ASPNETDB Configuration Guide
Use this guide along with the Data Tab Configuration guide to configure an ASPNETDB-integrated SecureAuth IdP realm.
Prerequisites
Have an on-premises ASPNETDB data store
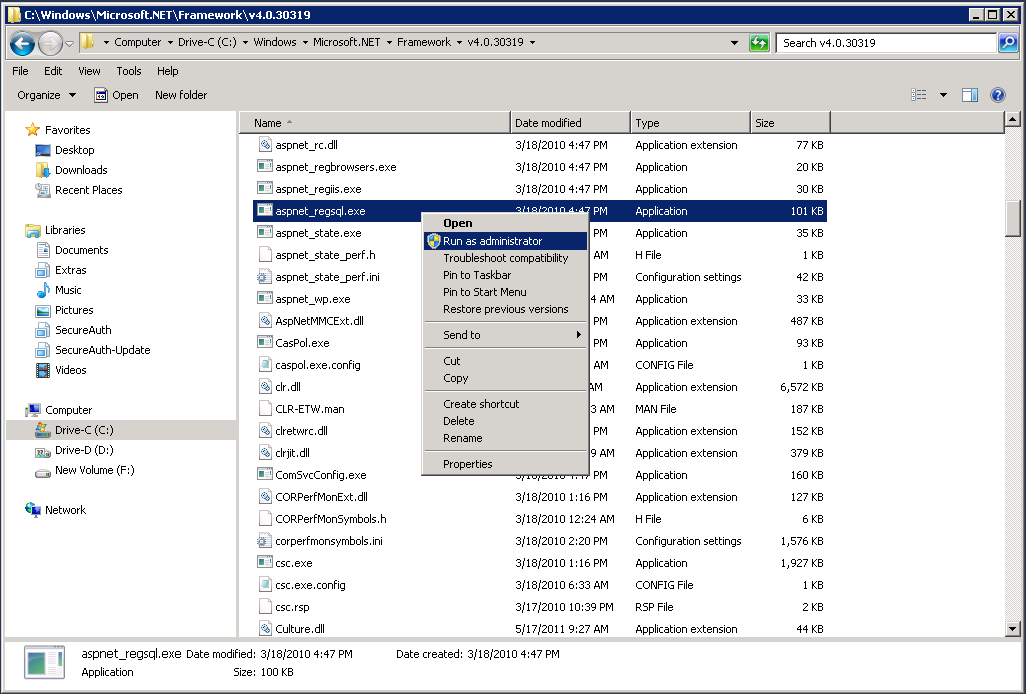
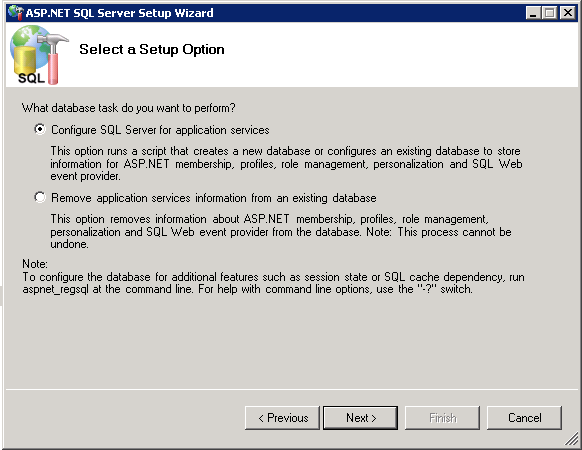
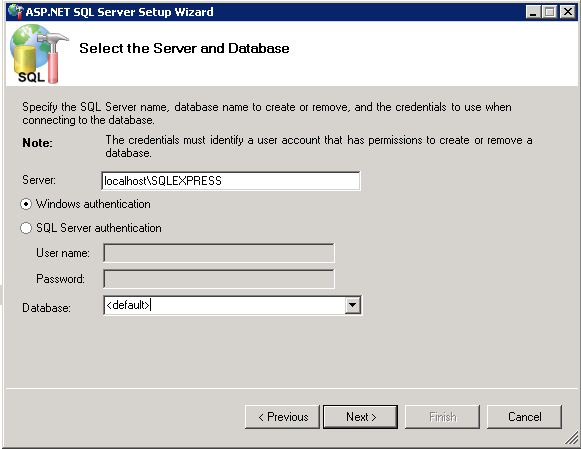
To create an ASP.NET database, see ASP.NET database configuration.
Designate a service account with read access (and optional write access) for SecureAuth IdP
ASP.NET database configuration
SecureAuth IdP configuration
The configuration settings are in the Advanced Settings (formerly Classic Experience).
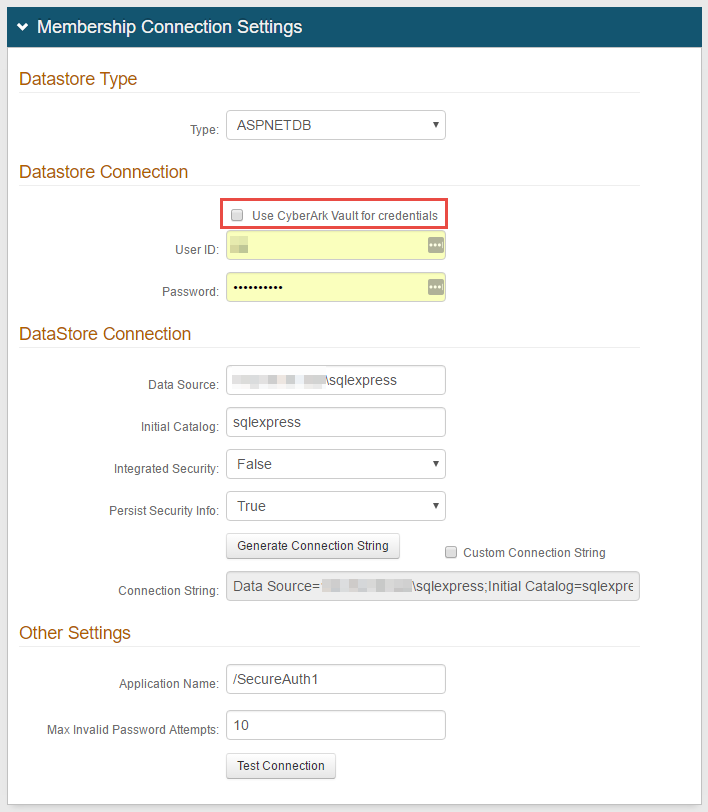
On the Data tab, in the Membership Connection Settings section, set the following configurations: set the Type to ASPNETDB.
Datastore Type
Type
Set to ASPNETDB.
Datastore Connection/Credentials
Use CyberArk Vault for credentials
If you select this check box, follow the steps in CyberArk Password Vault Server and AIM Integration with SecureAuth IdP.
With this feature, you do not need to fill out the User ID and Password fields for the data store credentials.
User ID
User ID for the SecureAuth IdP service account.
Password
Password associated with the User ID.
DataStore Connection
Data Source
Provide the Fully Qualified Domain Name (FQDN) or the IP Address.
Initial Catalog
Set the database name.
Integrated Security
Set to one of the following values:
True – Use this if the IIS app pool's service account is to be used in the connection (see Integrated Auth Requirements below)
False – Use this if you want to specify a SQL service account.
Persist Security Info
Set to True to allow access to the username and password information.
Generate Connection String
Click Generate Connection String, to autopopulate the Connection String field.
Other Settings
Application Name
Provide the Application Name set in ASP.NET database configuration in Step 15.
For example, /SecureAuth.
Max Invalid Password Attempts
Set the number of maximum invalid password attempts before locking the user's account.
For example, 10
Test Connection
Click Test Connection to ensure that the connection is successful.
Tip
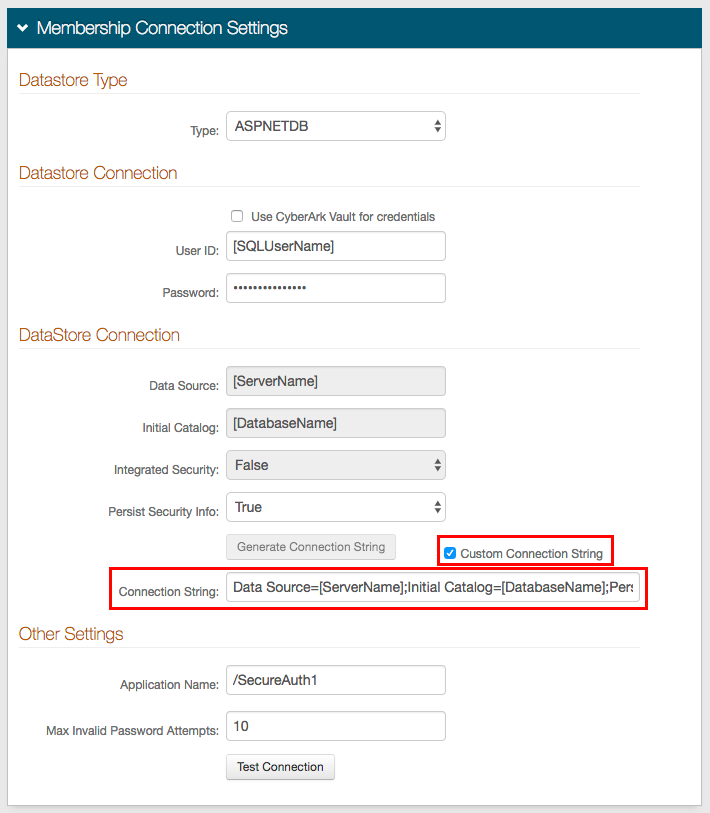
If using a Custom Connection String and experience an error when testing the connection, then refer to the Custom Connection String Error section below for a workaround
Refer to Data Tab Configuration to complete any remaining configuration steps in the Data tab of the Web Admin.
Troubleshooting / Common Issues
Custom Connection String Error
If manually entering a custom connection string, an error may occur when testing the connection, which hinders the SQL Server to successfully integrate with SecureAuth IdP
This error may occur only if Custom Connection String is checked, the Connection String is manually entered into the field rather than generated by the Web Admin, and the fields that comprise the generated Connection String are left empty / default
 |
Workaround
Go to the System Info tab.
In the Links section, click the Click to edit Web Config File link.
2. Search for ASPNETDB and manually enter the connection string into the web.config file.
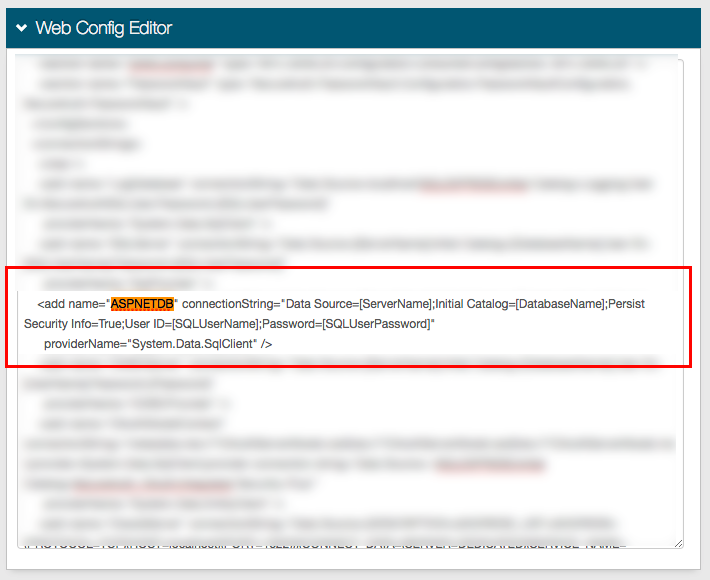
Save your changes.
Note
This enables a successful connection; however, clicking Test Connection in the Data tab may still yield an error
XML Error
If an XML error occurs while attempting to call setpropertyvalues, then the clientmembership table and stored procedure may need to be created; and the aspnet_Profile_FullAccess role may need to be assigned to the stored procedure
ClientMembership Table and Stored Procedure
CREATE TABLE [dbo].[ClientMembership](
[UserId] [uniqueidentifier] NULL,
[ClientGuid] [uniqueidentifier] NULL,
[CreatedOn] [datetime] NOT NULL,
[CreatedBy] [varchar](50) NULL,
[UpdatedOn] [datetime] NULL,
[UpdatedBy] [varchar](50) NULL
) ON [PRIMARY]
GO
SET ANSI_PADDING OFF
GO
ALTER TABLE [dbo].[ClientMembership] ADD CONSTRAINT [DF_ClientMembership_CreatedOn] DEFAULT (getdate()) FOR [CreatedOn]
GO
CREATE PROCEDURE [dbo].[getClientMembership]
@ApplicationName nvarchar(256),
@UserName nvarchar(256)
AS
BEGIN
DECLARE @ApplicationId uniqueidentifier
SELECT @ApplicationId = NULL
SELECT @ApplicationId = ApplicationId FROM dbo.aspnet_Applications WHERE LOWER(@ApplicationName) = LoweredApplicationName
IF (@ApplicationId IS NULL)
RETURN
DECLARE @UserId uniqueidentifier
SELECT @UserId = NULL
SELECT @UserId = UserId
FROM dbo.aspnet_Users
WHERE ApplicationId = @ApplicationId AND LoweredUserName = LOWER(@UserName)
IF (@UserId IS NULL)
RETURN
SELECT Top 1 ClientGuid FROM ClientMembership WHERE @UserID = UserId
END
GOAfter adding the table and stored procedure (above), update the profile section in the SecureAuth IdP web.config file to include a ClientGUID property value
web.config profile section
<properties>
<add name="FirstName" />
<add name="LastName" />
<add name="AuxID1" />
<add name="AuxID2" />
<add name="AuxID3" />
<add name="AuxID4" />
<add name="AuxID5" />
<add name="AuxID6" />
<add name="AuxID7" />
<add name="AuxID8" />
<add name="AuxID9" />
<add name="AuxID10" />
<add name="Email1" />
<add name="Email2" />
<add name="Phone1" />
<add name="Phone2" />
<add name="Phone3" />
<add name="Phone4" />
<add name="kbq1" />
<add name="kbq2" />
<add name="kbq3" />
<add name="kba1" />
<add name="kba2" />
<add name="kba3" />
<add name="CertCount" />
<add name="CertResetDate" />
<add name="GroupList" />
<add name="pinHash" />
<add name="MobileResetDate" />
<add name="MobileCount" />
<add name="CertSerialNumber" />
<add name="ExtSyncPwdDate" />
<add name="HardwareToken" />
<add name="iOSDevices" />
<add name="Email3" />
<add name="Email4" />
<add name="OATHSeed" />
<add name="DigitalFP" type="object" />
<add name="ClientGUID" />
</properties>