How to Read a Syslog Message
Introduction
Use this guide to decode the elements of a syslog message. Documentation is included for both versions of syslog messages used by SecureAuth IdP: RFC5424 and RFC3164 (legacy; generally no longer used).
Sample RFC5424 Message
<86>1 2015-08-05T21:58:59.693Z 192.168.2.132 SecureAuth0 23108 ID52020 [SecureAuth@27389 UserAgent="Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; rv:11.0) like Gecko" UserHostAddress="192.168.2.132" BrowserSession="0gvhdi5udjuqtweprbgoxilc" Realm="SecureAuth0" Appliance="secureauthqa.gosecureauth.com" Company="SecureAuth Corporation" UserID="Tester2" PEN="27389" HostName="192.168.2.132" Category="AUDIT" Priority="4"] Found the user for retrieving user's profile
Header
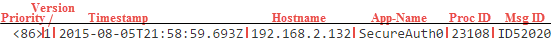 |
Element | Example | Description |
Priority | <86> | |
Facility Code: 10 Severity Code: 6 | NOTE: The Facility Code and Severity Level of a syslog message are derived from the PRIORITY value, which in this case is 86. To determine the value, divide the Priority by 8. The Facility Code is the quotient, while the Severity Level is the remainder (ex: 86/8 = 10 remainder 6). Map these numbers to the corresponding Facility Code/Severity Level tables (see below) to get the descriptions. For more information on how the priority value is calculated see section 6.2.1 in https://tools.ietf.org/html/rfc5424#section-6.2.1. | |
Version | 1 | Version of the syslog protocol specification. |
Timestamp | 2015-08-05T21:58:59.693Z | yyyy-mm-dd T hh:mm:ss.fff Z (where "f" is milliseconds). |
Hostname | 192.168.2.132 | Machine that originally sent the syslog message. |
App-Name | SecureAuth0 | Device or application that originated the message. SecureAuth IdP uses the realm name here. |
Proc ID | 23108 | Indicates any discontinuity/disruption in syslog reporting when this value changes. Typically, the process name or ID of the syslog system is used. |
Msg ID | ID52020 | Identifies the type of message. SecureAuth IdP uses the Event ID here. |
Facility Code Table
Numerical Code | Facility |
|---|---|
0 | Kernel messages |
1 | User-level messages |
2 | Mail system |
3 | System daemons |
4 | Security/authorization messages |
5 | Messages generated internally by syslogd |
6 | Line printer subsystem |
7 | Network news subsystem |
8 | UUCP subsystem |
9 | Clock daemon |
10 | Security/authorization messages |
11 | FTP daemon |
12 | NTP subsystem |
13 | Log audit |
14 | Log alert |
15 | Clock daemon |
16 | Local use 0 |
17 | Local use 1 |
18 | Local use 2 |
19 | Local use 3 |
20 | Local use 4 |
21 | Local use 5 |
22 | Local use 6 |
23 | Local use 7 |
Severity Code Table
Numerical Code | Severity |
|---|---|
0 | Emergency: system is unusable |
1 | Alert: action must be taken immediately |
2 | Critical: critical conditions |
3 | Error: error conditions |
4 | Warning: warning conditions |
5 | Notice: normal but significant condition |
6 | Informational: informational messages |
7 | Debug: debug-level messages |
Structured-Data Pairs
[SecureAuth@27389 UserAgent="Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; rv:11.0) like Gecko" UserHostAddress="192.168.2.132" BrowserSession="0gvhdi5udjuqtweprbgoxilc" Realm="SecureAuth0" Appliance="secureauthqa.gosecureauth.com" Company="SecureAuth Corporation" UserID="Tester2" PEN="27389" HostName="192.168.2.132" Category="AUDIT" Priority="4"]
Element | Example | Description |
Structured-Data ID | SecureAuth@27389 | Name:SecureAuth
PEN:27389
|
Dictionary Key-Value Pairs | UserAgent="Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; rv:11.0) like Gecko" UserHostAddress="192.168.2.132" BrowserSession="0gvhdi5udjuqtweprbgoxilc" Realm="SecureAuth0" Appliance=" secureauthqa.gosecureauth.com " Company="SecureAuth Corporation" UserID="Tester2" PEN="27389" HostName="192.168.2.132" Category="AUDIT" Priority="4" | |
Dictionary Key Name | Sample Value | |
|---|---|---|
By default, the following 4 properties are added to the Structured-Data element | ||
Priority | 3 | |
Category | AUDIT | |
HostName | 192.168.40.127 | |
PEN (Private Enterprise Number) | 27389 | |
AUDIT syslog entries (like the sample above) contain most or all of the following xml elements: | ||
UserAgent | Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; rv:11.0) likeGecko | |
UserHostAddress | 192.168.2.132 | |
BrowserSession | e7ba435a-370c-479c-9ea9-73033776cd1d | |
Realm | SecureAuth0 | |
Appliance | secureauthqa.gosecureauth.com | |
Company | SecureAuth Corporation | |
UserID | Tester2 | |
Audit syslog entries with Norse Dark Viking data contain the following additional property: | ||
AE.IP.RiskScore | 100 | |
Transaction audit syslog entries contain the following additional properties: | ||
CompanyID,ApplianceID,ApplianceMachineName,HashedUserID,ProductType,ReceiveToken,AuthGuiMode,AuthRegMethod,AuthRegMethodInfo,IsPreAuth,PreAuthPage,DestinationSiteUrl,ReturnUrl,TargetUrl,SAMLConsumerSiteUrl,SAMLRelayState,SAMLTargetUrl,Succeed,Comment,TimeStamp, &AEResult | ||
New keys added in IdP v8.1: | ||
Key Value | Description | |
AllowedTokens | Text string. Possible values are: COOKIE, ZCOOKIE, BROWSERFINGERPRINT, ALL
| |
EventID | Category of the event being logged | |
ReceivedToken | Integer value | |
RequestDuration | Displays the response time of an application request. Applicable only to log entries with EventID 9004x. | |
RequestID | Displays a unique identifier that shows the workflow for a specific request. | |
TrxResult | Displays result of an authentication attempt. | |
UseJava | True/false. Displays whether Java plugin was used during the authentication process. | |
Loading: realm | Describes the realm number that was opened in the Web Admin. | |
Saving to: realm | Describes the realm number(s) where changes were saved in the Web Admin. | |
MSG
Found the user for retrieving user's profile
Provides a free-form summary of the event being logged.
Sample RFC3164 Message
<86>Aug 17 11:43:33 192.168.40.127 SecureAuth0<Root><EventID>21010</EventID><Priority>3</Priority><Message>GetUser Success</Message><Category>AUDIT</Category><UserAgent>Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; rv:11.0) like Gecko</UserAgent><UserHostAddress>192.168.2.132</UserHostAddress><BrowserSession>e7ba435a-370c-479c-9ea9-73033776cd1d</BrowserSession><Realm>SecureAuth0</Realm><Appliance>secureauthqa.gosecureauth.com</Appliance><Company>SecureAuth Corporation</Company><UserID>Tester2</UserID><HostName>192.168.40.127</HostName></Root>
An RFC3164 syslog entry has 3 components:
PRIORITY
HEADER
MSG
PRIORITY
<86>
Element | Example | Description |
Priority | <86> | |
Facility Code: 10 Severity Code: 6 | NOTE: The Facility Code and Severity Level of a syslog message are derived from the PRIORITY value, which in this case is 86. To determine the value, divide the Priority by 8. The Facility Code is the quotient, while the Severity Level is the remainder (ex: 86/8 = 10 remainder 6). Map these numbers to the corresponding Facility Code/Severity Level tables (see below) to get the descriptions. For more information on how the priority value is calculated see section 6.2.1 in https://tools.ietf.org/html/rfc3164#section-4.1.1 |
Facility Code Table
Numerical Code | Facility |
|---|---|
0 | Kernel messages |
1 | User-level messages |
2 | Mail system |
3 | System daemons |
4 | Security/authorization messages |
5 | Messages generated internally by syslogd |
6 | Line printer subsystem |
7 | Network news subsystem |
8 | UUCP subsystem |
9 | Clock daemon |
10 | Security/authorization messages |
11 | FTP daemon |
12 | NTP subsystem |
13 | Log audit |
14 | Log alert |
15 | Clock daemon |
16 | Local use 0 |
17 | Local use 1 |
18 | Local use 2 |
19 | Local use 3 |
20 | Local use 4 |
21 | Local use 5 |
22 | Local use 6 |
23 | Local use 7 |
Severity Code Table
Numerical Code | Severity |
|---|---|
0 | Emergency: system is unusable |
1 | Alert: action must be taken immediately |
2 | Critical: critical conditions |
3 | Error: error conditions |
4 | Warning: warning conditions |
5 | Notice: normal but significant condition |
6 | Informational: informational messages |
7 | Debug: debug-level messages |
HEADER
Aug 17 11:43:33 192.168.40.127
Element | Example | Description |
|---|---|---|
Timestamp | Aug 17 11:43:33 | Local Time in the format MMM dd hh:mm:ss
|
Hostname | 192.168.40.127 | Hostname, IPv4 or IPv6 address of the originator of the message. |
MSG
SecureAuth0<Root><EventID>21010</EventID><Priority>3</Priority><Message>GetUser Success</Message><Category>AUDIT</Category><UserAgent>Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; rv:11.0) like Gecko</UserAgent><UserHostAddress>192.168.2.132</UserHostAddress><BrowserSession>e7ba435a-370c-479c-9ea9-73033776cd1d</BrowserSession><Realm>SecureAuth0</Realm><Appliance>secureauthqa.gosecureauth.com</Appliance><Company>SecureAuth Corporation</Company><UserID>Tester2</UserID><HostName>192.168.40.127</HostName></Root>
Element | Example | Description |
|---|---|---|
Tag | SecureAuth0 | Name of the program or process that generated the message |
Content | <Root><EventID>21010</EventID><Priority>3</Priority><Message>GetUser Success</Message><Category>AUDIT</Category><UserAgent>Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; rv:11.0) like Gecko</UserAgent><UserHostAddress>192.168.2.132</UserHostAddress><BrowserSession>e7ba435a-370c-479c-9ea9-73033776cd1d</BrowserSession><Realm>SecureAuth0</Realm><Appliance>secureauthqa.gosecureauth.com</Appliance><Company>SecureAuth Corporation</Company><UserID>Tester2</UserID><HostName>192.168.40.127</HostName></Root> | The Content field is formatted to be a valid xml that contains various informational properties. Each of these properties is stored in an xml element. |