Active Directory - New and Classic Web Admin
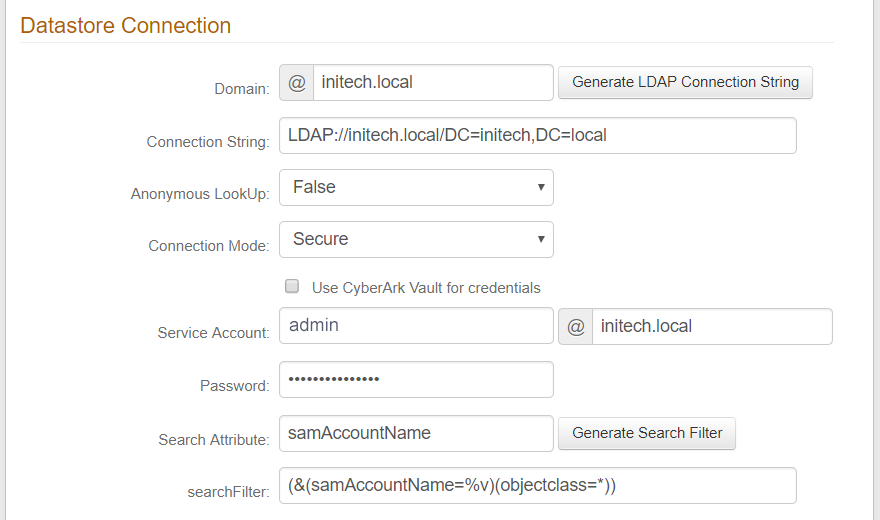
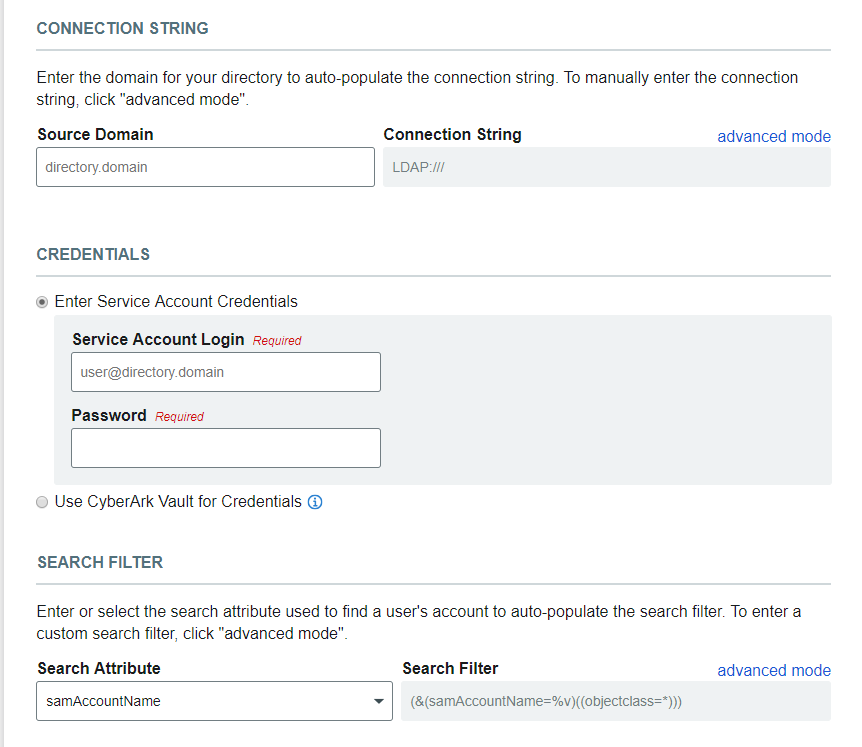
Connection String
Create the LDAP Connection String to let SecureAuth IdP communicate with the data store.
Either enter the Source Domain and auto-generate the string, or click advanced mode and customize the content of the string.
Credentials
Select the option SecureAuth IdP will use to log on the connected data store.
Either enter the Service Account email address and Password for SecureAuth IdP to use, or provide account information from an integrated CyberArk Password Vault that stores this service account information.
Search Filter
Specify the type of search SecureAuth IdP will perform to find the end-user's account information in the data store.
Either select the Search Attribute and then auto-generate the Search Filter, or click advanced mode and customize the content of the search filter syntax.
 |
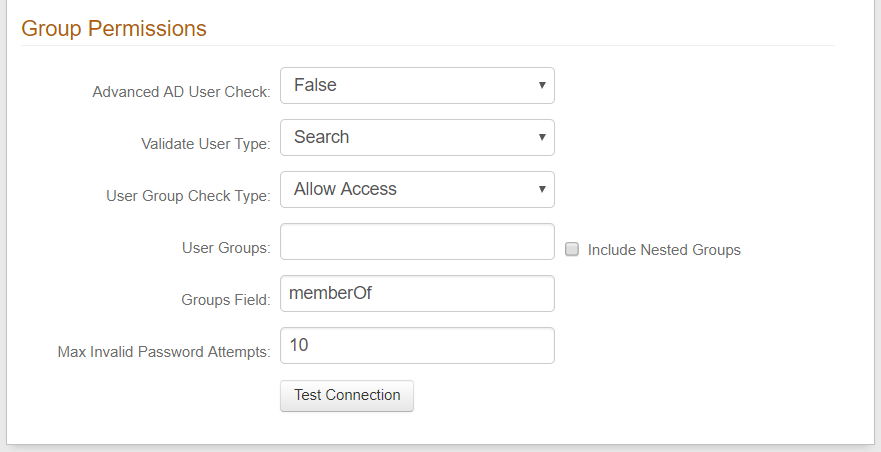
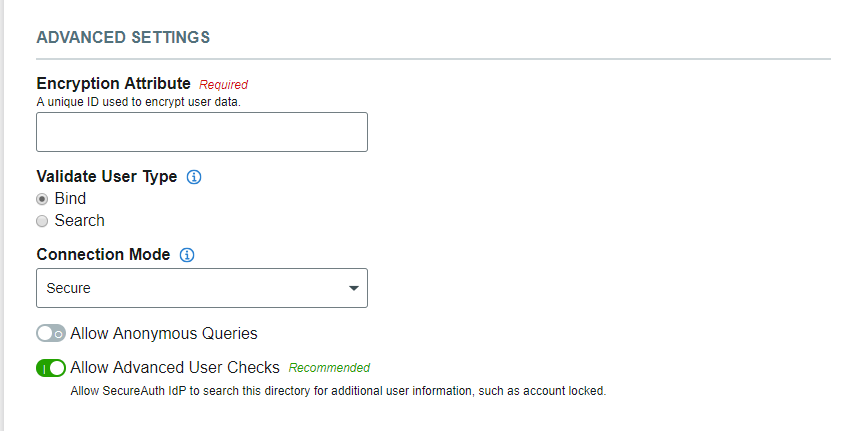
Advanced Settings
Specify the Encryption Attribute – a unique value from the data store – that SecureAuth IdP will use to encrypt user profile data. For example: sAMAccountName.
Specify the Validate User Type option SecureAuth IdP will use to get the username and password: Bind to let SecureAuth IdP make a direct call to the directory, or Search to let SecureAuth IdP search the data store.
Select the Connection Mode SecureAuth IdP will use to access the data store: Secure, SSL, or Standard.
If using a generic LDAP directory, you can Allow Anonymous Queries to let non-authenticated users access protected resources.
For cases when a user's account is locked, having Allow Advanced User Checks enabled lets SecureAuth IdP check the data store for more than just the username.
 |
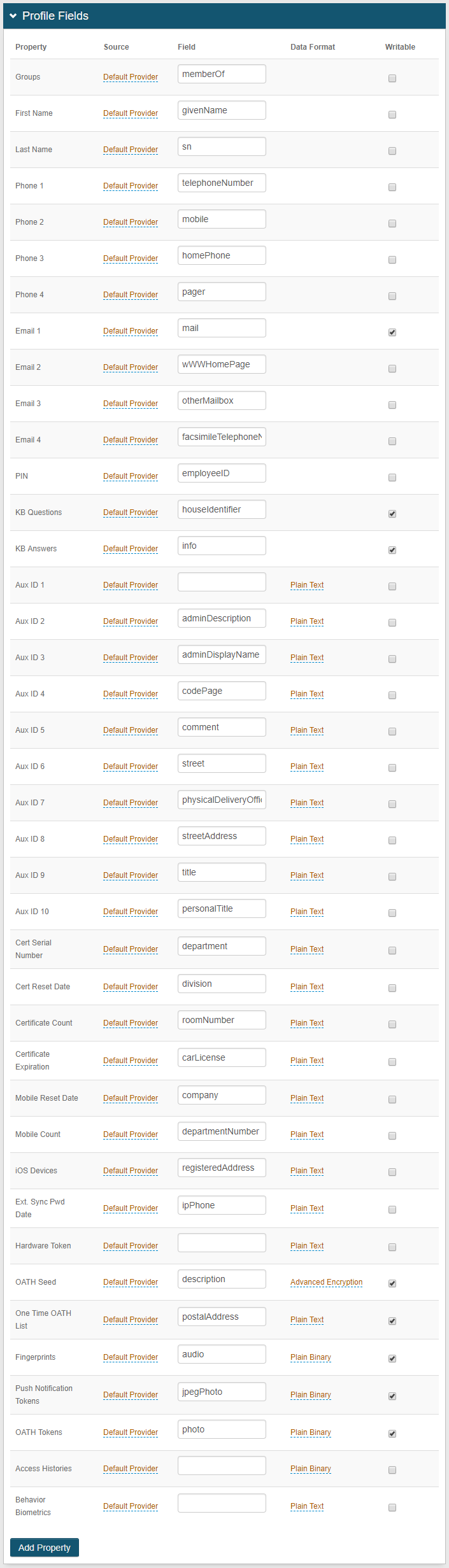
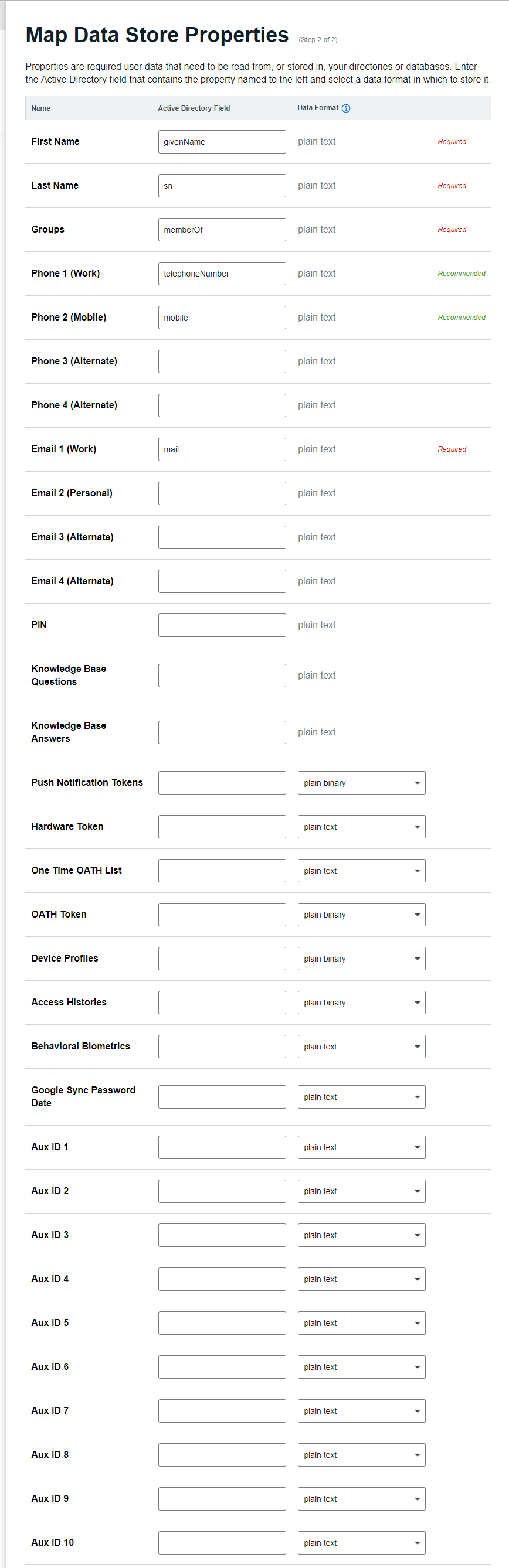
Map Data Store Properties
In the New Experience, there are some required and some recommended entries for mapping fields in Active Directory to data store properties:
Required: First Name, Last Name, Groups, Email 1 (Work).
Recommended: Phone 1 (Work), Phone 2 (Mobile).
 |
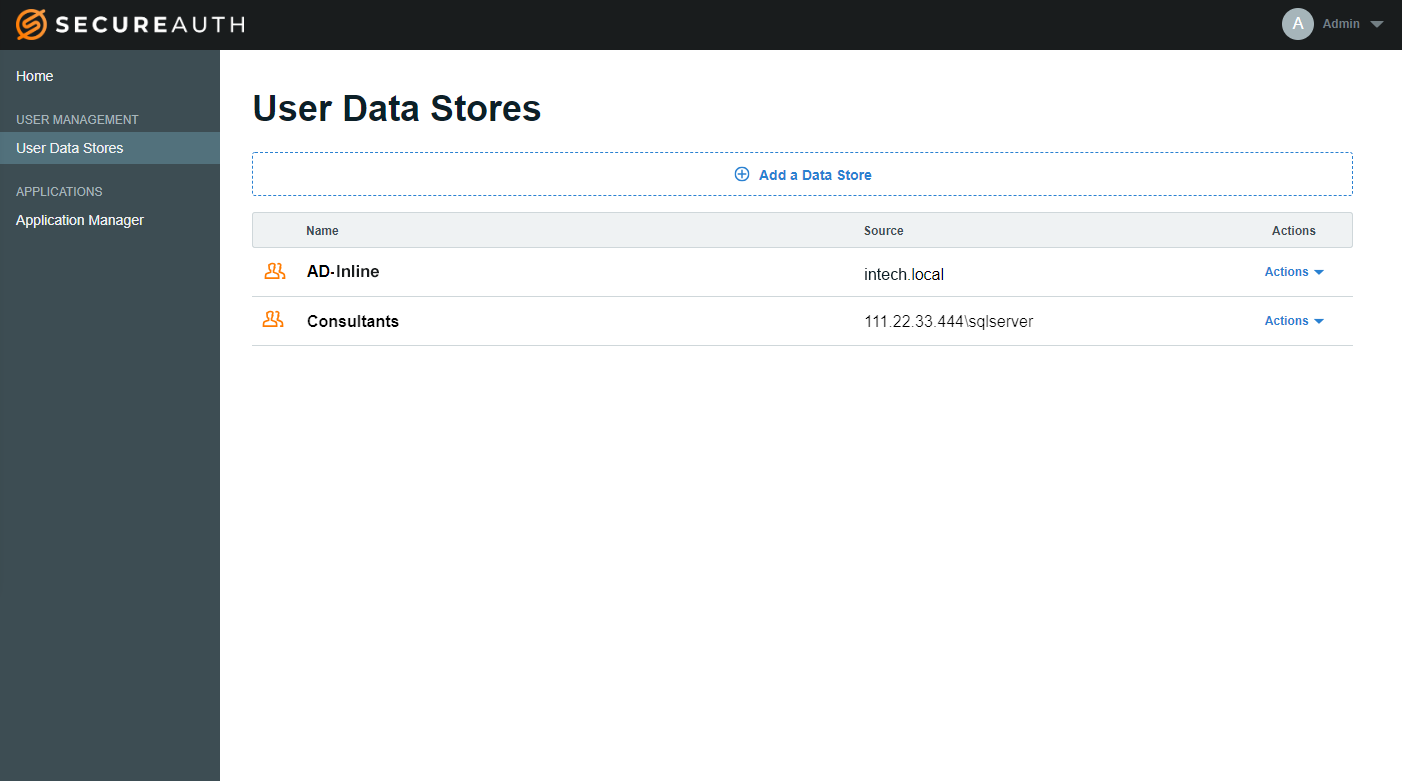
Save the configuration
Click Save.
The added data store appears on the User Data Stores list.
 |