Outbound SCEP Configuration Guide
Introduction
Use this guide to configure Outbound Simple Certificate Enrollment Protocol (SCEP) settings in a SecureAuth IdP realm.
The Network Device Enrollment Service (NDES) allows software on network and other devices that run without domain credentials to obtain certificates based on SCEP.
SecureAuth IdP supports both Outbound and Inbound from MobileIron SCEP calls.
Outbound SCEP Calls are made when an on-premises Certificate Authority (CA) is being utilized to issue certificates rather than the SecureAuth IdP Cloud Services. A user requests a certificate from SecureAuth IdP to access an application or VPN, and SecureAuth IdP then calls to the on-premises CA via SCEP to receive the certificate to provide access.
For Inbound SCEP Calls from MobileIron configuration steps, refer to the Inbound SCEP from MobileIron VSP Configuration Guide.
Prerequisites
1. Have the Issuing CA running on Windows 2008 Enterprise edition
2. Have a pre-installed and functional SCEP / NDES service
3. The CA's root and intermediates certificate distribution point should be available to all clients (internal and / or external) to enable access to the AIA and CDP files (CRT and CRL files)
4. Have the SCEP / NDES Listener URL for SecureAuth IdP configuration
5. Access to the SecureAuth IdP Web Admin and all Realms requiring Outbound SCEP configuration
Issuing Certificate Authority Configuration Steps
Properties
1. Enable Auto Enrollment by opening the Certificate Authority from the Start menu
2. Right click the Issuing Certificate Name and click Properties
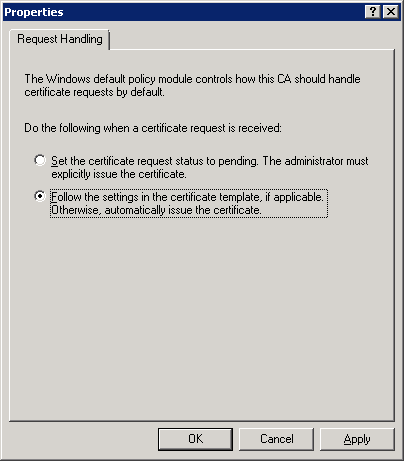
3. In the new window, click the Policy Module tab, and then click Properties
4. Select Follow the settings in the certificate template... and click OK
Registry Editor
Notice
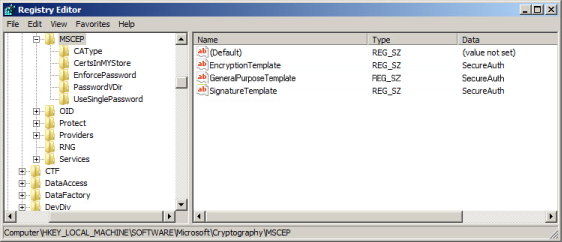
The SCEP / NDES server uses a single certificate template to issue all end-user certificates. To select which certificate template to use, complete the following the steps.
5. Open the Registry Editor on the CA and go to HKEY_LOCAL_MACHINE\Software\Microsoft\Cryptography\MSCEP
6. Change the values of the following registry keys to a common Template Name, e.g. SecureAuth
The Template Name will appear under the Data field, as shown in the image
The Template Name will be the name without spaces
There is a Template Display Name present, but it should not be used
7. Start a Command Prompt with Admin privileges on the SCEP server (Start, Cmd, Right Click, Run as Admin)
8. Type iisreset and press Enter to restart the IIS server
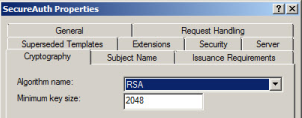
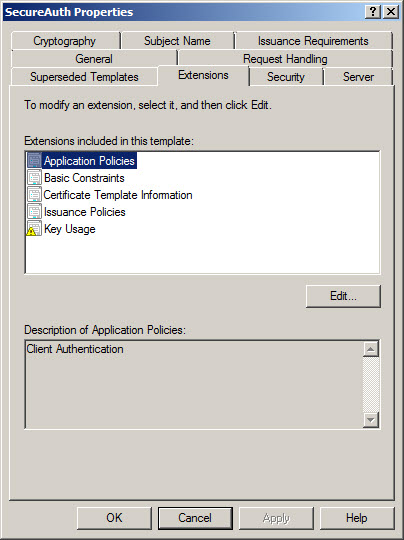
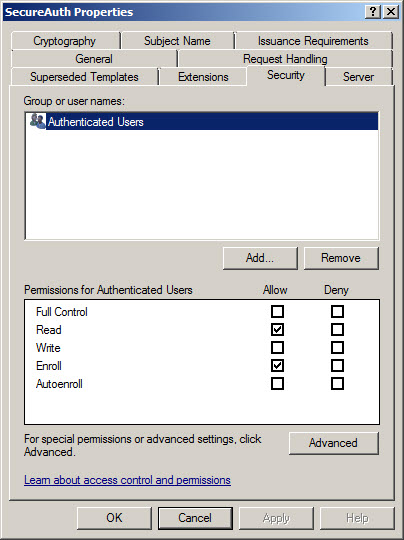
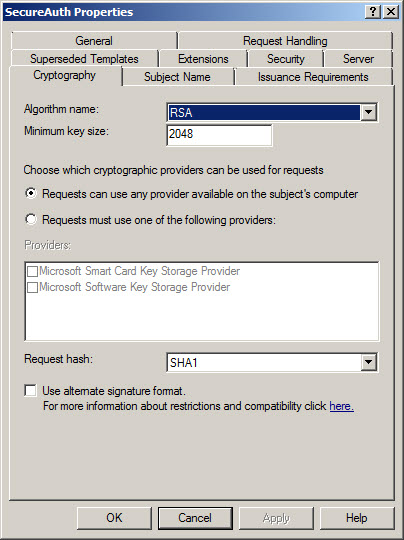
Certificate Template Configuration
Here is an example of the appropriate settings in a Windows 2008 Enterprise Certificate
Windows Server 2003 Enterprise and Windows 2008 Enterprise Certificate Templates can be used
Notice
The SCEP / NDES server can only use a single certificate template before the type of certificate delivered to the end-user is limited to the settings defined in the template
This includes key length and algorithm used, certificate validity period, Application Policy, etc.
Note
The certificate key length must be the same in both the SCEP and SecureAuth IdP server configurations (1024 or 2048). A mismatch on either side will cause issues in delivering the certificate properly.
SCEP / NDES Server Configuration Steps
Registry Editor
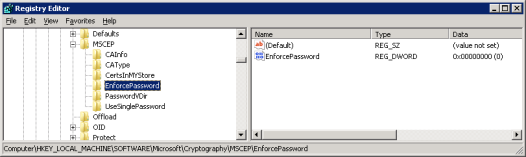
1. Disable SCEP Enforce Password by updating the following registry key / value pair in the SCEP / NDES server:
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\MSCEP\EnforcePassword]
Set to: "EnforcePassword"= dword: 00000000
SecureAuth IdP Configuration Steps
Note
These configurations are required for each SecureAuth IdP realm that utilizes Outbound SCEP calls
System Info
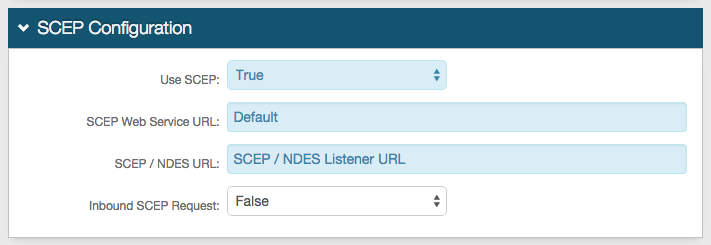
1. In the SCEP Configuration section, select True from the Use SCEP dropdown
2. Leave the SCEP Web Service URL as the default unless the web service is being hosted in a different location
3. Set the SCEP / NDES URL as the SCEP / NDES Listener URL
Warning
Click Save once the configurations have been completed and before leaving the System Info page to avoid losing changes
Sample Output
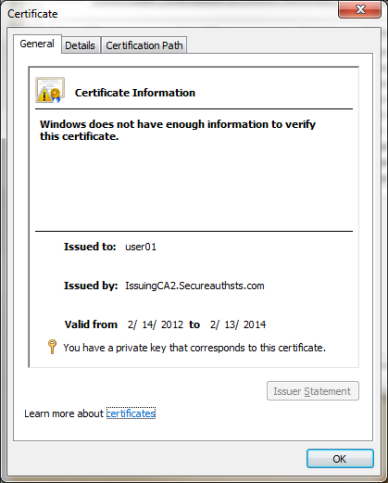
1. Go through the SecureAuth IdP workflow to obtain a certificate
2. Open the Certificate Store to inspect the certificate
3. The Issued By value should state the name of the on-premises CA