Meraki Dashboard (IdP-initiated) Integration Guide
Introduction
Use this guide to enable SecureAuth IdP-initiated Multi-Factor Authentication and Single Sign-on (SSO) access via SAML to Meraki's Administrator Dashboard.
Prerequisites
1. Have a Meraki enterprise dashboard
2. Create a New Realm in the SecureAuth IdP Web Admin for the Meraki integration
3. Configure the following tabs in the Web Admin before configuring the Post Authentication tab:
Overview – the description of the realm and SMTP connections must be defined
Data– an enterprise directory must be integrated with SecureAuth IdP
Workflow– the way in which users will access this application must be defined
Multi-Factor Methods– the Multi-Factor Authentication methods that will be used to access this page (if any) must be defined
SecureAuth IdP Configuration Steps
Data
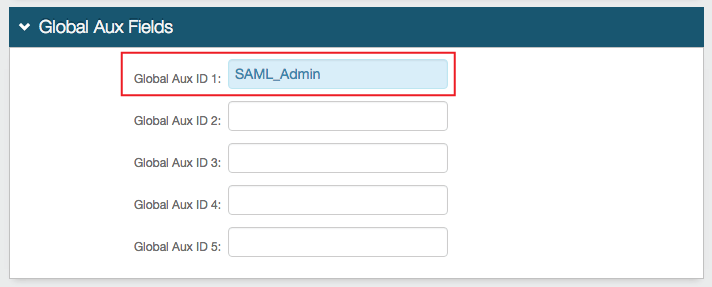 |
1. In the Global Aux Fields section, set Global Aux ID 1 to the Role Name to be used in the Meraki Configuration Steps (below)
Note
This value can also be stored as an attribute in the directory and mapped to a SecureAuth IdP Profile Property if preferred
Warning
Click Save once the configurations have been completed and before leaving the Data tab to avoid losing changes
Post Authentication
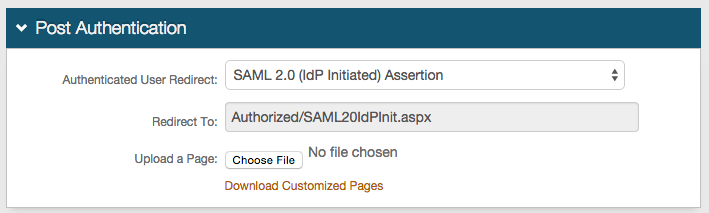 |
2. In the Post Authentication section, select SAML 2.0 (IdP Initiated) Assertion from the Authenticated User Redirect dropdown
3. An unalterable URL will be auto-populated in the Redirect To field, which appends to the domain name and realm number in the address bar (Authorized/SAML20IdPInit.aspx)
User ID Mapping
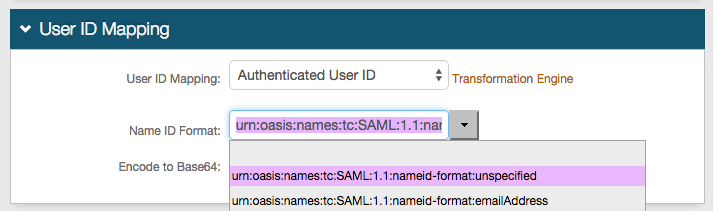 |
4. Select Authenticated User ID from the User ID Mapping dropdown (default)
5. Select urn:oasis:names:tc:SAML:2.0:nameid-unspecified from the Name ID Format dropdown (default)
SAML Assertion / WS-Federation
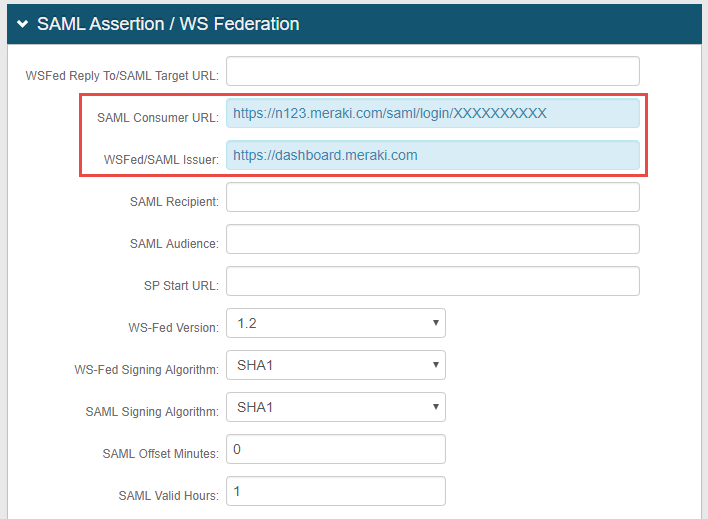 |
6. Set the SAML Consumer URL to the Consumer URL value generated in the Meraki admin console (see Meraki Configuration Steps below)
7. Set the WSFed/SAML Issuer to https://dashboard.meraki.com
Note
No configuration is required for the WSFed Reply To/SAML Target URL, SAML Recipient, SAML Audience, or SP Start URL fields
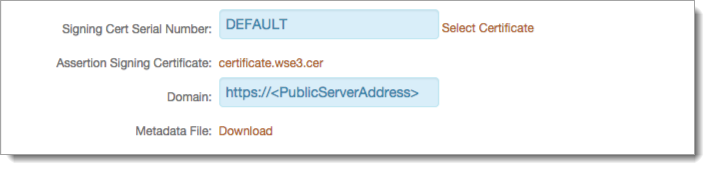 |
8. Leave the Signing Cert Serial Number as the default value, unless there is a third-party certificate being used for the SAML assertion
If using a third-party certificate, click Select Certificate and choose the appropriate certificate
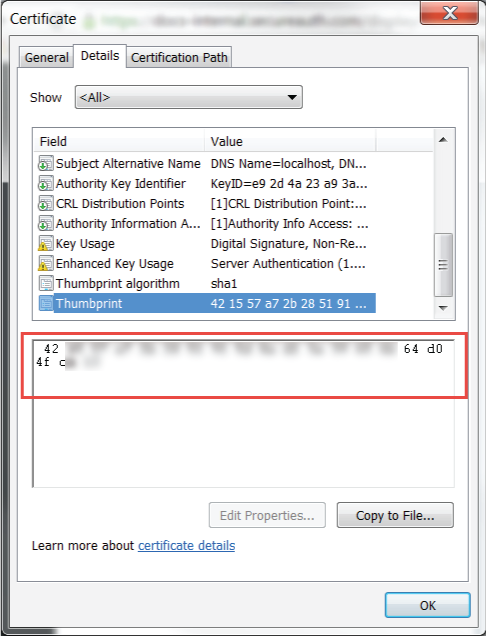
9. Click the Assertion Signing Certificate to download the certificate and to retrieve the thumbprint, which is used in the Meraki Configuration Steps
SAML Attributes / WS-Federation
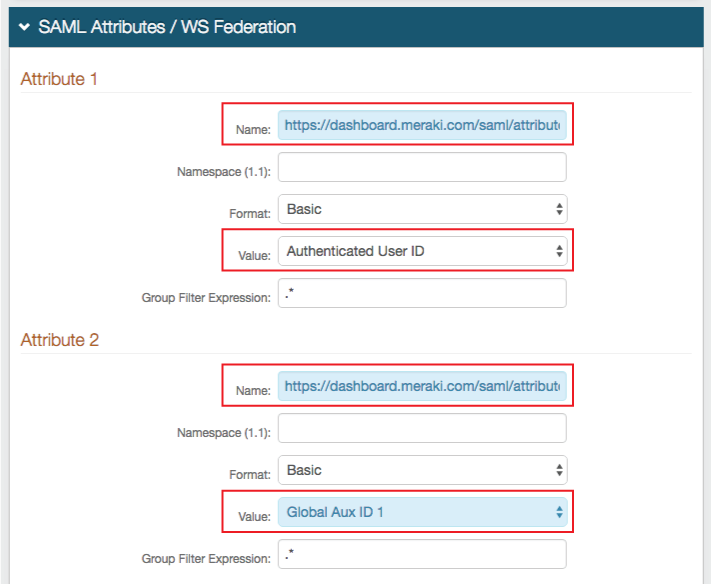 |
10. Set the Name of Attribute 1 to https://dashboard.meraki.com/saml/attributes/username
11. Select Authenticated User ID from the Value dropdown
12. Set the Name of Attribute 2 to https://dashboard.meraki.com/saml/attributes/role
13. Select Global Aux ID 1 from the Value dropdown
Note
If storing the Meraki Role Name in a directory attribute rather than the Global Aux ID, then select the SecureAuth IdP Profile Property to which the directory attribute is mapped
Warning
Click Save once the configurations have been completed and before leaving the Post Authentication page to avoid losing changes
Forms Auth / SSO Token
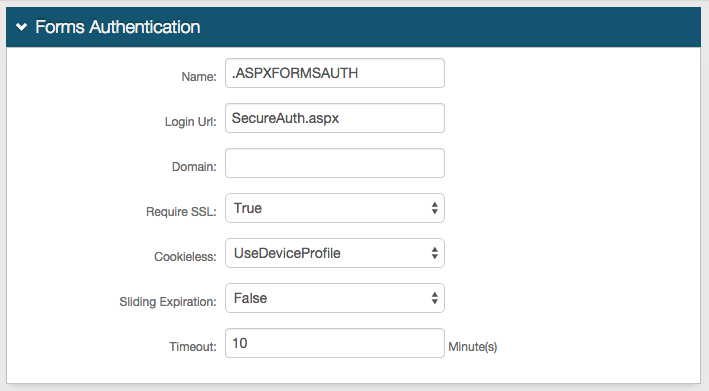
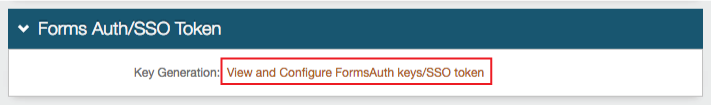
Optionally, in the Forms Auth / SSO Token section, click the View and Configure FormsAuth keys/SSO token link to configure the token/cookie settings and configure this realm for SSO.
 |
Meraki Configuration Steps
 |
1. Log into the Meraki System Manager Dashboard, and navigate to Organization --> Configure --> Settings
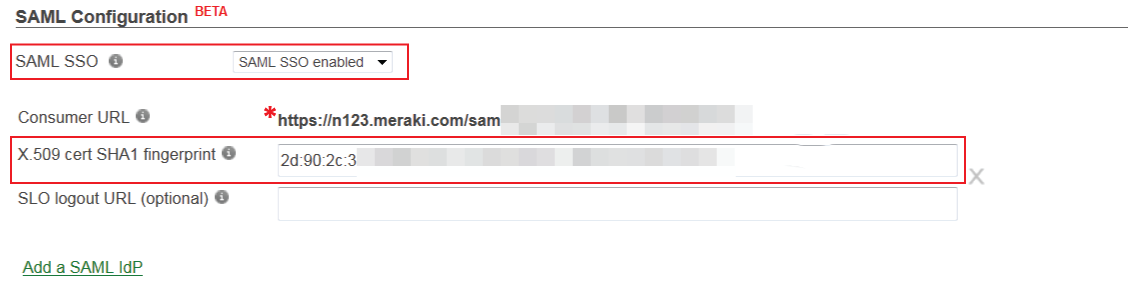
2. In the SAML Configuration section, select Add SAML IdP
3. Select SAML SSO enabled from the SAML SSO dropdown
4. Paste the certificate thumbprint value acquired from the SecureAuth IdP Assertion Signing Certificate (step 9) into the X.509 cert SHA1 fingerprint field
5. (OPTIONAL) Set the SLO logout URL to the Fully Qualified Domain Name (FQDN) of the SecureAuth IdP appliance, followed by the Meraki-integrated realm and /logout.aspx, e.g. https://secureauth.company.com/secureauth2/logout.aspx; or any desired logout destination
6. Click Save
7. Once the configuration is saved, the Consumer URL is populated with a unique URL, which is the required value for step 6 in the SecureAuth IdP Configuration Steps
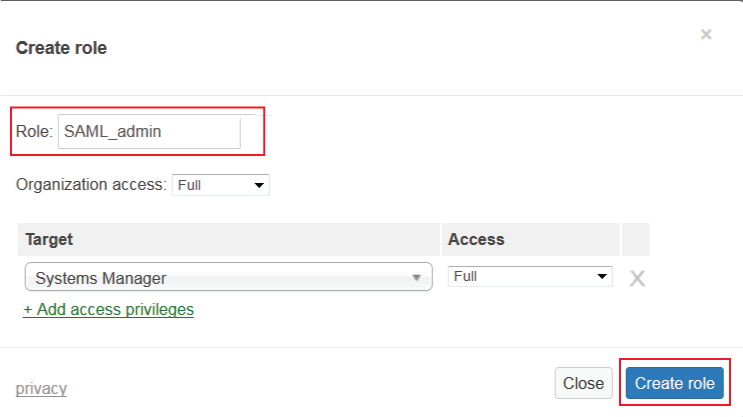
Create Role
 |
8. Navigate to Organization --> Configure --> Administrators
9. Select Add SAML Role
10. Set the Role to the same name set in step 1 of the SecureAuth IdP Configuration Steps, e.g. SAML_Admin
11. Configure the Organization Access and Target System as preferred, and click Create Role
Refer to Configuring SAML Single Sign-on for Dashboard for more information