Is SecureAuth IdP Impacted by the DROWN Attack?
Issue
This article discusses the DROWN Attack and its impact on SecureAuth IdP appliances.
Background
Security researchers have discovered that SSLv2 is vulnerable to theBleichenbacher RSA padding attack which aims to decrypt RSA cipher text without knowledge of the matching private RSA key. During the attack, responses from a server which has a private key are observed, and then the private key is used to decrypt attacker-provided cipher texts. Researchers also discovered a new cross-protocol attack that exploits the SSLv2 weakness by decrypting SSL/TLS sessions which use the newer SSLv3 protocol or any version of TLS. This flaw is an SSLv2 protocol issue and affects all implementations of the protocol.
Impact to SecureAuth IdP Customers
Use the table below to determine whether the SecureAuth IdP appliance is affected based on its status
SecureAuth IdP Version | Appliance OS Version | Status |
|---|---|---|
6.x+ (see Disclaimer) | Windows Server 2012 R2 | SSLv2 is disabled by default 1 |
Windows Server 2012 | SSLv2 is disabled by default 1 | |
Windows Server 2008 R2 | SSLv2 is disabled by default 1 | |
Windows Server 2008 | Possibly impacted 2 | |
Windows Server 2003 | Impacted and not supported 3 |
1These appliances are only affected if SSLv2 was manually enabled after delivery (not recommended).
2 Some appliances from this generation may be impacted. See the section How to Disable SSLv2 for steps on disabling SSLv2 to mitigate this issue.
3 For customers using SecureAuth IdP appliances running on Windows Server® 2003, this operating system is no longer supported by Microsoft® as of July 2015. SecureAuth strongly recommends upgrading appliances to the latest version of the product and Microsoft Windows Server® version. This upgrade is complimentary to customers with a current SecureAuth support contract. Contact SecureAuth Support to speak with a support representative about the upgrade process.
Notice
Disclaimer
SecureAuth applies the latest Microsoft security updates on all SecureAuth IdP appliances before shipment
NOTE: Any SecureAuth IdP appliance out in the field before the occurrence of this vulnerability may be affected if the security update referenced in this article has not yet been applied at the user's site
This note also pertains to SecureAuth IdP appliances out in the field that have been upgraded to the latest SecureAuth IdP software release version at the user's site
Recommendations
To protect the SecureAuth IdP appliance environment from the DROWN Attack, review the recommendations below.
1. The SSL Binding certificate used to protect SecureAuth IdP appliances should be dedicated only to that environment and not be used for other servers. If this is not possible, ensure the certificate is NOT used on servers where SSLv2 is enabled since this would open the SecureAuth IdP environment to the DROWN Attack.
2. SecureAuth IdP appliances ship with hardening to protect appliances against attacks. During the hardening process, SSLv2 is disabled since it is now considered insecure. Thus, SSLv2 should NOT be enabled since this would result in decreased security which would allow for a DROWN Attack to be used against the appliance.
How to Disable SSLv2
Warning
Before disabling SSL 2.0 on SecureAuth appliances, perform an audit of the network to ensure no devices that communicate with the SecureAuth IdP appliance require SSL 2.0. If any device has a dependency on SSL 2.0 and the protocol is removed from the appliance, communication will no longer be possible and may potentially result in downtime for users.
Warning
These instructions explain how to modify the Windows registry. However, serious problems may occur if the registry is modified incorrectly. Therefore, be sure to follow these instructions carefully.
For added protection, back up the registry before proceeding with the instructions below. The registry can then be restored if a problem occurs.
For more information about how to back up and restore the registry, see the Microsoft Knowledge Base article How to back up and restore the registry in Windows.
Some SecureAuth IdP appliances running Windows Server 2008 might be impacted by the DROWN Attack. The instructions below explain how to disable SSLv2 on the appliance to mitigate the attack.
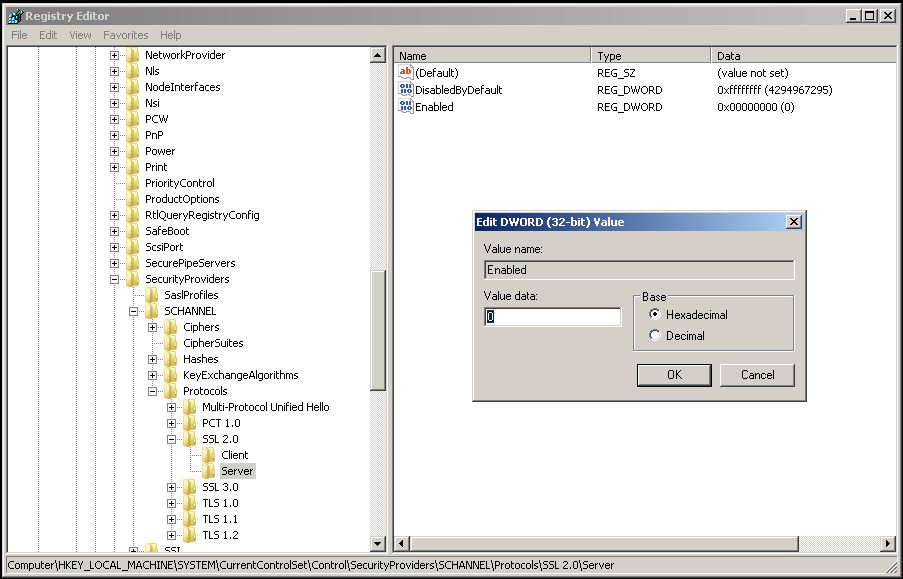
1. Open the Registry Editor
a. Click Start, and then click Run
b. Type Regedit, and then click OK
2. Edit the Registry
a. In the Registry Editor, locate the following key:HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0
b. Locate the Server key
c. In the Server key, set the Enabled DWORD to 0 (zero)
 |