0 Authenticator) to Allowed.
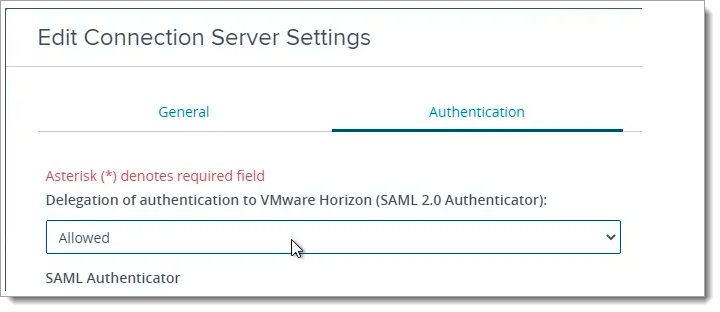
Click Manage SAML Authenticators.
Click Add.
Set the authenticator Type to Static.
Dynamic is valid only for VMware Access (aka Identity Manager).
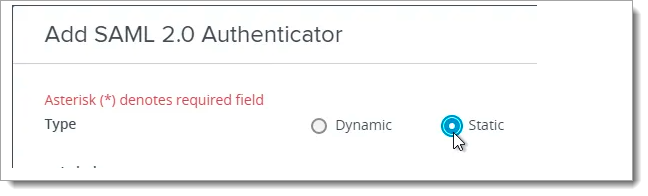
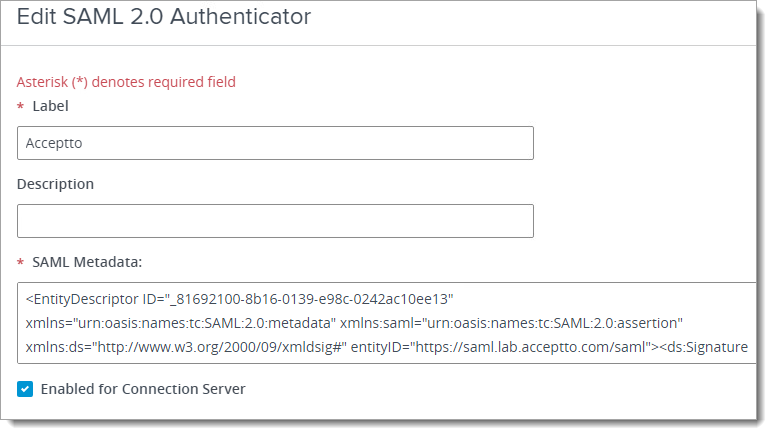
With a text editor, open the metadata.xml file you just downloaded from UAG, and copy its contents to your clipboard. Then, go back to the Horizon Console and paste in the SAML Metadata field.
Give your SAML 2.0 Authenticator a name in the Label field and click OK.
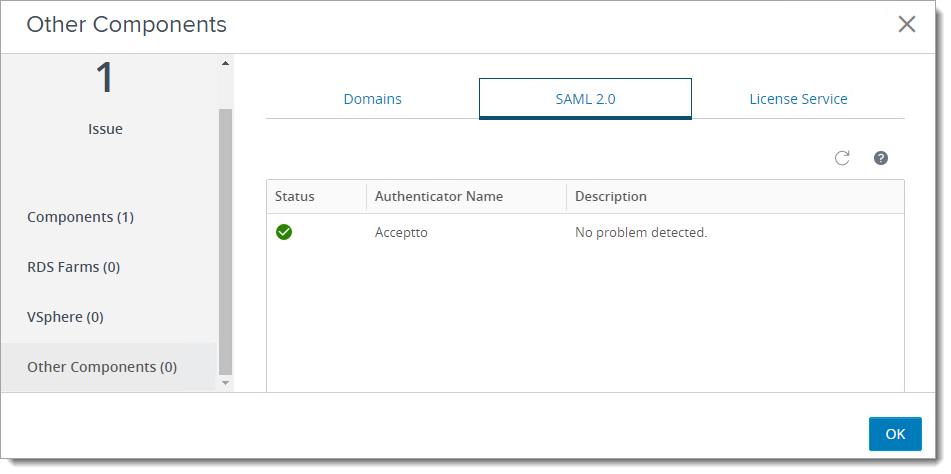
In Horizon Console, do the following:
Go to Monitor > Dashboard.
In the System Health section, click VIEW.
On the left, select Other Components.
On the right, select the SAML 2.0 tab.
You should see the SAML authenticator name and status for Arculix.
Enable True SSO on the Horizon Connection Server
On the Connection Server, open an elevated command prompt and run the following commands.
Note
The commands in this section are case sensitive.
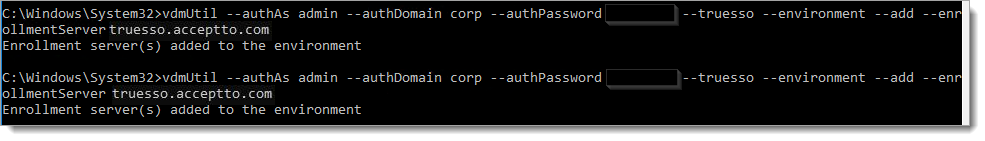
To add the Enrollment Server, run the following command.
vdmUtil --authAs admin-role-username --authDomain domain-name --authPassword admin-user-password --truesso --environment --add --enrollmentServer enroll-server1-fqdn
To see the available certificate authorities and certificate templates for a particular domain, run the following command.
vdmUtil --authAs admin-role-username --authDomain domain-name --authPassword admin-user-password --truesso --environment --list --enrollmentServer enroll-server-fqdn --domain domain-fqdn
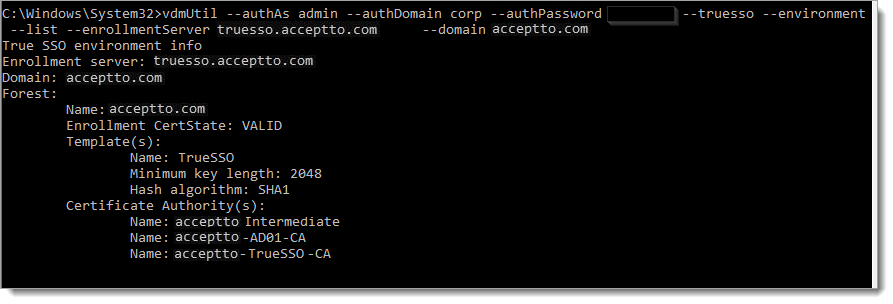
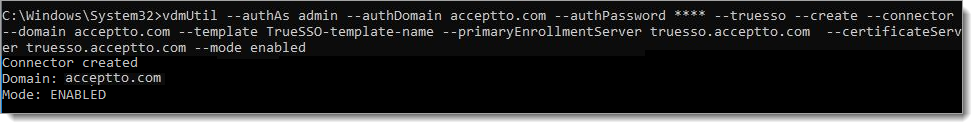
To enable the Enrollment Servers for a particular domain, run the following command.
vdmUtil --authAs admin-role-username --authDomain domain-name --authPassword admin-user-password --truesso --create --connector --domain domain-fqdn --template TrueSSO-template-name --primaryEnrollmentServer enroll-server-fqdn --certificateServer ca1-common-name1 --mode enabled
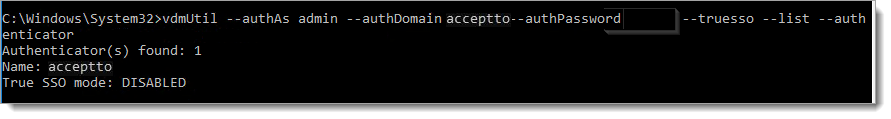
To see the SAML authenticators configured in Horizon Console, run the following command.
vdmUtil --authAs admin-role-username --authDomain domain-name --authPassword admin-user-password --truesso --list --authenticator
To enable True SSO for a particular SAML authenticator, run the following command.
vdmUtil --authAs admin-role-username --authDomain domain-name --authPassword admin-user-password --truesso --authenticator --edit --name authenticator-fqdn --truessoMode {ENABLED|ALWAYS}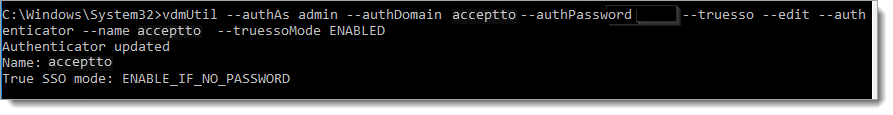
In Horizon Connection console, do the following:
Go to Monitor > Dashboard.
In the System Health section, click VIEW.
On the left, select Components.
On the right, select the TrueSSO tab.
You should see the status of True SSO in Horizon Console.
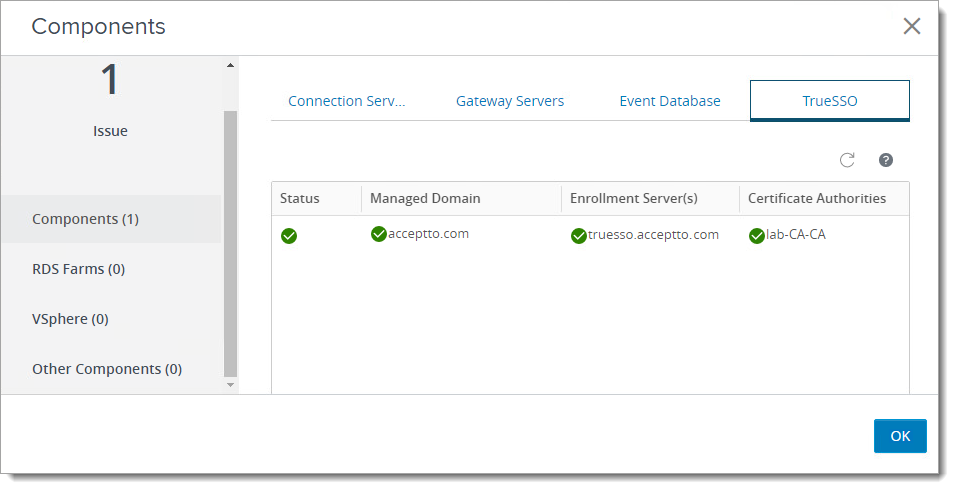
Test your application integration
Go to your UAG URL through a browser or VMWare Horizon client.
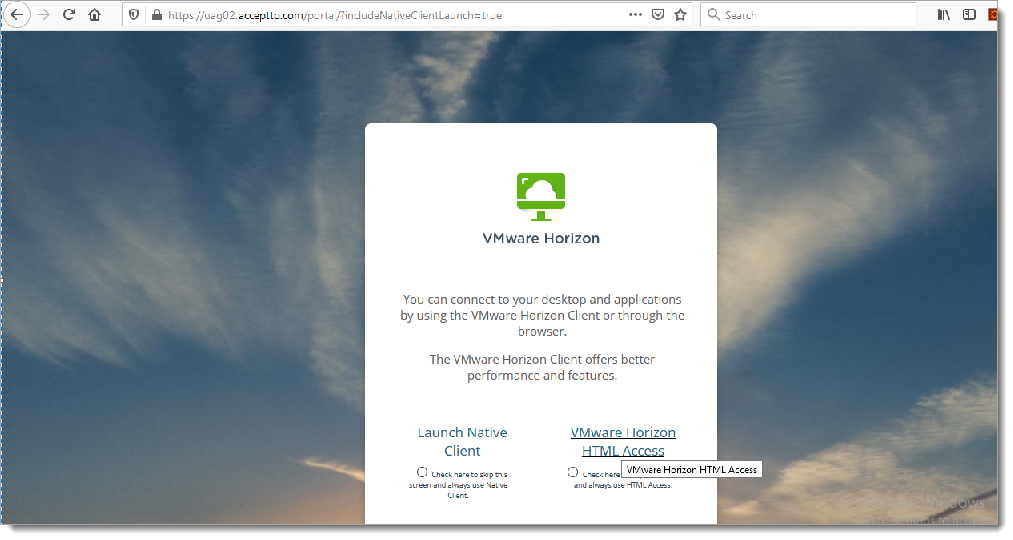
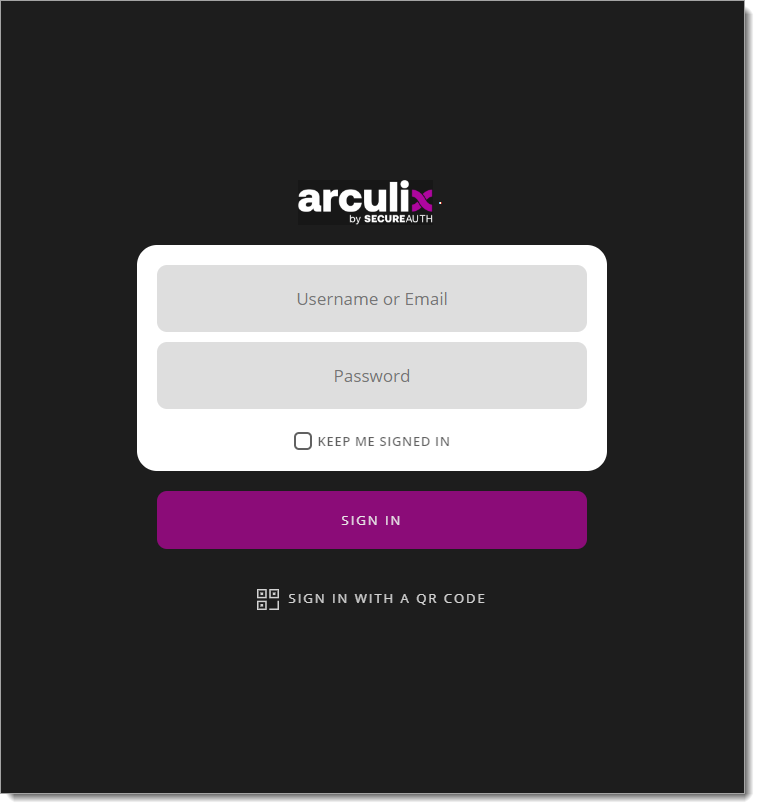
You will be redirected to the Arculix SSO page.
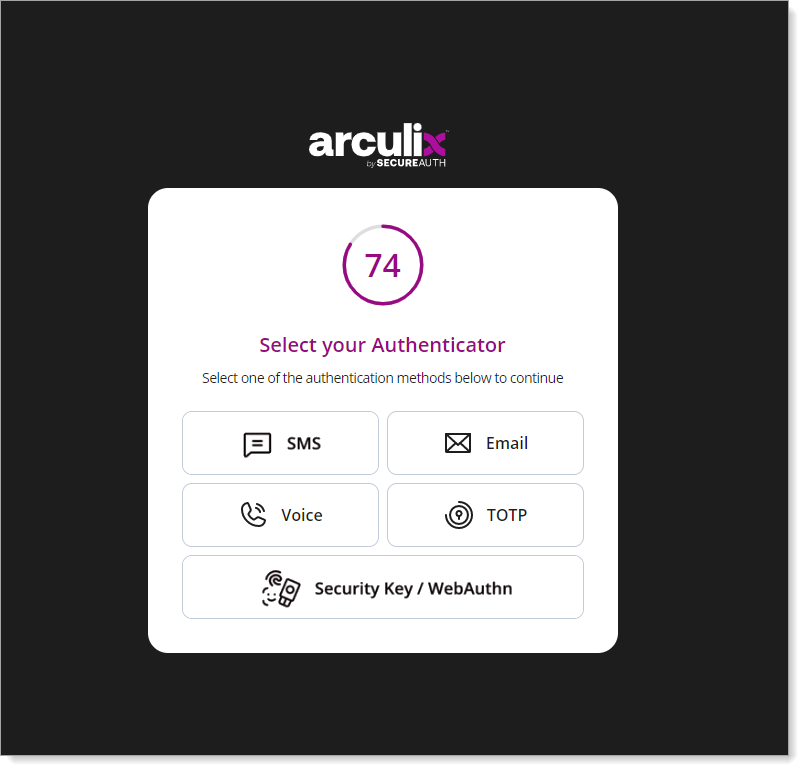
After successful authentication, select your preferred MFA method to approve access to the VMware Horizon application.
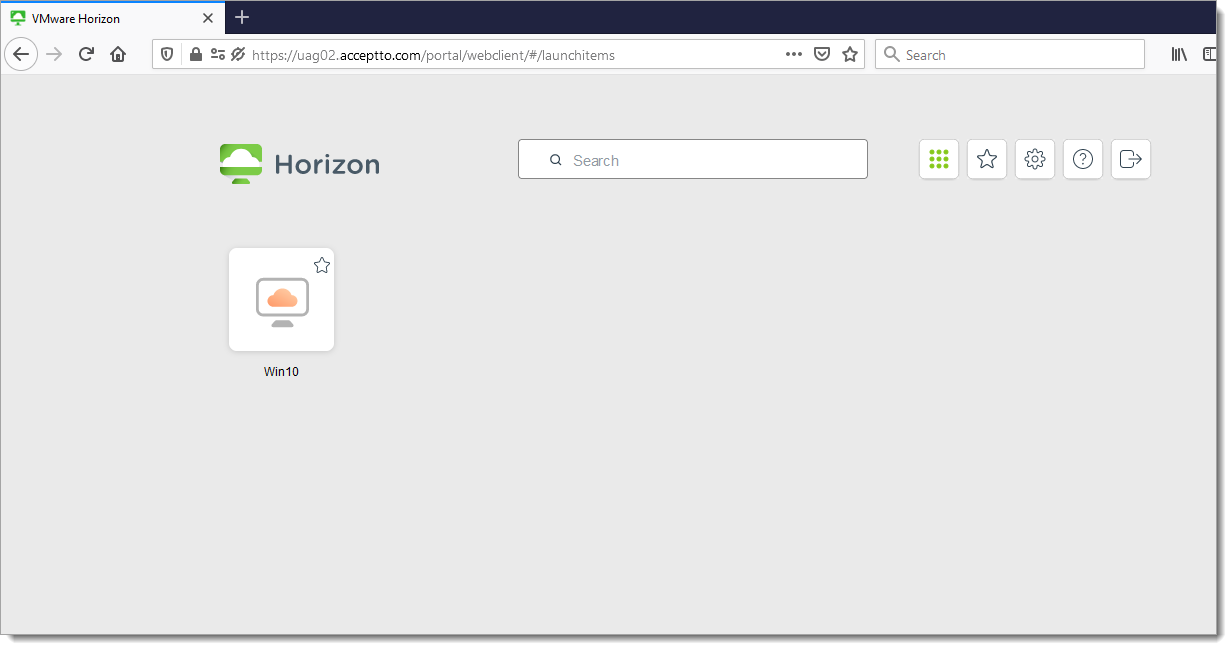
You will be redirected to your resource page. Click the Windows icon.
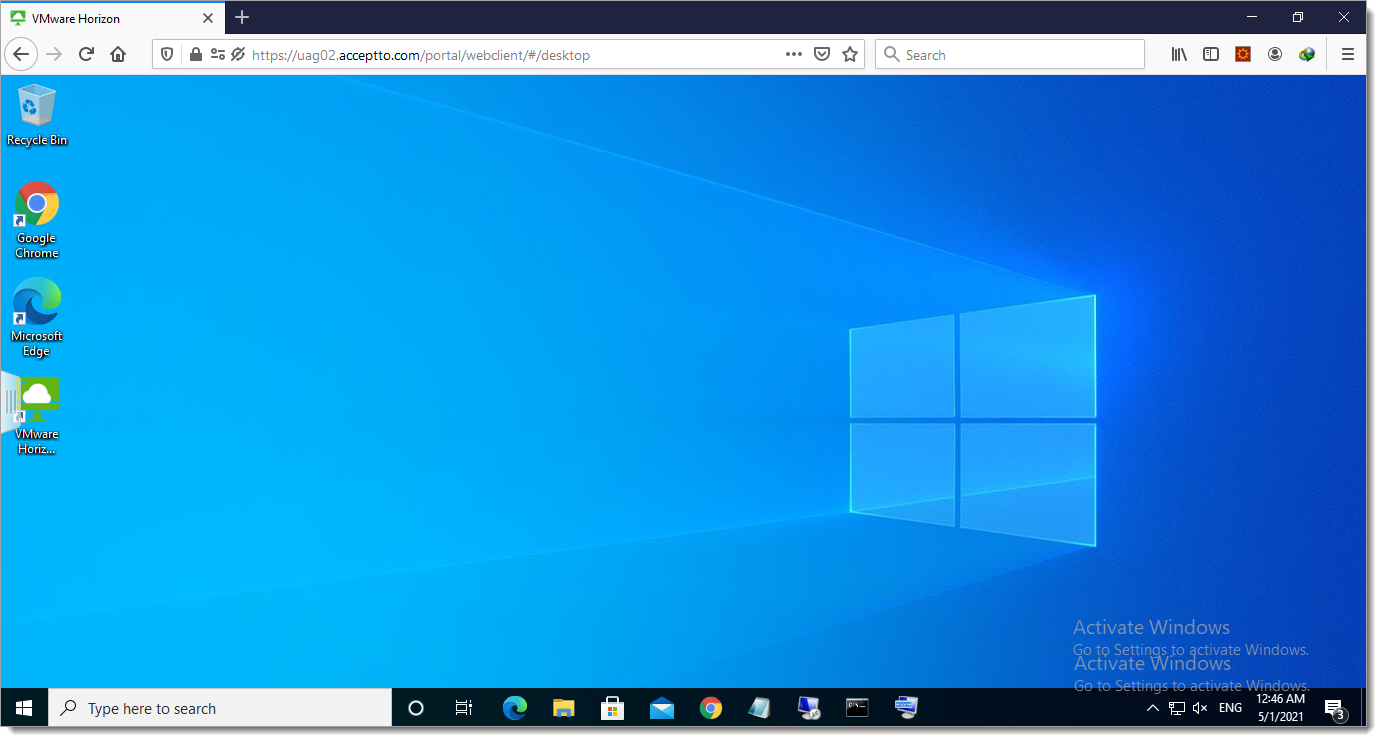
You will be automatically logged into your Windows machine without any additional authentication through an integration between Arculix SSO and VMWare TrueSSO.
Support
If you have questions or need assistance, contact SecureAuth Support.
Sales
Want to learn more about our MFA solutions? Contact our Professional Services for a demo today.
Disclaimer
All product names, trademarks, and registered trademarks are the property of their respective owners.
All company, product, and service names used in this document are for identification purposes only. The use of these names, trademarks, and brands do not constitute an endorsement by the SecureAuth Corporation.