SecureAuth IdP version 9.3 architecture
SecureAuth IdP version 9.3 introduces cloud-based, administrative components for front-end and storage configuration. Data stores and integrated applications are configured on the New Experience user interface hosted in the cloud, and all objects configured on this user interface are stored in the cloud. The on-premises, SecureAuth IdP appliance stores all other administrative components configured on the Classic Experience Web Admin user interface.
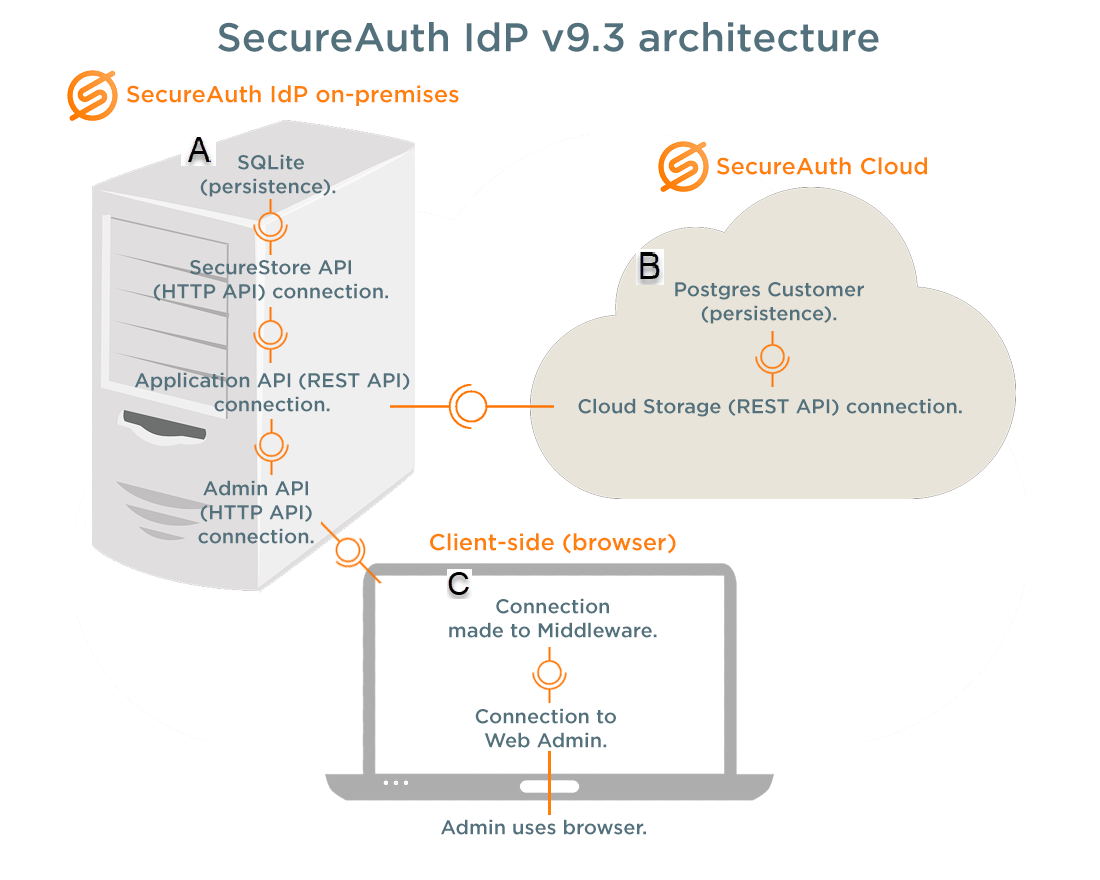 |
 SecureAuth IdP on-premises (appliance)
SecureAuth IdP on-premises (appliance)
The on-premises appliance hosts configuration data, APIs that communicate with the cloud and Web Admin, and a new Secure Storage database. Admin API calls are used in Web Admin and appliance communications. The internal Application API makes calls to the customer cloud database and Secure Storage API. The latter API stores credential information locally on the appliance, avoiding credential storage in the cloud.
 SecureAuth IdP client-side (browser)
SecureAuth IdP client-side (browser)
Access the New Experience Web Admin through a SecureAuth IdP client-side browser that connects to the U.S.-based, Amazon Simple Storage Service (Amazon S3). Admin API calls, contained in the middleware data layer, enable communications with the on-premises SecureAuth IdP appliance. The template rendering engine reads and renders JSON files and inputs on the page, and then submits data objects to APIs. API logging code is stored in Utilities.
 SecureAuth Cloud
SecureAuth Cloud
The U.S.-based AWS S3 hosts the SecureAuth Cloud that communicates with SecureAuth IdP on-premises via authenticated APIs, and includes the REST API cloud storage. The container-based, customer-specific repository stores directory and application integration data from the Web Admin configuration. Sensitive data, such as directory integration credentials and user data, are not stored in the SecureAuth Cloud.
Logs
View information on communications between SecureAuth IdP and cloud components in logs at:
D:\Secureauth\ApplicationApi > nlog-all-20XX-XX-XX.log
View data stores and applications configuration data in logs at:
D:\Secureauth\ApplicationApi\CloudContent
For the latter log, a JSON file with a cached configuration is used if SecureAuth Cloud is unresponsive.
Data Store data records
Information SecureAuth IdP requires to access the Active Directory or SQL Server provider is stored only in the SecureAuth Cloud. These settings are not written to the web.config file of a SecureAuth IdP realm, because data stores are configured as reusable objects.
Service Account credentials are not stored in the SecureAuth Cloud – these credentials provided by the administrator in the New Experience user interface are sent to the SecureAuth IdP appliance where they are extracted from the data store record and saved to a local Secure Storage database. The record sent to cloud storage contains only a randomly-generated ID that is used to access the credentials on the SecureAuth IdP appliance when the data store record is retrieved.
The most sensitive data stored in SecureAuth Cloud is the customer's directory connection – for example: LDAP://secureauth.local/DC=secureauth,DC=local
Application data records
The configuration data for an application integration is stored in the SecureAuth Cloud and in the web.config file on the SecureAuth IdP appliance. SecureAuth Cloud stores integration settings supplied by the administrator and pre-configured values in application templates – for example: Login URLs, Issuer, Name ID Mapping, etc., as well as a list of data stores associated with the application integration.
This list does not include data store configuration settings. No usernames or passwords are stored in application data records.
The most sensitive data stored in SecureAuth Cloud is the customer's specific application URL – for example: https://login.salesforce.com?so=00Dd0000000bbbb
SecureAuth Cloud failover
In the event of a SecureAuth Cloud communication failure, SecureAuth IdP Web Admin pulls configuration information from the cached file and displays these settings in the user interface until Cloud communications resume. Locate the latest cache of your configuration at:
D:\Secureauth\ApplicationApi\CloudContent