Certificate authentication via SSL configuration guide
Use this guide to enable certificate authentication via SSL in SecureAuth IdP realm(s).
This configuration initiates a begin site that forces the browser to request a certificate before the end user provides any information (client-side certificate) to enable access to the target resource (application, VPN, IdM tool, etc.)
Prerequisites
Have a valid certificate that is used to access the realm configured for certificate authentication via SSL. You can use any of the following certificates:
Certificates generated by SecureAuth IdP
Issued certificates – If your organization has their own issued certificates, make sure it meets the validation requirements in the next section, Certificate validation requirements and realm configuration options
Smart card certificates – If you have a smart card certificate, then the certificate chain must be imported from the card issuer to the SecureAuth IdP appliance
On SecureAuth IdP version 9.1 and later, create a new realm or edit an existing realm to which SSL certificate authentication is applied in the SecureAuth IdP Web Admin.
Before setting up a realm for certificate authentication via SSL, configure the following tabs in the Web Admin:
Overview – define the realm and SMTP connections
Data – integrate an enterprise directory with SecureAuth IdP
Workflow – define the user login process for accessing the target resource
Multi-Factor Methods – define the Multi-Factor Authentication methods used to access the target (if any)
Post Authentication – define the target resource or post authentication action
Logs – enable or disable the the logs for this realm
Certificate validation requirements and realm configuration options
This section is required only if your organization wants to use their own issued certificates instead of SecureAuth IdP-generated certificates. The SecureAuth IdP has a stock out-of-the-box (OOTB) validation scheme to validate security certificates.
To ensure that certificates can be validated by SecureAuth IdP, see the following requirements to tailor your issued certificates. You can use your issued certificates if there are no expectations to modify the cSSL.aspx.vb file, as long as the issued certificates meet the following requirements.
If your organization has issued certificates using a defined format for most of your end user base, then it requires a customization option. To accommodate defined certificates for validation by SecureAuth IdP, it requires code changes to .dll or .vb files. Contact SecureAuth Support to customize the issuing certificate realm.
To apply your defined certificates in the realm, make the following configurations.
Realm configuration for certificate authentication via SSL
These configuration steps are for the realm to which certificate authentication via SSL applies.
Go to the Workflow tab.
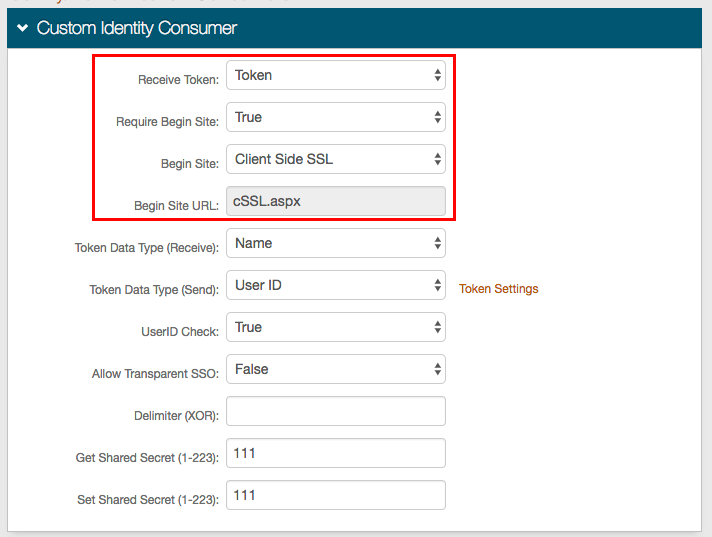
In the Custom Identity Consumer section, set the following:
Receive Token
Set to Token.
Require Begin Site
Set to True.
Begin Site
Set to Client Side SSL.
Begin Site URL
This field is autopopulated with cSSL.aspx.
Click Save.
Internet Information Services (IIS) Manager configuration
Go to the Internet Information Services (IIS) Manager.
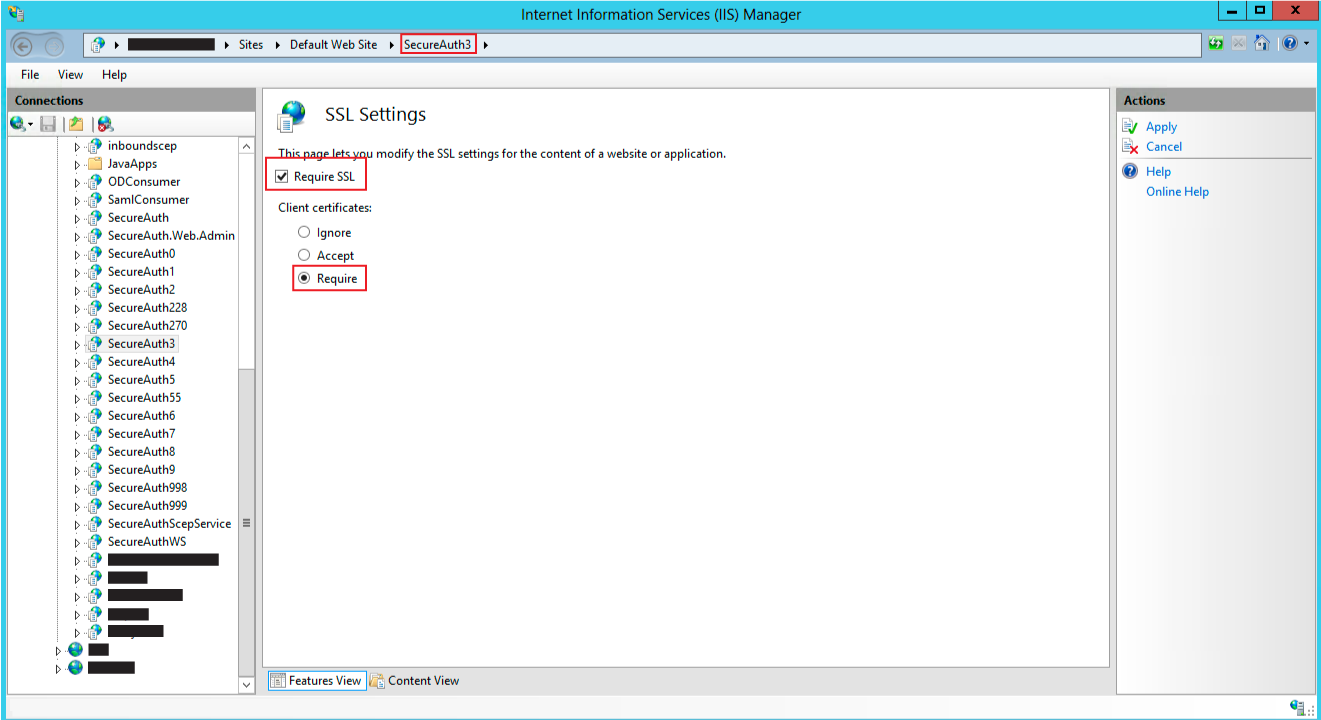
Under Sites > Default Web Site, select the realm to which the SSL certificate is applied (for example, SecureAuth3).
Click SSL Settings and set the following:
Require SSL
Select the check box.
Client certificates
Choose the Require option.
Sample end user workflow
When the end user attempts to access the certificate authentication via SSL realm, the SSL certificate Begin Site opens.
From the Begin Site, the end user is immediately prompted for a certificate.
A list of certificates are retrieved, from which the end user selects the appropriate certificate.
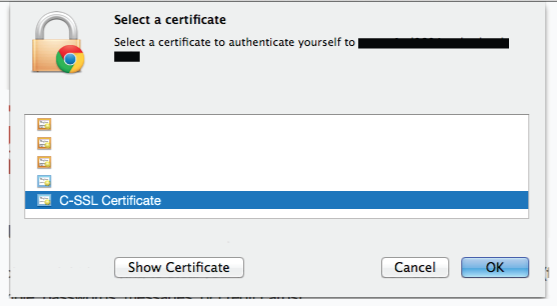
The end user is redirected to the SecureAuth IdP, and follows the workflow of the SSL certificate realm and then to the target resource.
Troubleshooting and common issues
Using Certificate Revocation List (CRL)
If using a separate Certificate Revocation List (CRL) rather than SecureAuth IdP, then make sure the SecureAuth IdP appliance can access the CRL to check the validity of certificates.
403 Errors
If you are getting 403 errors, then check the IIS logs to view the sub error code to further troubleshoot. For example:
403.7 – No certificate provided
407.17 – Certificate was revoked