Step B: IdP Realms configuration, v20.06
Administrators with teams using SecureAuth Identity Platform will continue to set up SecureAuth RADIUS on SecureAuth IdP realms until feature parity is achieved.
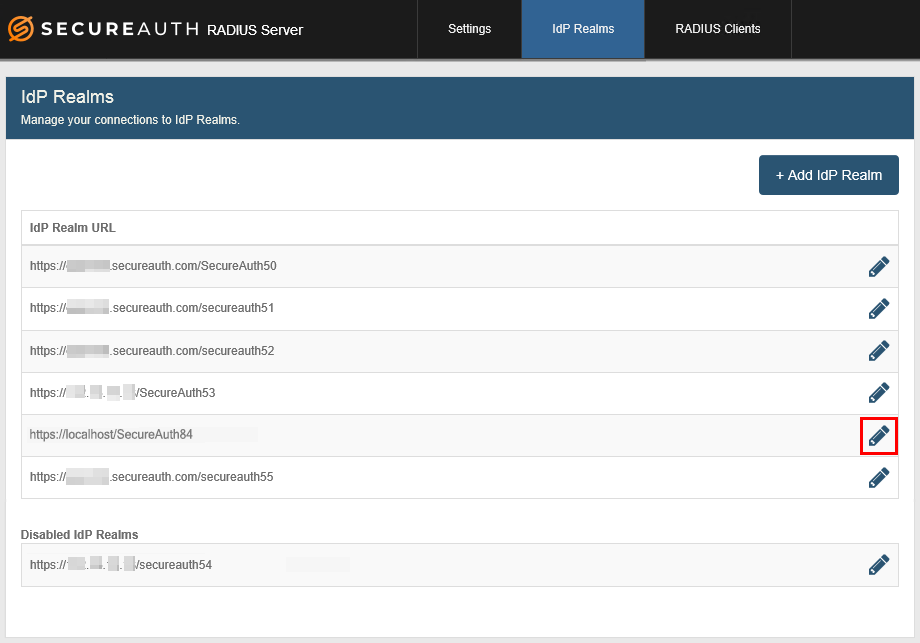
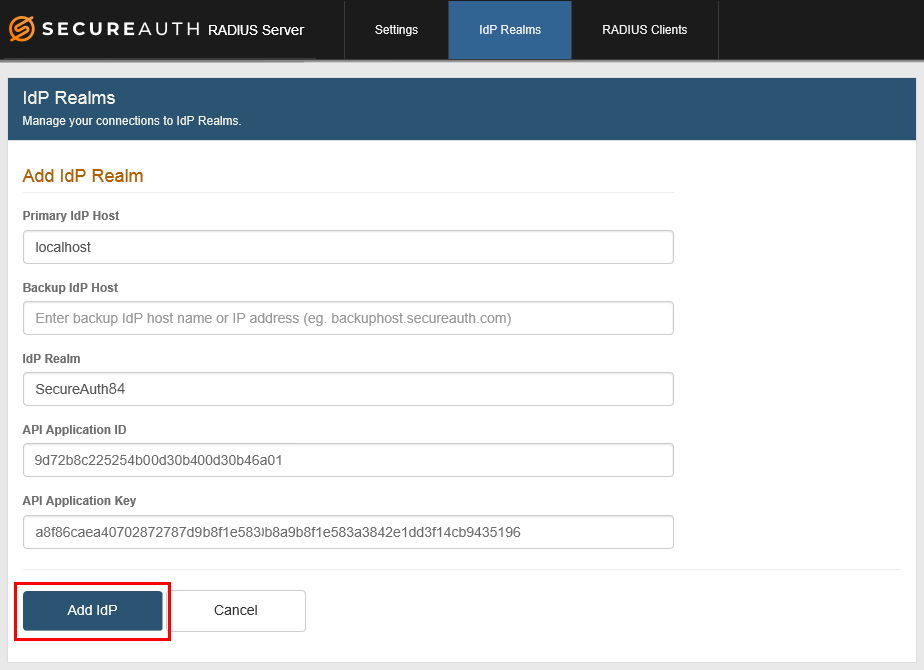
1. On the IdP Realms page, click Add IdP Realm.
 |
Add IdP realm
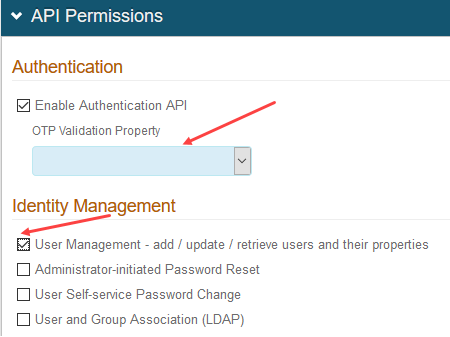
Ensure that the SecureAuth IdP API can connect to User properties. In the API realm in "API Permissions," ensure the following:
If using Identity Platform v19.07 or later, check that the "OTP Validation Property" field is empty. If populated, use the dropdown to reset it to empty.
Check that "User Management" is enabled. If disabled, check the box. Enable the option if using SecureAuth IdP or Identity Platform.
 |
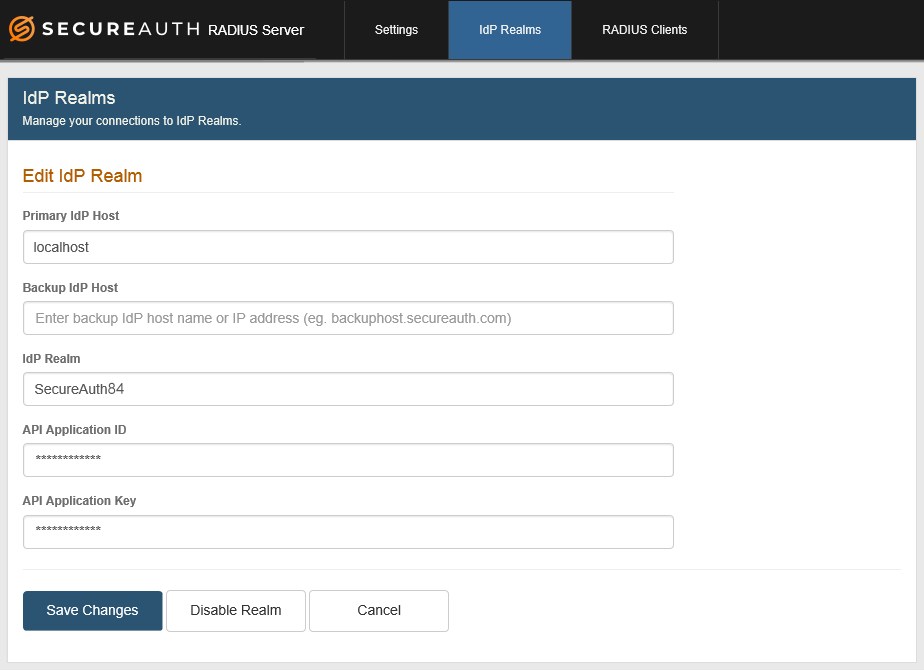
2. In the Primary IdP Host field, localhost appears by default.
If the realm is hosted on a different SecureAuth IdP than the one hosting this RADIUS server, enter the IdP host name or the IP address of the SecureAuth IdP realm to be used with this RADIUS server.
Examples: hostname.secureauth.com or XXX.XXX.XXX.XXX (where "X" represents a number in the IP address).
3. OPTIONAL: In the Backup IdP Host field, enter the host name or IP address of each SecureAuth IdP appliance to use for failover functionality, with each entry separated by a comma ( , ).
Failover to a backup server can occur in these scenarios:
Communications are faulty with the target SecureAuth IdP.
RADIUS server receives no response.
RADIUS server receives errors from SecureAuth IdP.
During failover, end-users can log on the VPN without disruption.
NOTE: For more information see View sample logs for RADIUS failover scenarios, v20.06.
4. Enter the IdP Realm name and number. Examples: secureauth53 or SecureAuth84
5. From the SecureAuth IdP server, copy the Application ID generated for the realm and paste that content in the API Application ID field.
NOTE: See the Authentication API guide for steps on generating the Application ID in the API Key section of the API tab.
6. From the SecureAuth IdP server, copy the Application Key generated for the realm and paste that content in the API Application Key field.
NOTE: See the Authentication API guide for steps on generating the Application Key in the API Key section of the API tab.
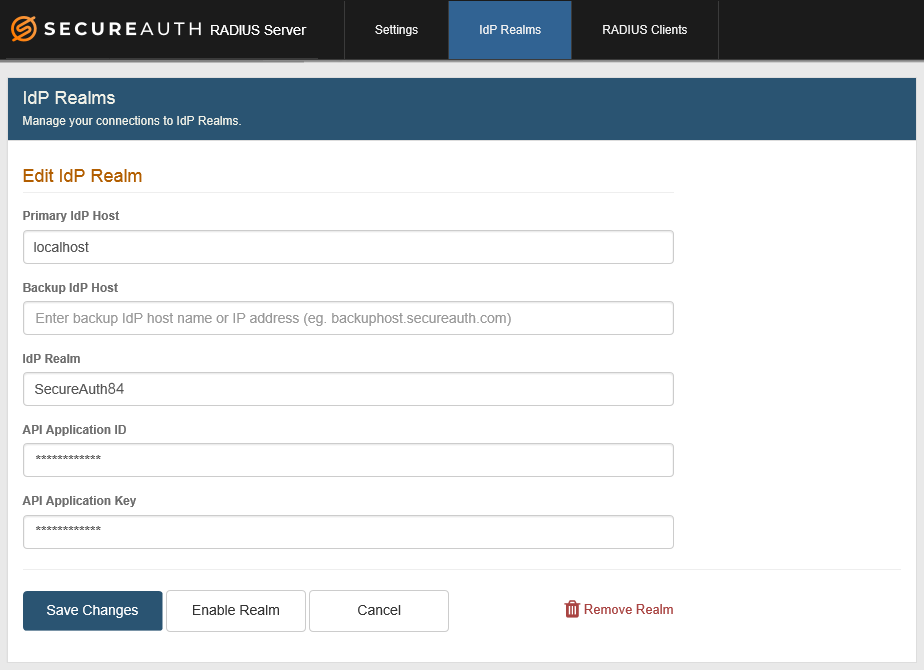
7. Click Add IdP to enable the realm for use with the RADIUS server, or click Cancel to return to the IdP Realms page without adding the realm.
 |
Edit the IdP Web Config file
A default setting in the SecureAuth IdP v9.3 or earlier Web Config file causes RADIUS client end-user logins to fail for certain 2FA methods. To ensure end-users can log in using any 2FA method, remove the Property in the SecureAuth IdP Web Admin configuration by completing the following steps.
1. In the SecureAuth IdP realm you added in Step B, step 1 above, click the System Info tab.
2. On the System Info tab, in the Links section, select Click to edit Web Config file.
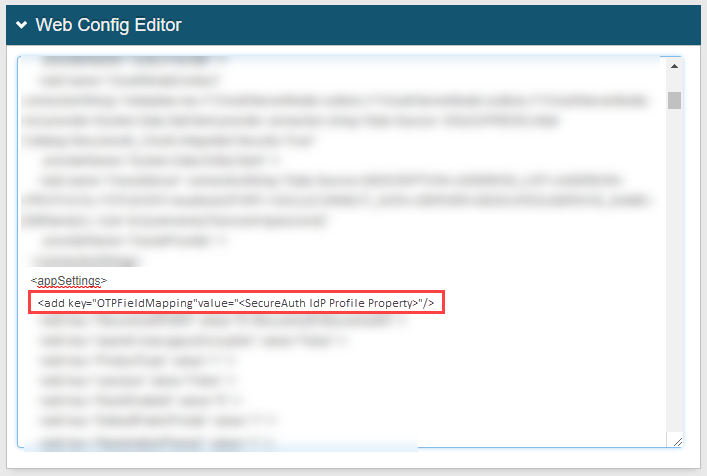
3. In the Web Config Editor section, under <appSettings>, remove the following line because SA RADIUS does not use /api/v1/otp/validate to validate OTP codes:
<add key="OTPFieldMapping"value="<SecureAuth IdP Profile Property>"/>
4. Click Save.
 |