Certificate Finder (V1 and V2) Begin Site Configuration Guide
Introduction
Use this guide to enable a SecureAuth IdP realm to utilize a Certificate Finder begin site.
At this begin site, SecureAuth IdP can search for a Java certificate and extract the user ID from it. From there, the end-user follows the SecureAuth IdP workflow configured in the realm (e.g. Multi-Factor Authentication) without requiring to enter the user ID, and is asserted to the Post Authentication target.
SecureAuth IdP includes Certificate Finder V1 and Certificate Finder V2 begin sites. They perform the same functions; but Certificate Finder V2 includes a master page that alerts end-users that SecureAuth IdP is checking for a certificate and resembles the login page theme, whereas Certificate Finder V1 displays only a blank page.
Prerequisites
1. Have a valid Java certificate from which SecureAuth IdP can extract the user ID
2. Create a New Realm or edit an existing realm to which Certificate Finder will be applied in the SecureAuth IdP Web Admin
3. Configure the following tabs in the Web Admin before configuring for Certificate Finder:
Overview – the description of the realm and SMTP connections must be defined
Data – an enterprise directory must be integrated with SecureAuth IdP
Workflow – the way in which users will access the target must be defined
Multi-Factor Methods – the Multi-Factor Authentication methods that will be used to access the target (if any) must be defined
Post Authentication – the target resource or post authentication action must be defined
Logs – the logs that will be enabled or disabled for this realm must be defined
SecureAuth IdP Configuration Steps
Workflow
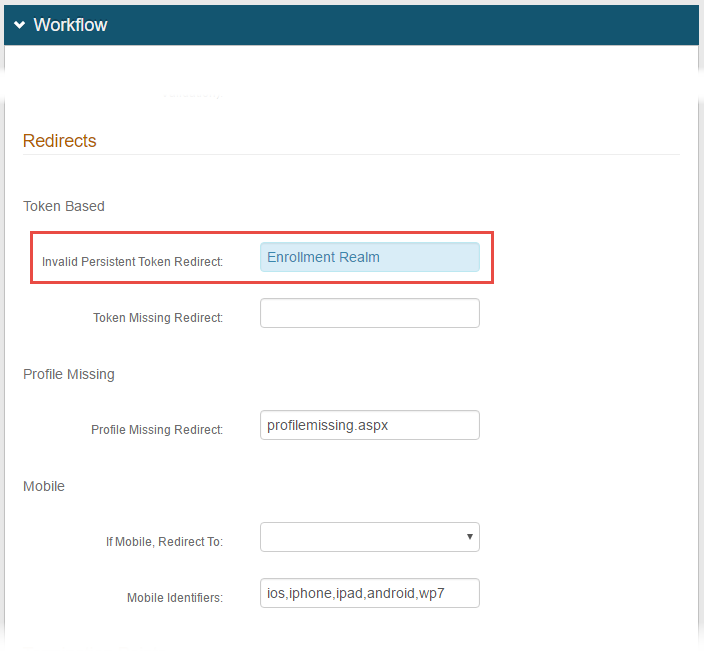 |
1. In the Workflow section under Redirects, set the Invalid Persistent Token Redirect to the SecureAuth IdP realm in which end-users can enroll for a certificate
If end-users land on the Certificate Finder begin site without a valid Java certificate, then they are redirected to this realm to enroll for a certificate that can then be used for the begin site
Custom Identity Consumer
 |
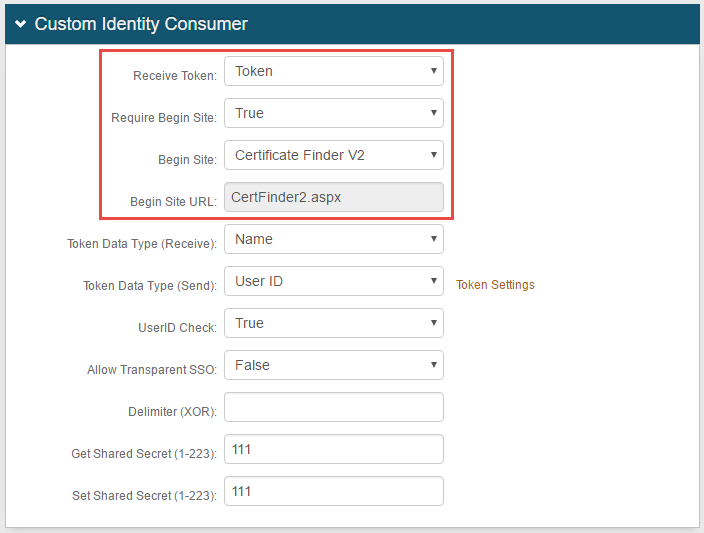 |
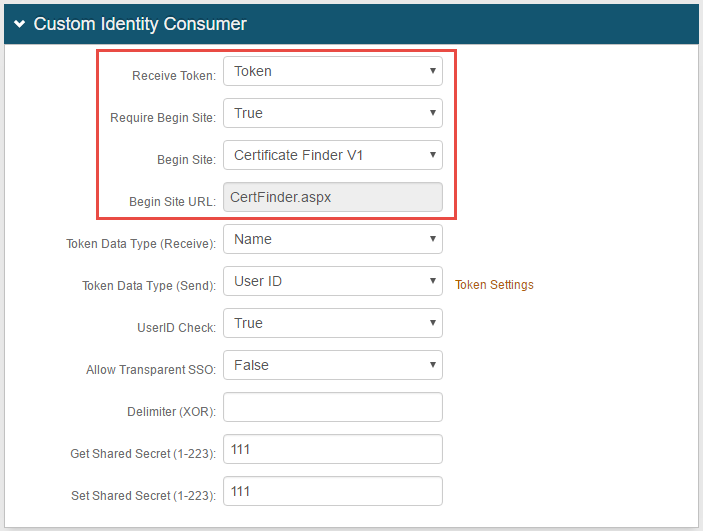
2. Select Token from the Receive Token dropdown
3. Select True from the Require Begin Site dropdown
4. Select Certificate Finder V1 or Certificate Finder V2 from the Begin Site dropdown
5. CertFinder.aspx or CertFinder2.aspx auto-populates in the Begin Site URL field
Warning
Click Save once the configurations have been completed and before leaving the Workflow page to avoid losing changes