How to configure the Windows Server 2016 / 2012 R2 firewall
Introduction
This document explains how to manage the Windows Advanced Firewall on a SecureAuth IdP appliance. For information on configuring a perimeter firewall, see the support document Network communication requirements for SecureAuth IdP.
NOTE: This document applies to SecureAuth IdP version 9.1 and later on Windows Server 2016 / Windows Server 2012 R2. Graphics from Windows Server 2012 R2 are included in this document.
CONTENTS:
Configuration steps
Firewall settings management
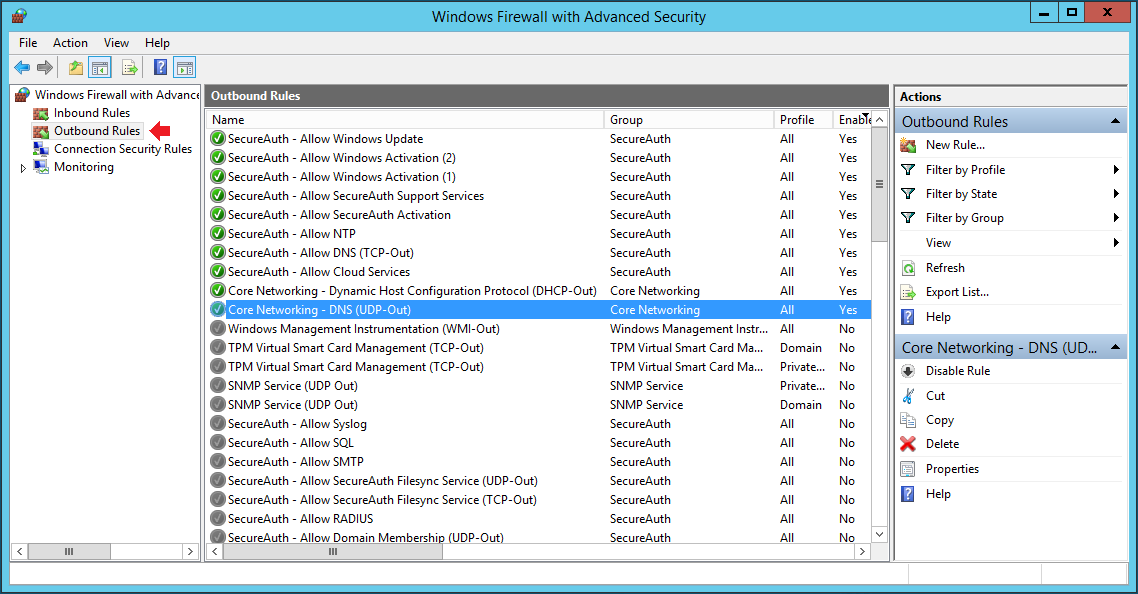
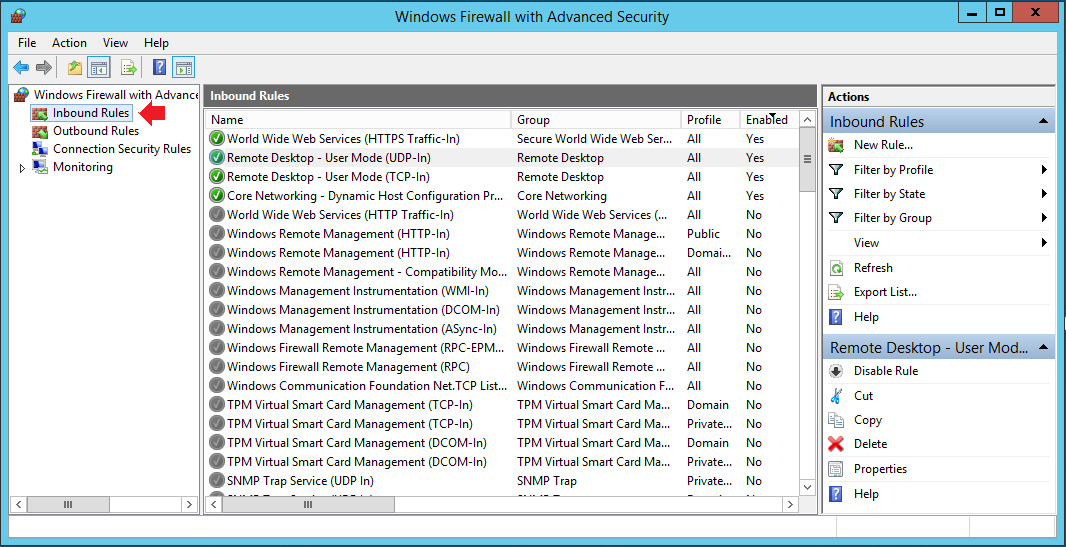
Windows Firewall with Advanced Security is a host-based firewall included with Windows Server 2012 and enabled by default on all SecureAuth IdP appliances. Firewall settings within Windows Server 2012 are managed from within the Windows Firewall MMC (Microsoft Management Console).
Do the following to review and configure firewall settings:
1. Open Windows Firewall with Advanced Security.
If using the Windows interface:
a. Click Start > All Programs > Administrative Tools > Windows Firewall with Advanced Security
b. If the User Account Control dialog box appears, confirm that the action it displays is what you want, and then click Continue
If using the command prompt:
a. Open a command window
b. Type wf.msc and press Enter
c. If the User Account Control dialog box appears, confirm that the action it displays is what you want, and then click Continue
2. First review the Required Rules to ensure they are securely configured, then review the Optional Rules to see which of them should be activated in your environment.
Required rules
DNS
By default, the DNS rules on the SecureAuth IdP Appliance allow it to communicate with any DNS server for greater ease during the initial configuration. Post configuration security best practices recommend restricting communication to only trusted DNS servers on your network. Follow the instructions below to only include DNS traffic from DNS servers within your organization.
Network Time Protocol (NTP)
By default, the NTP rule on the SecureAuth IdP Appliance allows it to communicate with any (S)NTP server for greater ease during the initial configuration. Post configuration security best practices recommend restricting communication to only trusted (S)NTP servers on your network. Follow the instructions below to permit NTP traffic only to servers within your organization.
Remote Desktop
By default, a SecureAuth IdP Appliance allows any IP address to initiate a Remote Desktop session for greater ease during the initial configuration. Post configuration security best practices recommend restricting communication to only trusted IPs or a range of trusted IPs to maximize security on the appliance. Follow the instructions below to restrict Remote Desktop traffic.
Optional rules
Active Directory / LDAP
If the SecureAuth IdP Appliance will be communicating with a Microsoft Active Directory (AD) domain controller or an LDAP server, the following rules must be enabled and configured.
Active Directory password reset
If the SecureAuth IdP Appliance will be using Microsoft Active Directory as a Data Store and you would like to leverage the Password Reset IdM functionality, the following rules must be enabled and configured.
Joining a domain
If the SecureAuth IdP Appliance will be joined to a Microsoft Active Directory domain, the following rules must be enabled and configured.
SQL
If the SecureAuth IdP Appliance will use a SQL server as a Data Store and/or for reporting, the following rule must be enabled and configured.
SMTP
If the SecureAuth IdP Appliance will send One Time Passwords (OTP) via Email, the following rule must be enabled and configured.
Syslog
If the SecureAuth IdP Appliance will be using Syslog for reporting, the following rule must be enabled and configured.
RADIUS
If the SecureAuth IdP Appliance will be hosting the RADIUS service, the following rule must be enabled and configured.
SecureAuth FileSync service
If the SecureAuth IdP Appliance will be participating in a FileSync cluster, the following rules must be enabled and configured.