Arculix Device Trust FAQ
- Why do we need to eliminate passwords?
- What is the passwordless workstation project?
- What are the benefits of passwordless workstations?
- Do I need a mobile device to participate?
- What if I don’t want to use my personal mobile device?
- Can I stick to passwords and still do desktop MFA?
- If I leave my machine unlocked, can I monitor and lock it remotely using my phone?
- What factors are available for Arculix desktop / workstation MFA?
- What if my phone is out of battery, not available, or misplaced?
- What if my workstation is offline?
- What if my workstation is online, but I don’t have my phone, YubiKey or biometrics (on Windows)?
- The offline TOTP mode doesn’t work.
- Can I pair more than one phone?
- Do I need to pair my device and my workstation every time I upgrade my phone or replace a lost phone?
- Can a user unlock the workstation through their phone via a discrete intent/gesture and eliminate the need for a push and approve?
- Can I respond to an Arculix push notification from a locked screen if my “show previews” notifications are enabled?
- How do I register my enterprise username and pair my phone
- How do I pair my workstation and mobile device? How does it all work?
- I received a “pair your device” email, but when I click on the universal link on my mobile device, it doesn’t work.
Why do we need to eliminate passwords? | |||||||
Passwords are a huge contributor to enterprise vulnerability. With their high cost and friction, they’re the sore point that continually creates problems. According to the Verizon DBIR 2020, a whopping 75%- 81% of data breaches over the last 5 years are due to vulnerabilities of binary authentication, such as passwords—even when combined with weak two-factor authentication (2FA) and certain multi-factor authentication (MFA). No one believes that they’re the next victim of breach, until they are. Passwordless workstation secure login is the first step to establishing root of trust and eliminating the vulnerabilities of passwords. | |||||||
What is the passwordless workstation project? | |||||||
Passwordless workstation is a secure login for Windows 10 and Mac workstations that uses an intelligent multi-factor authentication and is the first step to establish root of trust to elevate platform security. | |||||||
What are the benefits of passwordless workstations? | |||||||
Combining the OS credential providers with an intelligent multi-factor authentication (MFA) makes passwords benign for both Windows 10 and Mac OS platforms. The benefits include:
| |||||||
Do I need a mobile device to participate? | |||||||
Yes, you need a mobile device in order to pair your workstation and websites (where applicable) to the Arculix Mobile app. | |||||||
What if I don’t want to use my personal mobile device? | |||||||
You will lose the convenience and safety of a risk-based authentication system. | |||||||
Can I stick to passwords and still do desktop MFA? | |||||||
No. The purpose of passwordless intelligent MFA is to eliminate passwords and their vulnerabilities. That said, enterprise IT has the option to enable various first factors, including passwords/passphrases. | |||||||
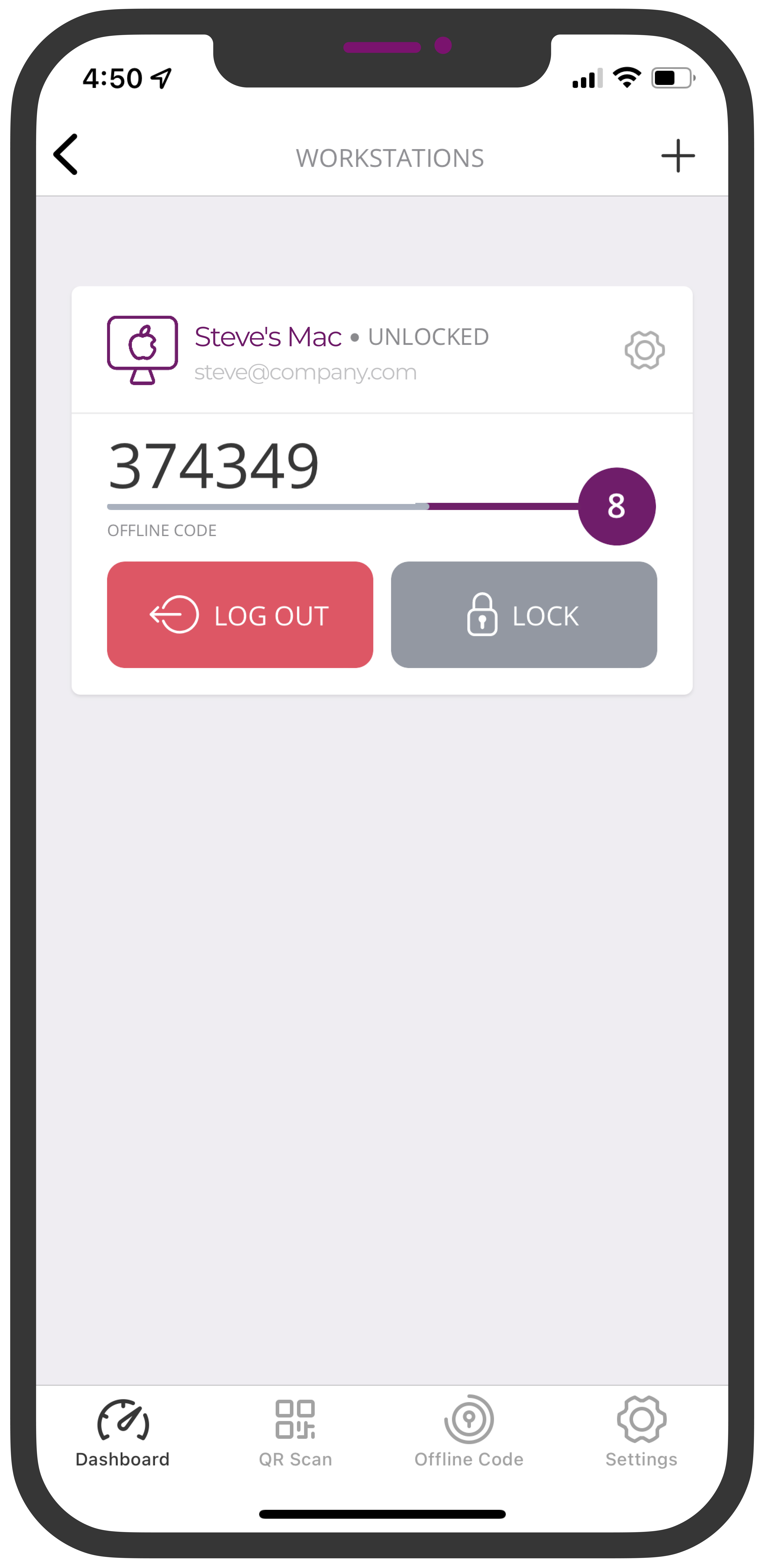
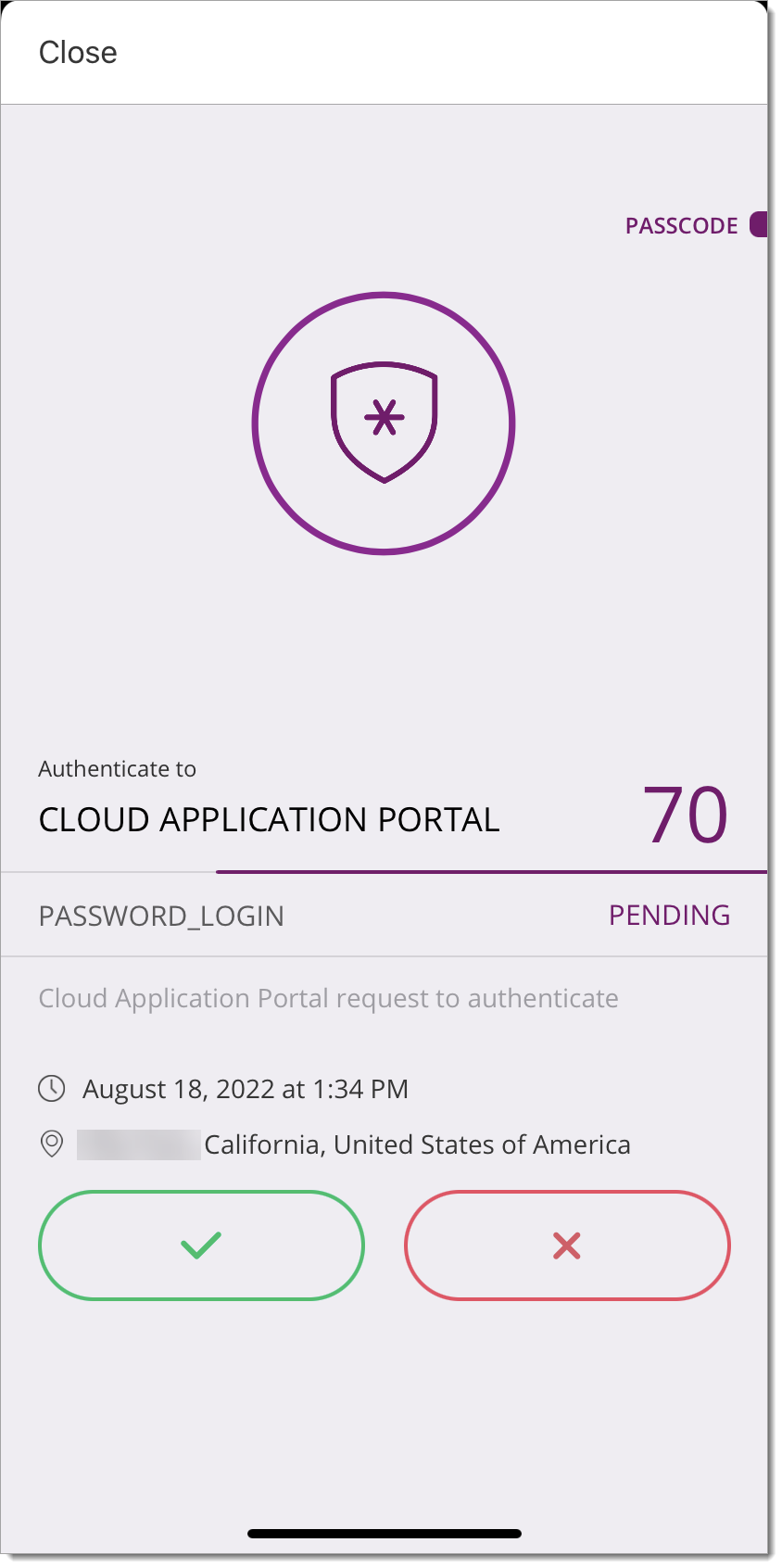
If I leave my machine unlocked, can I monitor and lock it remotely using my phone? | |||||||
Using Arculix Mobile app, you can lock your machine remotely. Navigate to the Workstations tab, then select your workstation and click on “Lock”.
| |||||||
What factors are available for Arculix desktop / workstation MFA? | |||||||
| |||||||
What if my phone is out of battery, not available, or misplaced? | |||||||
Other offline authenticators such as Windows Hello biometrics and FIDO authenticators (like YubiKey) can be provisioned for offline support. In certain instances, enterprise IT might enable password/passphrase factors. | |||||||
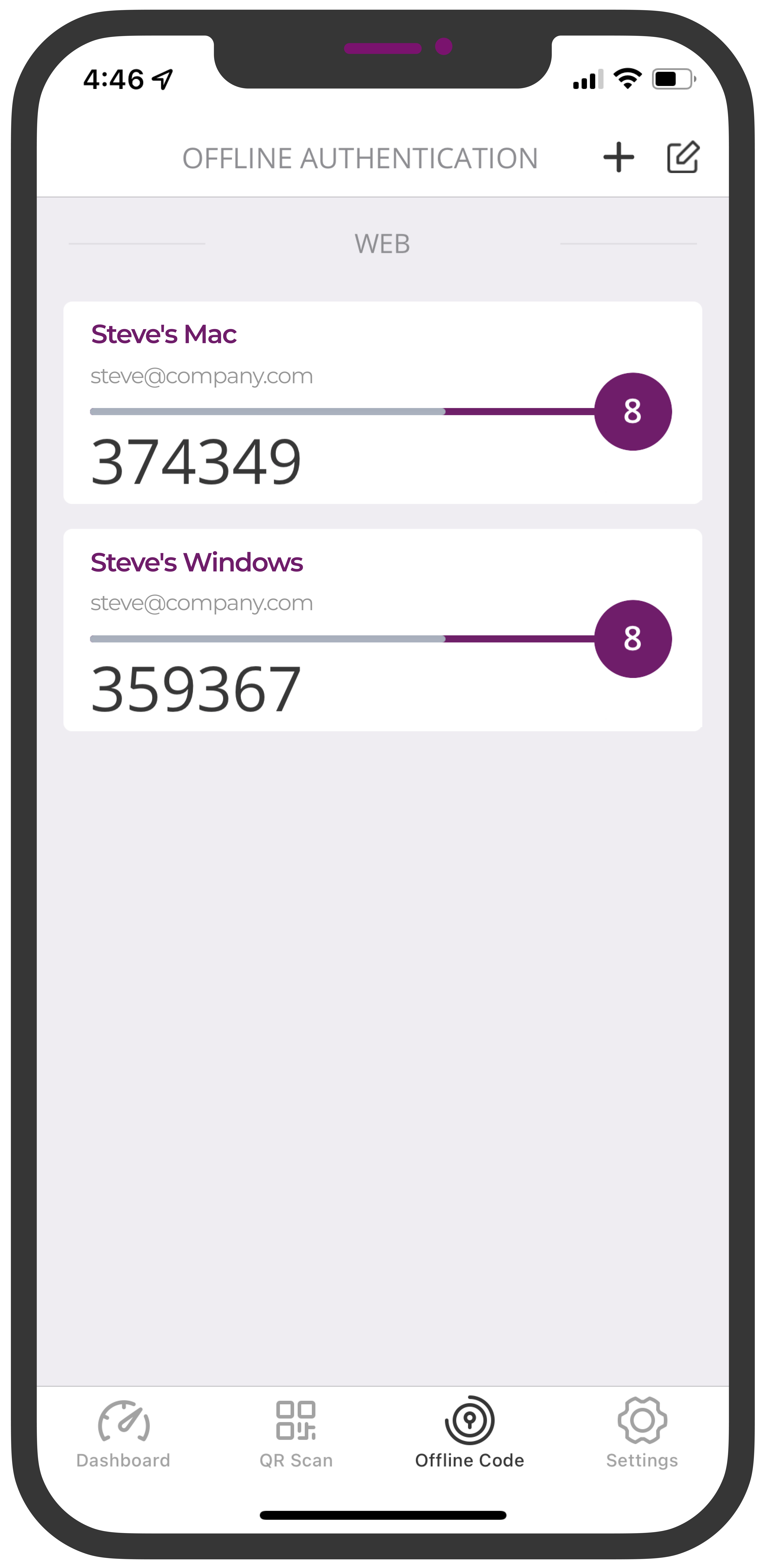
What if my workstation is offline? | |||||||
If you’re offline, you can log in to your machine using the Offline TOTP feature. On the Arculix Mobile app, go to the Workstations tab and enter the 6-digit TOTP code to log in. Other offline authenticators such as biometrics and YubiKey can be provisioned for offline support. | |||||||
What if my workstation is online, but I don’t have my phone, YubiKey or biometrics (on Windows)? | |||||||
Contact the help desk to unlock your workstation. | |||||||
The offline TOTP mode doesn’t work. | |||||||
There are a few reasons why your TOTP might not work:
| |||||||
Can I pair more than one phone? | |||||||
Yes, multiple pairings are allowed. Note that the first device and proof of identity on claimed identity are required to pair additional mobile devices. For security reasons, the offline TOTP on secondary device(s) is not automatic and requires manual pairing. This implies that upon replacing devices (lost or stolen device, upgrades) offline TOTP is lost, which puts offline authentication at risk. The unpair-pair procedure of secondary devices needs to be carefully understood by enterprise for this reason. | |||||||
Do I need to pair my device and my workstation every time I upgrade my phone or replace a lost phone? | |||||||
Arculix Mobile will retain any workstations you currently have when you upgrade or replace your mobile device. However, TOTPs are stored on the device for security reasons; therefore, when you view your workstation in Arculix Mobile on your new device, you will not see a TOTP. Use the ‘Add Offline Authenticator’ feature on the MFA dialog to add a new TOTP code on your new device. | |||||||
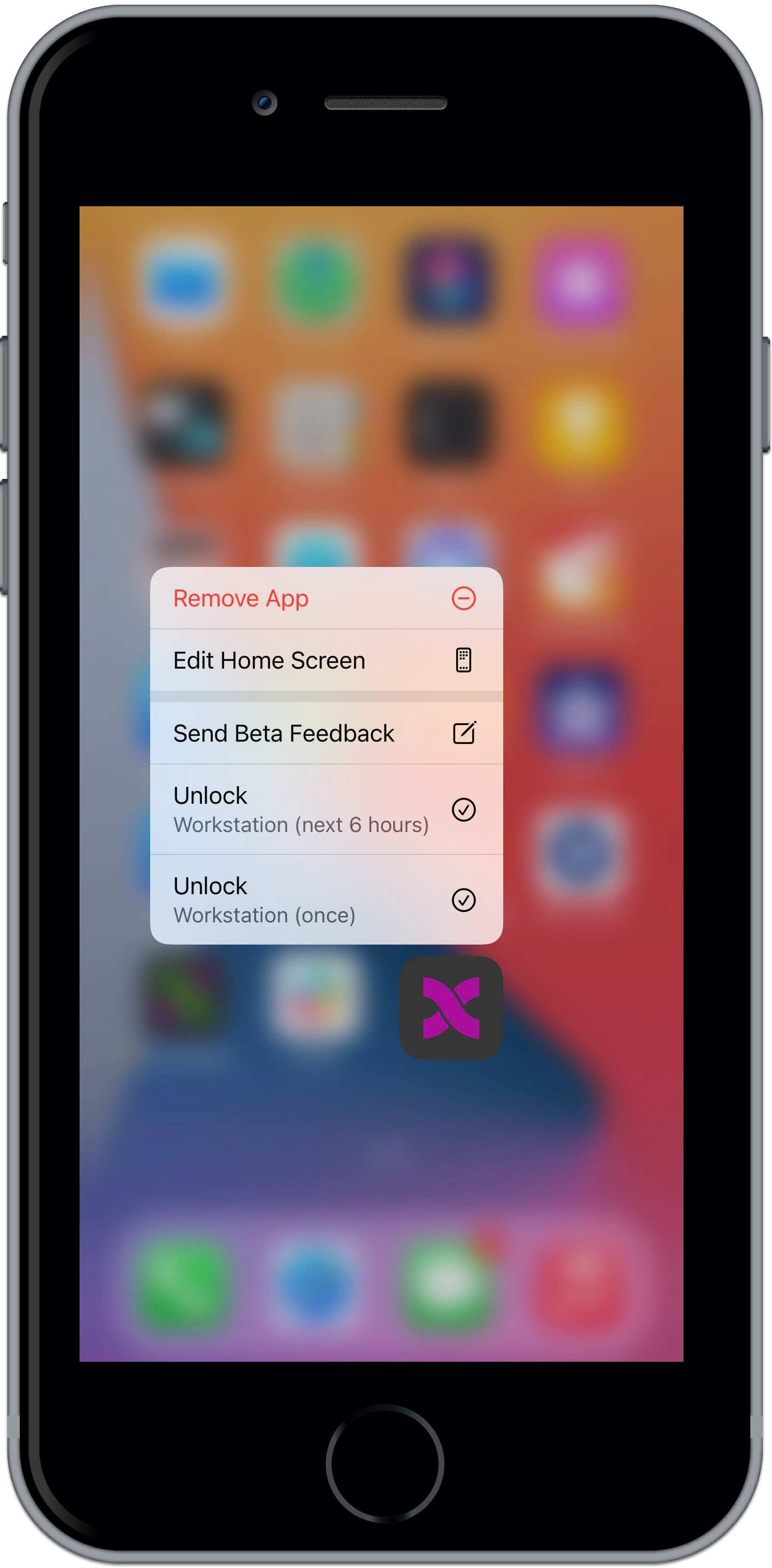
Can a user unlock the workstation through their phone via a discrete intent/gesture and eliminate the need for a push and approve? | |||||||
On the screen of your mobile device, press and hold the Arculix Mobile icon to reveal a list of options. Tap the Unlock Workstation option. This means that it will automatically accept the next workstation authentication for your account.
| |||||||
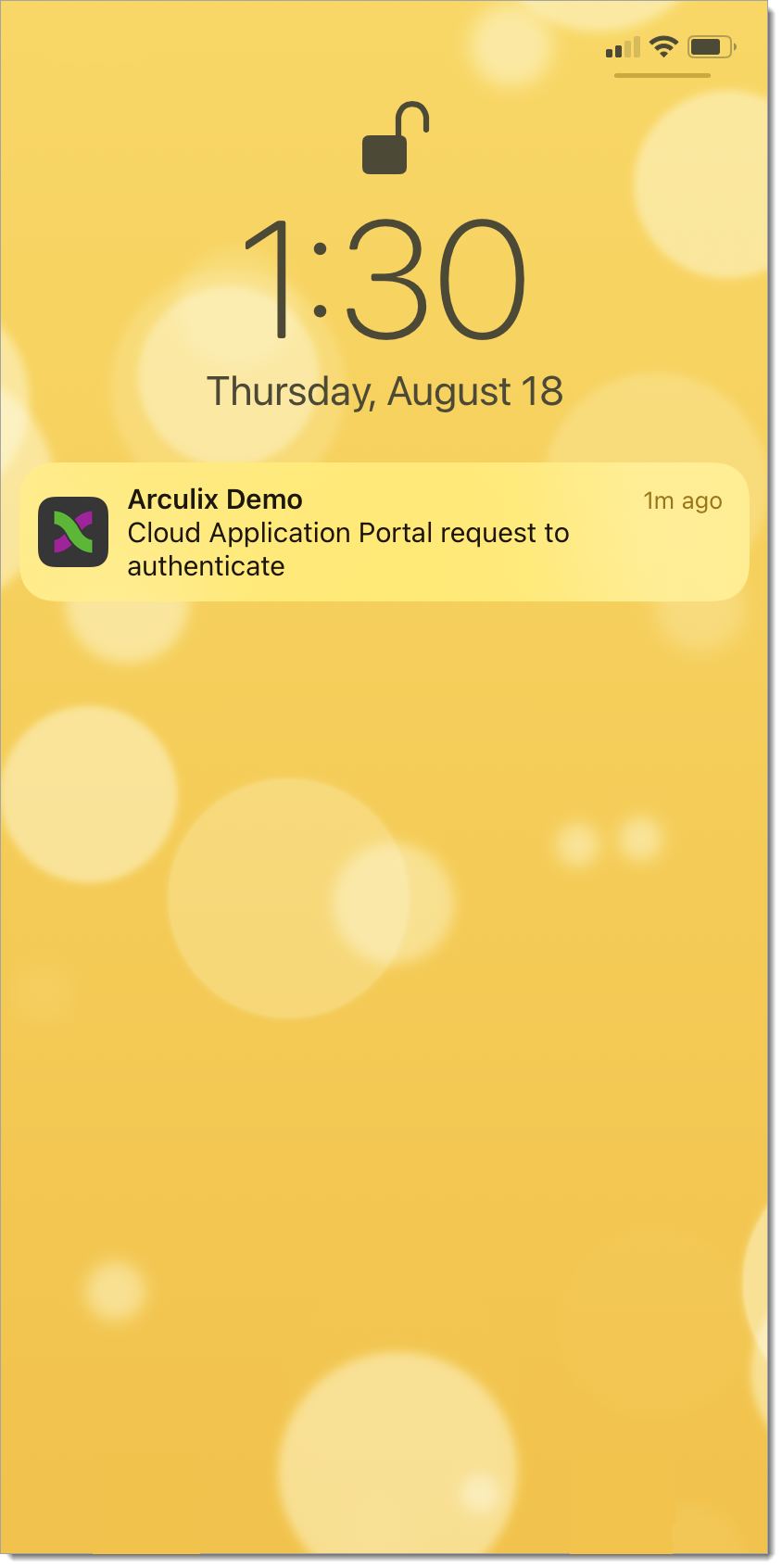
Can I respond to an Arculix push notification from a locked screen if my “show previews” notifications are enabled? | |||||||
Yes, with “show previews” enabled on your device, it is possible to respond to a push notification from the locked screen. From the locked screen, tap on the preview notification and select “Accept”. This will be followed by a biometric gesture (Face or Touch ID) to approve authentication. If this authentication method is not verified, it will then ask for the next failsafe method, e.g. a passcode.
| |||||||
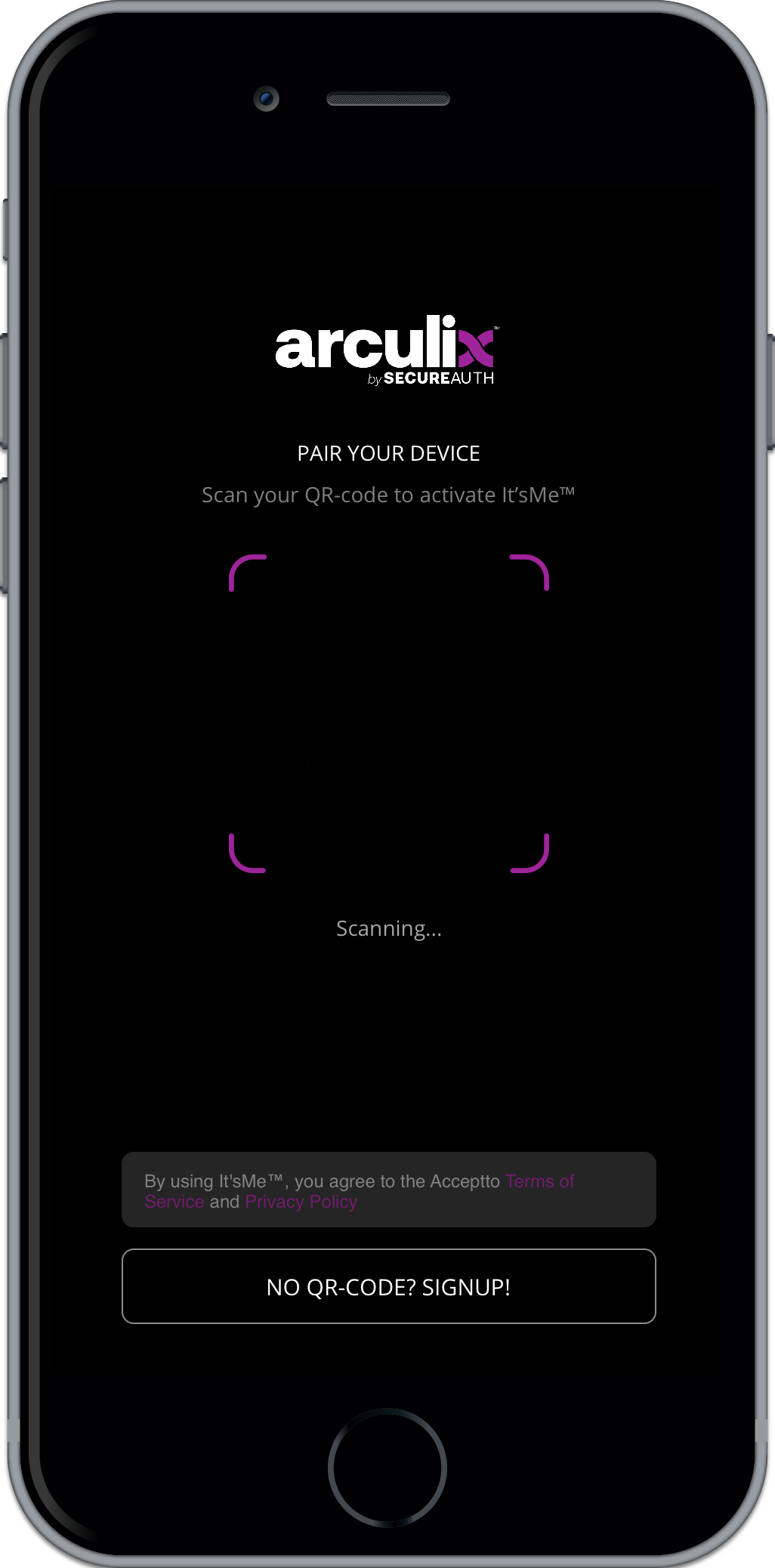
How do I register my enterprise username and pair my phone | |||||||
Before Arculix Mobile can be used, it must be paired with Arculix. After installing and opening the app for the first time, you will see the pairing screen. From this this screen there are two ways to pair:
For fast pairing on your mobile device, click on universal link icon in the received “Pair your device” email.
However, there is a known Apple issue with universal links. If you encounter this iOS bug, you can scan the QR code from the Workstation “Pair your device” email. | |||||||
How do I pair my workstation and mobile device? How does it all work? | |||||||
The video below explains how the pairing process as well as different authentication factors for online and offline access work. | |||||||
I received a “pair your device” email, but when I click on the universal link on my mobile device, it doesn’t work. | |||||||
There is a known Apple issue with Universal Links not working properly on mobile devices. Read more here. You can open the email on your workstation and then scan the pairing QR code that is within the body of the email to pair Arculix Mobile. |