What's new
Read on to learn more about new features and improvements in SecureAuth IdP version 9.3.
New and Classic Experience Web Admin
SecureAuth IdP version 9.3 introduces the New Experience user interface to configure Web Admin components. This Web Admin user interface is separate from the familiar Web Admin user interface called the Classic Experience in this release.
Refer to this set of documents for an overview on the New Experience and Classic Experience Web Admin user interfaces, and how to navigate between them:
Classic Experience Web Admin changes
SecureAuth IdP version 9.3 includes new features and enhancements affecting some tabs on the Classic Experience Web Admin as described below.
Workflow tab
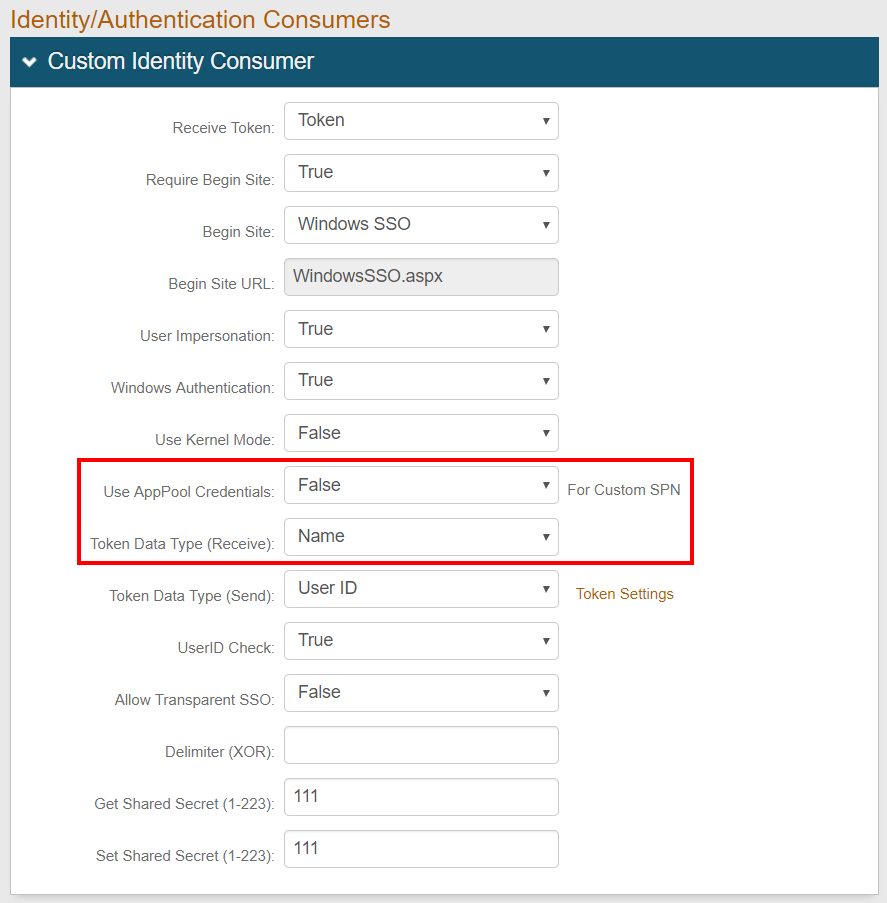
Custom Identity Consumer section
Two new fields accommodate environments in which custom Service Principal Names are used for Integrated Windows Authentication (Kerberos). Use Kernel Mode and Use AppPool Credentials can be enabled to use kernel mode authentication and application pool credentials (Active Directory service account). Previously, these entries were made in the web.config editor.
Configure these fields for a Windows desktop SSO configuration.
 |
Adaptive Authentication tab
Adaptive Authentication section
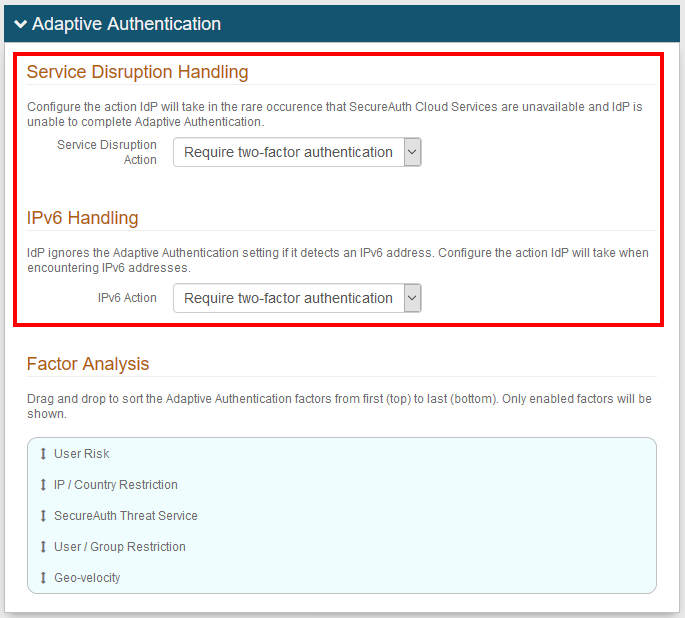
Two new Adaptive Authentication fields can be configured to set the Adaptive Engine action for scenarios in which end-users are unable to authenticate.
Service Disruption Handling – in this scenario, with SecureAuth Cloud Services unavailable, end-users will not be able to use any authentication method that requires processing by SecureAuth Cloud Services.
IPv6 Handling – in this scenario, SecureAuth IdP is passed an IPv6 address (which it is unable to process), so the end-user cannot be authenticated.
Make these settings for the Adaptive Authentication configuration.
 |
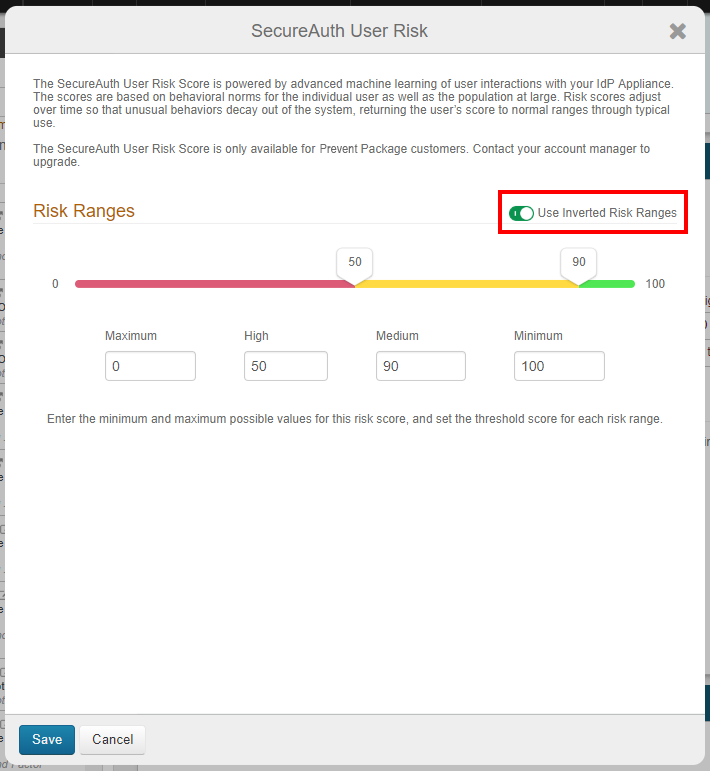
User Risk section
The new Use Inverted Risk Ranges toggle switch can be enabled to show high score Risk Ranges for good users, and low scores for risky users. This setting accommodates third-party providers such as NetSkope that deliver scores in descending order.
Make these settings in the Adaptive Authentication configuration for user risk, or for third-party providers such as Exabeam UEBA or SailPoint IdentityIQ.
 |
Multi-Factor Methods tab
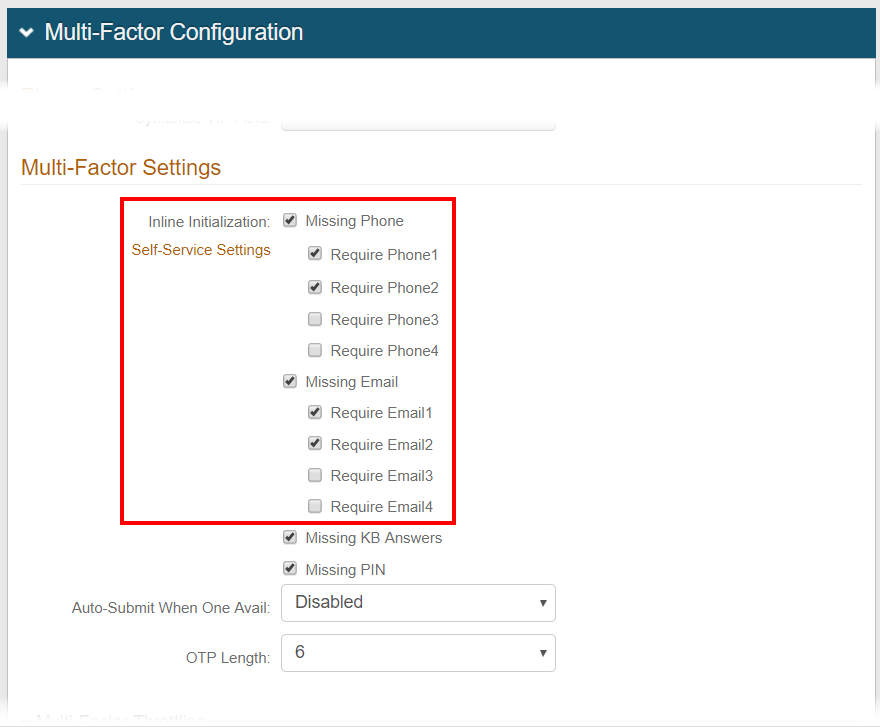
Multi-Factor Configuration section
Under Inline Initialization Self-Service Settings, the new Require Phone 1 - 4 and Require Email 1 - 4 check boxes can be enabled for up to four different types of phone numbers and four different types of email addresses to be required in a user's profile.
Configure these settings for Inline Initialization - Self-service.
 |
Post Authentication tab
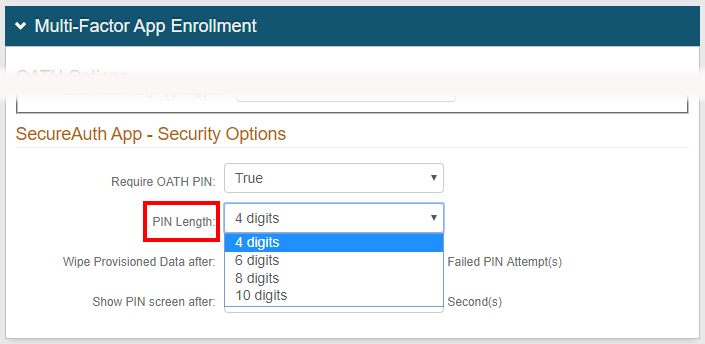
Multi-Factor App Enrollment section
The new PIN Length field enables a 4, 6, 8, or 10-digit PIN to be configured as a security setting for use on:
SecureAuth Authenticate app (version 5.2 and later)
SecureAuth Passcode for Windows / Mac app (version 2.0 and later) works with a 4-digit PIN only
If configured, users of these apps will be required to enter a PIN of the configured length to view the TOTP on the app.
Configure these settings under SecureAuth App - Security Options, as described in:
 |
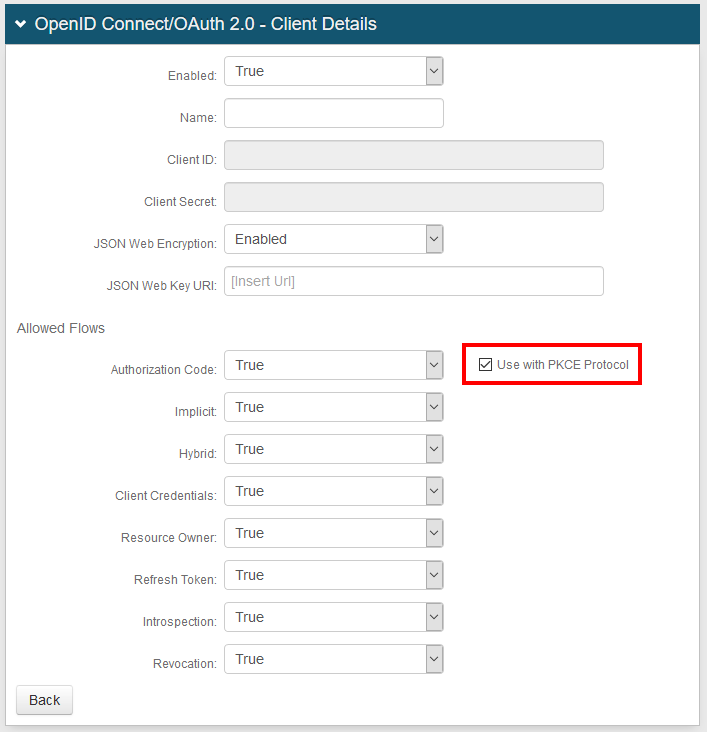
OpenID Connect / OAuth 2.0 - Client Details section
The new Use with PKCE Protocol check box enables secure access to native and mobile apps via the Authorization Code with Proof Key for Code Exchange (PKCE).
Enable this setting in OpenID Connect and OAuth 2.0 configuration.
 |
System Info tab
Links section
The Web Config Editor link (Click to edit Web Config file.) is removed from this section, ensuring greater security on the SecureAuth IdP appliance.
To edit the web.config file, go to D:\SecureAuth\SecureAuth1 on the appliance.
See System Info configuration for information on using the System Info tab in version 9.3.
 |