Palo Alto GlobalProtect VPN SAML integration
Multi-Factor Authentication (MFA) is an extra layer of security used when logging into websites or apps. Individuals are authenticated through more than one required security and validation procedure that only they know or have access to.
Security Assertion Markup Language (SAML) is a protocol for authenticating to web applications. SAML allows federated apps and organizations to communicate and trust one another’s users.
Prerequisites
Configured Arculix instance and user account with administrative privileges for Arculix.
Configured Arculix LDAP Agent.
For more information, see the Arculix LDAP Agent deployment guide.
User account with administrative access to Palo Alto.
Arculix SAML configuration as an Identity Provider (IdP)
In this section, you'll configure Palo Alto GlobalProtect VPN as an identity provider, add an application, and set the SAML configuration settings. This will be the Identity Provider (IdP) side of the configuration.
Log in to Arculix with an administrative account and in the left navigation, click Identity Provider.

Select the SAML Certificates tab and verify whether you have an available certificate with a subject attribute or whether you need to generate a new one for the Palo Alto GlobalProtect VPN integration.
If there isn't one, click Generate Self-Signed Certificate, enter a friendly name, and click Generate Certificate.
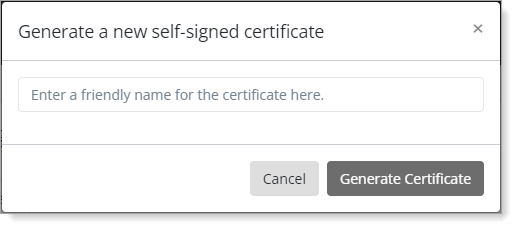
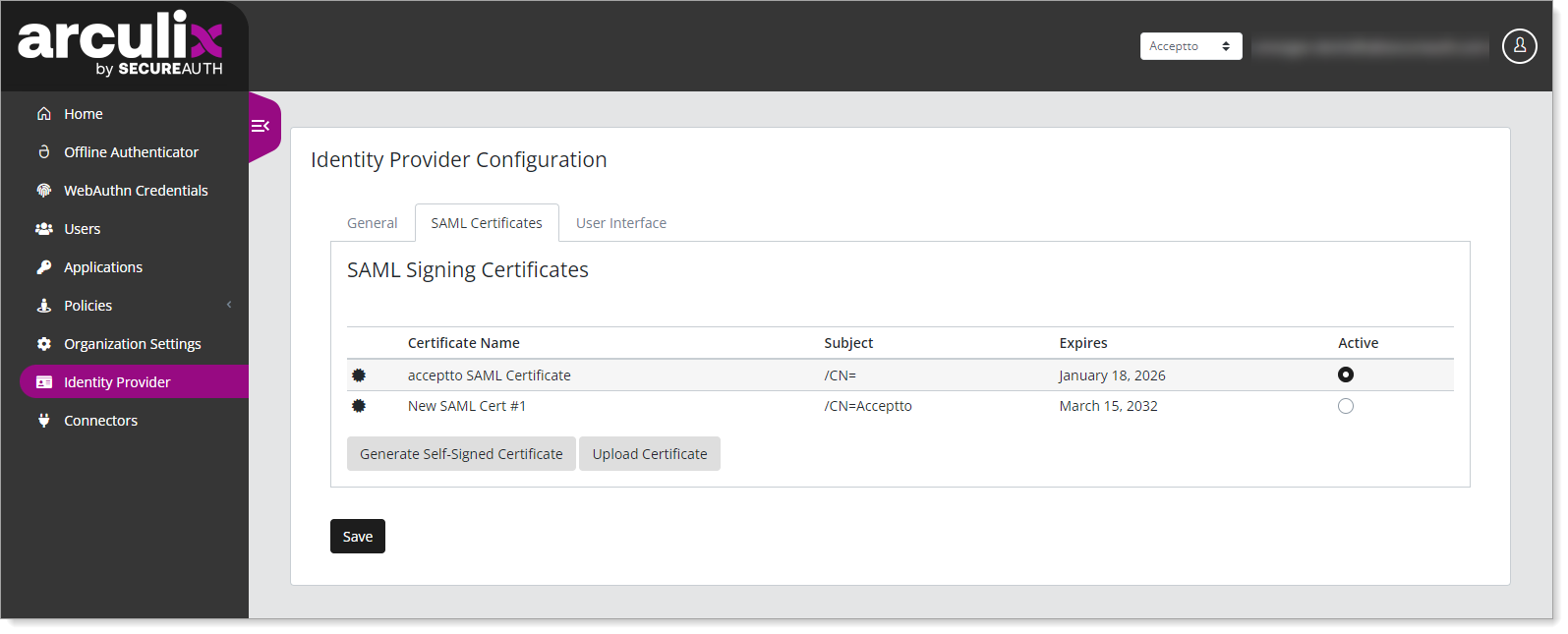
Review the certificate settings.
You could set the new certificate to Active, but this can interfere with applications that were set with the previous certificate. You'll want to use this new certificate separately for the Palo Alto GlobalProtect VPN application that you will create next.
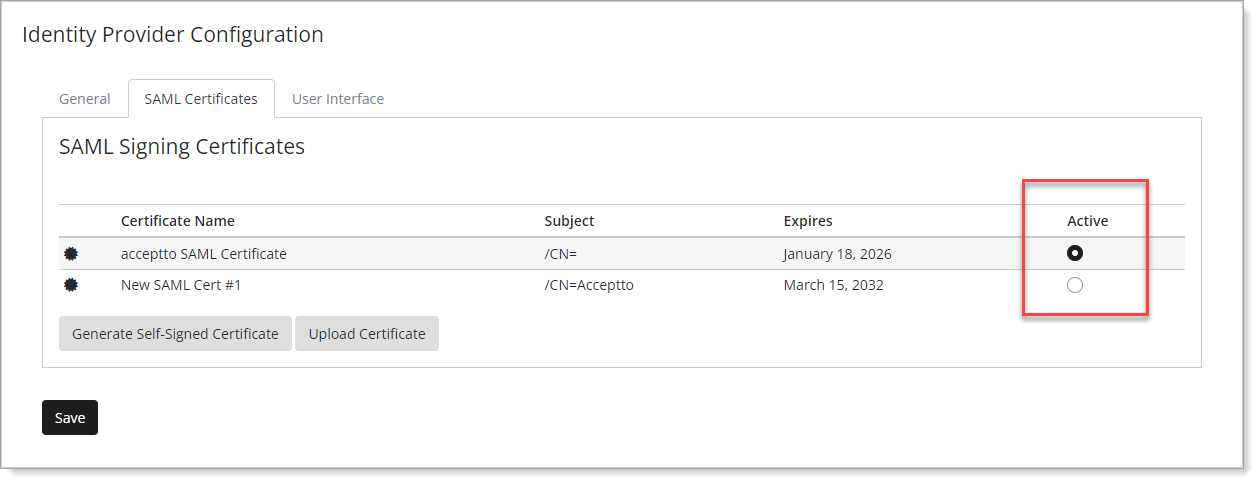
Save your changes.
Be sure to save your changes so that the SAML certificate has the subject attribute.
In the left navigation, click Applications.
Click Create New Application.
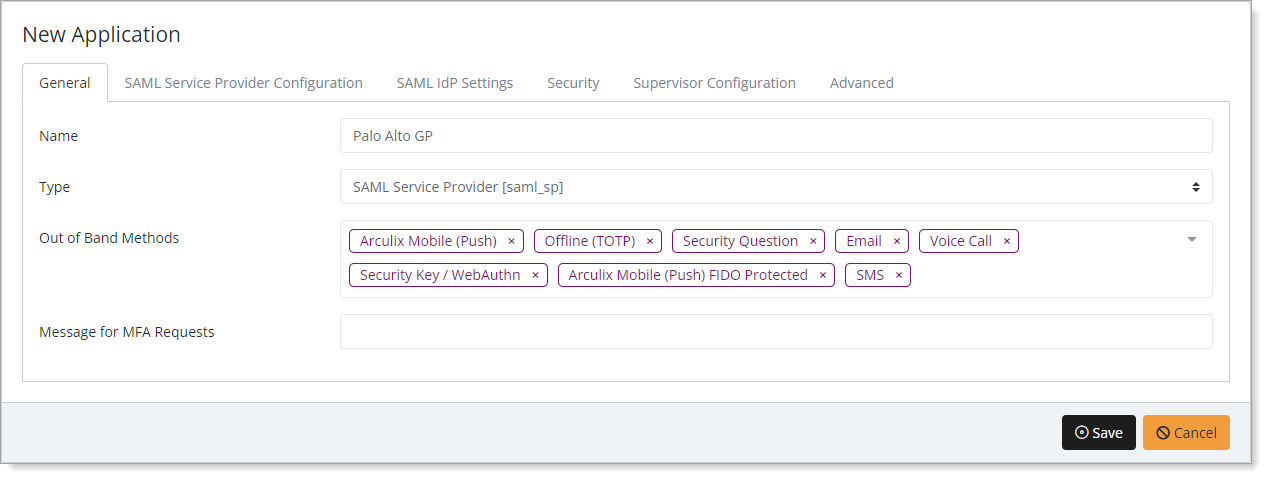
In the New Application form, on the General tab, set the following configurations:
Name
Set the name of the application. This is the name to display for push notifications, in the Admin panel, Application portal, and audit logs.
For example, Palo Alto GP
Type
Set to SAML Service Provider.
Out of Band Methods
Select the allowed methods end users can choose to approve MFA requests.
For example, Arculix Mobile app (push notifications), SMS, or Security Key.
Message for MFA Requests
Optional. Type a message displayed to end users when sending an MFA request via push notification, SMS, or email.
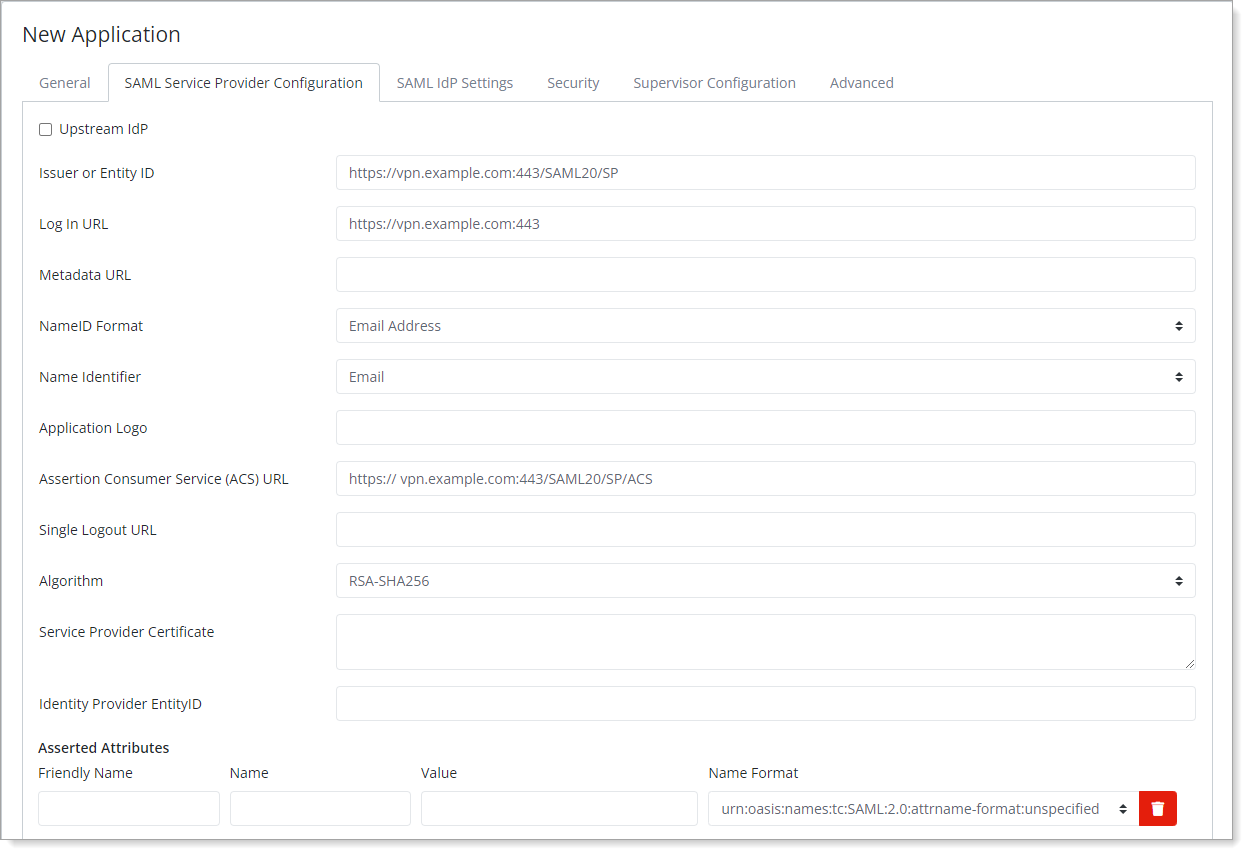
Select the SAML Service Provider Configuration tab, and set the following configurations:
Issuer or Entity ID
Enter the Issuer or Entity ID of your Palo Alto VPN.
For example,
https://vpn.example.com:443/SAML20/SPLog in URL
Enter the URL used by your users to access the VPN.
For example,
https://vpn.example.com:443NameID Format
Set to Email Address.
Name Identifier
Set to Email.
ACS URL
Enter the Assertion Consumer Service of your Palo Alto VPN.
For example,
https:// vpn.example.com:443/SAML20/SP/ACSCertificate
Scroll down to the bottom of the page, move the slider to enable Select IdP Siging Certificate and select the certificate with the subject attribute as Active.
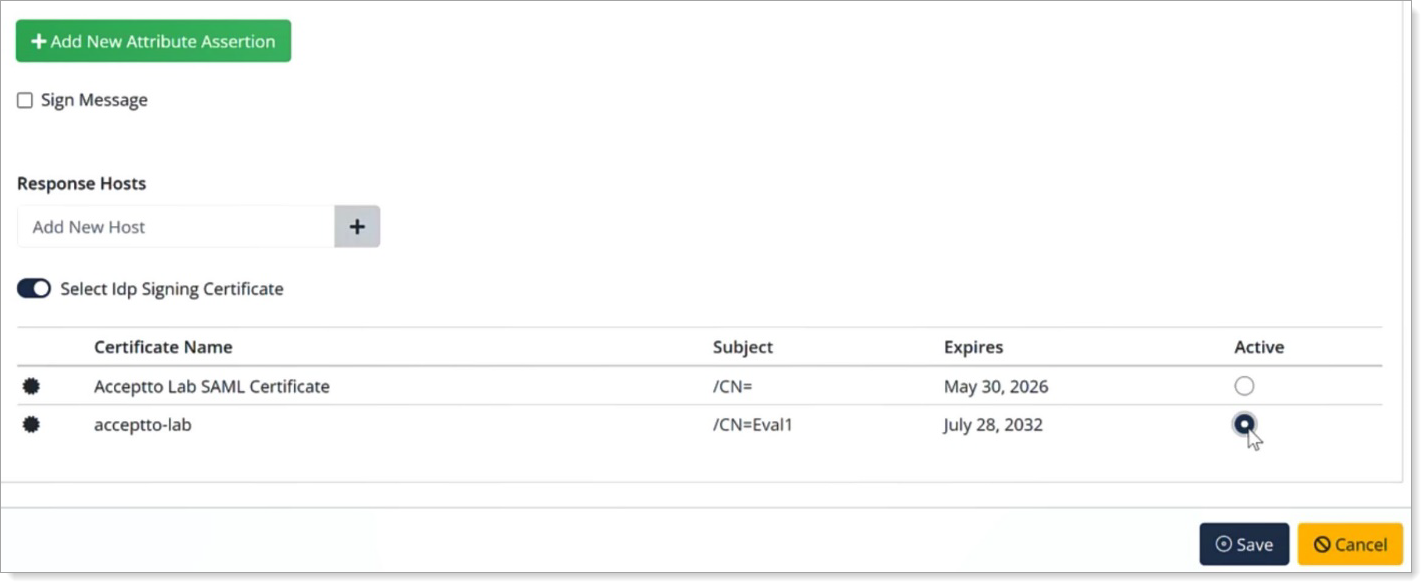
Save your changes.
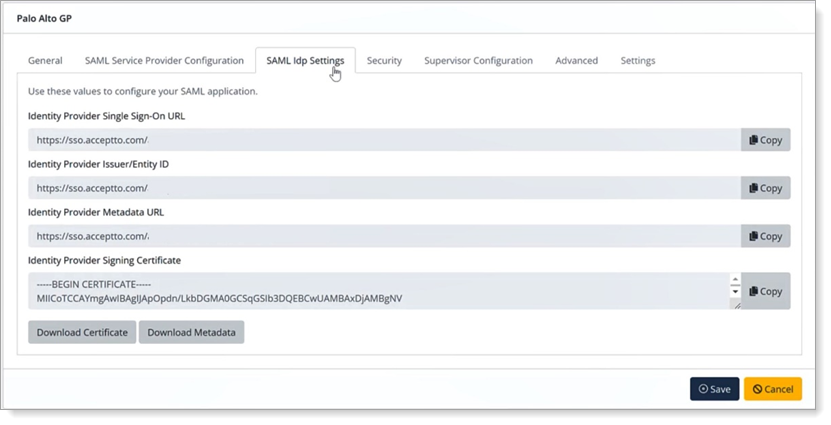
Next, download the metadata for this application.
Go back to the application you just created, click Edit and then Download Certificate.
Palo Alto GlobalProtect VPN configuration
In this section, you'll configure Palo Alto GlobalProtect VPN as a service provider (SP).
Log in to Palo Alto as an administrator.
To upload the Arculix SAML metadata, go to the Device tab, then SAML Identity Provider, and click Import.
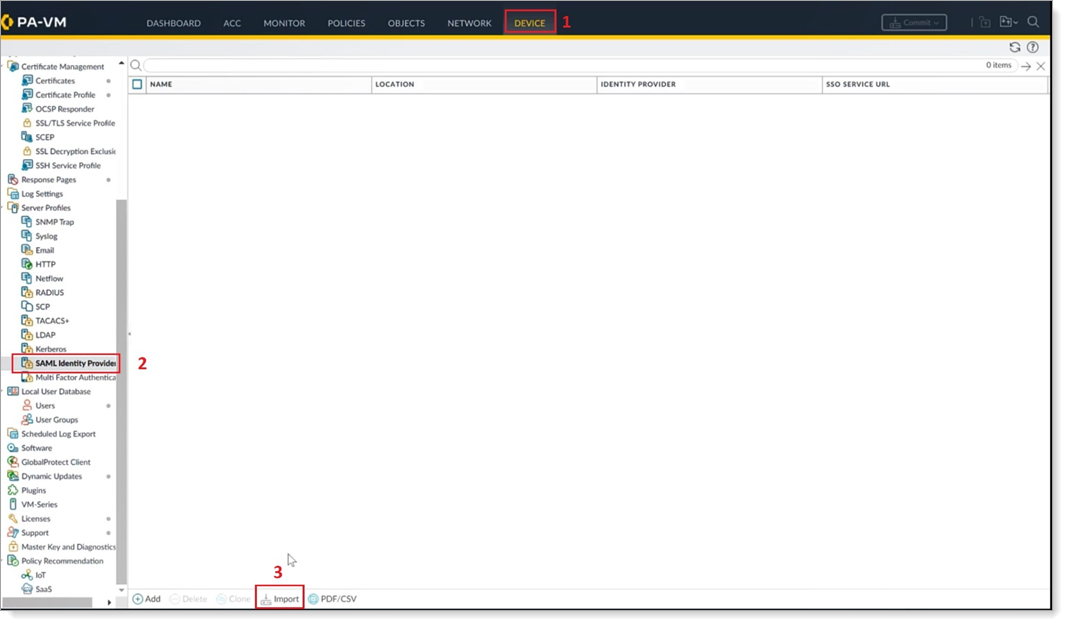
Set the following configurations:
Profile Name
Set a profile name for this integration.
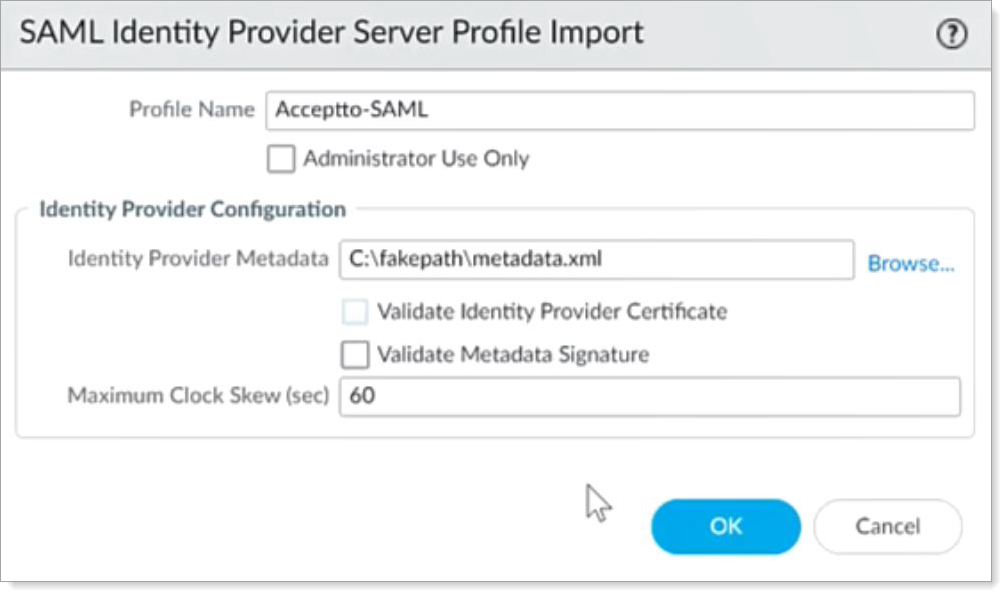
Identity Provider Metadata
Browse to the folder that contains the Arculix metadata file.
Validate Identity Provider Certificate
Clear this check box.
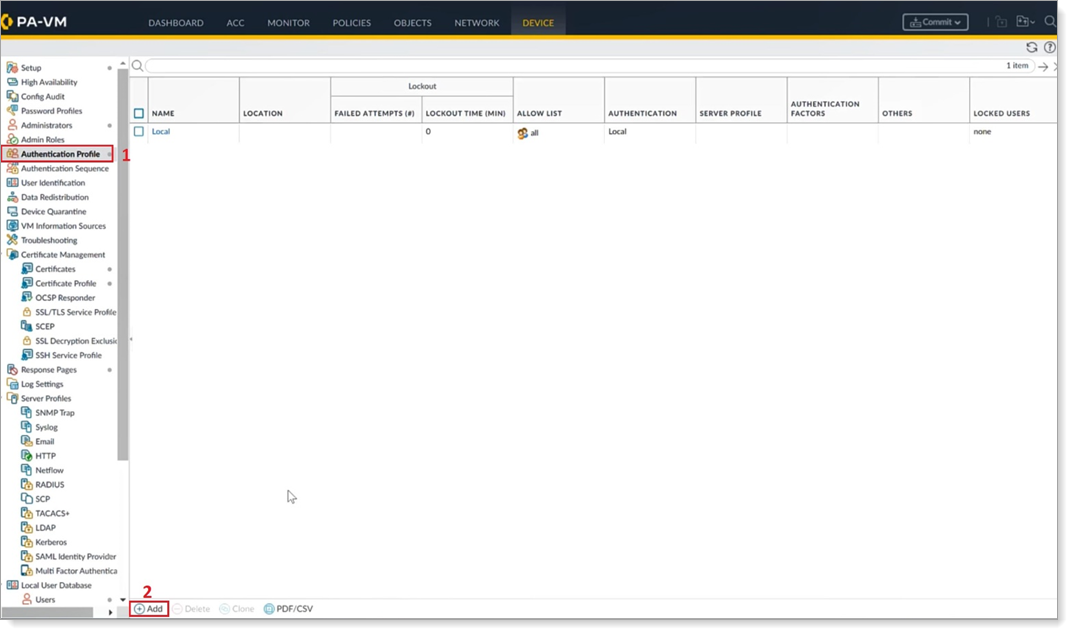
In the left navigation, go to Authentication Profile and then click Add.
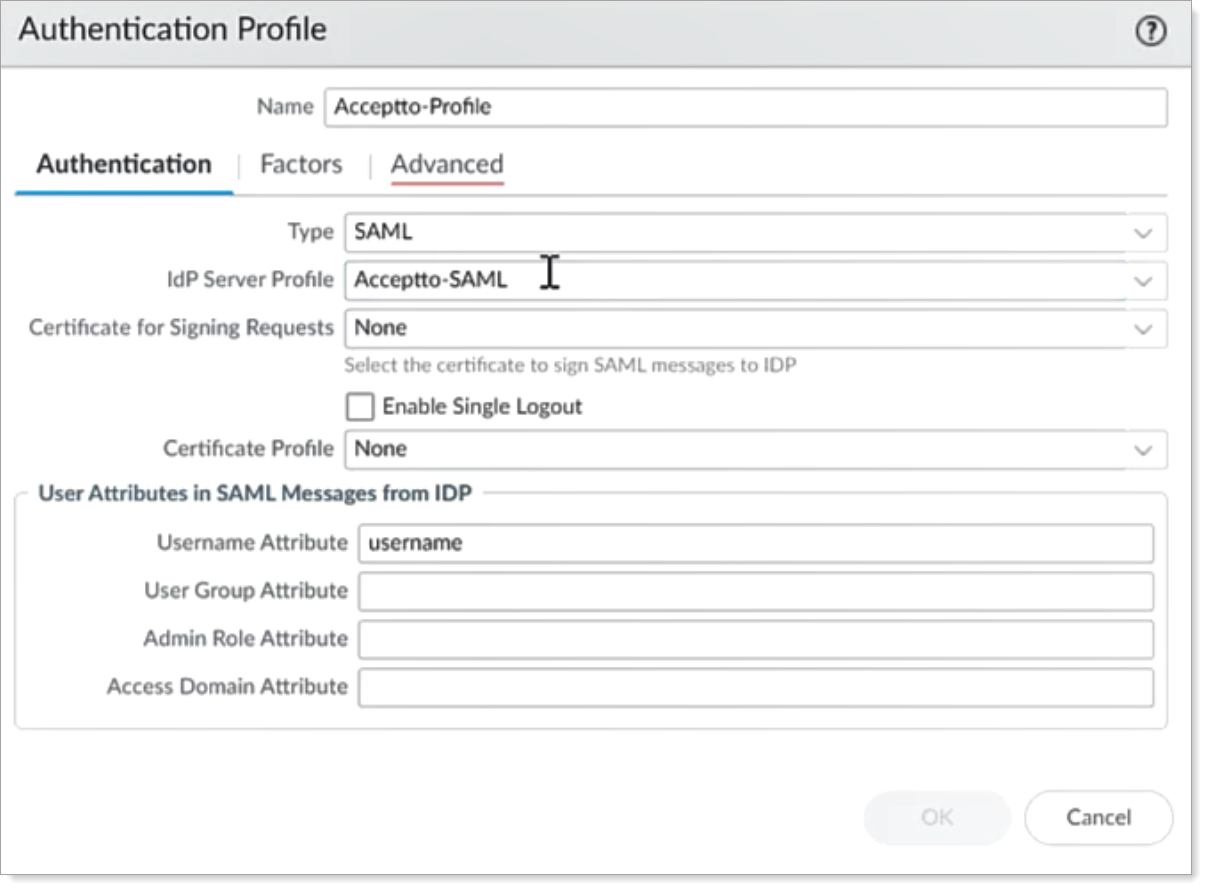
On the Authentication tab, set the following configurations:
Name
Set an authentication profile name for this integration.
Type
Set the type to SAML.
IdP Server Profile
Set to the name of the Arculix SAML server.
Leave the other settings as set by default.
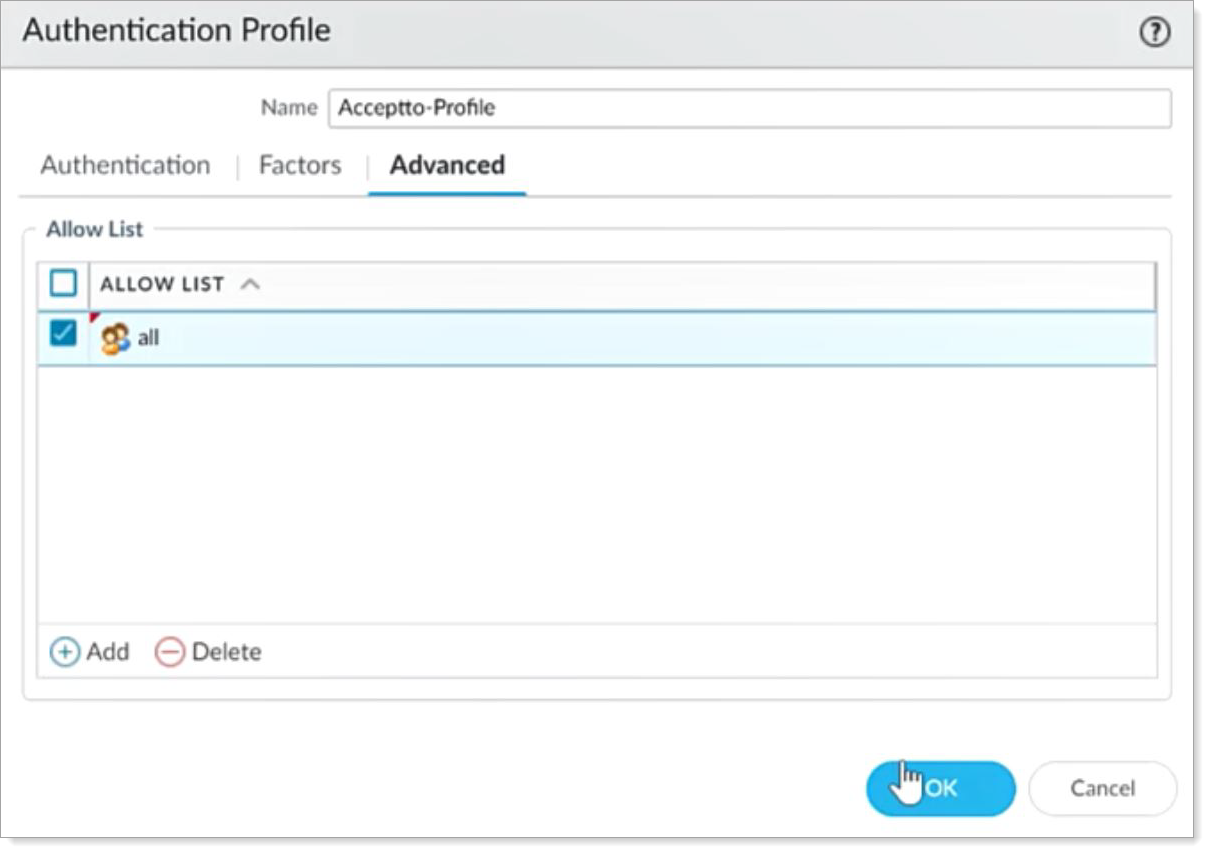
Select the Advanced tab, click Add, select the All check box and click OK.
Next, you need to change your Global Protect authentication to SAML; either for Portals or Gateways, or both.
In the left navigation, expand GlobalProtect and click Portals.
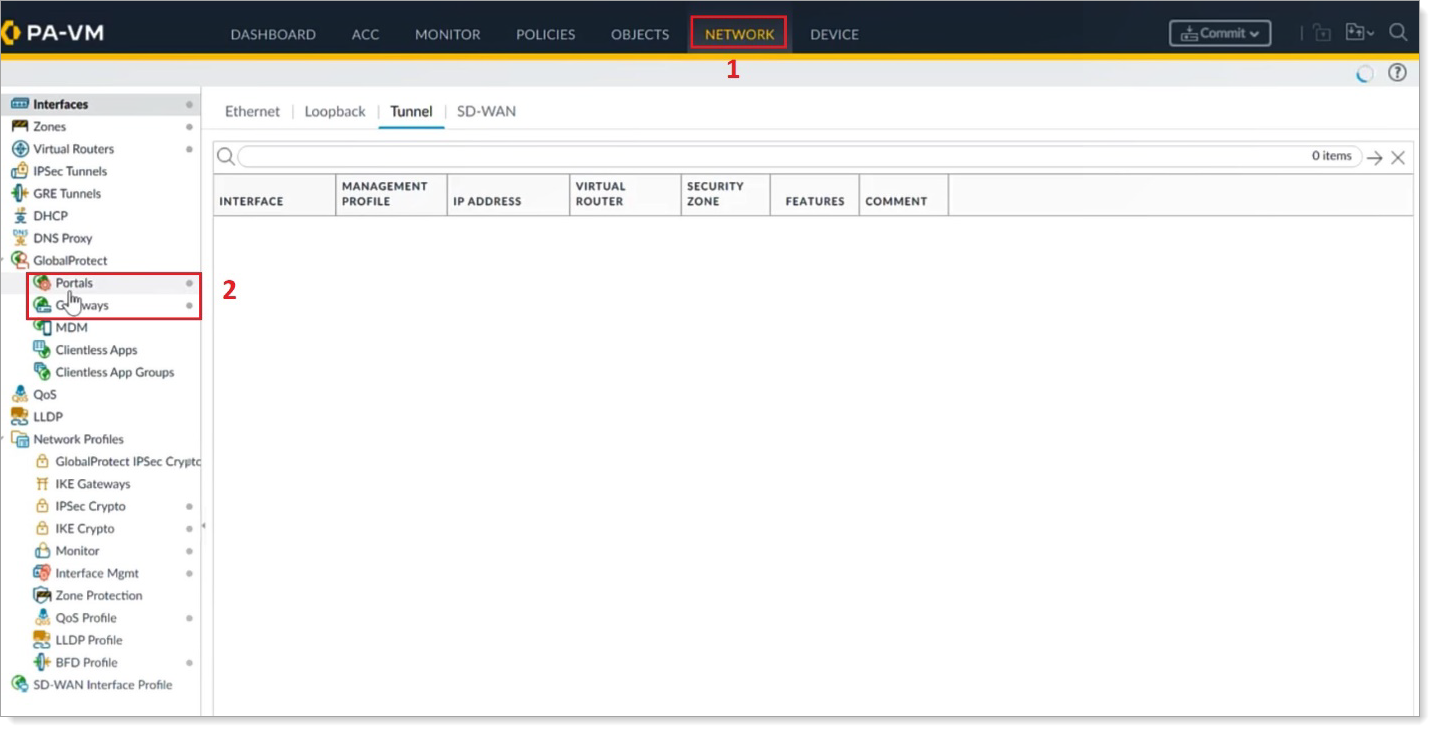
Select the portal you want to configure.
On the GlobalProtect Configuration page, to create a new client authentication, click Authentication.
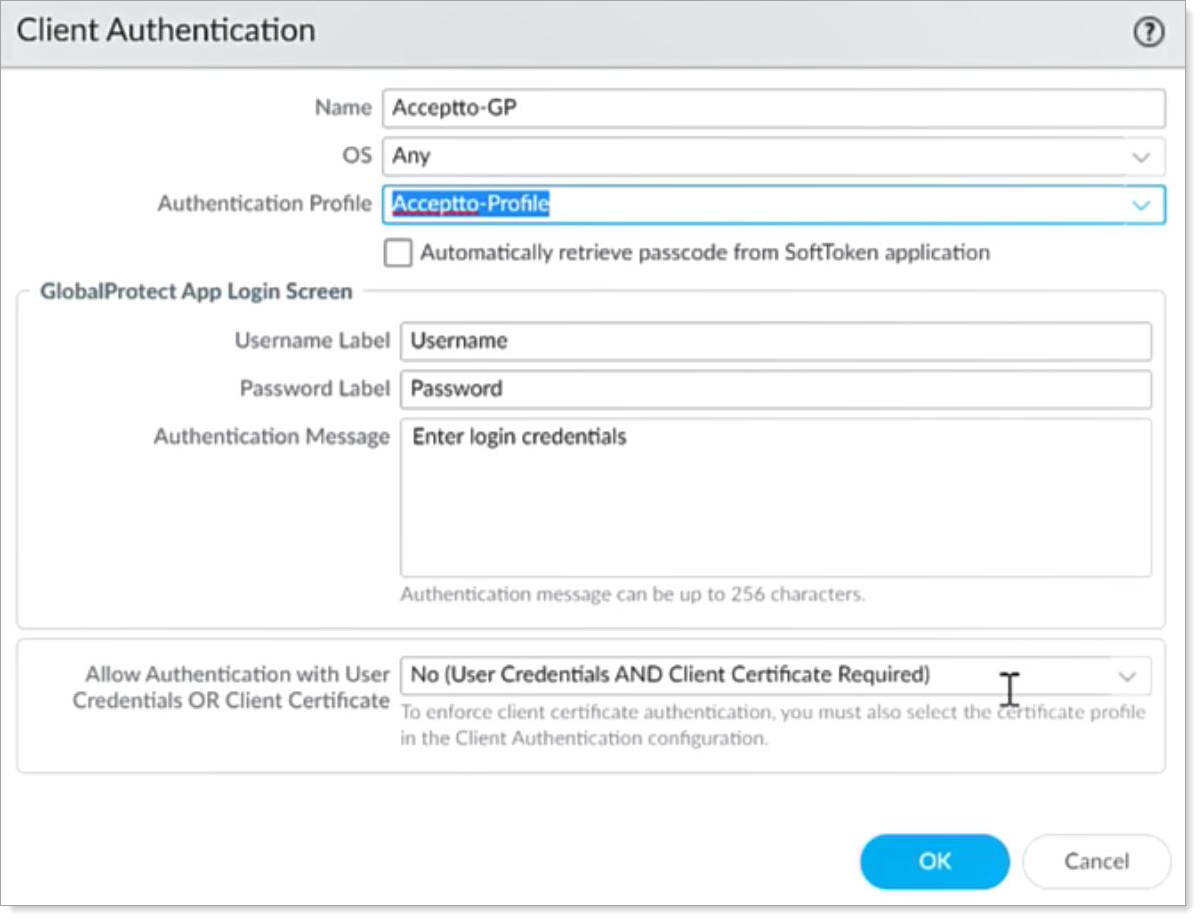
On the Client Authentication page, set the Name and select the Authentication Profile that you just created.
On the GlobalProtect Portal Configuration page, click Agent and select the agent to configure.
Select the App tab.
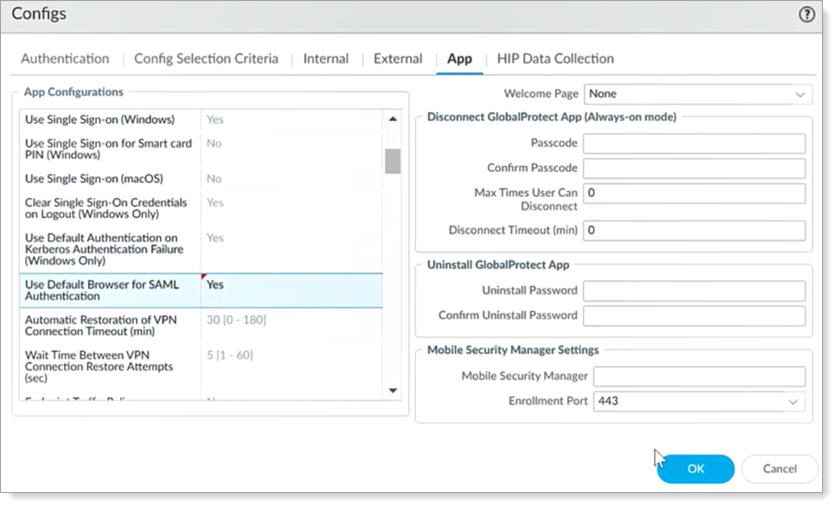
Find the App Configuration setting for Use Default Browser for SAML Authentication and set it to Yes.
The internal browser for the GlobalProtect VPN client does not support WebAuthn, so you will need to set this configuration if you want to use WebAuthn for authentication.
To change the Gateway authentication setting, go to Gateways and select the gateway to configure.
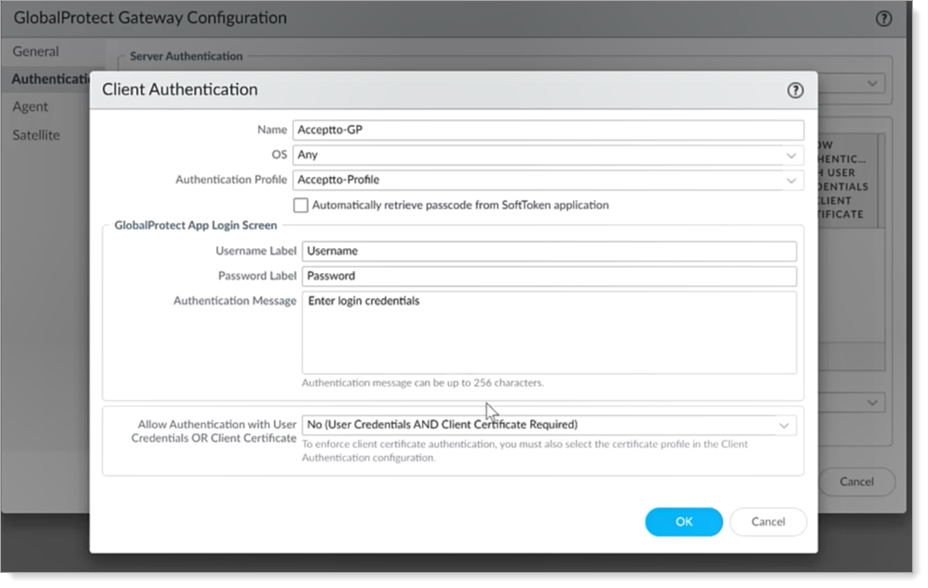
On the GlobalProtect Gateway Configuration page, click Authentication.
Create a Client Authentication for the gateway, just like you did in Step 10.
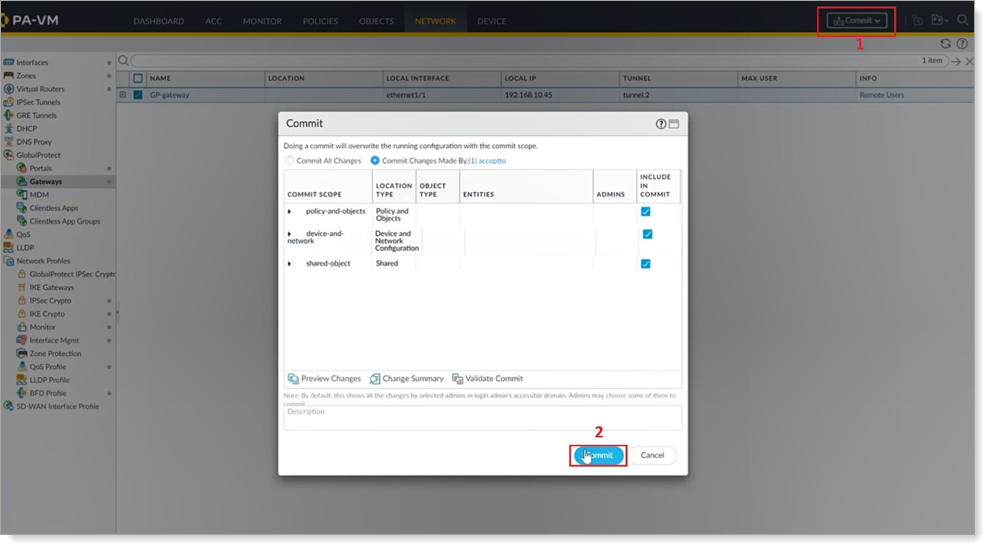
To check your configurations, click Commit. Verify your changes, and click Commit to apply your changes.
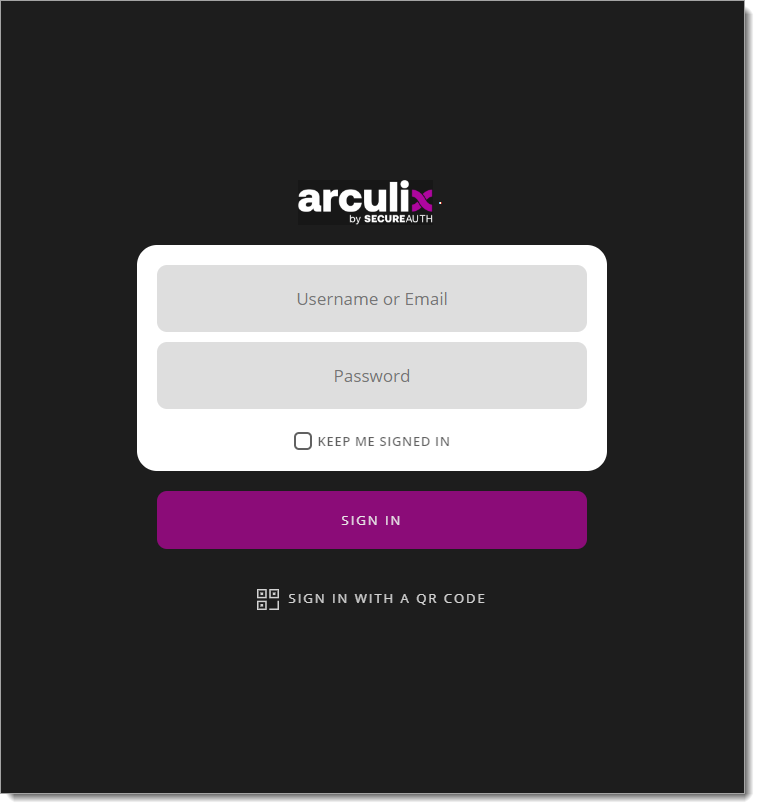
Test your set up
Add the Palo Alto GlobalProtect URL to your VPN or enter the URL in a browser.
You will be redirected to the Arculix SSO page.
After successful authentication, select your preferred MFA method to approve access to the Palo Alto GlobalProtect VPN.
Finally, it establishes your VPN connection.

Support
If you have questions or need assistance, contact SecureAuth Support.
Sales
Want to learn more about our MFA solutions? Contact our Professional Services for a demo today.
Disclaimer
All product names, trademarks, and registered trademarks are the property of their respective owners.
All company, product, and service names used in this document are for identification purposes only. The use of these names, trademarks, and brands do not constitute an endorsement by the SecureAuth Corporation.