Use IP / Country Restriction as a risk check
You can define user access based on country codes or IP addresses.
Go to the Adaptive Authentication tab.
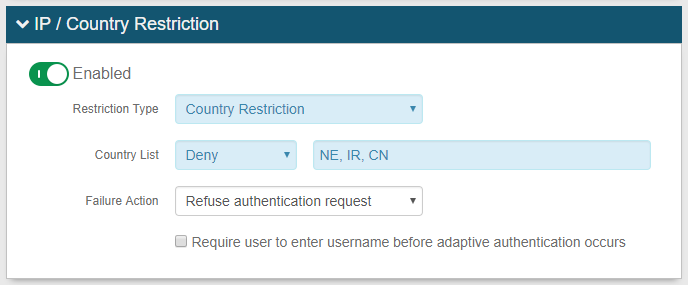
In the IP / Country Restriction section, move the slider to Enable.
Set the following:
Restriction Type
Rule to determine access by a restriction type:
Country Restriction – Restricts access by one or more country codes
IP Restriction – Restricts access by one or more IP addresses
Country List / IP List
Choose whether to allow or deny access to a resource (realm) when the user login originates from a specific country code or IP address:
Allow – Allow access when the user login is within the defined country code or IP address
Deny – Deny access when the user login is within the defined country code or IP address
Provide a list of one or more country codes or IP addresses to allow or deny access. Country codes must be listed in the two-letter ISO format.
IP addresses can be entered in any of the following formats, separated by a comma:
Specific IP address – for example:
72.32.245.182CIDR Notation – for example:
72.32.245.0/24IP range – for example:
72.32.245.1-72.32.245.254
Different formats can be used in the same field. For example, this entry is valid:
72.32.245.182,72.32.245.0/24,72.32.245.1-72.32.245.254Failure Action
Specify the adaptive authentication action SecureAuth IdP takes when the user is allowed or denied access to a protected resource (realm).
For more information about the actions and its descriptions, see the risk check action definitions.
Require user to enter username before adaptive authentication occurs
To require end users to provide their username before a country or IP address is analyzed, select this check box.
Save your changes.