Palo Alto VPN Integration Guide (RADIUS)
Introduction
Use this guide to enable Multi-Factor Authentication access via RADIUS to Palo Alto Networks (PAN) VPN.
Prerequisites
1. Have PAN-OS 5.0 and above
2. Configure the Multi-Factor App Enrollment Realm (SecureAuth998) in the SecureAuth IdP Web Admin for the RADIUS OTP authentication requests
3. Install and configure the SecureAuth RADIUS Server
Palo Alto Configuration Steps
 |
1. Create a RADIUS Server Profile by navigating to Server Profile > RADIUS > click Add
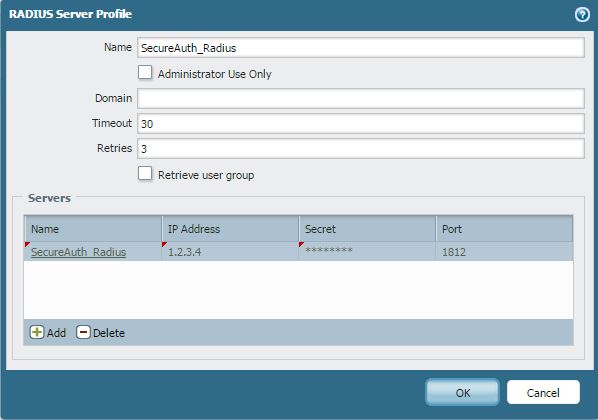
2. Name the RADIUS Server profile
Leave the Domain name Blank
Time out = 30 seconds
Retries = 3 (default)
 |
3. Add Server to the profile by clicking Add on the bottom of the profile
Name = Generic name for the RADIUS Server
IP address = IP address of the SecureAuth Server
Secret = Secret shared between Palo Alto and SecureAuth RADIUS
Port = 1812 (UDP)
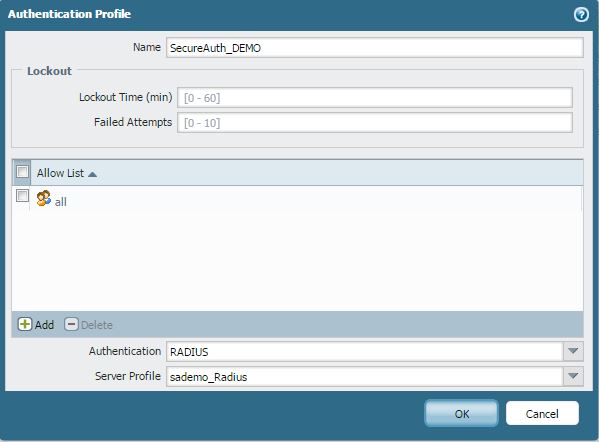 |
4. Navigate to Authentication Profile and click Add to add a new profile
5. Enter a name for the new Authentication Profile and configure the settings
6. For Authentication, select RADIUS as the authentication method
7. For Server Profile, select the SecureAuth RADIUS Profile created in step 2 and click OK
 |
8. Click the Network tab
 |
9. Navigate to the GlobalProtect Portal of the PAN by clicking Portals and then clicking Add
Tip
You can also use the existing portal, if any exists
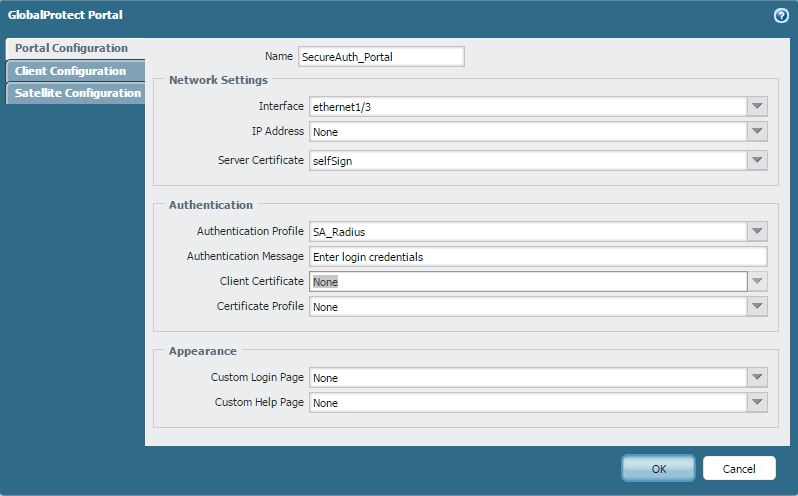 |
10. Configure the portal with the following information
Name: Enter a name for the realm
Network Setting:
Interface
IP Address
Server Certificate
Authentication:
Authentication Profile: Select the same one created in step 4
Other options can be customized as needed
11. Click OK and then test the Palo Alto Networks VPN