Edcor (IdP-initiated) Integration Guide
Introduction
Use this guide to enable Multi-Factor Authentication and Single Sign-on (SSO) access via SAML to Edcor.
Prerequisites
1. Receive a SSO Partner Agreement document from Edcor that includes:
SP Connection ID, which is the SAML Audience value for SecureAuth IdP
RelayState (Target URL), which is the SAML Target URL for SecureAuth IdP
ACS URL (if using port 443), which is the SAML Consumer URL and SAML Recipient for SecureAuth IdP
2. Create a New Realm on the SecureAuth IdP Web Admin for the Edcor integration
3. Configure the following tabs in the Web Admin before configuring the Post Authentication tab:
Overview – the description of the realm and SMTP connections must be defined
Data – an enterprise directory must be integrated with SecureAuth IdP
Workflow – the way in which users will access this application must be defined
Multi-Factor Methods – the Multi-Factor Authentication methods that will be used to access this page (if any) must be defined
SecureAuth IdP Configuration Steps
Data
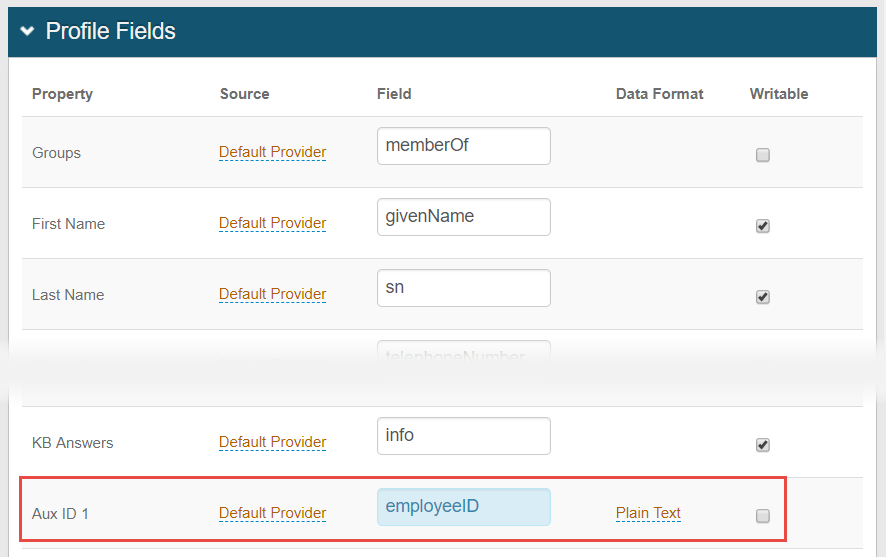 |
1. In the Profile Fields section, map the directory Field containing the user employeeID attribute to the SecureAuth IdP Property
In this example, employeeID is mapped to the AUX ID 1 Property
Notice
NOTE: This integration uses Active Directory as the Enterprise Directory integrated with SecureAuth IdP
The saml:NameID value in the saml:Subject of the SAML assertion which SecureAuth IdP generates is the only attribute Edcor uses to authenticate the user
Therefore the NameID value should be the Employee ID
However, if the Employee ID cannot be passed to Edcor, the Email Address can be passed for the NameID instead
Warning
Click Save once the configurations have been completed and before leaving the Data page to avoid losing changes
Post Authentication
Post Authentication
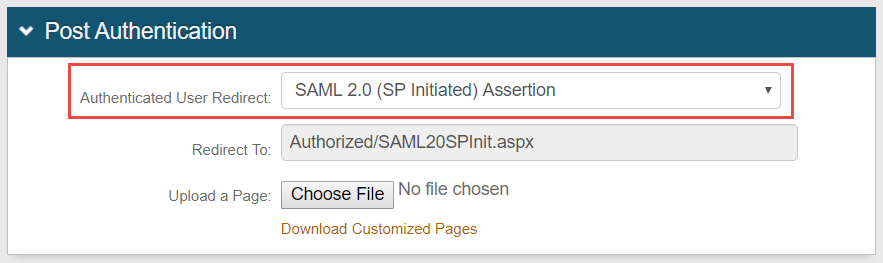 |
2. Select SAML 2.0 (IdP Initiated) Assertion from the Authenticated User Redirect dropdown
The unalterable URL (Authorized/SAML20IdPInit.aspx) which auto-populates the Redirect To field appends to the domain name and realm number in the address bar
User ID Mapping
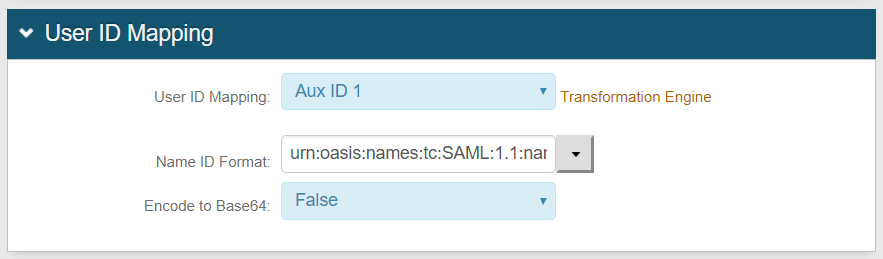 |
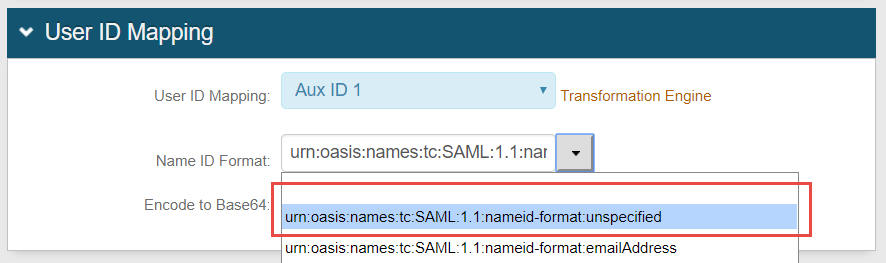
3. Select the SecureAuth IdP Property corresponding to the employeeID attribute from the User ID Mapping dropdown – i.e. Aux ID 1, in this example
4. Select urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified from the Name ID Format dropdown (default)
5. Set Encode to Base64 to False(default)
SAML Assertion / WS Federation
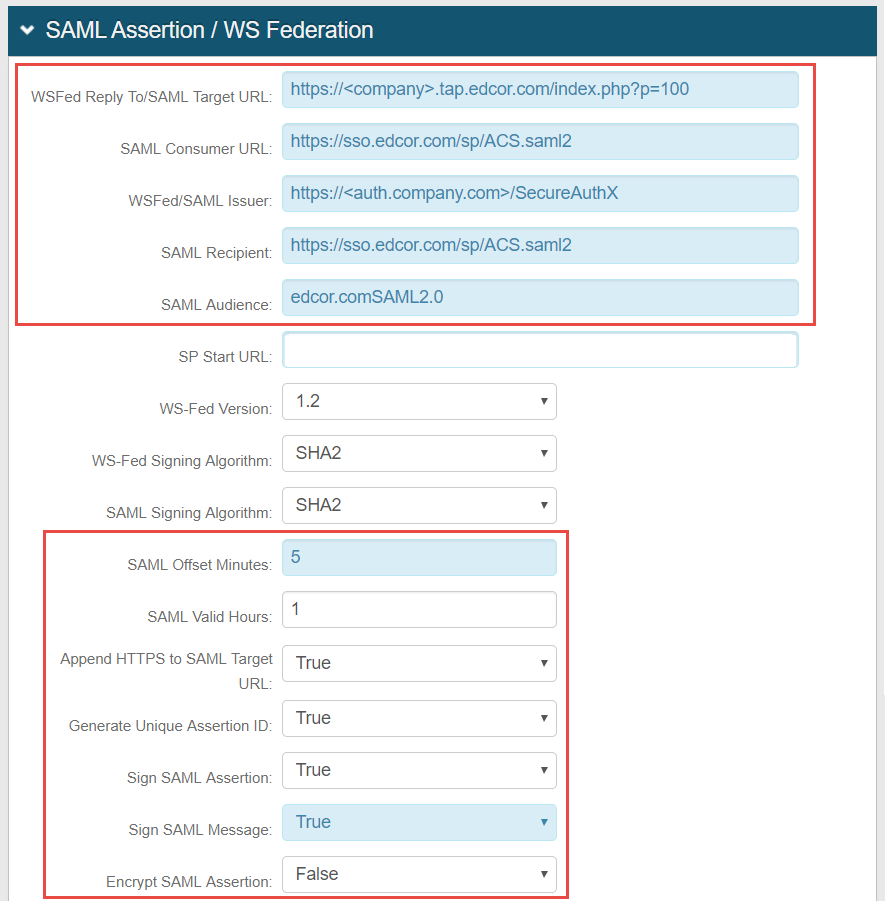 |
6. Set WSFed Reply To / SAML Target URL to the Fully Qualified Domain Name of the Edcor service as provided in the SSO Partner Agreement document from Edcor
e.g. https://<company>.tap.edcor.com/index.php?p=100, in which <company> is the company name
7. Set SAML Consumer URL to the value provided in the SSO Partner Agreement document from Edcor
e.g. https://sso.edcor.com/sp/ACS.saml2
8. Set WSFed / SAML Issuer to the Fully Qualified Domain Name of the SecureAuth IdP server and the corresponding realm on which this integration is configured
e.g. https://< auth.company.com>/SecureAuthX – in which <auth.company.com> is the FQDN of the SecureAuth IdP server and SecureAuthX is the realm on which this integration is configured
9. Set SAML Recipient to the value provided in the SSO Partner Agreement document from Edcor
e.g. https://sso.edcor.com/sp/ACS.saml2
10. Set SAML Audience to the value provided in the SSO Partner Agreement document from Edcor
e.g. edcor.comSAML2.0
11. Set SAML Offset Minutes to 5
12. Set SAML Valid Hours to 1
13. Set Append HTTPS to SAML Target URL to True (default)
14. Set Generate Unique Assertion ID to True (default)
15. Set Sign SAML Assertion to True
16. Set Sign SAML Message to True (default)
17. Set Encrypt SAML Assertion to False (default)
Warning
Click Save once the configurations have been completed and before leaving the Post Authentication page to avoid losing changes