Cisco ISE (pxGrid) Begin Site Configuration Guide
Introduction
Use this guide to integrate Cisco Platform Exchange Grid (pxGrid) with SecureAuth IdP to create a begin site that leverages the user ID from the Cisco ISE authentication, eliminating the need to enter the user ID during the SecureAuth IdP workflow.
Cisco pxGrid allows multiple systems and all of their context to connect to a single interface. The pxGrid framework is comprised of the pxGrid controller and pxGrid connection agent. The pxGrid controller uses the Cisco Identity Services Engine (ISE) to enable connectivity between platforms and conduct contextual information sharing among them. The pxGrid connection agent – integrated in the partner platform – lets the partner platform communicate with the pxGrid controller to determine which information is shared with which partner platform.
The pxGrid integration with SecureAuth IdP requires a Java-based Windows service running in the Windows Server on the SecureAuth IdP appliance; a configured IdP realm; at least one configured pxGrid controller; and pertinent certificates that allow communications between SecureAuth IdP and Cisco ISE. The setup requires the pxGrid controller server(s) to be actively managing the organization's wireless access, as well as information about users on the wireless network, such as their user IDs and associated IP addresses.
In this setup, when an end-user is authenticated on a wireless network connected to an ISE server, the SecureAuth IdP pre-authentication page pulls the current IP address and sends it in a web service request to the Windows Service (pxGrid client). Then client then reaches out to the ISE server to retrieve the username that is mapped to that IP address, which is then sent to the pre-authentication page.
If the username is found, then the pre-authentication page generates a preauth cookie and sends the user to SecureAuth.aspx, at which SecureAuth.aspx extracts the username from the preauth cookie and continues with the configured workflow, skipping the initial username entry requirement. If the username is not found, then the pre-authentication page redirects users to the URL specified in the invalid persistent token redirect field (optional configuration step below).
Prerequisites
1. Have Cisco pxGrid installed in the wireless environment
2. Import one trusted Root Certificate for each pxGrid controller server used to the Trusted Root Certification Authorities store folder, which is used by SecureAuth IdP to trust the ISE controller server(s)
3. Have the pxGrid client private key certificate, which can either be the SecureAuth IdP appliance certificate (out-of-the-box) or a third-party certificate
If using a third-party certificate, then import this certificate to the client keystore folder on the SecureAuth IdP appliance
4. Import the matching public key certificate from SecureAuth IdP or the third-party to each ISE controller server to be used – this certificate is used by the ISE controller server to trust the SecureAuth IdP appliance
Tip
Cisco and SecureAuth each recommend using the default self-signed certificates that come with the product/appliance. SecureAuth IdP integrations with Cisco ISE only support certificates supplied by Cisco.
5. Contact SecureAuth Support to download the pxGridService-0.1.0.zip folder
6. Install the Java service in the Windows Services console on the SecureAuth IdP appliance to enable SecureAuth IdP to run as a Windows service on the Windows Server
Notice
The minimum supported version of Java Runtime Environment (JRE TM) is Java 8 (1.8.0_XX)
6. Create a New Realm in the SecureAuth IdP Web Admin for the Cisco pxGrid integration
7. Configure the following tabs in the Web Admin before configuring Cisco ISE:
Overview – the description of the realm and SMTP connections must be defined
Data – an enterprise directory must be integrated with SecureAuth IdP
Workflow – the way in which users access the target must be defined
Multi-Factor Methods – the 2-Factor Authentication methods that are used to access the target (if any) must be defined
Post Authentication – the target resource or post authentication action must be defined
Logs – the logs that are enabled or disabled for this realm must be defined
SecureAuth IdP Configuration Steps
Workflow
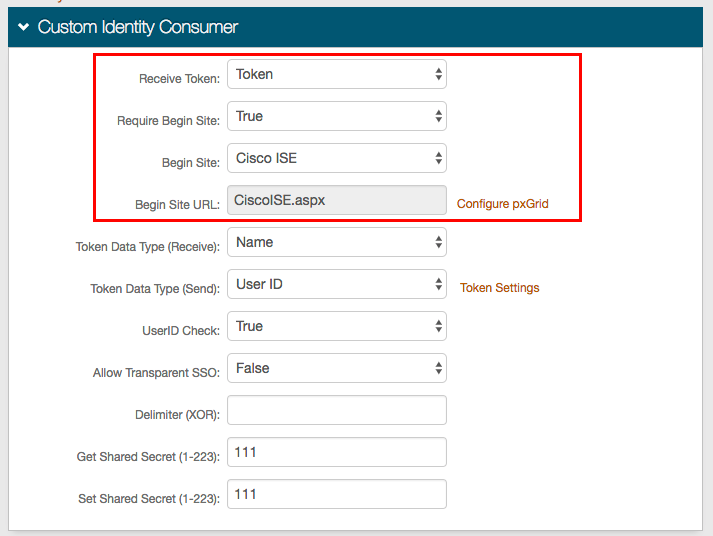 |
1. In the Custom Identity Consumer section, select Token from the Receive Token dropdown
2. Select True from the Require Begin Site dropdown
3. Select Cisco ISE from the Begin Site dropdown
4. The unalterable URL auto-populated in the Begin Site URL field (CiscoISE.aspx) appends to the domain name and realm number in the address bar
5. Click Configure pxGrid to configure criteria so each pxGrid controller server and the pxGrid client can communicate with SecureAuth IdP
Cisco pxGrid Integration
Notice
If using a load balancer or firewall (e.g. Edge Gateway device), then be sure to pass the client's IP address.
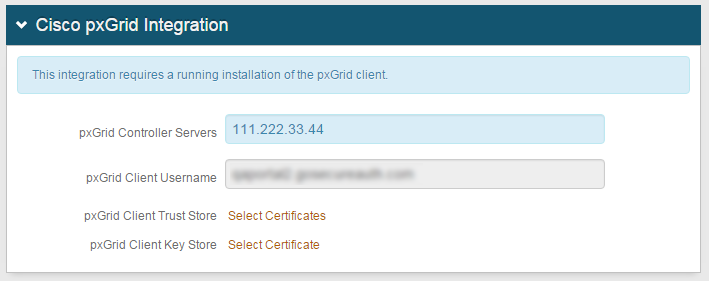 |
6. Enter the IP addresses of the pxGrid Controller Servers to communicate with the SecureAuth IdP appliance, separating each IP address with a comma
Notice
In an environment using server redundancy, the order in which IP addresses are entered in this field determines the sequence in which the corresponding server is used in a failover event
7. The unalterable URL auto-populated in the pxGrid Client Username field is unique and hardcoded to the appliance ID
8. Click Select Certificates to choose the certificate(s) from the pxGrid Client Trust Store
The selected certificate(s) is used to build the trust store between the ISE controller server(s) and SecureAuth IdP appliance
9. Click Select Certificate to choose the private certificate from the pxGrid Client Key Store
The selected certificate is used to build the Java key store that enable communications between the Java service and Windows service
Certificate Selection
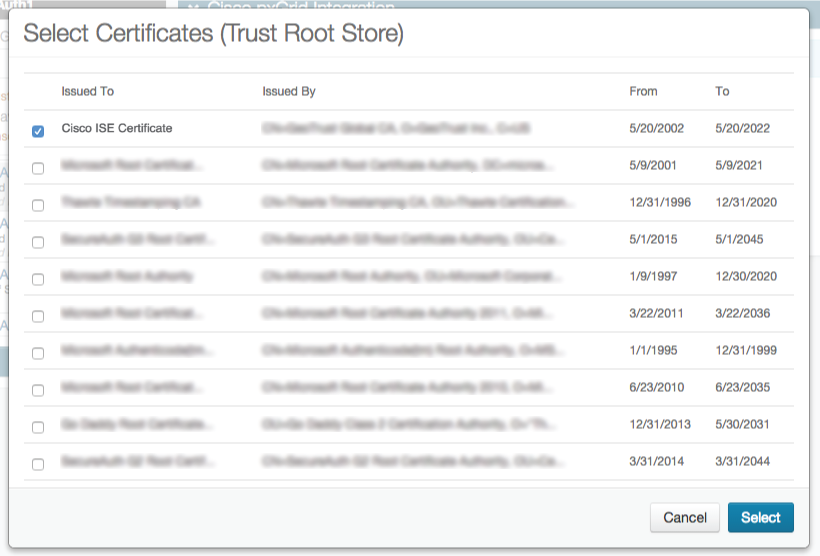 |
8a. Choose the certificate corresponding to each ISE controller server to be used with this SecureAuth IdP appliance
8b. Click Select to save the selection(s) and close the dialog
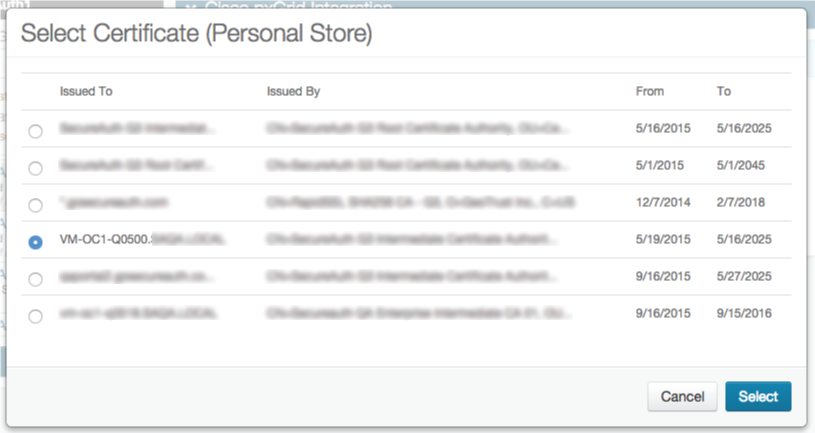 |
9a. Choose the private key certificate that is used to build the Java key store (e.g. appliance certificate)
9b. Click Select to save the selection and close the dialog
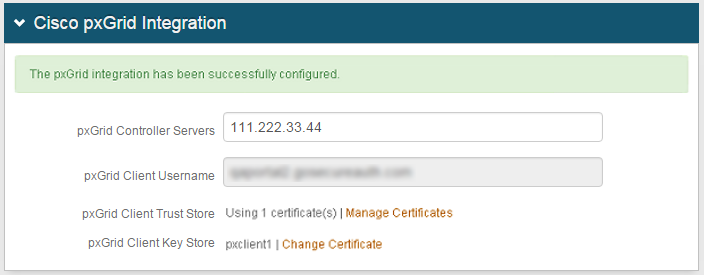 |
When the pxGrid client is successfully registered with the ISE controller server(s), a confirmation message appears: "The pxGrid integration has been successfully configured."
Notice
Certificate selections can be updated by clicking the appropriate Certificate/s link, choosing the replacement certificate(s), and then clicking Save before leaving the Workflow page
Warning
Click Save once the configurations have been completed and before leaving the Workflow page to avoid losing changes
Optional Configuration
Workflow
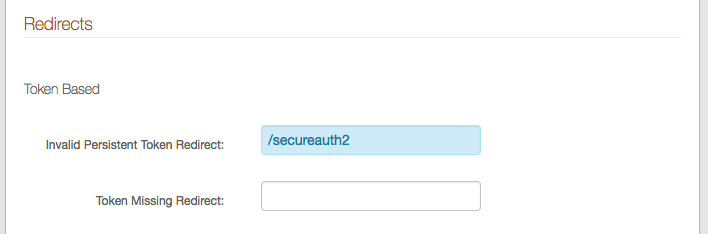 |
In the Workflow section under Redirects, provide an Invalid Persistent Token Redirect URL, which redirects end-users that have not been authenticated by Cisco ISE
SecureAuth recommends providing another SecureAuth IdP realm, which is configured for the same post-authentication action but does not require Cisco ISE authentication
The second realm can also be configured with more secure authentication to ensure that end-users' identities are being validated either by Cisco ISE or SecureAuth IdP