Time-based Passcodes (OATH) Registration Method for Multi-Factor Authentication
Introduction
Use this guide to enable the use of Time-based Passcodes (OATH OTPs) as a Registration Method for Multi-Factor Authentication.
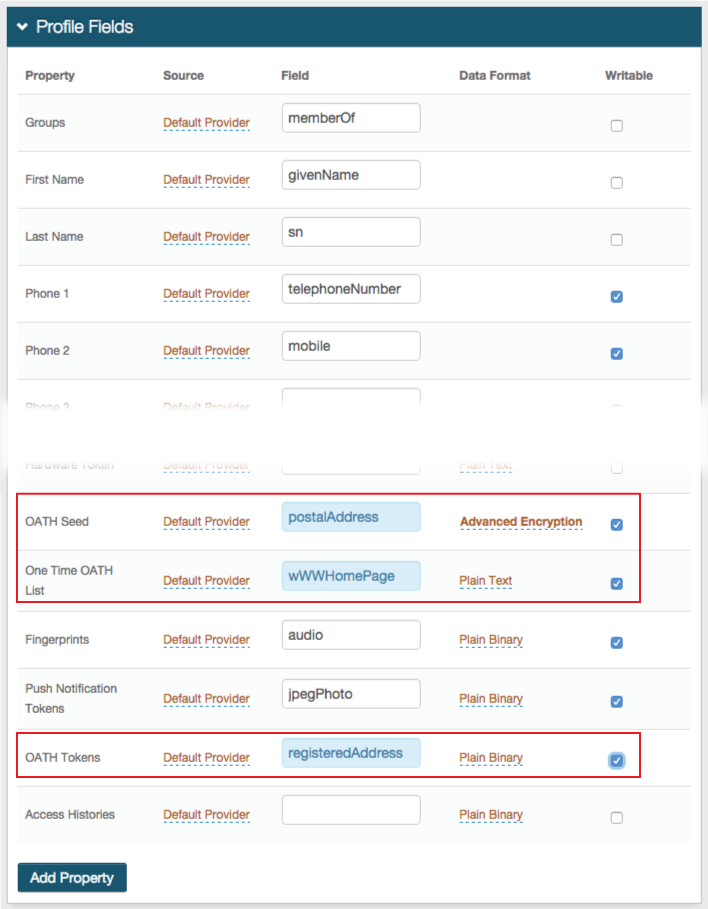
OATH OTPs are generated on the SecureAuth Mobile Apps, Desktop Client Applications, and Chrome Browser Extension; and can be utilized in any realm requiring Multi-Factor Authentication to access the post-authentication action. Depending on how the Multi-Factor App Enrollment realm is configured and on the application(s) being used to generate OATH OTPs, SecureAuth IdP can create OATH Tokens or OATH Seeds.
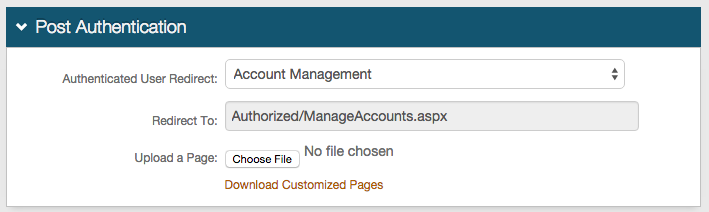
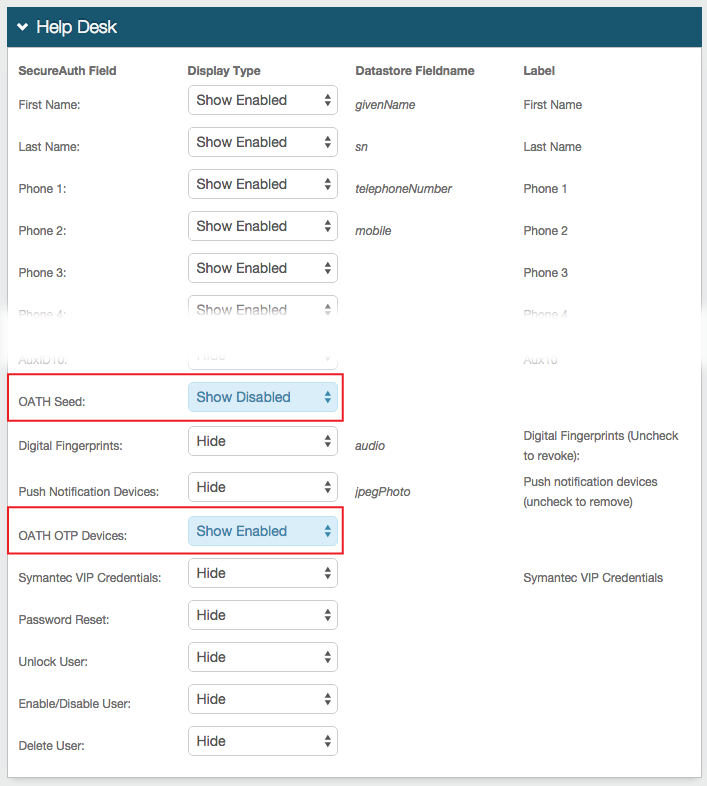
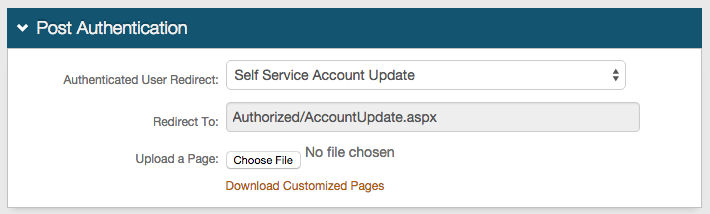
If OATH Tokens are being used, SecureAuth IdP enables one-touch revocation of OATH Tokens to ensure security even if an OTP application is compromised. Refer to the Account Management (Help Desk) Realm Configuration Steps and Self-service Account Update Realm Configuration Steps below to learn how to configure the Help Desk and Self-services realms to enable administrator or self-revocation of OATH Tokens; and refer to the End-user Experience section below to learn how to revoke OATH Tokens on the client-side pages.
Prerequisites
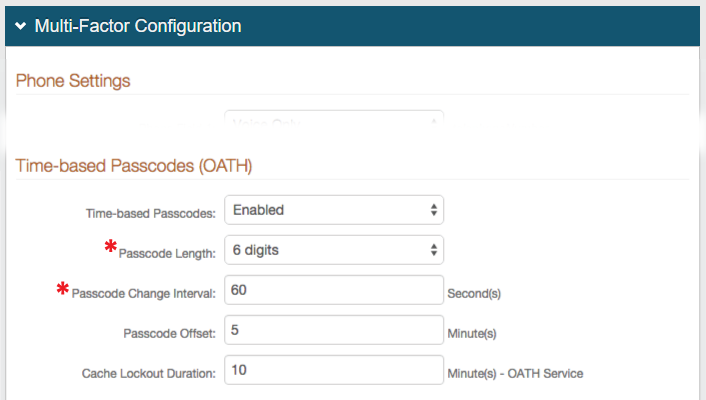
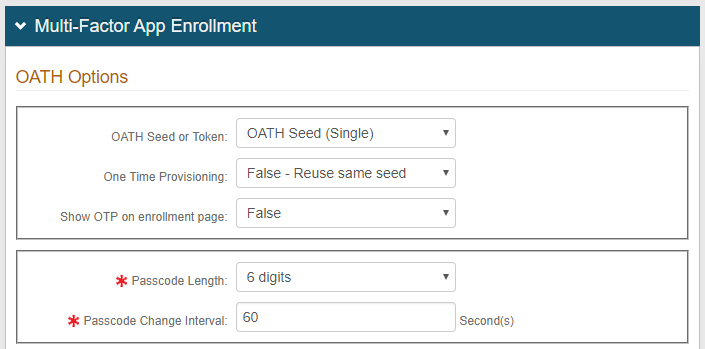
1. Configure the Multi-Factor App Enrollment Realm
2. Provision end-users' devices / browsers to generate Time-based Passcodes:
SecureAuth Authenticate App for Android and iOS (OATH Token and OATH Seed support)
Windows Desktop Passcode Application (OATH Token and OATH Seed support)
Mac Desktop Passcode Application (OATH Token and OATH Seed support)
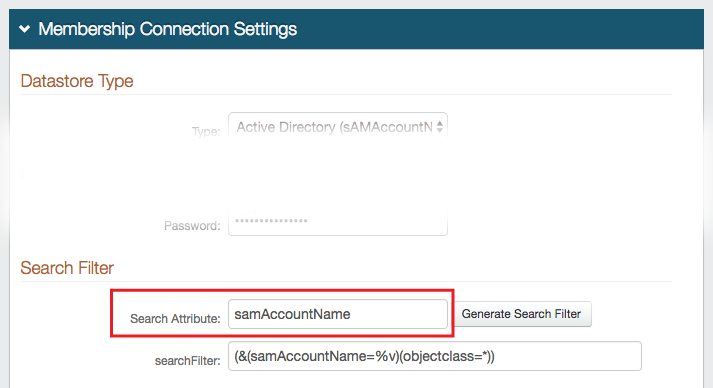
3. Create a New Realm in the SecureAuth IdP Web Admin or access existing realm(s) for which OATH OTPs are to be used for Multi-Factor Authentication
4. Configure the following tabs in the Web Admin before configuring for OATH OTPs:
Overview – the description of the realm and SMTP connections must be defined
Data – an enterprise directory must be integrated with SecureAuth IdP
Workflow – the way in which users will access the target must be defined
Multi-Factor Methods – the Multi-Factor Authentication methods that will be used to access the target (if any) must be defined (for Account Management Realm and Self-service Account Update Realm only)
Post Authentication – the target of the realm must be defined (for Realm Using OATH as Second Factor only)
Follow the Configuration Steps for the Specified Realm Type
End-user Experience
Notice
When the end-user is presented the page of Multi-Factor Authentication methods from which to choose, the Multi-Factor Authentication method that was last selected and used in a successful login attempt persists as the default method for the next login in each device / browser
Realm Using OATH as Second Factor
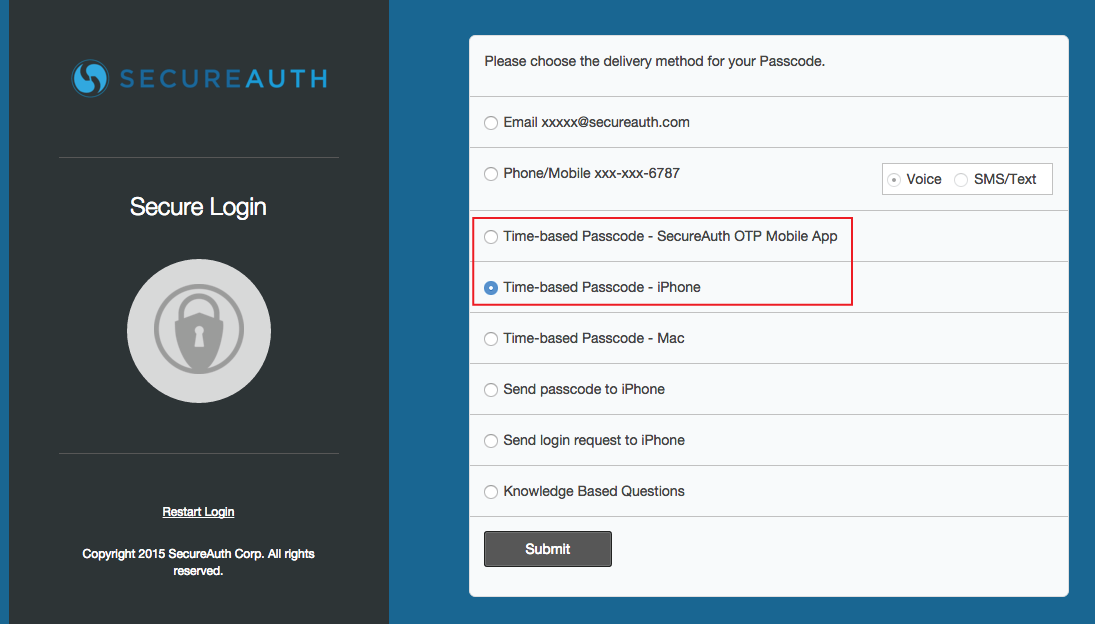 |
1. When logging on a SecureAuth IdP realm in which OATH OTP is enabled, the Time-based Passcode choice(s) appears in the Multi-Factor Authentication methods list
2. Select Time-based Passcode and click Submit
Notice
If the device is provisioned on a Single (OATH Seed) Multi-Factor App Enrollment realm, then select Time-based Passcode - SecureAuth OTP Mobile App; if the device is provisioned on a Multi (OATH Token) SecureAuth App Enrollment realm, then select the appropriate app, e.g. Time-based Passcode - iPhone
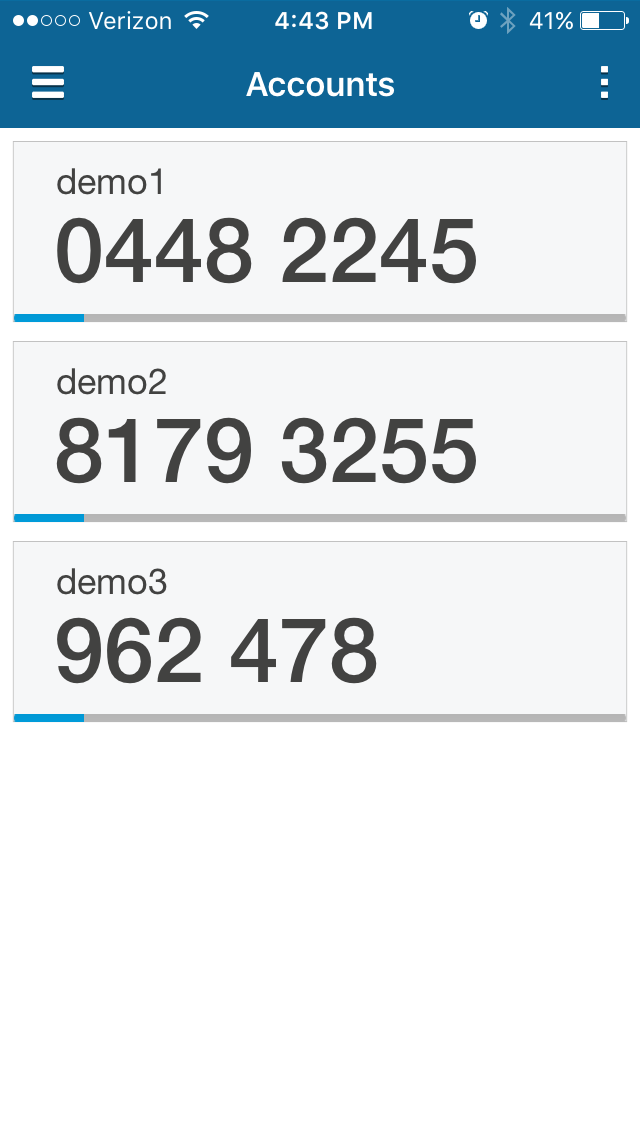 |
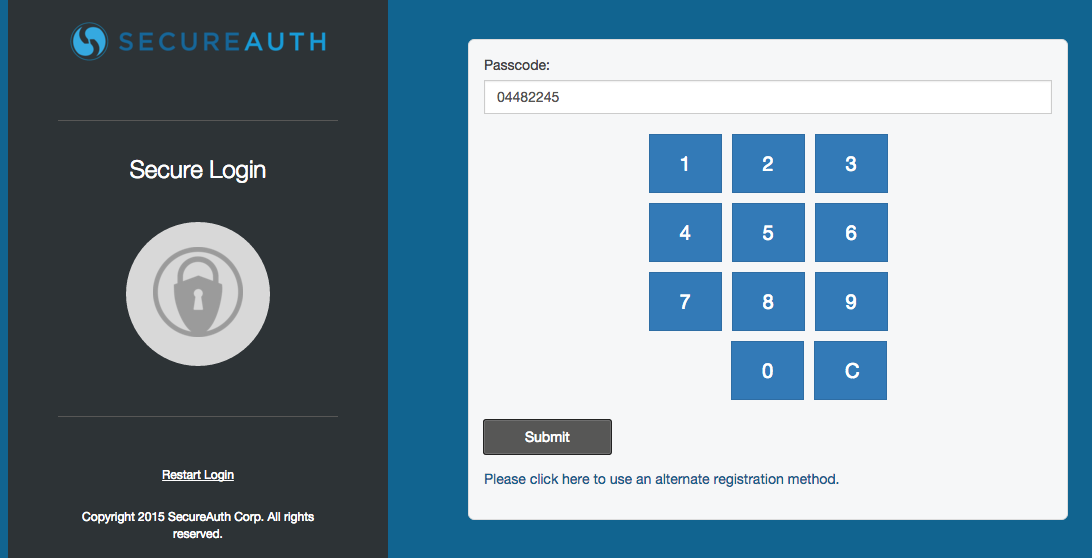 |
3. Open the SecureAuth App being used (SecureAuth Authenticate App for Android and iOS shown in the example) and copy the OATH OTP
4. Paste or enter the OATH OTP into the web page, and click Submit
Account Management (Help Desk) Realm
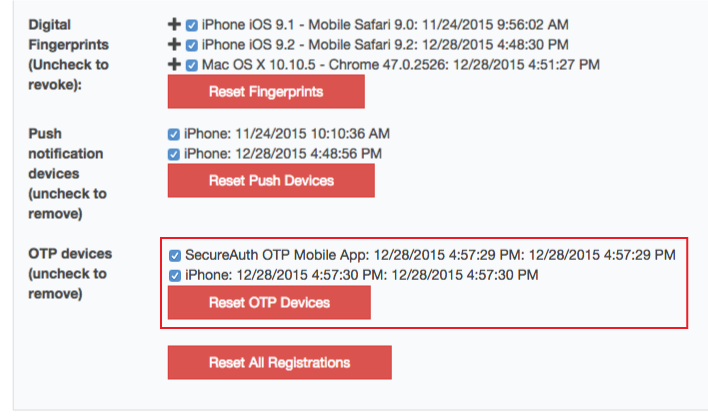 |
1. Once authenticated to the Account Management Help Desk Page, enter the username of the end-user whose OATH OTP Devices are to be revoked
2. Uncheck the undesired devices listed, or select Reset OTP Devices
3. Click Update and the changes are saved
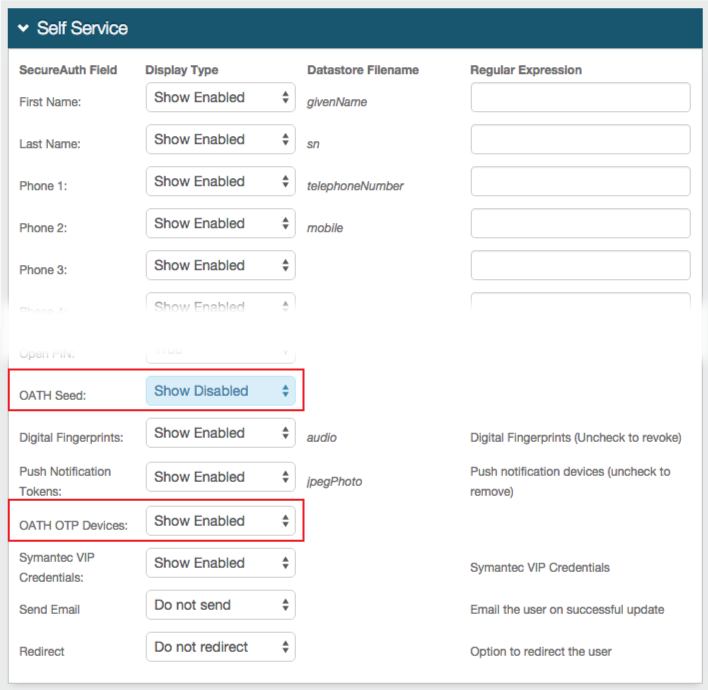
Self-service Account Update Realm
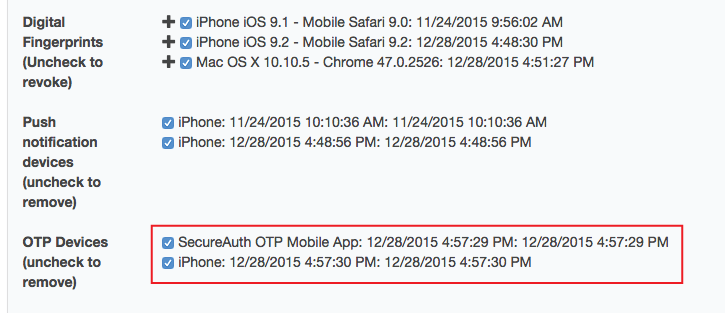 |
1. Once authenticated to the Self-service Account Update Page, scroll to the bottom and uncheck the undesired devices listed
2. Click Update and the changes are saved