Clickjacking Vulnerability and SecureAuth IdP
Issue
Clickjacking is a malicious practice that tricks a web user into clicking an object to access a seemingly innocuous web page, but in actuality has the user accessing content that potentially reveals confidential information or gives control of the user's computer to another party.
A clickjack takes the form of embedded code or a script that can execute without the user's knowledge, such as clicking a button that appears it would perform another function.
Applies to
This browser security issue is a vulnerability across a variety of browsers and platforms, and affects:
SecureAuth IdP Version | OS Version |
|---|---|
7.x+ |
|
Solutions
Attacks can be mitigated by applying the recommended settings to each SecureAuth IdP Web Admin and / or IIS
Notice
SecureAuth IdP Web Admin and / or IIS settings can be applied together or separately, depending on the use case
SecureAuth IdP Web Admin
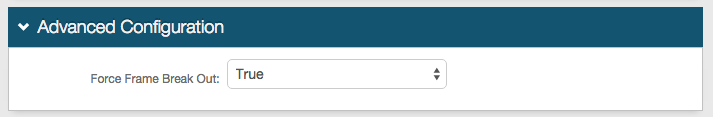 |
1. On the System Info tab, scroll to the bottom of the page, and locate the Advanced Configuration section
2. Select True from the Force Frame Break Out dropdown
Notice
This is the default selection for SecureAuth IdP appliances
Warning
Click Save once the configurations have been completed and before leaving the System Info page to avoid losing changes
3. Repeat these steps as necessary on each realm
IIS
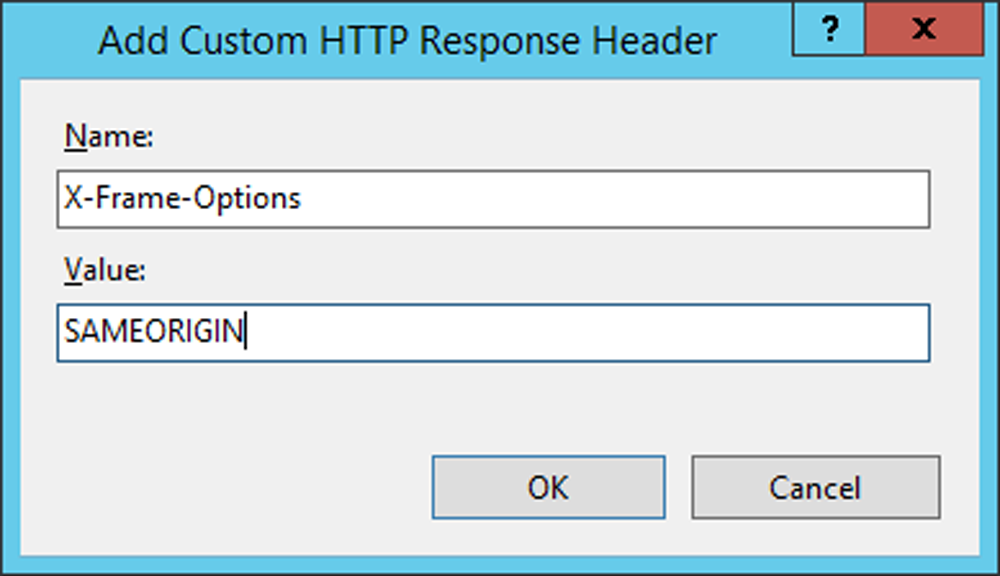 |
1. Add the X-Frame-Options header on IIS, which applies globally, versus applying this setting on the realm level, as described in the SecureAuth IdP Web Admin option
2. Set the Value to SAMEORIGIN
Warning
Ensure that the HTTP header value does not break application functionality
For example, with Blackberry OTP or Windows Desktop OTP applications, iFrame must run properly; therefore this configuration change cannot be completed
If Blackberry OTP and Windows Desktop OTP apps are necessary in the environment, then the Force Frame Break Out option must be set to False in the OATH Provisioning Realm / App Enrollment Realm (typically SecureAuth998)
Note
SecureAuth announced the end of life for Blackberry OTP and Windows Desktop OTP apps on September 22, 2016