Amazon WorkSpaces Integration Guide (RADIUS)
Introduction
Use this guide to enable Multi-Factor Authentication for an AD Connector directory via RADIUS to Amazon WorkSpaces, the secure, virtual cloud desktop running on AWS.
Prerequisites
1. Have the following items:
AD Connector – see AWS Direct Connect
Amazon WorkSpaces, configured and tested
2. Have a supported RADIUS client
3. Install and configure the SecureAuth IdP RADIUS service on the SecureAuth IdP appliance
4. Configure the Multi-Factor App Enrollment (QR Code) Realm for the RADIUS OTP authentication requests
Or, optionally configure the Multi-Factor App Enrollment (URL) Realm (SecureAuth998) for RADIUS OTP authentication requests
SecureAuth RADIUS Admin Console Configuration Steps
 |
1. Configure RADIUS Server Settings and IdP Realms. See the SecureAuth RADIUS Server documentation.
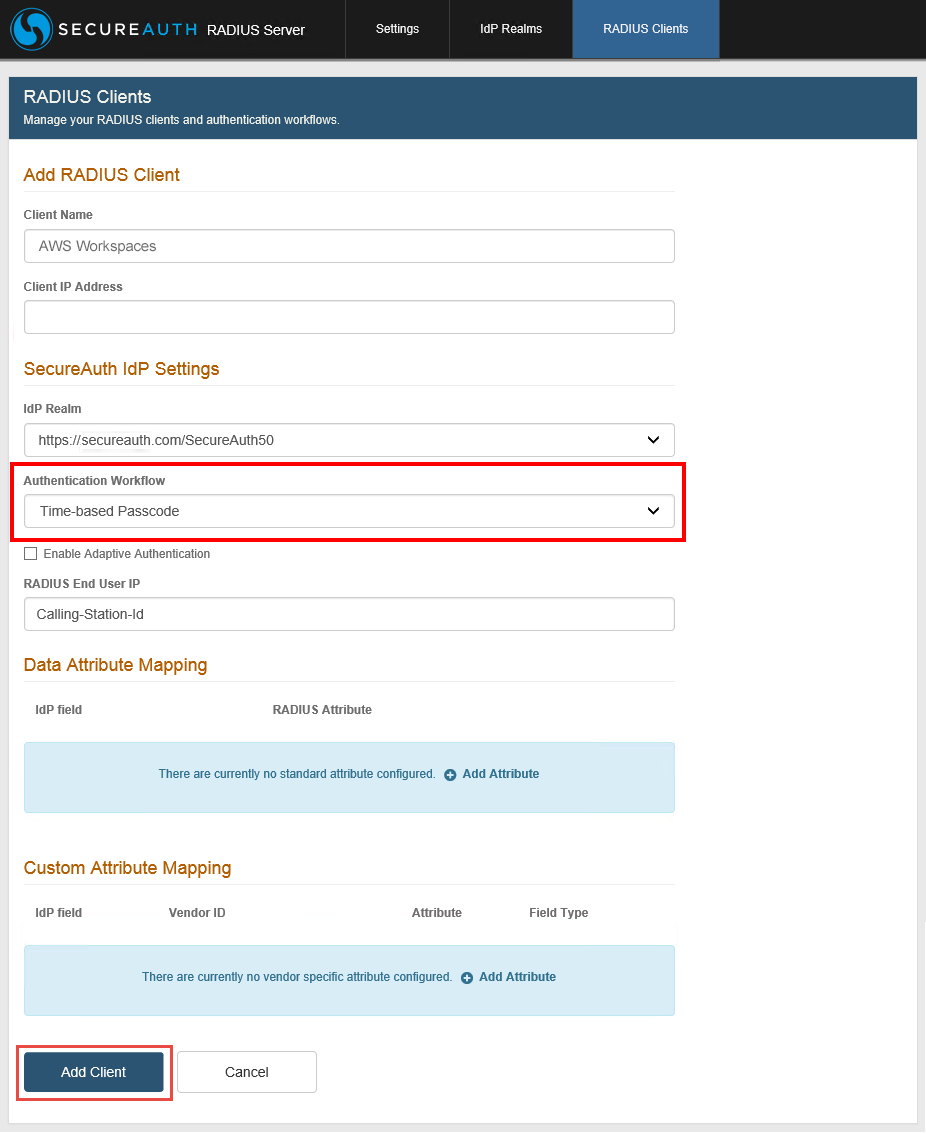
2. When configuring RADIUS Clients, follow these steps under Add RADIUS Client and SecureAuth IdP Settings:
a. Enter the Client Name – e.g. AWS Workspaces
b. Enter the Client IP Address
c. Select the IdP Realm from the dropdown
d. Select Time-based Passcode from the Authentication Workflow dropdown – this is the only selection that should be made
3. After configuring other necessary settings, click Add Client
AWS Directory Service Console Configuration Steps
 |
1. Log on AWS WorkSpaces, and in the AWS Directory Service console navigation pane, select Directories
2. Select the directory ID link to the AD Connector directory
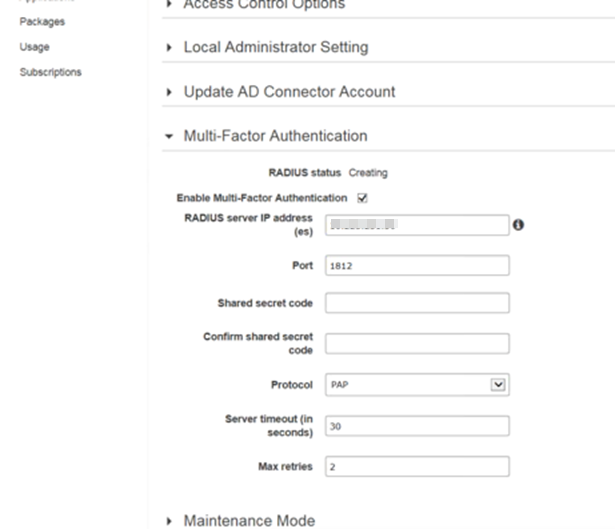
3. Select the Multi-Factor Authentication tab
4. Check the Enable Multi-Factor Authentication box
5. Enter the RADIUS server IP address(es) of the SecureAuth IdP RADIUS Server
6. Set the RADIUS server Port number to 1812 for RADIUS server communications
The on-premises network must allow inbound traffic via the default RADIUS server port (1812) from AWS Directory Service servers
7. Enter the same Shared secret code that was entered on the SecureAuth IdP RADIUS Server, and Confirm shared secret code
8. Select PAP from the Protocol dropdown – this should be the setting configured on the SecureAuth IdP RADIUS Server
9. Set the Server timeout (in seconds) to 60 seconds to wait for the RADIUS server to respond
10. Set the number of Max retries to 10 attempts for communicating with the RADIUS server
Note
NOTE: Multi-Factor Authentication is available when the RADIUS Status is set to Enabled