SecureAuth IdP Digital Certificate Overview
Introduction
This article discusses digital certificates and how they are used with SecureAuth IdP.
Note
Disclaimer
Information about products not made by SecureAuth Corporation is provided for informational purposes only and does not constitute SecureAuth Corporation's recommendation or endorsement.
Applies to
SecureAuth IdP Version | OS Version |
|---|---|
7.x+ |
|
Discussion
What is a Digital Certificate and How is it Used by SecureAuth IdP?
A digital certificate (also known as an identity certificate) is an electronic credential that binds the identity of the certificate owner to a pair of electronic keys (public and private) that can be used to encrypt and sign information digitally.
SecureAuth IdP uses industry-standard X.509 v3 digital certificates to verify the identity of end-users and organizations on the Internet. These electronic credentials ensure that the keys actually belong to the individual or organization detected online. Messages can be encrypted with either the public or the private key, and then decrypted with the other key. This is the same technology used by SSL/TLS to help ensure secure communications between web servers and clients for sensitive communications (e.g. Banking and eCommerce).
Notice
See Windows Digital Certificate Management for information about how to access and manage digital certificates used with SecureAuth IdP
What is a Binding Certificate and How is it Used by SecureAuth IdP and IIS?
A binding certificate is a digital certificate that is bound from a web server to a specific client IP and port.
SecureAuth IdP runs atop Microsoft IIS which uses a binding certificate to facilitate SSL/TLS communications with a web client.
Due to the sensitive communications SecureAuth IdP appliances handle from the moment an end-user credential leaves the web browser to the time it enters the appliance, all sessions are encrypted with SSL/TLS. This is the industry standard for encryption in web transactions and SecureAuth IdP employs some of the strongest forms commercially available. In fact, SecureAuth IdP servers are configured to only allow encrypted communications from web clients to help ensure maximum security.
The video tutorials below from prominent commercial Certificate Authorities demonstrate how to install a binding certificate on the Windows Server family which underlies SecureAuth IdP.
Certificate Authority | Video |
|---|---|
Symantec | How to Install an SSL Certificate on Microsoft Server 2008 & 2012 IIS 7 & 7.5 |
DigiCert | |
Thawte |
Notice
For information on installing a binding certificate see the support document SSL Certificate Replacement Guide - IIS X
What is an Identity Certificate and How is it Used by SecureAuth IdP?
An identity certificate is a certificate signed by the same entity it certifies.
SecureAuth IdP issues identity certificates to end-users configured to use Java in their authentication workflow, and to the end-user native browser configured for a certificate enrollment workflow.
Java Identity Certificate
In a SecureAuth IdP workflow configured to use Java, SecureAuth IdP issues x.509v3 identity certificates to end-users who have successfully passed Multi-Factor Authentication so they do not have to go through this process again until the administratively set time period expires.
The identity certificate is stored by Java in the Java Keystore (JKS), a repository of security certificates that can't be copied or moved from the workstation. This feature helps customers strike a balance between an organization's IT security policies and the convenience of its end-users.
Native Browser Identity Certificate
In a SecureAuth IdP workflow configured for certificate enrollment, SecureAuth IdP issues an x.509v3 identity certificate that is stored by the native browser.
For Microsoft Internet Explorer, Google Chrome and Apple Safari, the certificate is stored in the underlying operating systems certificate store. Firefox, on the other hand, stores the identity certificate in a private repository which only it can access. This mode of operation is commonly used by Cisco and Juniper VPNs which require an x.509 v3 certificate to establish a VPN connection. By having certificates issued through SecureAuth IdP, the organization adding Multi-Factor Authentication to their VPN helps ensure only authorized end-users are allowed to establish a connection.
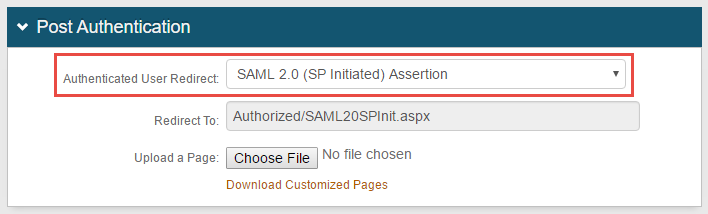
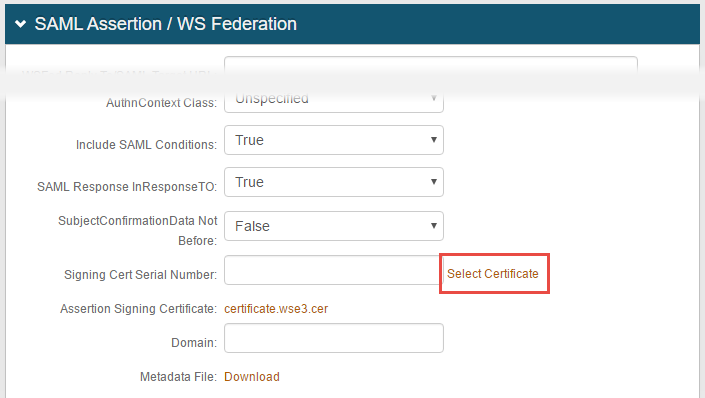
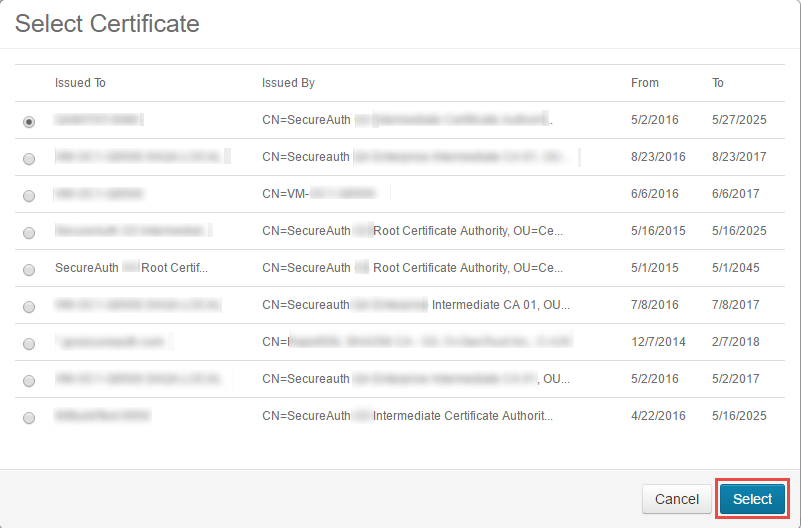
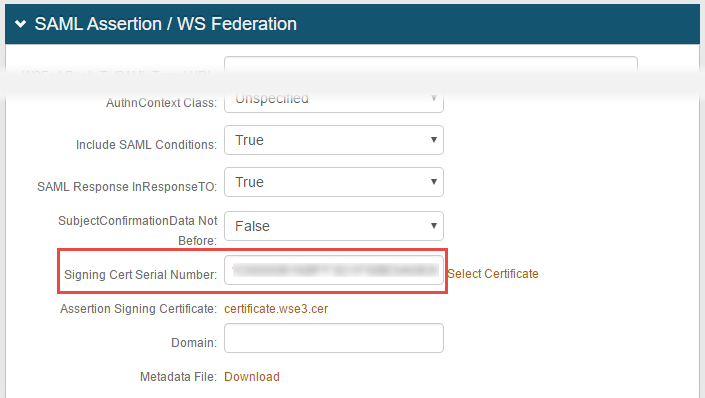
What is a Signing Certificate and How is it Used by SecureAuth IdP?
A signing certificate is used to identify the signing entity in the electronic world. Signing certificates can be either self-signed or purchased from a public CA (e.g. Symantec VeriSign, GoDaddy).
In SecureAuth IdP workflows configured for SAML or WS-Federation integrations, a signing certificate is used to cryptographically sign the assertion.
This certificate is stored in the Windows Certificate Store on the SecureAuth IdP server.
How are Digital Certificates Used with Encryption of Data Store Attributes in SecureAuth IdP?
In the SecureAuth IdP Web Admin, a digital certificate facilitates encryption of applicable attributes in the Data Store for enhanced security.
This setting can either be compulsory or enabled by the administrator when additional security guarantees are desired by the organization.
The digital certificate is stored in the Windows Certificate Store on the SecureAuth IdP server.
What is WSE / WCF Encryption and How is it Used with SecureAuth IdP?
SecureAuth IdP Appliances use Microsoft Windows Communication Foundation (WCF) and Web Services Enhancements (WSE3) message-level security to communicate with the SecureAuth IdP cloud environment.
A digital certificate is used to encrypt the message, and by default the appliance uses the certificate issued by SecureAuth Corporation.
This certificate is stored in the Windows Certificate Store on the SecureAuth IdP server.
Digital Certificates in an Environment with Multiple SecureAuth IdP Appliances Using the SecureAuth FileSync Service
When multiple SecureAuth IdP Appliances use the SecureAuth FileSync Service, a single web.config file is shared between all nodes within the cluster. Therefore all nodes must be uniformly configured and have the same assets to ensure proper operation. From a digital certificate perspective, this means all nodes in the cluster must have the following certificates in their Windows Certificate Store.
SAML / WS Federation Signing Certificate
License Info Certificate
WSE 3.0 / WCF Client Certificate
If any node lacks one or more of the listed certificates, functionality will break on that specific node. For information on the import and export of certificates, see the document Windows Digital Certificate Management.