Generic SAML Integration Guide
Use this guide as a reference to configuring a SAML application integration to enable Multi-Factor Authentication and Single Sign-on (SSO).
SecureAuth IdP enables both IdP- and SP-initiated SAML integrations. In IdP-initiated integrations, end-users start the login process at SecureAuth IdP and are then asserted to the application once successfully authenticated, never seeing the application's login screen. In SP-initiated integrations, end-users start the login process at the Service Provider (SP) / application, are redirected to SecureAuth IdP for authentication, and then are asserted back to the application once successfully authenticated.
This is a general SAML integration guide to assist in configuring actual application integrations. Refer to the specific application integration guide for applicable steps.
Note
For SAML integrations that require the use of AssertionConsumerServiceIndex instead of AssertionConsumerServiceURL, there is a hotfix that includes support for AssertionConsumerServiceIndex.
For more information, see SAML integrations using AssertionConsumerServiceIndex hotfix .
Prerequisites
Have a SAML application and access to administrative console
Create a New Realm in the SecureAuth IdP Web Admin for the SAML integration
Configure the following tabs in the Web Admin before configuring the Post Authentication tab:
Overview – the description of the realm and SMTP connections must be defined
Data – an enterprise directory must be integrated with SecureAuth IdP
Workflow – the way in which users will access this application must be defined
Multi-Factor Methods – the Multi-Factor Authentication methods that will be used to access this page (if any) must be defined
SecureAuth IdP configurations
Complete the steps on the Data tab only for LDAP directory integrations. The Data tab configuration is necessary have the user ID mapped to the SecureAuth IdP in order to assert the end user to the application.
Tip
If the application ID of the user is the same as the user ID provided to authenticate with SecureAuth IdP, then you do not need to complete the configurations on the Data tab.
In the Membership Connection Settings section, the user ID provided to SecureAuth IdP is the directory field that equals %v in the Search Filter field.
For example, (&(sAMAccountName=%v)(objectclass=*)) indicates the ID value stored in the sAMAccountName directory attribute is provided by the user to authenticate, and when this is the same user ID value required by the application, then no further mapping is required.
For LDAP directory integrations only, go to the Data tab.
To use a SQL-type data store, the mapping must be completed appropriately in the stored procedures.
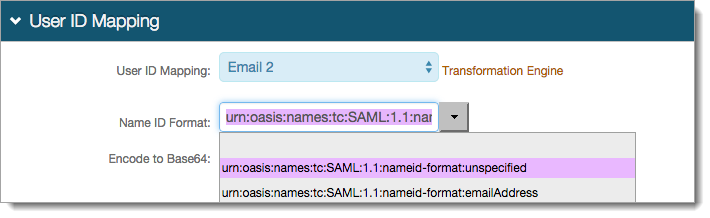
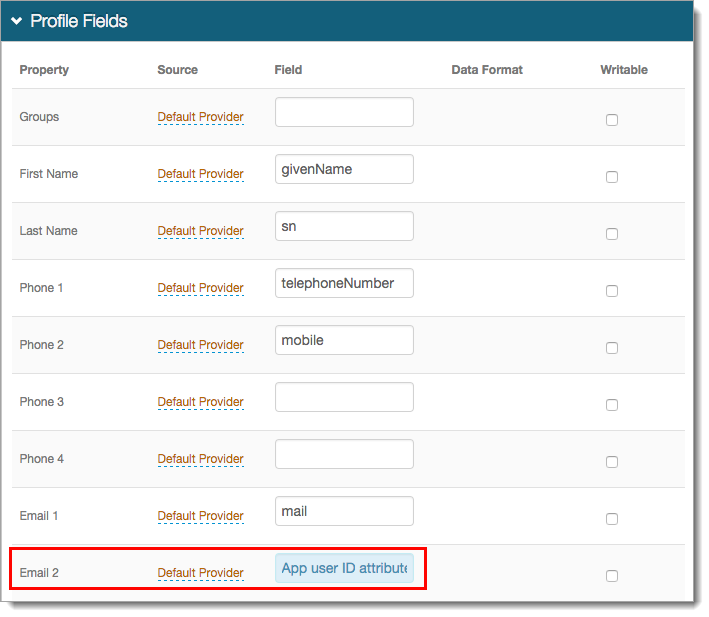
In the Profile Fields section, map the the directory Field containing the user's application ID to a SecureAuth IdP Property.
For example, add the application ID field to the Email 2 property.
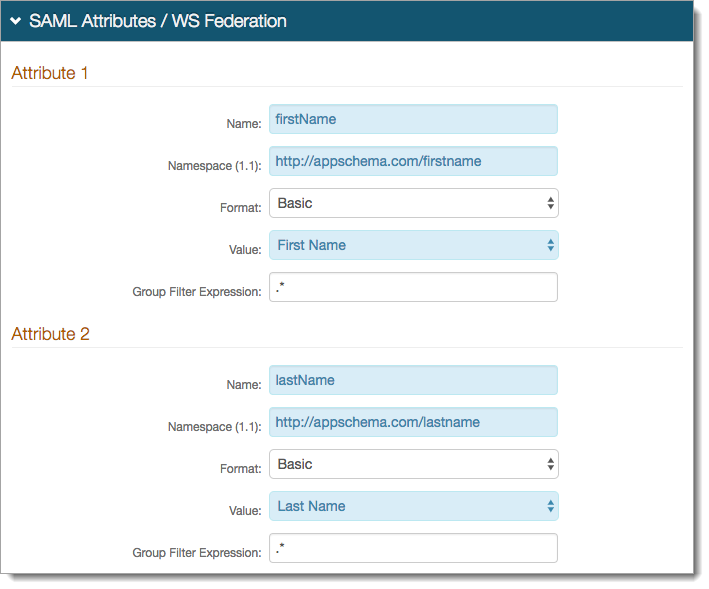
Save your configurations.
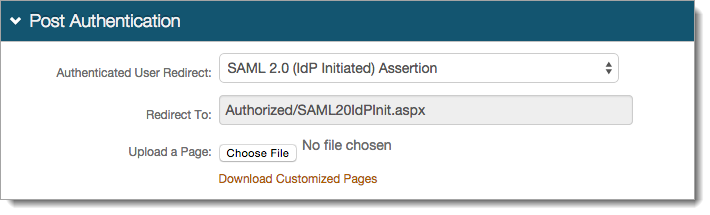
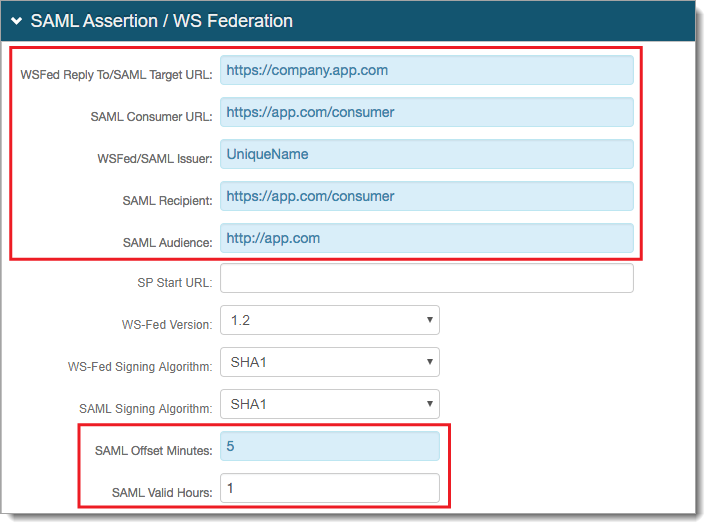
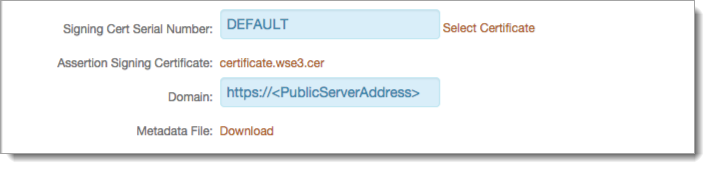
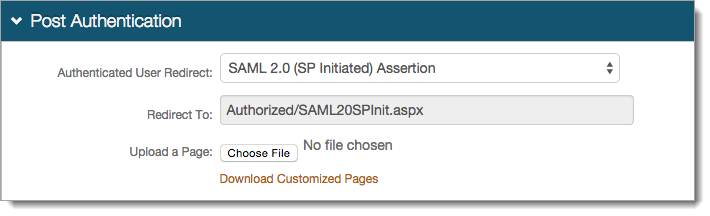
Go to the Post Authentication tab and make the following configurations for an IdP-initiated or SP-initiated integration.
To configure the token/cookie settings for this realm
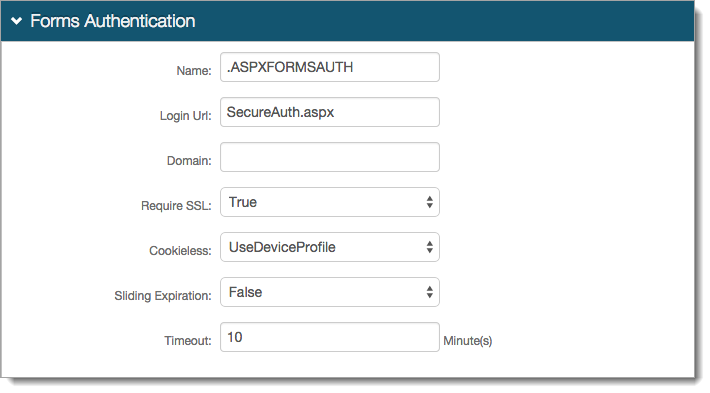
In the Forms Authentication section, set the following:
Require SSL
If SSL is required to view the token, set to True.
Cookieless
Select whether SecureAuth IdP is to deliver the token in a cookie to the user's browser or device:
UseCookies – Enables SecureAuth IdP to always deliver a cookie
UseUri – Disables the delivery of a cookie by SecureAuth IdP. Instead, deliver the token in a query string
AutoDetect – Enables SecureAuth IdP to deliver a cookie, if the user settings allow it
UseDeviceProfile – Enables SecureAuth IdP to deliver a cookie, if the browser settings allow it, regardless of the user settings.
Sliding Expiration
Set to True to have the cookie remain valid as long as the user is interacting with the page.
Timeout
Indicate in minutes how long a cookie is valid.
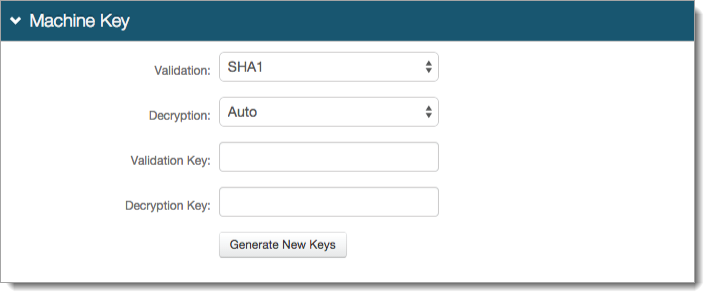
In the Machine Key section, set the following:
Validation
Verify whether the default value (SHA1) matches your configuration requirement. Otherwise, select another value.
Decryption
Verify whether the default value (Auto) matches your configuration requirement. Otherwise, select another value.
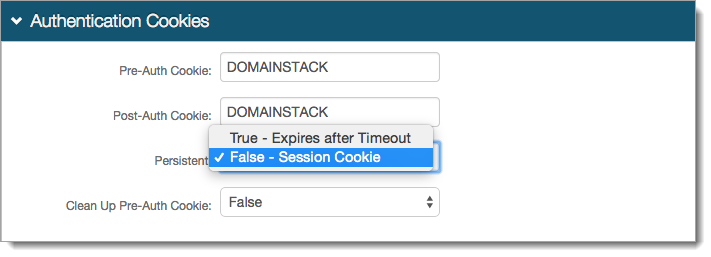
In the Authentication Cookies section, set the following:
Persistent
Set to one of the following:
True - Expires after Timeout – Cookie remains valid until the length of the Timeout is met.
False - Session Cookie – Cookie remains valid until the browser closes or the session expires.
Save your changes.
Other SSO configuration options
To configure this realm for SSO, see SecureAuth IdP Single Sign-on (SSO) Configuration Guide.
To configure this realm for Windows Desktop SSO, see the Windows desktop SSO configuration topic.