Configure password reset policy
This guide shows how to enable the password reset flow, configure MFA options, and control which verification methods users can use during password reset.
Prerequisite for Active Directory environments
If you're using Active Directory as your user directory, complete the following before proceeding:
Update the LDAP Agent: Ensure the latest version of the LDAP Agent is installed to support password reset capabilities.
Requires LDAP Agent version 4.0.0 or later
Configure YAML settings: Add the necessary YAML keys to enable password reset functionality. For more information, see Release notes - April 24, 2025.
Step 1: Enable password reset in the directory
In Arculix Core, go to User Directories.
Edit the directory and enable:
Reset Password
Change Password
Note
Only directories that support reset functionality will show these options.
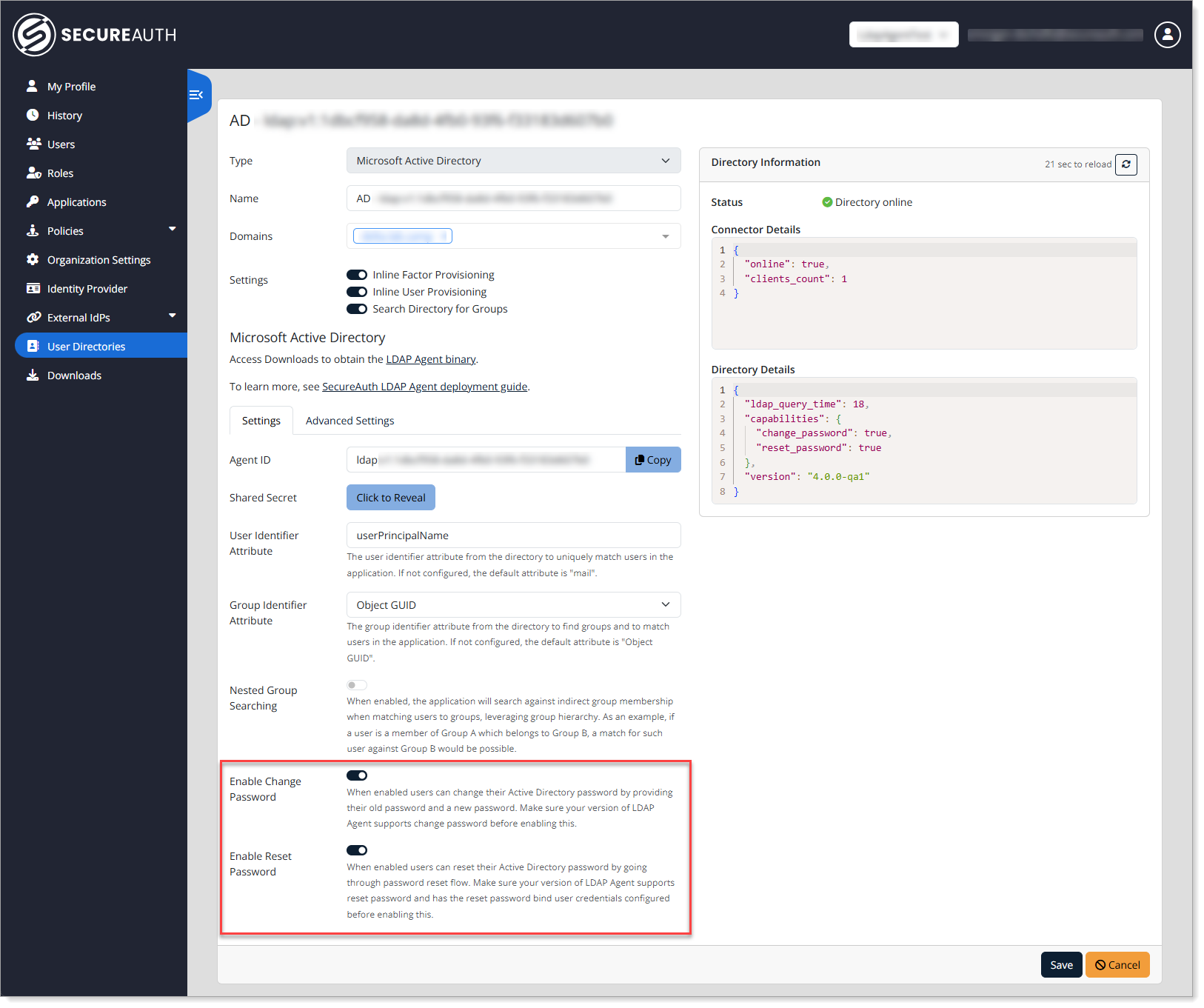
Save your changes.
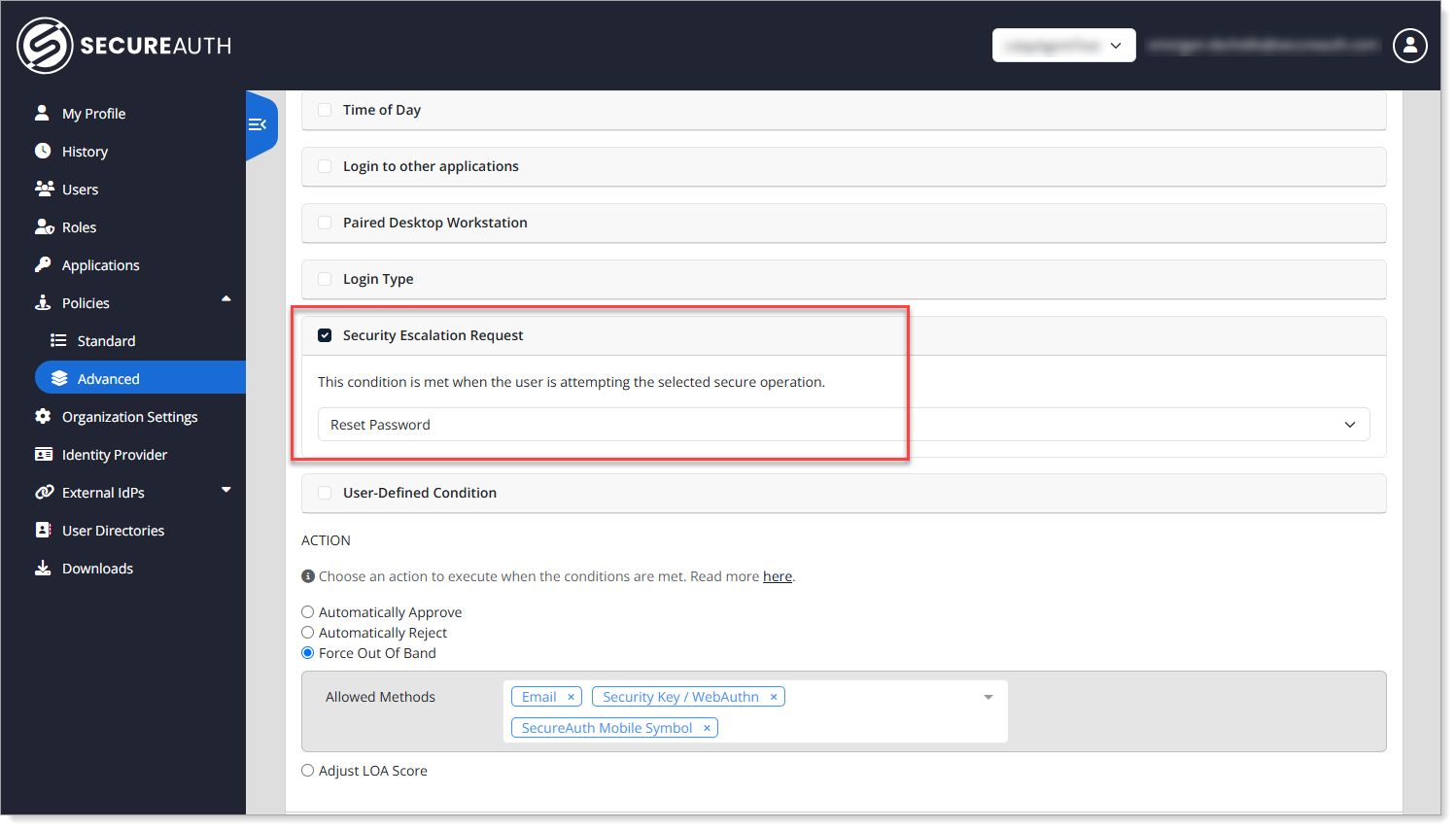
Step 2: Create a reset password policy
Go to Policies > Advanced.
Create a new policy and name it appropriately, like
Reset Password MFA Controls.In the When section, set Security Escalation Request to Reset Password.
Step 3: Define authentication factors for password reset
In the Action section of the policy, use the Force Out-of-Band setting to override default behavior and require users to complete MFA using only the specific factors you select for password reset.
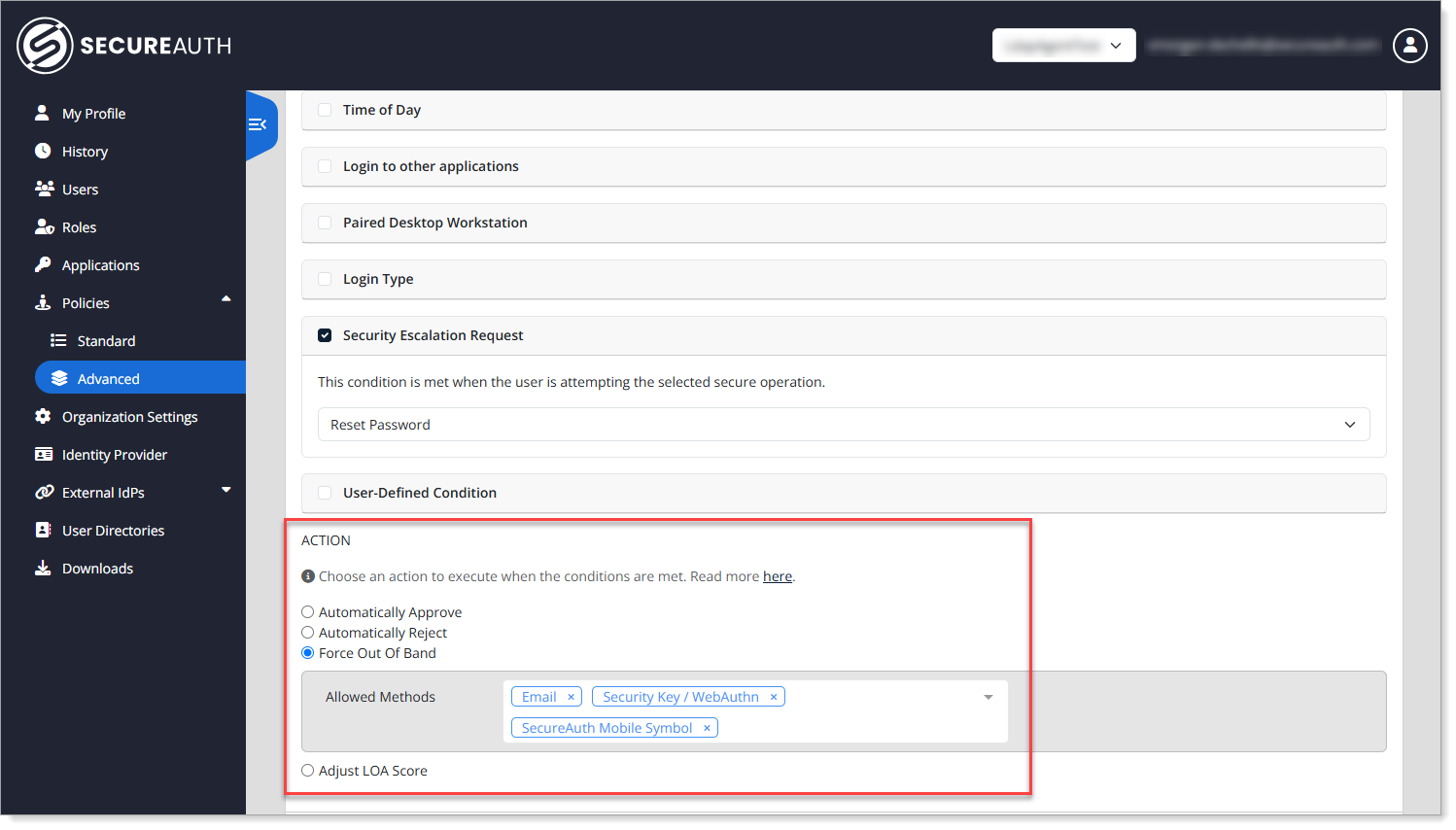
Set the Allowed Methods (like Email OTP, Security Key / WebAuthn, and Symbol Push).
For example, do not use SMS if it's not considered secure.
Step 4: Apply the policy
Scroll up to the top of the policy and assign the policy to the relevant application (typically Dashboard Core).
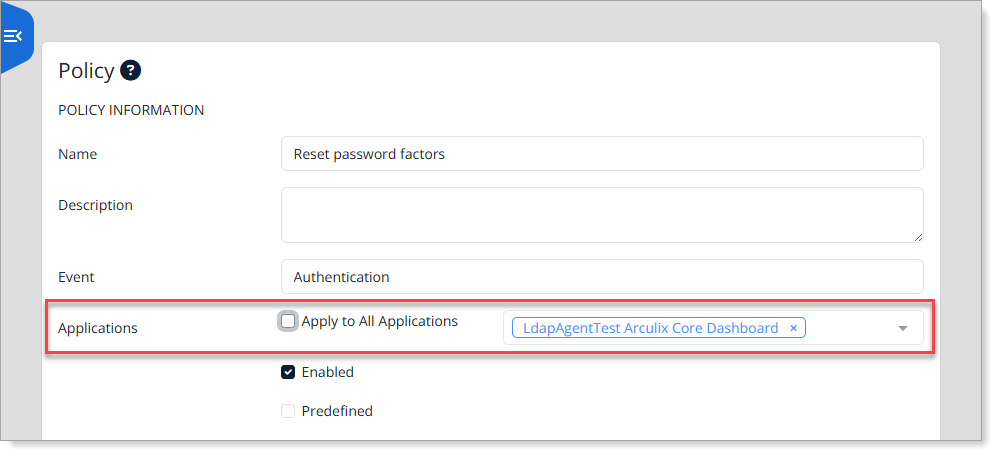
Optionally, apply it across all applications.
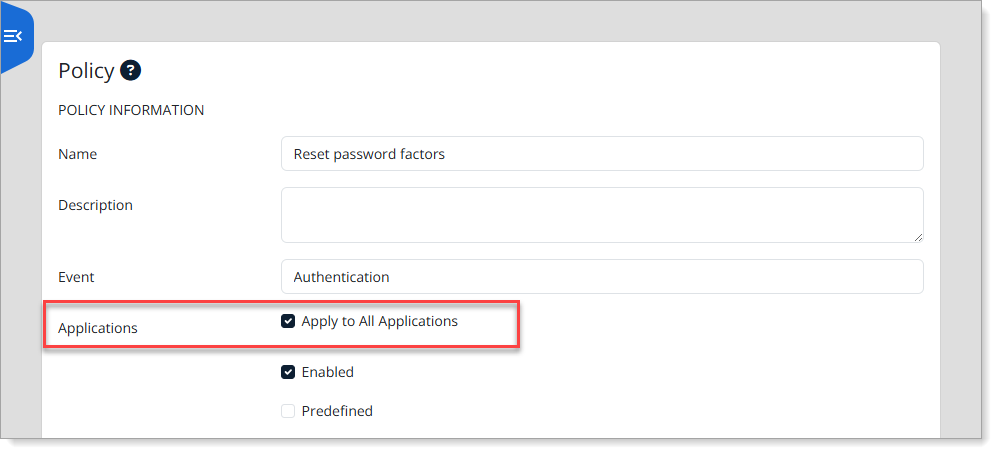
Save your changes.
Result
When a user clicks Forgot Password, only the allowed MFA methods appear in the reset flow. Users complete identity verification, then reset their password securely.
For the end user password reset flow, see How to reset your password.