Windows desktop SSO configuration
Use Windows desktop single sign-on (SSO) to allow immediate and secure access to resources via Kerberos-based authentication.
To enable this feature on any SecureAuth IdP realm, the SecureAuth IdP appliance must be joined to the company domain. Window desktops must be on the same company domain, with the ability to process and use Kerberos tickets.
You can configure realms to use Windows desktop SSO in any of the following ways:
- Windows SSO
When the Begin Site is configured to use Windows SSO login workflow, you have the option to include multi-factor authentication (MFA) and adaptive authentication. This method is more secure because it includes the Device Recognition layer.
- Windows SSO (skip workflow)
When the Begin Site is configured to use Windows SSO (skip workflow), it bypasses the login workflow, skips MFA, and routes the user directly to the Post Authentication page once it validates the Kerberos ticket. This method bypasses the Device Recognition layer, however, it increases system performance.
Prerequisites
SecureAuth IdP version 9.1 and later
SecureAuth IdP realm or integrated application with the following configured:
Overview tab
Data tab
Workflow tab
Multi-Factor Methods configuration
Post Authentication configuration
Logs tab
Microsoft Active Directory in use and integrated with SecureAuth IdP
Set up custom identity SPN to leverage Integrated Windows Authentication (IWA)
Enable universal Windows desktop SSO in the environment
The most effective way to enable universal Windows desktop SSO is to push out a local intranet URL via Group Policy Object (GPO); however, end users can also configure their own devices and browsers to enable this feature.
To enable Windows desktop SSO
Add the SecureAuth IdP server Fully Qualified Domain Name (FQDN) to the Local intranet list of websites in Chrome, Internet Explorer, and Firefox browsers.
Grant the "Authenticated Users" group access to the signing certificate being used in the realm.
For instructions, see Grant Permission to Use Signing Certificate Private Key.
Install the Machine Key Tool per the instructions in the document.
Run the Machine Key Tool to assign "Authenticated Users" permissions to the RSA .NET Framework Configuration Key.
Select option A on the Privileges tab in the document.
SecureAuth IdP configuration
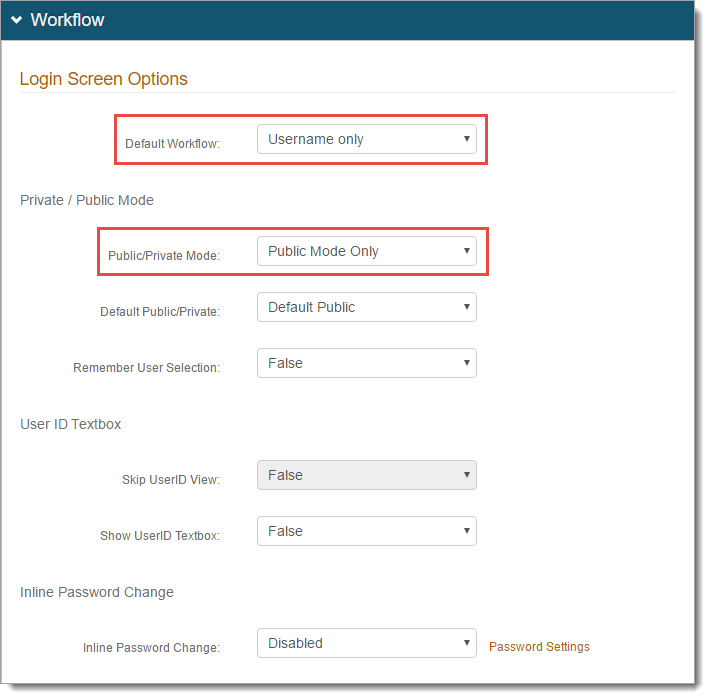
Go to the Workflow tab.
In the Workflow section, set the following:
Default Workflow
Set to Username only.
Note
To configure two-factor authentication (2FA), select Username | Second Factor.
Public/Private Mode
Set to Public Mode Only.
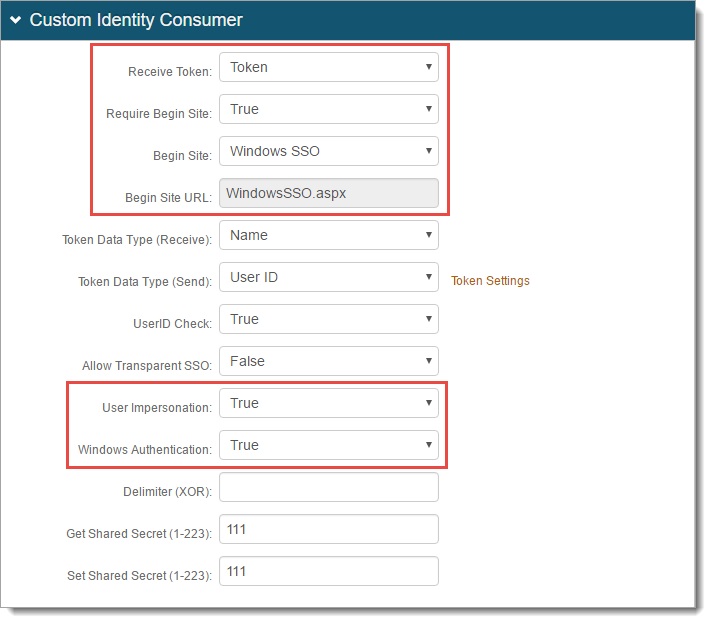
In the Custom Identity Consumer section, set the following:
Receive Token
Set to Token.
Require Begin Site
Set to True.
Begin Site
Use any of the following options:
To include MFA and adaptive authentication in login workflow, set to Windows SSO. This method adds the Device Recognition layer, and is more secure.
To skip the login workflow and go directly to the Post Authentication page, set to Windows SSO (skip workflow). This method does not include MFA, adaptive authentication, and increases performance.
Begin Site URL
Depending on the Begin Site selection, this field is auto-populated with WindowsSSO.aspx or WindowsSSO2.aspx.
User Impersonation
Set to True.
Windows Authentication
Set to True.
Click Save.