Connect Exabeam UEBA to SecureAuth IdP
This topic describes how to connect Exabeam UEBA to SecureAuth IdP to enable adaptive authentication user risk checks.
Exabeam takes existing security-related output from logs and log systems (example: Splunk) and analyzes that data for anomalous behavior in a process called Stateful User Tracking. Indicators of anomalous behavior include usage patterns like time of day, location, device, VPN connection, and credentials. Exabeam then assigns the user a risk score.
SecureAuth IdP accesses that score via API and then takes action based on the level of threat indicated by that score. As an administrator, you can configure score thresholds for High, Medium and Low risk behavior and assign an action to take for each level.
For each level of user risk (High, Medium, and Low) you can define which action SecureAuth IdP is to take as described in risk check actions.
Prerequisites
SecureAuth IdP realm configured with an application integration
Optional: Prevent package license to use the machine learning user risk score analysis feature – contact SecureAuth Support
Existing, on-premises installation of Exabeam UEBA
Trusted certificate installed on the Exabeam server
SecureAuth IdP configuration
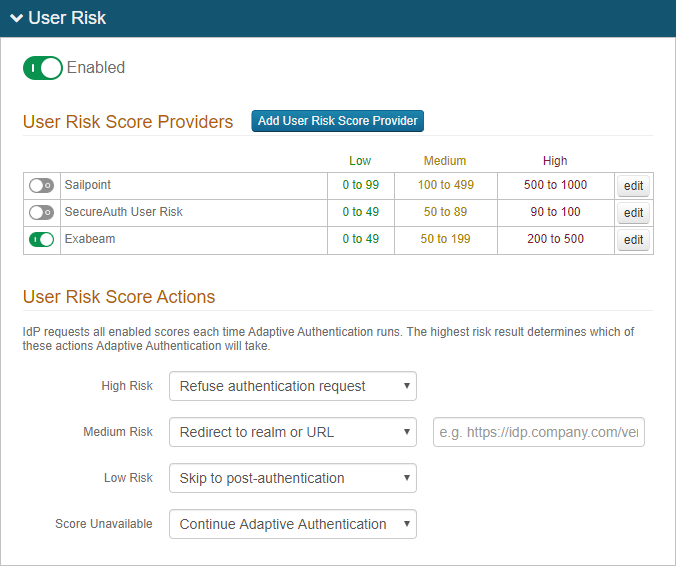
Select the Adaptive Authentication tab.
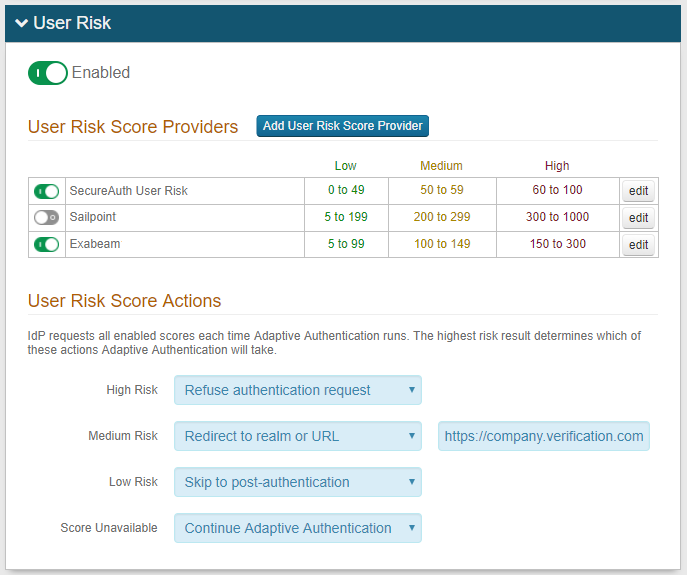
In the User Risk section, move the slider to Enabled for the User Risk analysis feature.
Click Add User Risk Score Provider or edit an existing Exabeam configuration.
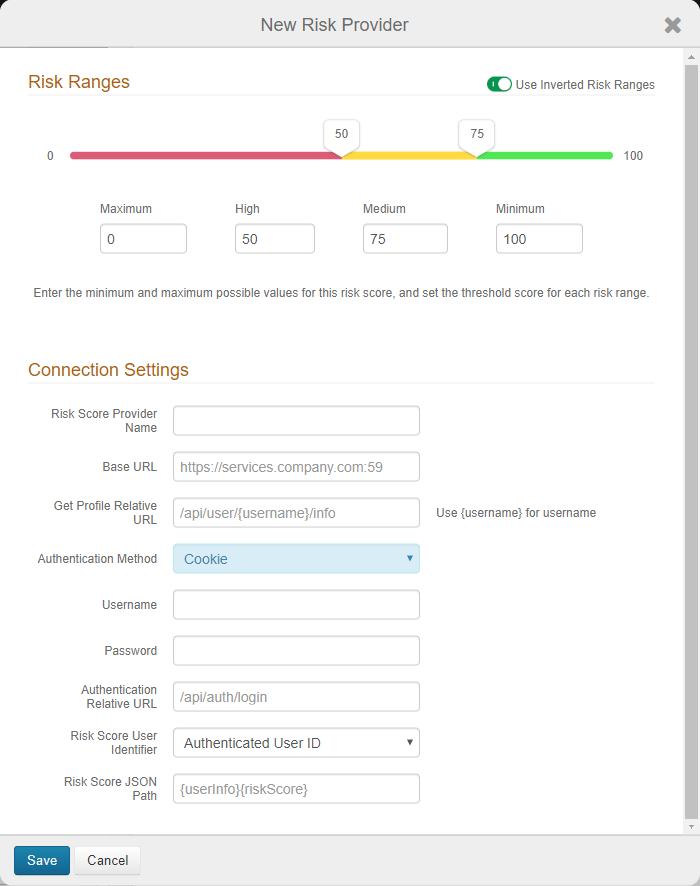
On the risk ranges configuration page, set the following:
Risk Ranges
Configure the risk ranges for Minimum, Medium, High, and Maximum risk scores.
By default, a low score indicates a good user, and a high score indicates a risky user.
Alternatively, you can set the risk ranges in reverse order by moving the slider to enable Use Inverted Risk Ranges.
With inverted risk ranges, a low score indicates a risky user, and a high score indicates a good user.
Risk Score Provider Name
Set the descriptive name for the risk provider.
Base URL
Set the base URL of the Exabeam instance in this format: https://services.company.com:59.
Get Profile Relative URL
Set the endpoint of the REST API provider in this format: /api/user/{username}/info.
Insert the {username} variable in the position the endoint expects the userID to be in the string.
Authentication Method
Set to Cookie as the authentication method supported by the REST service.
Username
Set the username of the Exabeam service account to which it has access to retrieve user profile information.
Password
Provide the password associated with the Username.
Authentication Relative URL
Set the URL endpoint used for authentication by the REST service in this format: /api/auth/login.
Risk Score User Identifier
Set the target user ID in the format to which the user risk provider expects to identify end users. It most cases, it is the same value as the default User Authenticated ID. In other cases, the user risk provider might use a different user ID; for example, the end user logs in with a sAMAccount name, but the user risk provider uses an email address as the user identifier.
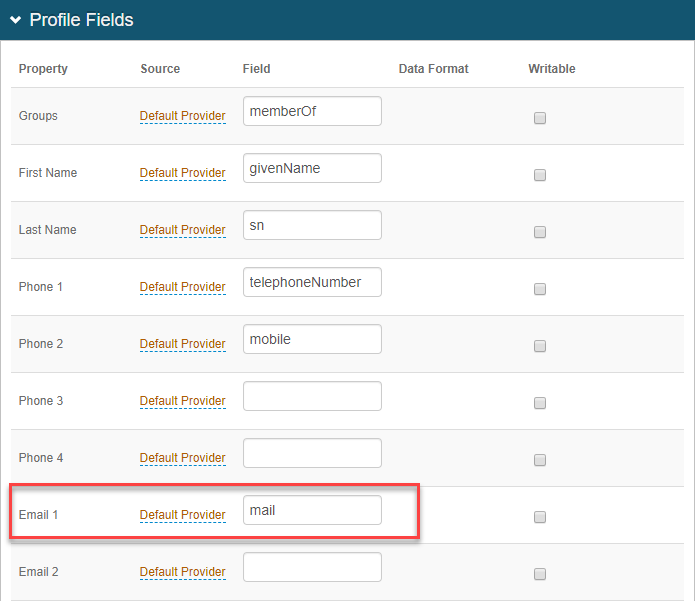
To use another user identifier, you must map that field to a property in the Data tab. Then, from the Risk Score User Identifier list, select the mapped Property.
For example, on the Data tab, in the Profile fields section, Email 1 field is mapped as a Default Provider source with a field entry of mail. So, for the Risk Score User Identifier field, you would select Email 1.
Risk Score JSON Path
Set the risk score JSON path values used to parse the JSON string returned to SecureAuth IdP and to extract the numeric score value from it. See the following table for example JSON path values.
Risk Score JSON path
Example JSON response
{userInfo}{riskScore}{ "status": true, "user": "rfobber", "userInfo": { "riskScore": 90, }, }{risk_score}{ "status": found, "userID": "rfobber", "risk_score": 0 }
Save the Exabeam user risk configuration.
Under User Risk Score Actions, for each risk range (High, Medium, Low, and Score Unavailable), specify the adaptive authentication action SecureAuth IdP takes when the user risk score falls within the specified range.
For more information about the actions to take, see the risk check actions definitions.
The Score Unavailable risk score can occur when the user is not found in the data source or does not have an assigned risk score in the data source.
If the SecureAuth IdP is unable to communicate with the data source, see the Knowledge base article Unable to Communicate with the User Risk Adaptive Authentication Data Provide for more information.
Save the configuration.
To update the risk provider configuration, click edit in the far right column.
To delete the risk provider, click edit in the far right column, and on the edit page, click Delete Risk Provider.