Blackberry SecureAuth Mobile OTP App Troubleshooting / Common Issues
Introduction
Use this guide to resolve common issues presented with the SecureAuth Mobile OTP App for Blackberry.
Notice
SecureAuth announced the end of life for these products on September 22, 2016
Product | Version | Release Date | Removal from App Store |
|---|---|---|---|
SecureAuth OTP for Blackberry | 3.1.0.20 | June 24, 2014 | October 20, 2016 |
SecureAuth OTP RC for Blackberry | 0.0.1.1 | July 31, 2015 | October 20, 2016 |
NOTE: If currently installed on the end-user mobile device, either app can still be used, as long as it is not deleted from the device
However, no new updates will be provided, and once deleted, the app cannot be reinstalled
Force Frame Breakout
Follow these configuration steps to ensure the Blackberry Mobile OTP App properly loads pages
SecureAuth IdP Web Admin
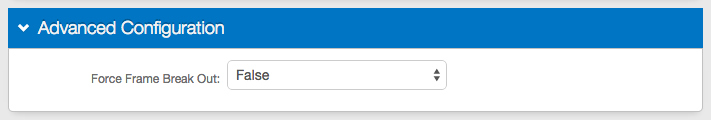
1. In the Advanced Configuration section, select False from the Force Frame Break Out dropdown
 |
Warning
Click Save once the configurations have been completed and before leaving the System Info page to avoid losing changes
IIS
2. In IIS Manager, expand Sites, go to Default Website, and select the OATH Provisioning Realm / SecureAuth App Enrollment Realm (e.g. https://secureauth.company.com/secureauth998)
3. Double-click the HTTP Response Headers icon in the feature list
4. Locate X-Frame-Options and remove entirely
5. Click OK to save changes
Confirm Changes
1. To confirm the changes, open a Chrome browser and browse to the OATH Provisioning / SecureAuth App Enrollment Realm
2. Access the Developer Tools
3. Select the Network tab, and click Record (red circle)
4. Refresh the page, and select secureauth998/ (or the realm being used)
5. Confirm that under Response Headers, no X-Frame-Options appear
Web Service Requirements
Follow these steps if using Web Service (Multi-Data Store) in the OATH Provisioning / SecureAuth App Enrollment Realm
Data Tab
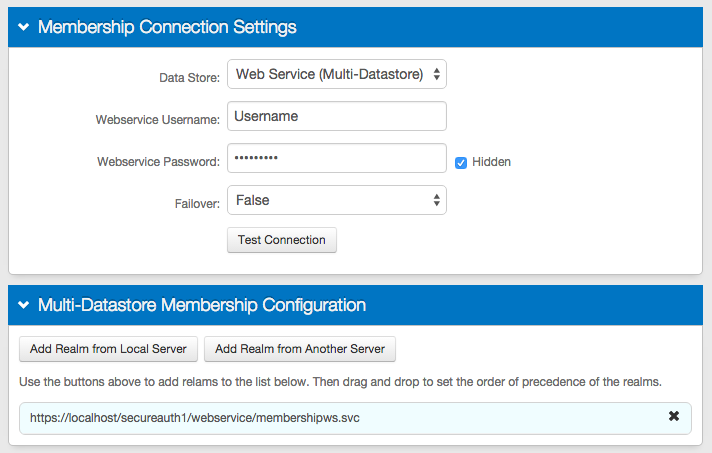 |
If in the OATH Provisioning Realm / SecureAuth App Enrollment Realm (e.g. SecureAuth998) utilizes the Web Service (Multi-Data Store) option (as shown in image), then the Server URL must be set to https://<SecureAuthIdPFQDN>/<OATHProvisioningRealm>/WebService/ProfileWS.svc in the application enrollment process, e.g. https://secureauth.company.com/secureauth998/WebService/ProfileWS.svc