Basic connectivity checks
Verify the SecureAuth IdP appliance is connected to your network and can communicate with SecureAuth's cloud services.
Warning
IMPORTANT: If you have SecureAuth IdP appliances running versions prior to 8.0 in your environment, speak to your sales or deployment engineer.
Prerequisites
Complete Install the appliance
Note
DHCP vs. Static IPs
SecureAuth IdP is configured to support Dynamic Host Configuration Protocol (DHCP) for automatic IP address assignment. If the network segment the SecureAuth IdP appliance is configured for does not support DHCP, you may close the SecureAuth IdP Setup Utility and perform the appropriate network adapter IP configuration for that network segment. Once you have confirmed network connectivity, re-launch the setup utility and continue with activation.
Proxy Configuration
SecureAuth IdP receives proxy configuration information from the Internet Options window. If the installation requires a proxy setup, verify that proxy settings are correctly configured there.
To access Internet Options, click Start, then type Internet Options.
Process
The following outline lists the checks that must be done to confirm the SecureAuth IdP is properly connected to your network. It also includes post-install connection troubleshooting checks.
Task A: Check IP address configuration
This task is to confirm IP address and other networking settings.
Open a command prompt on the appliance.
From the Start menu, type cmd and select the Command Prompt app.
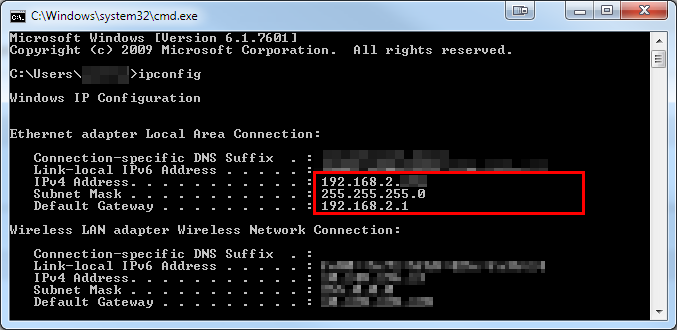
In the command prompt, type ipconfig and press Enter.
Verify the settings are correct for:
IPv4 Address
Subnet Mask
Default Gateway
Task B: Check DNS settings
This task is to verify or set the proper DNS server addresses.
Verify the DNS server (both internal and external) is configured and working.
Register the appliance name in the appropriate DNS lookup zones.
For more information about working with DNS, see the following Microsoft documentation:
Task C: Check NTP settings
This task is to enable NTP and synchronize the Windows Server clock with an NTP server.
Key notes to consider:
To work correctly, the appliance must keep its time accurate to within ~5 minutes. When a time deviation is too high (or if an incorrect region is set during the Windows installation), it causes problems with Kerberos.
If SecureAuth IdP is installed on a virtual machine, verify the NTP settings are correct on the hypervisor server.
For in-depth documentation on configuring a time source, refer to:
To synchronize time, in the Windows taskbar, click the Date/Time icon.
Click the Change date and time settings link.
In the Date and Time window, verify the Time zone matches your location.
If the time zone is not correct, click Change time zone and select the correct time zone.
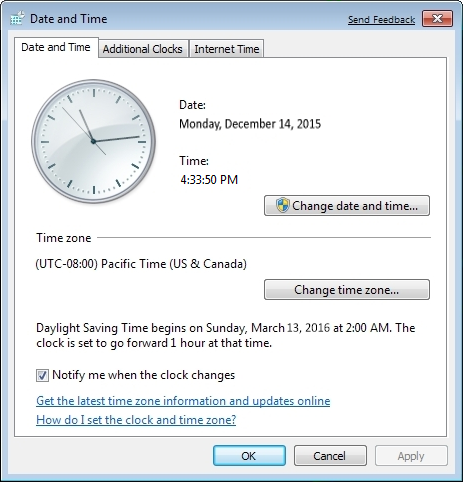
Select the Internet Time tab, and then click Change settings.
If the Internet Time tab is not present, then the appliance is a member of a domain and synchronizes with the domain controller.
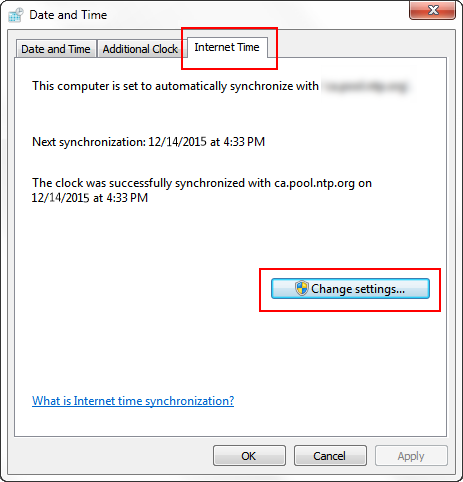
5. In the Internet Time Settings window, enter the IP or Hostname of the company NTP server, or choose a server from the list.
Task D: Test Cloud Services access
This task is to verify the appliance can reach SecureAuth cloud services.
On the appliance, start a browser window.
Navigate to https://us-cloud.secureauth.com/
The SecureAuth "Default Services Page" should appear.
Navigate to https://us-trx.secureauth.com/
The SecureAuth "Default Services Page" should appear.
If either destination is unreachable, check that every firewall on your network has the appropriate ports opened (see Network communication requirements for SecureAuth IdP).
Next steps
After the SecureAuth IdP appliance passes all of the above connectivity checks, proceed to Run the SecureAuth IdP Setup Utility.
If there are connectivity issues after installing SecureAuth IdP, continue to the next section.
Troubleshooting connectivity after installation
This section is intended for troubleshooting after SecureAuth IdP is successfully installed.
Troubleshooting A: Test connectivity in the Web Admin
This is a post-installation troubleshooting task to test connectivity in the Web Admin.
On the SecureAuth IdP Web Admin, go to the admin realm (SecureAuth0).
Select the System Info tab.
In the WSE 3.0 / WCF Configuration section, click the Test button.
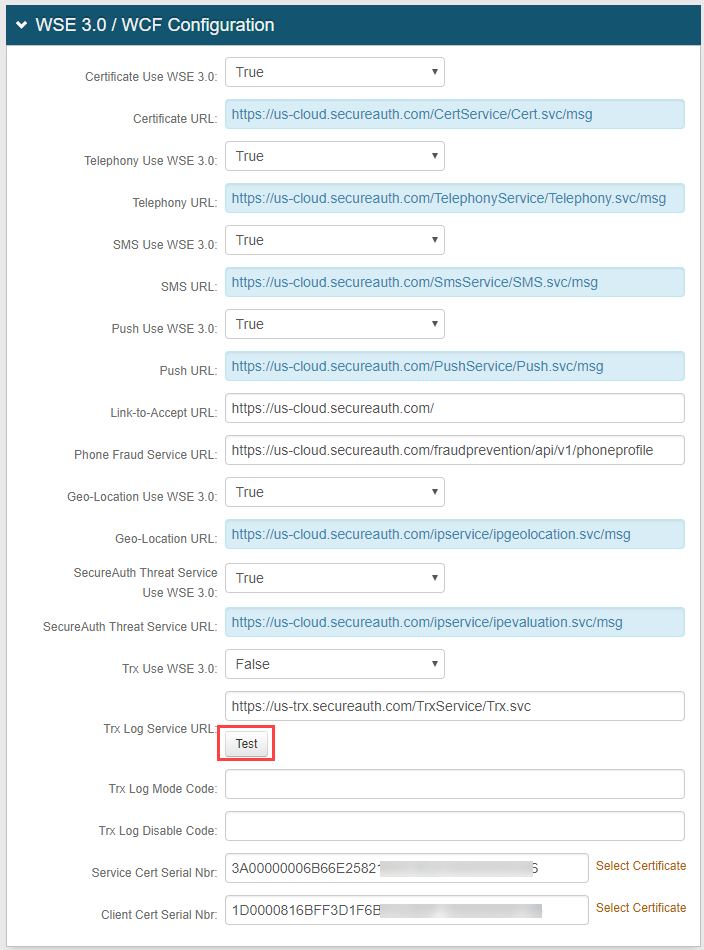
The "Passed" result should appear beside the Test button:

If this test fails, verify that every firewall on your network has the appropriate ports opened (see Network communication requirements for SecureAuth IdP).
Troubleshooting B: Test the Web Admin connection from an external source
This is a post-installation troubleshooting task to test connectivity to the Web Admin from an external source.
Start a web browser from a different client on the corporate network.
Navigate to the SecureAuth1 realm.
If the login screen appears, connectivity is validated and the test is successful.