Multi-Factor App Enrollment (URL) Realm Configuration Guide (version 9.1 and 9.2)
Note
Refer to Multi-Factor App Enrollment (QR Code) Realm Configuration Guide to enroll apps on devices via QR code
Introduction
The Multi-Factor App Enrollment (URL) realm is utilized by end-users to enroll the app on their desktop and mobile devices for OATH OTPs, and the app on mobile devices for Push Notifications and Push-to-Accept / Symbol-to-Accept requests for Multi-Factor Authentication. Multiple Multi-Factor App Enrollment (URL) realms can be created on a SecureAuth IdP appliance to make available the correct configuration for the application support requirements.
A realm configured for Multi-Factor App Enrollment via URL enables OATH Seed or OATH Token provisioning:
OATH Seed (Single) configurations generate a single OATH seed that is utilized by all devices for all realms.
OATH Token (Multi) configurations generate an OATH Token that contains the unique OATH seed and the device ID for each individual enrollment.
OATH Tokens are used by end-users to provision their devices against diverse SecureAuth IdP appliances and / or enterprise directories to create distinct tokens that ensure that the associated OATH seed can only work with the app / browser on that device.
End-users must be sure the correct URL is used in order to provision apps on supported devices / browsers to the appropriately configured Multi-Factor App Enrollment (URL) realm:
Feature | App on Supported Device / Browser Type | Supported Configuration for Device / Browser Type |
|---|---|---|
Time-based Passcodes (OATH OTPs) | SecureAuth Authenticate App for Android and iOS | supports both Single and OATH Token (Multi) configurations |
Credential Provider (Windows 2-Factor Authentication login) | only supports the OATH Seed (Single) configuration | |
Windows and Mac Desktop OTP Client Applications | support both Single and OATH Token (Multi) configurations | |
Push Notifications | SecureAuth Authenticate App for Android and iOS | supports both Single and OATH Token (Multi) configurations |
Push-to-Accept/Symbol-to-Accept | SecureAuth Authenticate App for Android and iOS | supports both Single and OATH Token (Multi) configurations |
Once an end-user has provisioned a mobile device against the Multi-Factor App Enrollment (URL) realm, Time-based Passcodes, Push Notifications, and Push-to-Accept requests are available for use.
Note
Refer to SecureAuth compatibility guide for supported versions of Mobile Apps, OTP Clients, Desktop Browsers, and Paired Smartwatches
Refer to SecureAuth Authenticate App for Android and iOS v5.x for information about enrollment instructions and Symbol-to-Accept
Prerequisites
1. Create a New Realm or access an existing realm (e.g. SecureAuth998) in the SecureAuth IdP Web Admin to configure for Multi-Factor App Enrollment (URL)
2. Configure the following tabs in the Web Admin before configuring the Post Authentication tab:
Overview – the description of the realm and SMTP connections must be defined
Data – an enterprise directory must be integrated with SecureAuth IdP
Workflow – the way in which users will access the target must be defined
Multi-Factor Methods – the Multi-Factor Authentication methods that will be used to access the target (if any) must be defined
SecureAuth IdP Configuration Steps
Data
Notice
The following Data tab steps are for LDAP directories only
If using a different directory (SQL, ASPNET, Oracle etc.), then the Properties need to be mapped to the data store via stored procedures (step 2)
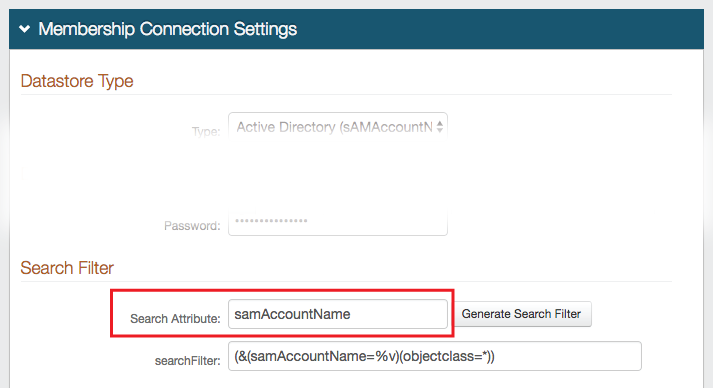 |
1. In the Membership Connection Settings section, note the Search Attribute directory field, e.g. sAMAccountName
Notice
The Search Attribute directory field must be the same in the Multi-Factor App Enrollment realm and all realms using Time-based Passcodes for Multi-Factor Authentication
Profile Fields
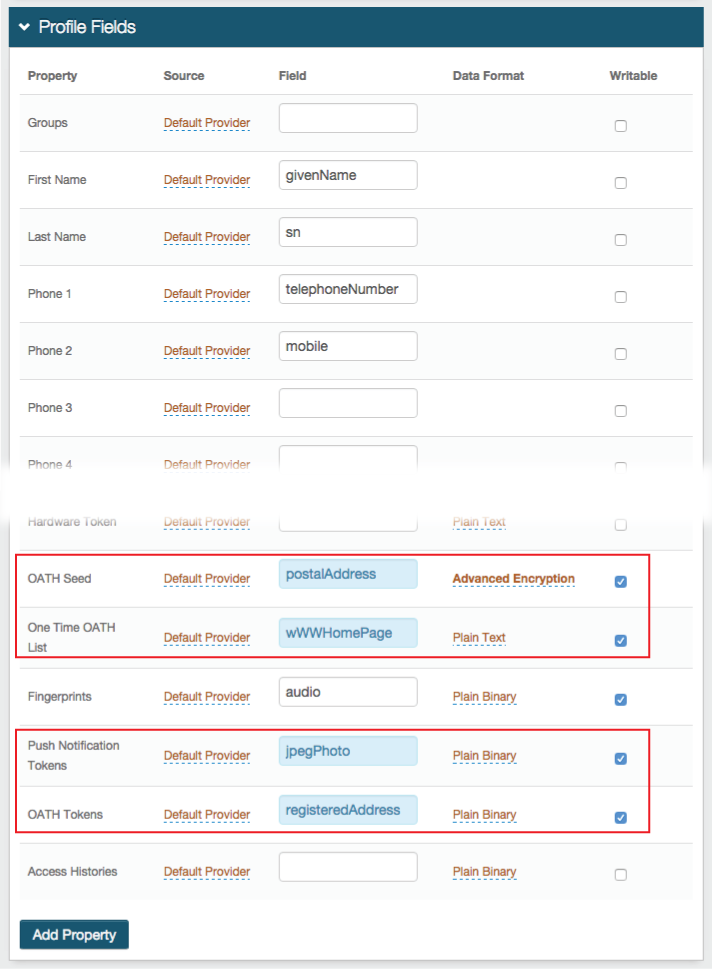 |
2. Map the necessary Properties to data store fields and check Writable:
The OATH Seed Property is required if OATH Seed (Single) is selected in the Multi-Factor App Enrollment section in the Post Authentication tab (step 6a below); otherwise, no mapping is necessary
Map the OATH Seed Property to a directory field that fulfills the following requirements:
DirectoryString (syntax: 2.5.5.12)
Upper Range of at least 4096
Supports Advanced Encryption, as selected from the Data Format options
For Active Directory data stores, the postalAddress field can be used
The One Time OATH List Property is required to enable the use of the feature; otherwise no mapping is necessary
The One Time OATH List feature temporarily stores a Time-based Passcode in the directory until the configured expiration to ensure that the OTP is used only once throughout its validity
Map the One Time OATH List Property to any directory field that is a DirectoryString
For Active Directory data stores, the wWWHomePage field (among many others) can be used
The OATH Tokens Property is required if OATH Token (Multi) is selected in the Multi-Factor App Enrollment section in the Post Authentication tab (step 6b below); otherwise, no mapping is necessary
The OATH Tokens Property can be stored as Plain Binary, JSON, or JSON Encrypted format, and has distinct requirements for the LDAP directory attribute mapped to the Property based on the Data Format selection
For Plain Binary, map the OATH Tokens Property to a directory field that fulfills the following requirements:
OctetString (syntax: 2.5.5.10)
Multi-valued
Upper Range of at least 4096
For JSON or JSON Encrypted, map the OATH Tokens Property to a directory field that fulfills the following requirements:
DirectoryString (syntax: 2.5.5.12)
Multi-valued
Upper Range of at least 4096
For typical Active Directory integrations, the Data Format is Plain Binary and the registeredAddress field is used
The Push Notification Tokens Property is required to enable the use of Push Notifications or Push-to-Accept / Symbol-to-Accept requests; otherwise, no mapping is necessary
The Push Notification Tokens Property can be stored as Plain Binary or in JSON format, and has distinct requirements for the LDAP directory attribute mapped to the Property based on the Data Format selection
For Plain Binary, these requirements must be met for the directory field that contains the Push Notification Token:
Length: 4096 minimum
Data Type: Octet string (bytes)
Multi-valued
For JSON, these requirements must be met for the directory field that contains the Push Notification Token:
Length: 4096 minimum
Data Type: DirectoryString
Multi-valued
For typical Active Directory integrations, the Data Format is Plain Binary and the jpegPhoto field is used
Note
NOTE: If the DirectoryString Data Type is not present, UnicodeString can be used instead, as long as other requirements for the attribute are met
Warning
NOTE: For SQL, ASP.net, and Oracle data stores, only the Plain Binary Data Format is supported for the OATH Tokens and Push Notification Tokens Properties (configured in the Data tab); and for ODBC data stores, the two Properties are not supported
Note
Refer to LDAP Attributes / SecureAuth IdP Profile Properties Data Mapping for the full list of requirements
Warning
Click Save once the configurations have been completed and before leaving the Data page to avoid losing changes
Post Authentication
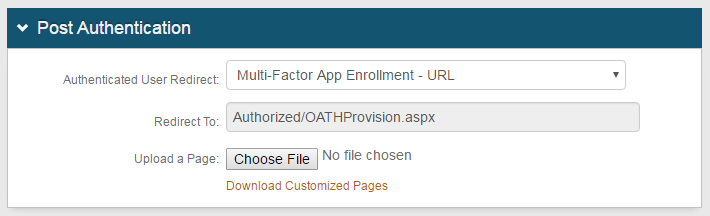 |
3. In the Post Authentication section, select Multi-Factor App Enrollment - URL from the Authenticated User Redirect dropdown
4. An unalterable URL will be auto-populated in the Redirect To field, which appends to the domain name and realm number in the address bar (Authorized/OATHProvision.aspx)
User ID Mapping
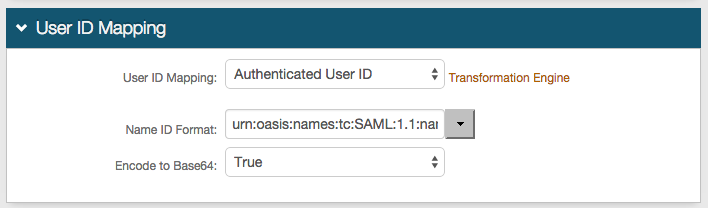 |
5. Select Authenticated User ID from the User ID Mapping dropdown (default)
Multi-Factor App Enrollment
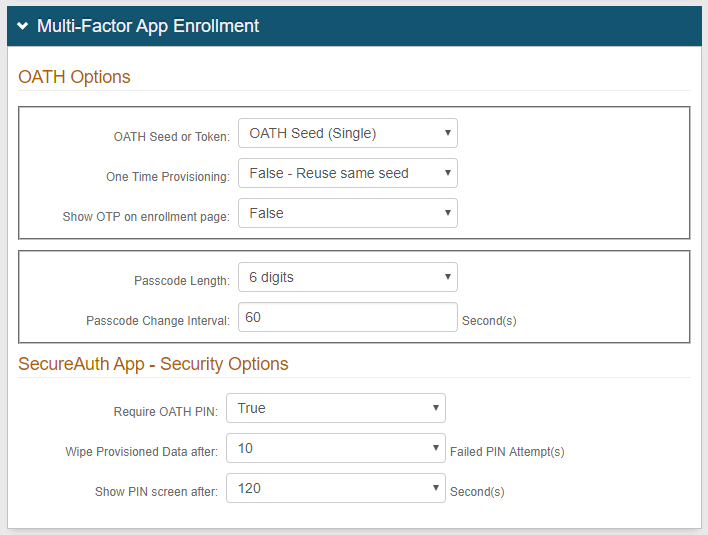 |
6a. In the OATH Options section, select OATH Seed (Single) from the OATH Seed or Token dropdown to provision user devices to utilize a single seed across multiple devices to generate the OATH OTPs
Notice
For the Credential Provider, this is the only provisioning option available
7a. Select False - Reuse same seed to enable the use of one seed with multiple devices (each newly provisioned device will reuse the same seed); or select True - Generate new seed from the One Time Provisioning dropdown to restrict the use of passcode OTPs on one device at a time (each newly provisioned device will have a new seed that will disable the use of the old seed)
8a. Select False from the Show OTP on enrollment page dropdown, unless the visibility of this information is required
9a. Select the number of digits comprising the passcode from the Passcode Length dropdown
10a. Set the Passcode Change Interval to the number of seconds during which an OATH OTP is valid
11a. In the SecureAuth App - Security Options section, select True from the Require OATH PIN dropdown if a PIN code is required to unlock the app; select False if it is not required
12a. Set the number of attempts allowed before the provisioned data is deleted from the application in the Wipe Provisioned Data after field
13a. Set the number of seconds allowed for the application to remain idle before requiring the PIN in the Show PIN screen after field
(no steps 14 - 16)
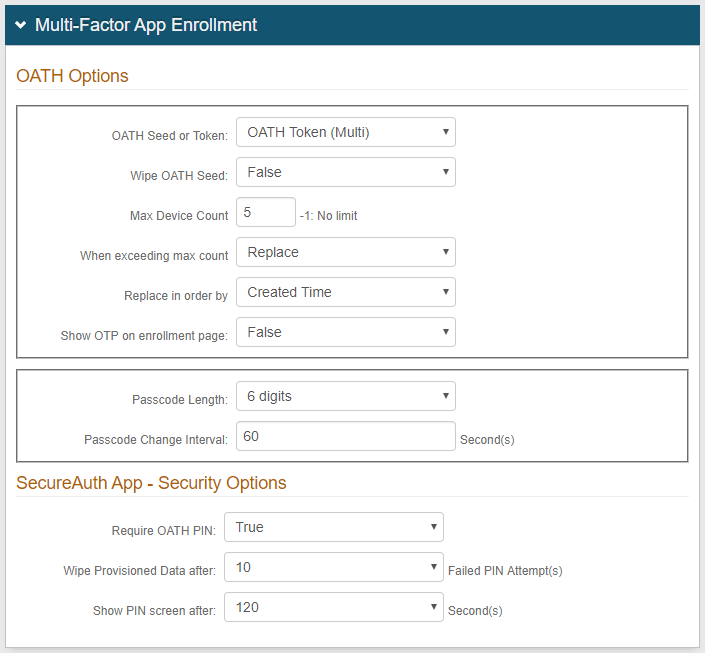 |
6b. In the OATH Options section, select OATH Token (Multi) from the OATH Seed or Token dropdown to provision user devices to utilize multiple tokens (that each contain a distinct OATH seed) on a single device
7b. Select False from the Wipe OATH Seed dropdown to enable the continued use of already-provisioned devices (pre-SecureAuth IdP v8.1); or select True to delete the existing the OATH seed and to enable only the use of an OATH Token
8b. Set the maximum amount of devices (tokens) allowed per user account in the Max Device Count field
Set to -1 if there is no limit to the number of devices allowed per user account
9b. Select Replace from the When exceeding max count dropdown to enable the replacement of existing provisioned devices with new ones after the maximum number of devices is met (if limit is set in step 8b)
10b. Select Created Time from the Replace in order by dropdown to replace the oldest OATH Token with the newest one; or select Last Access Time to replace the least frequently used OATH Token with the newest one (if Replace is selected in step 9b)
11b. Select False from the Show OTP on enrollment page dropdown, unless the visibility of this information is required
12b. Select the number of digits comprising the passcode from the Passcode Length dropdown
13b. Set the Passcode Change Interval to the number of seconds during which an OATH OTP is valid
14b. In the SecureAuth App - Security Options section, select True from the Require OATH PIN dropdown if a PIN code is required to unlock the app; select False if it is not required
15b. Set the number of attempts allowed before the provisioned data is deleted from the application in the Wipe Provisioned Data after field
16b. Set the number of seconds allowed for the application to remain idle before requiring the PIN in the Show PIN screen after field
Note
If using the Windows Desktop OTP Client Application, then there may be some provisioning issues
Refer to Trouble Provisioning Windows OTP Client v1.0 for more information
Warning
Click Save once the configurations have been completed and before leaving the Post Authentication page to avoid losing change
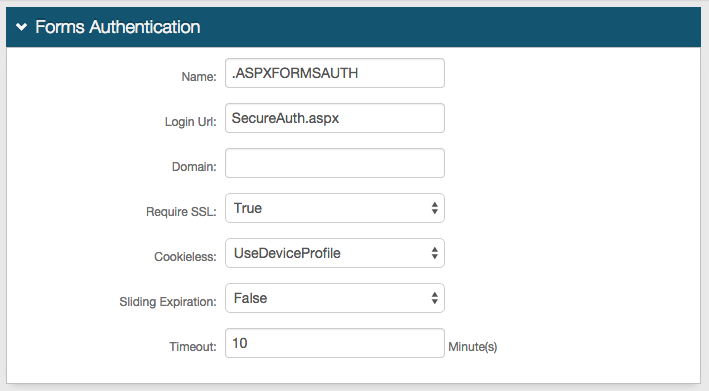
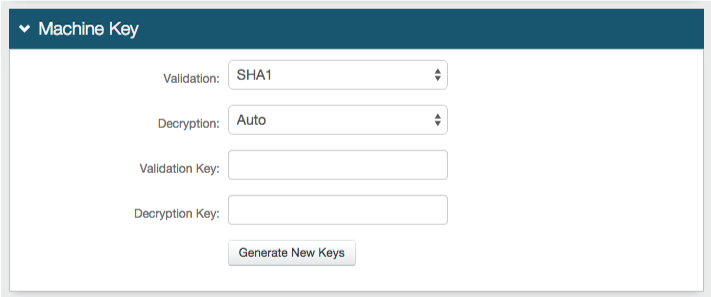
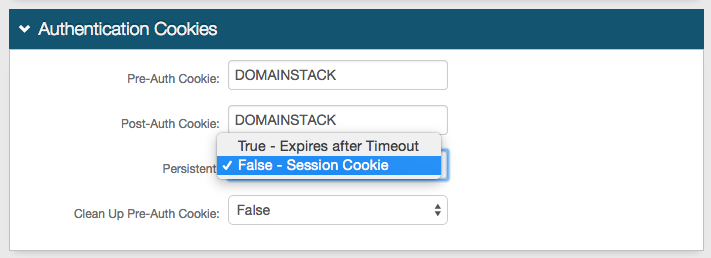
Forms Auth / SSO Token
Optionally, in the Forms Auth / SSO Token section, click the View and Configure FormsAuth keys/SSO token link to configure the token/cookie settings and configure this realm for SSO.
 |