Integrated Windows Authentication (IWA) Troubleshooting
Introduction
This article discusses basic troubleshooting techniques you can use to resolve problems with SecureAuth realms configured for Integrated Windows Authentication (IWA) workflows. This type of workflow is also referred to as Desktop SSO.
Applies to
SecureAuth IdP
Troubleshooting
Ensure firewalls are configured properly
Review the document Network Communication Requirements for SecureAuth IdP to ensure all firewalls between the SecureAuth IdP Appliance and the Domain Controller(s) are configured properly. Also verify the RPC high ports (Default Dynamic port range) are configured correctly as well. Per the Internet Assigned Numbers Authority (IANA) and Microsoft recommendations, the default start port should be 49152 and the end port 65535. See the Microsoft support document Active Directory and Active Directory Domain Services Port Requirements for further information on the topic.
Ensure all devices are joined to the domain
For IWA to work properly the workstation and SecureAuth appliance must be joined to the same domain. Verify the SecureAuth appliance(s) and workstation attempting IWA are properly joined to the same domain. You also need to verify the SecureAuth appliance has the necessary connectivity to the Domain Controllers to properly fulfill the request. See the support document Appliance Pre-Deployment Installation Checklist for further information.
To determine if a Windows endpoint device is joined to a domain | |
|---|---|
Windows 7 Devices |
|
Windows 8 Devices |
|
To determine if a SecureAuth appliance is joined to a domain | |
Appliances running Windows Server 2008 R2 |
|
Appliances running Windows Server 2012 R2 |
|
Ensure the time is correct
IWA (by default) uses the Kerberos protocol which is sensitive to time drifts. The workstation, SecureAuth server, and Domain Controllers must all have accurate timekeeping for IWA to work properly. Normally, when joined to a domain, the SecureAuth server and workstation should be deriving time from a Domain Controller however in certain circumstances this may not happen. You should check the time in all three places to ensure they are within a few minutes of each other.
Ensure the web browser is configured correctly
For security reasons a browser will not provide a user's credentials to the SecureAuth server unless the site (or subdomain) is on an allowed list.
For Internet Explorer and Chrome on Windows
For Internet Explorer and Chrome the SecureAuth servers must be under Local Intranet zone in Internet Options. Otherwise the credentials will not be passed to the site and the user will be prompted to obtain their credentials. The Local Intranet zone setting can be implemented either locally on the workstation or through a GPO.
For FireFox on Windows
In FireFox the Windows Internet Options are not used, instead the about:config setting network.automatic-ntlm-auth.trusted-uris is used. Below please find instructions to configure the option.
1. Open FireFox
2. In the address bar type about:config and press Enter.
3. If prompted with the security warning choose "I'll be careful, I promise".
4. After the configuration page loads, in the filter box, type: network.automatic
5. Modify network.automatic-ntlm-auth.trusted-uris by double-clicking the row and enter the FQDN of the SecureAuth server (e.g. https://secureauth.company.com). If there are multiple entries they should be separated with commas.
Ensure the realm is configured properly for IWA
In the workflow tab the following settings need to be configured to enable IWA operation. Please verify the settings on the impacted realm.
Note
Starting with SecureAuth IdP 8.0.0 the Authentication Mode must be set to either Username Only or Username | Second Factor. If Authentication Mode is set to any other value, the IWA workflow will fail.
Setting | Value |
|---|---|
Authentication Mode | Username Only |
User Impersonation | True |
Windows Authentication | True |
Receive Token | Token |
Require Begin Site | True |
Begin Site | Windows SSO |
Ensure the realms' Authentication settings are correct
When a realm is configured for IWA the authentication settings in IIS need to be modified. Normally this is handled through the SecureAuth GUI, but it is possible that a setting could have changed. Please follow the instructions below to ensure everything is configured properly.
For SecureAuth appliances running Windows Server 2008 R2
1. Launch the SecureAuth administrative interface and choose the realm you configured for IWA.
2. Go to the Workflow tab and verify the User Impersonation and Windows Authentication options are set to True.
3. On the Start menu, click All Programs, click Administrative Tools, and then click Internet Information Services (IIS) Manager.
4. In the Connections pane expand the Sites node followed by the Default Web Site node.
5. Now select the SecureAuth realm you have configured for IWA by clicking on it once so it becomes highlighted.
6. On the center pane, in the IIS section, double-click on the Authentication icon.
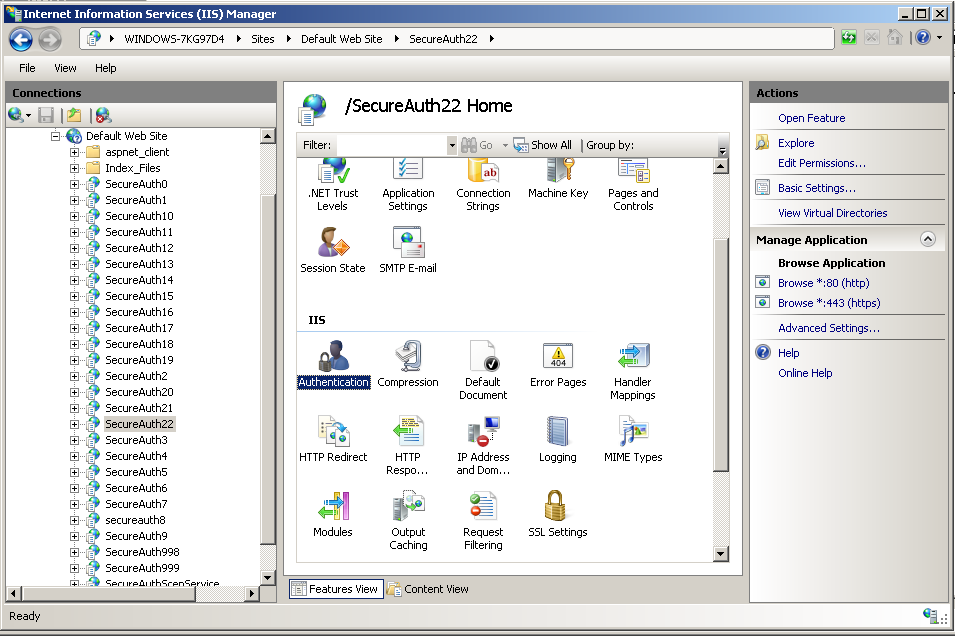 |
7. In the Authentication screen ensure Basic Authentication and Windows Authentication are set to Enabled. Next verify the remaining options are set to Disabled, if not, set them to Disabled.
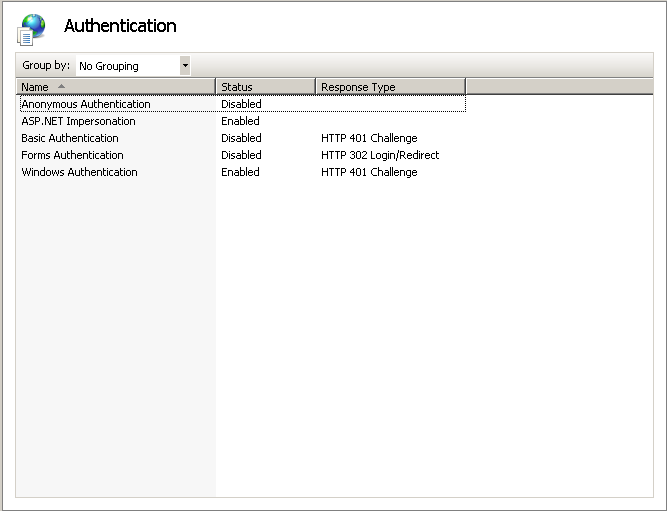 |
For SecureAuth appliances running Windows Server 2012
1. Launch the SecureAuth administrative interface and choose the realm you configured for IWA.
2. Go to the Workflow tab and ensure the User Impersonation and Windows Authentication are set to True.
3. On the desktop, hover the mouse cursor in the lower right corner of the screen, and then click Settings.
4. Click Control Panel.
5. Click System and Security, and then click Administrative Tools.
6. In the Administrative Tools window, double-click Internet Information Services (IIS) Manager.
7. In the Connections pane expand the Sites node followed by the Default Web Site node.
8. Now select the SecureAuth realm you would like to apply the redirect to by clicking on it once so it becomes highlighted.
9. On the center pane, in the IIS section, double-click on the Authentication icon.
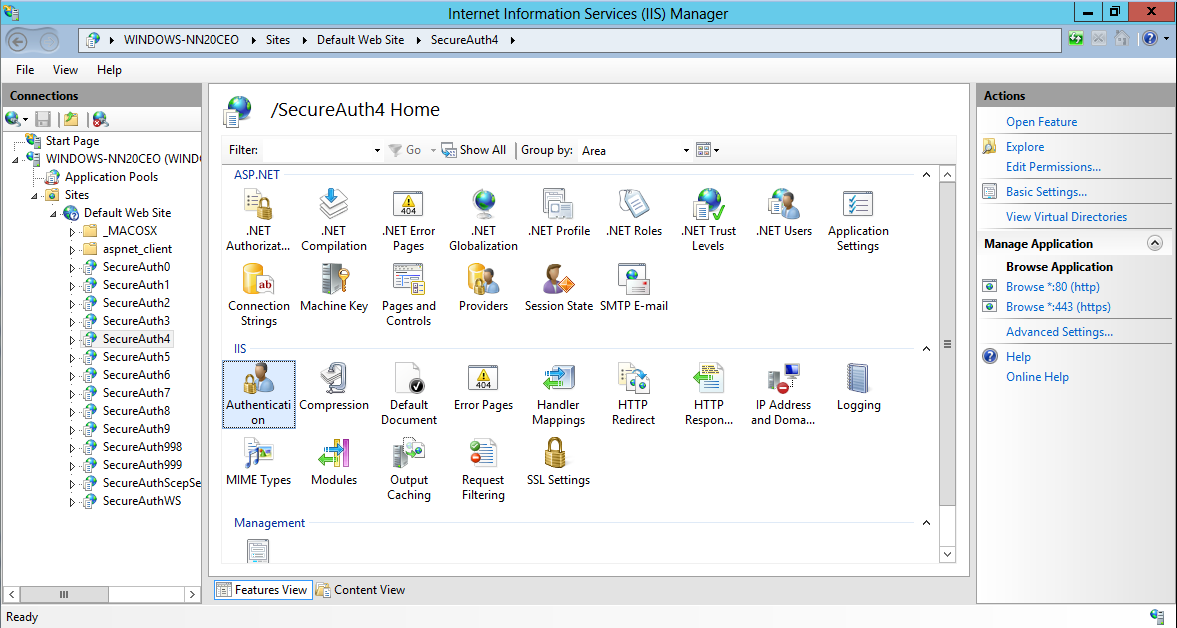 |
10. In the Authentication screen ensure Basic Authentication and Windows Authentication are set to Enabled. Next verify the remaining options are set to Disabled, if not, set them to Disabled.
 |