Multi-factor throttling configuration
Use this guide to configure SecureAuth IdP to prevent a user from attempting to log in to an application with invalid credentials too often over a specified period of time.
Multi-factor authentication (MFA) throttling provides protection against two common forms of attack:
Brute force. An attempt to log in using trial-and-error with a large number of one-time passcodes (OTPs).
Denial of service. An attempt to disrupt service by quickly generating a large number of one-time passcodes (OTPs) to overwhelm the system.
This feature uses a dynamic, rolling time period to keep count of MFA attempts. When an end user opens the application login page, an attempt count value increments by 1. That attempt lives for the duration of the configured time period; once the time period for that attempt has elapsed, the attempt count decrements by 1.
The configured throttling action occurs when the attempt count exceeds the number of allowed attempts
The attempt count is reset to 0 upon a successful authentication
Note
Throttling in multi-factor authentication is enabled on a per realm basis, but all realms share the same attempt count value.
Password entry is not considered in the attempt count for throttling in multi-factor authentication. For example, if the user successfully enters a multi-factor method, but enters the wrong password, then there is no throttling penalty.
APIs. The configuration settings for multi-factor throttling are in the Advanced Settings (formerly Classic Experience). There are APIs available for retrieving and resetting the attempt count value. For more information, see Multi-factor throttling authentication API guide.
Prerequisites
SecureAuth IdP 9.2 or later
Have an application realm with the following tabs configured:
Data / Directory integrations
Workflow
Multi-Factor Methods
Data tab configuration
To store the number of MFA attempts in a directory attribute, follow these steps.
Otherwise, to store the number of MFA attempts as a cookie for the length of the user's browser session, continue to the next section.
In the SecureAuth IdP, go to Advanced Settings (formerly Classic Experience).
Select the Data tab.
In the Profile Fields section, map a data store Field attribute to a profile Property to store the date and time of each invalid login attempt, and make this profile property Writable.
For example, map the
homePostalAddressfield attribute to the Aux ID 8 profile property, and select the Writable check box.Note
Directory attribute must be in Plain Text data format.
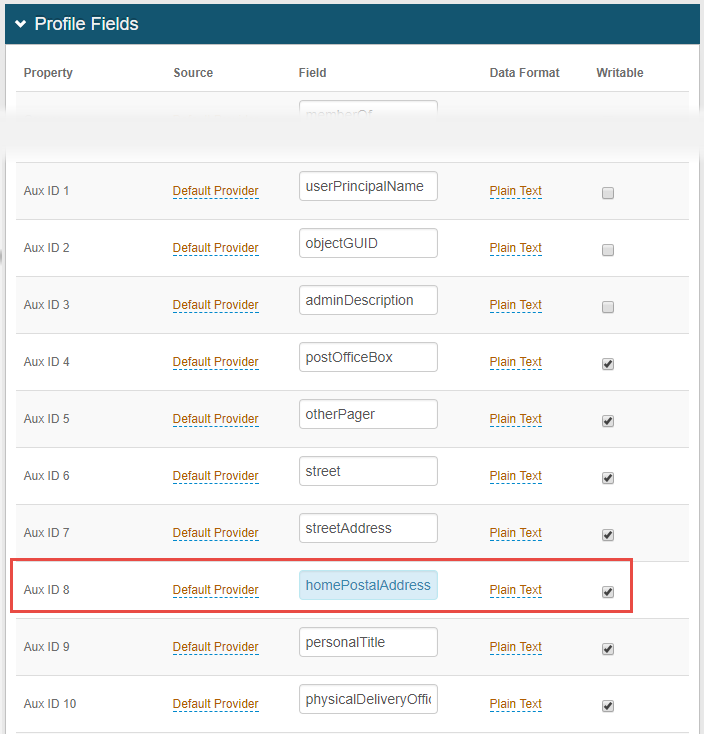
Save your changes.
Multi-Factor Methods tab configuration
In the SecureAuth IdP Advanced Settings, select the Multi-Factor Methods tab.
Scroll down the Multi-Factor Configuration section to the Multi-Factor Throttling section at the bottom.
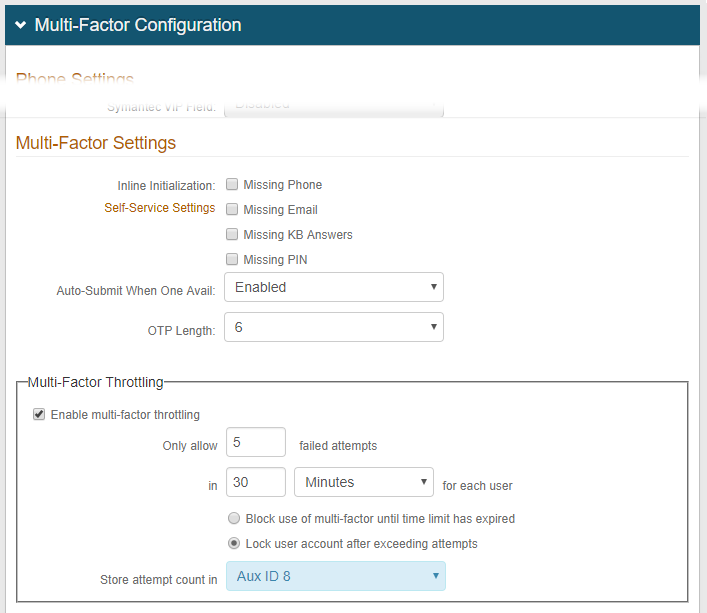
Set the following configurations:
Enable multi-factor throttling
Select this check box.
Only allow #number failed attempts in #time
Set the number of allowed authentication attempts within a moving timeframe before throttling takes effect for each user.
Action
Select what action to take when the user exceeds the allowed number of authentication attempts:
Block use of multi-factor until time limit has expired. End user cannot do another authentication attempt until the attempt count has decremented by at least one (1).
Lock user account after exceeding attempts. Lock the user account when they exceed the configured number of authentication attempts. For more information about locked accounts, see the Unlock Account page configuration guides..
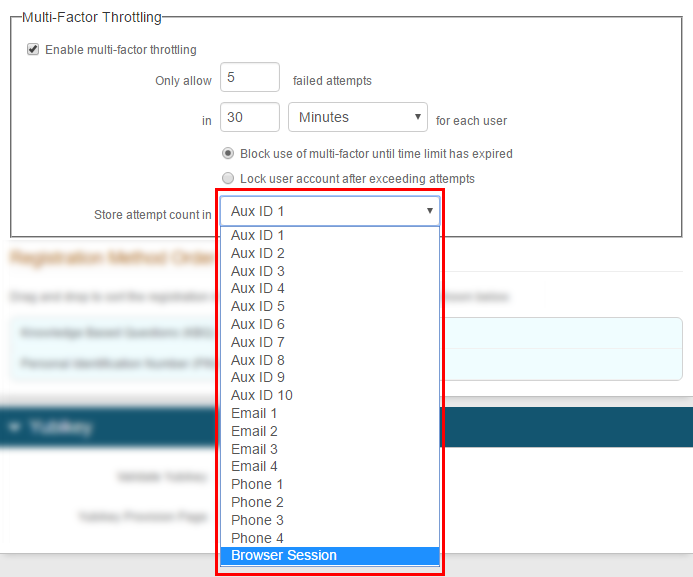
Store attempt count in
Select one of the following:
Set to the same profile property that you mapped this directory attribute to on the Data tab. For example, Aux ID 8.
Set to Browser Session to store the number of MFA attempts as a cookie for the length of the user's browser session.
Save your changes.
Throttling in the end user experience
When throttling in multi-factor authentication occurs, a message displays to the end user like the following examples.
You can customize the message by going to the Overview tab > Content and Localization and edit the registrationmethod_throttlelimit field.
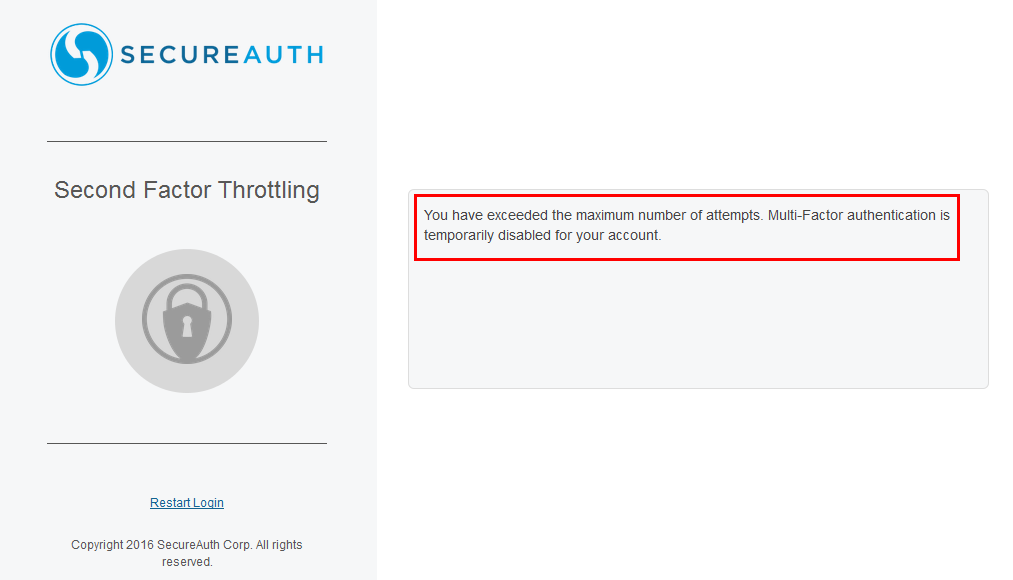
Block use of multi-factor until time limit has expired
By default, this message displays: "You have exceeded the maximum number of attempts. Multi-Factor authentication is temporarily disabled for your account."
 |
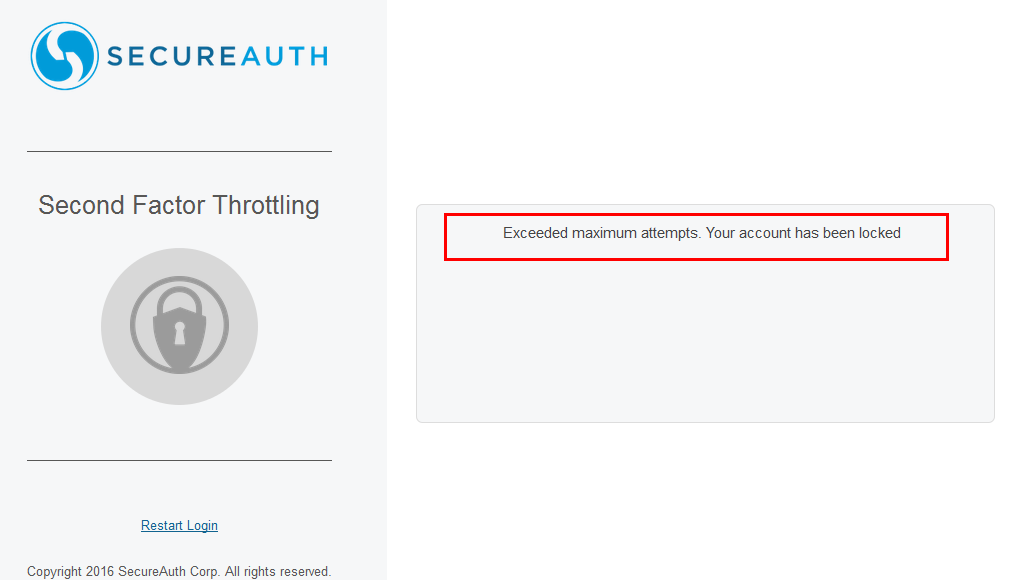
Lock user account after exceeding attempts
By default, this message displays: "Exceeded maximum attempts. Your account has been locked."
 |