Resolution for LDAP - Access Denied error message
Issue
The issue "LDAP - Access Denied" appears for either the Password Reset page or User Self-Service page.
Resolution
Review Active Directory
Review the affected user's Active Directory account to ensure it is configured to inherit permissions from the parent container object.
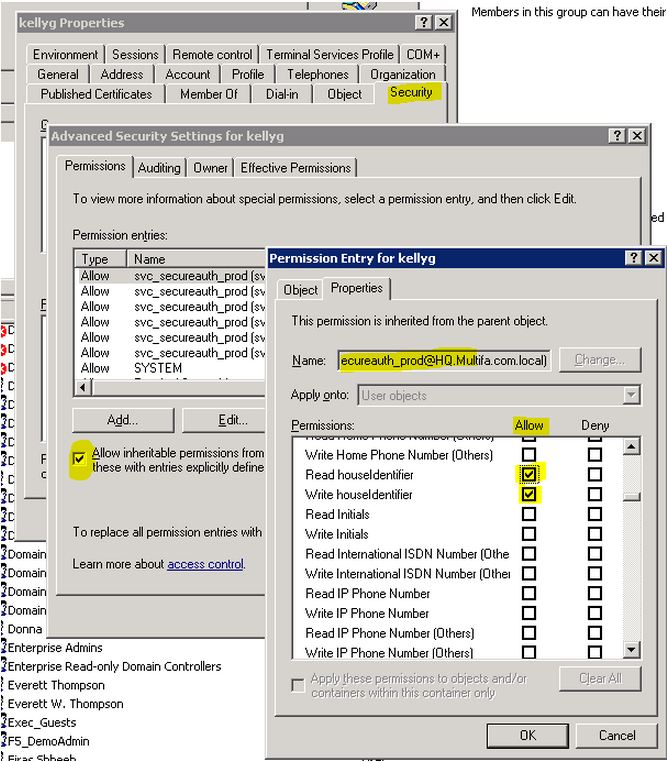
1. Open Active Directory Users and Computers snap-in and enable "Advanced Features" from the "View" menu.
2. Search / Select the affected users account for the Domain the user's account is located and view the properties.
3. Select the Security Tab and then select the "Advanced" button on the bottom of the Dialog box.
4. Verify the "Checkbox" is enabled next to "Allow inheritable permissions from the parent to propogate to the object and all child objects. Include these with entries explicity defined here." See image 1a below. If this is not enabled, please enable or manually add the delegated permissions as detailed in the Verify Permissions steps below.
Image 1a
Verify Permissions
Verify the permissions defined below have been inherited from the parent container object to the affected user's account. These permissions were delegated to the SecureAuth Service account at a parent container level (or domain level) to allow User Self-Service, Helpdesk or Password reset realms to function.
1. Select "Name" in the Permissions entries to sort the accounts which have permissions applied (delegated) to the account.
2. Scroll down until you see the service account.
3. Select each entry to verify which permission has been applied. Compare the applied permissions and type to the list below.
Note
"Read" permissions may not be explicitly defined. The Service account may have been granted "Read All Properties" rights or the any AD account can read the base attributes of other accounts. It is very important that the "Write", "Reset Password" and "Change Password" permissions are defined as shown below.
Typical Permissions and AttributeNames
Read givenName - Allow *
Read sn - Allow *
Read telephoneNumber - Allow *
Write mobile - Allow *
Read mail - Allow *
Write psdLastSet = Allow **
Write userAccountControl = Allow **
Write lockoutTime = Allow **
Write accountExpires = Allow **
Reset Password = Allow **
Change Password = Allow **
* For User Self Service Functionality
** For Password Change/Reset Functionality
 |
Information related to Service account permissions and Delegation of control can be found in SecureAuth IdP Service Account Setup and Configuration Guide for LDAP Directories (Active Directory and others).