Liferay (SP-initiated) Integration Guide
Introduction
Use this guide to enable SecureAuth's Multi-Factor Authentication and Single Sign-on (SSO) via SAML to Liferay.
Prerequisites
1. Have a Liferay Enterprise account and the environment set up
2. Set up an SSL connection with the Tomcat server to enable SSL on Liferay
3. Create a New Realm for the Liferay integration in the SecureAuth IdP Web Admin
4. Configure the followings tabs in the Web Admin before configuring the Post Authentication tab:
Overview – the description of the realm and SMTP connections must be defined
Data – an enterprise directory must be integrated with SecureAuth IdP
Workflow – the way in which users access this application must be defined
Multi-Factor Methods – the multi-factor authentication methods that are used to access this page (if any) must be defined
SecureAuth IdP Configuration Steps
Post Authentication
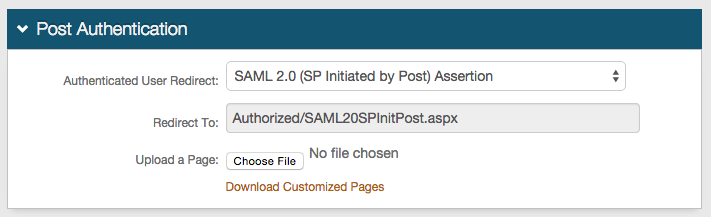 |
1. In the Post Authentication section, select SAML 2.0 (SP Initiated by Post) Assertion from the Authenticated User Redirect dropdown
User ID Mapping
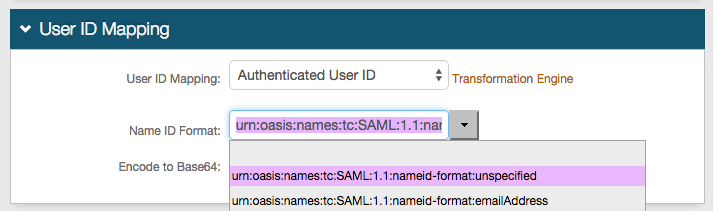 |
2. Select Authenticated User ID from the User ID Mapping dropdown (default)
3. Select urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified from the Name ID Format dropdown (default)
SAML Assertion / WS Federation
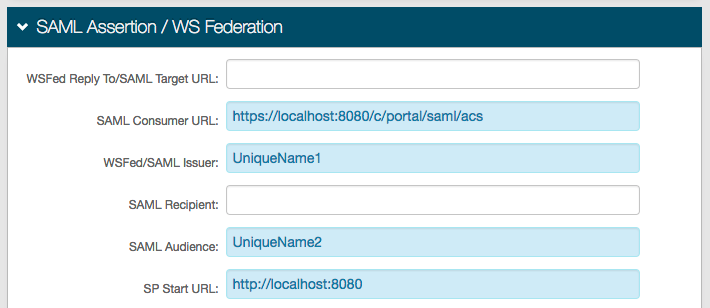 |
4. Set the SAML Consumer URL to the Liferay URL, followed by /c/portal/saml/acs, e.g. https://localhost:8080/c/portal/saml/acs
5. Set the WSFed/SAML Issuer to a Unique Name that is shared with Liferay
This value must match exactly on the SecureAuth IdP side and the Liferay side
6. Set the SAML Audience to a different Unique Name that is shared with Liferay
This value must match exactly on the SecureAuth IdP side and the Liferay side
Note
The WSFed/SAML Issuer value and the SAML Audience value must be distinct from each other
7. Set the SP Start URL to the login URL of the Liferay site, e.g. http://localhost:8080
Notice
No configuration is required for the WS Fed Reply To/SAML Target URL or SAML Recipient fields
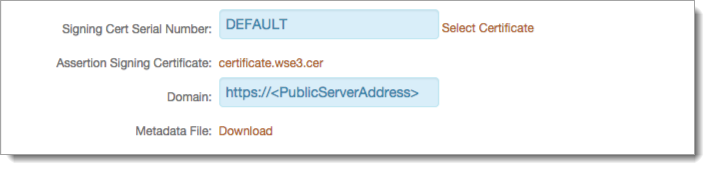 |
8. Leave the Signing Cert Serial Number as the defaulted SecureAuth IdP certificate, unless using a third-party certificate for the integration
If using a third-party certificate, then click Select Certificate and choose the preferred certificate from the list
9. Click to download the Assertion Signing Certificate, which is used in the Certificate Configuration Steps and Liferay Configuration Steps below
10. Provide the Domain of the SecureAuth IdP appliance and then click to Download the Metadata File, which is used in the Liferay Configuration Steps below
Warning
Click Save once the configurations have been completed and before leaving the Post Authentication tab to avoid losing changes
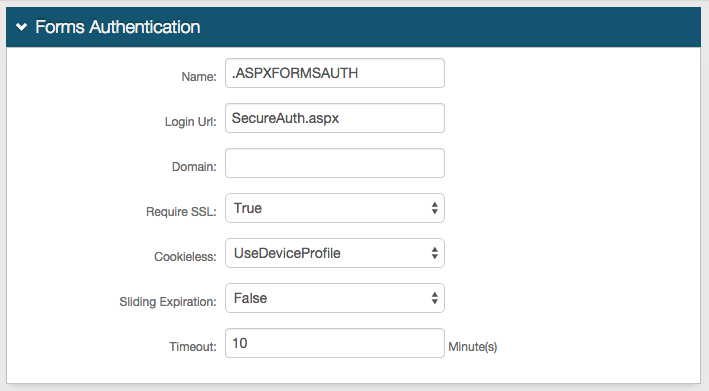
Forms Auth / SSO Token
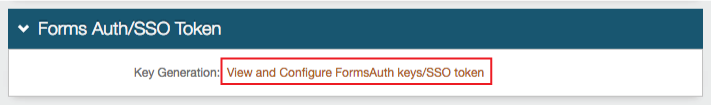
Optionally, in the Forms Auth / SSO Token section, click the View and Configure FormsAuth keys/SSO token link to configure the token/cookie settings and configure this realm for SSO.
 |
Certificate Configuration Steps
1. Export the SecureAuth IdP certificate with a private key downloaded in step 9 above in Base64
2. Follow the Certificate Export Wizard prompts
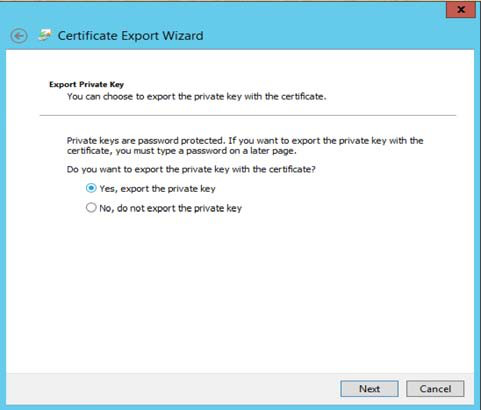
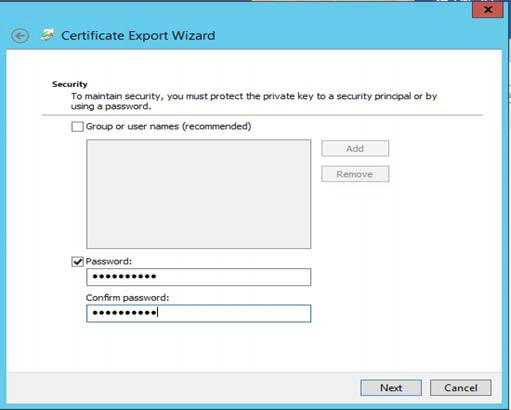
3. In the Wizard, select Yes, export the private key; and then create a Password for the key in the following prompts (see images below)
 |
 |
4. Complete the Wizard
5. Import the certificate into Liferay
6. Open the certificate's Properties, which are used in the Liferay Configuration Steps below
Liferay Configuration Steps
General
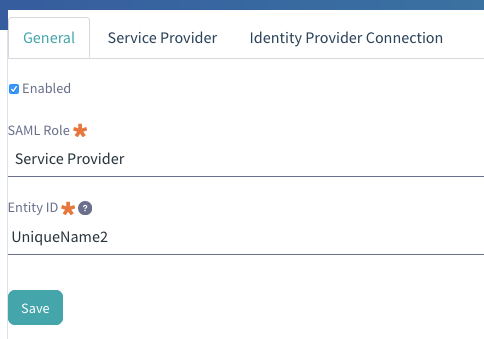 |
1. Sign into Liferay as an administrator, and navigate to Control Panel > Configuration > SAML Admin
2. In the General tab, select Service Provider from the SAML Role dropdown
3. Set the Entity ID to the unique name configured as the SAML Audience value in the SecureAuth IdP Configuration Steps (step 6)
4. Click Save
Certificate Settings
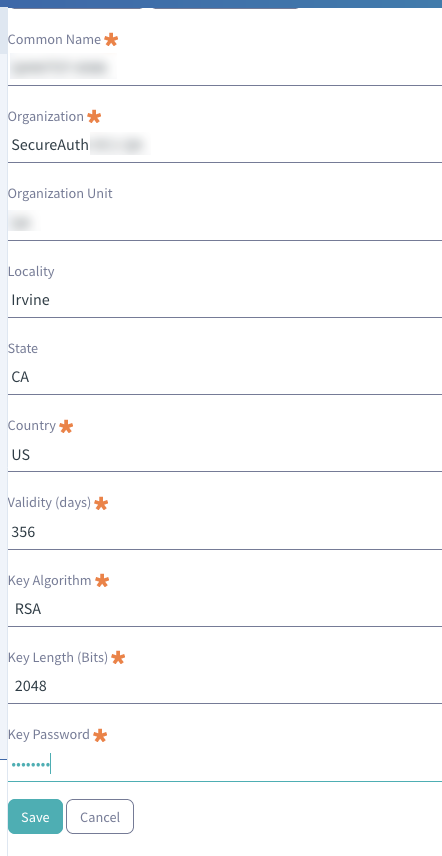 |
5. Using the SecureAuth IdP Certificate Properties, fill out the required information
Note
These values must match the Certificate Properties' values exactly
6. Set the Key Password to the password created during the certificate export from the Certificate Configuration Steps (step 3)
7. Click Save
Service Provider
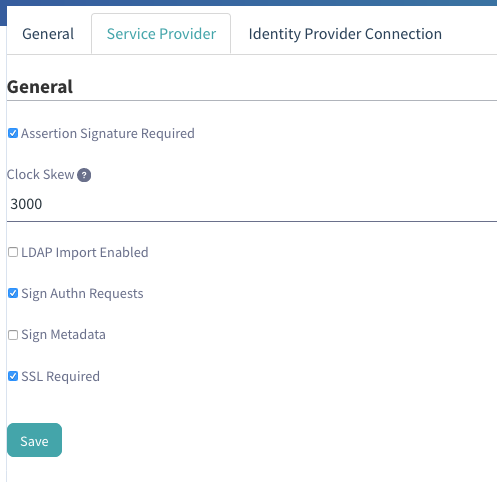 |
8. In the Service Provider tab, check the following boxes:
Assertion Signature Required
Sign Authn Requests
SSL Required
Other settings can be enabled per the organization's requirements, but SecureAuth recommends selecting the above three as a best practice
Identity Provider Connection
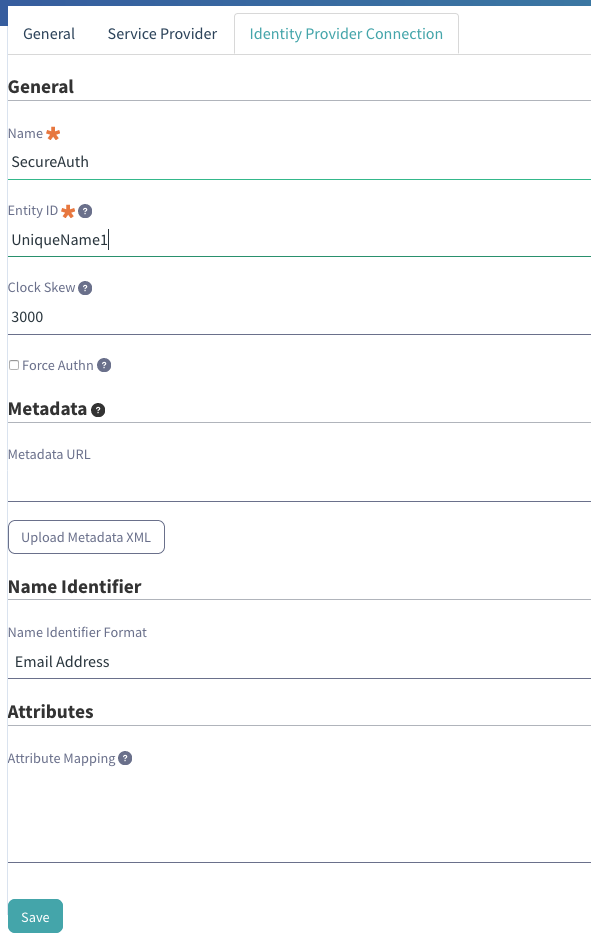 |
9. In the Identity Provider Connection tab, provide a friendly name for the integration, e.g. SecureAuth
10. Set the Entity ID to the Unique Name configured as the WSFed/SAML Issuer value in the SecureAuth IdP Configuration Steps (step 5)
11. Click Upload Metadata XML, then Browse, and then select the Metadata File downloaded from the SecureAuth IdP Configuration Steps (step 10)
12. Select Email Address from the Name Identifier Format dropdown
13. (OPTIONAL) Add any required attribute mapping
14. Click Save