YubiKey OATH-TOTP device provisioning and Multi-Factor Authentication guide
SecureAuth's Multi-Factor Authentication (MFA) method uses a YubiKey Time-based One-time Passcode (TOTP) device on a Windows or Mac machine for secure and hassle-free login access to a SecureAuth IdP realm. After you set up and enable a YubiKey device as a MFA method (OATH-TOTP), end-users can use their YubiKey device to log on the VPN through the SecureAuth IdP RADIUS server.
TOTP Multi-Factor Authentication requires the YubiKey device to be configured to provide OATH-TOTP authentication to access the realm. (Note that OATH-TOTP authentication is different from HOTP Multi-Factor Authentication, and each are set up in their own IdP realms.)
One of the common uses for this type of Multi-Factor Authentication method is in an environment that uses Login for Windows or Mac.
This guide provides instructions for:
Administrators to configure SecureAuth IdP to enable YubiKey TOTP device provisioning, with QR Code app enrollment.
Administrators to provision end-user YubiKey TOTP devices to use timed passcodes as a Multi-Factor Authentication method.
End-users to use their YubiKeys to log on the VPN through the SecureAuth IdP RADIUS server.
Prerequisites
1. Ensure the correct SecureAuth IdP and required components are installed and running.
SecureAuth IdP version 9.2 or later
SecureAuth IdP RADIUS server version 2.5 or later
Compatible RADIUS client
2. Create a realm or access an existing realm on which more than one Multi-Factor Authentication is required.
3. Configure the following tabs on the IdP Web Admin for QR Code app enrollment:
Overview: Define the description of the realm and SMTP connections.
Data: Integrate an enterprise directory with SecureAuth IdP.
Workflow: Define the way in which users will access the target.
Multi-Factor Methods: Define the Multi-Factor Authentication methods that will be used to access the target.
Post Authentication: Define the target resource or post-authentication action.
4. Ensure target end-user machines are running the appropriate supported OS versions. For more information, see Compatibility guide.
5. Ensure supported YubiKey devices are used. For more information, see Compatibility guide.
6. Download and install the YubiKey Personalization Tool from the Yubico website.
7. Ensure your phone camera works.
Note
IMPORTANT: If an end-user is already using a YubiKey device for YubiKey Multi-Factor Authentication on a SecureAuth IdP realm, the OATH seed and associated YubiKey device must be removed from the end-user's account to prevent a conflict when the end-user attempts to authenticate with a YubiKey TOTP device. (See the steps under End-user Multi-Factor Authentication in the YubiKey Multi-Factor Authentication Configuration Guide to remove the YubiKey device from the user account profile.)
NOTE: When using a YubiKey on a Mac, the device's Keyboard Setup Assistant wizard and the message "Your keyboard cannot be identified" might appear, but you can disregard it. Refer to Yubico's How to get started with YubiKey on macOS for steps to have the Mac recognize the YubiKey device.
SecureAuth IdP RADIUS server components and configuration
Administrator configuration steps
Configure the SecureAuth IdP RADIUS client to use one of the TOTP passcode workflows:
Password | One-Time Passcode (TOTP/HOTP) or Second Factor
One-Time Passcode (TOTP/HOTP) Only
Password | One-Time Passcode (TOTP/HOTP)
One-Time Passcode (TOTP/HOTP) | Password
One-Time Passcode | Passcode
Password & One-Time Passcode (TOTP/HOTP)
NOTE: These workflows currently appear in SecureAuth IdP RADIUS server product version 2.4 or later, but have been re-labeled to accommodate the following device and apps:
SecureAuth Authenticate (mobile app), SecureAuth Passcode (desktop app), YubiKey (Yubico Authenticator) that generates HOTP timed passcodes, or YubiKey (Yubico Authenticator) that generates TOTP timed passcodes
SecureAuth IdP configuration steps
Configure a SecureAuth IdP Multi-Factor Authentication realm to generate QR codes.
YubiKey OATH-TOTP configuration and usage steps
Required components
Yubico Authenticator for Windows or Mac. TOTP requires the Yubico Authenticator app because it reads OATH codes from YubiKeys, which do not have an internal clock, but need to know the time to create one-time passcodes.
Note: If you are provisioning a YubiKey using Yubico OTP protocol, the Yubico Authenticator app and provisioning steps are not required. The Yubico OTP protocol is provisioned and ready for use immediately, without any set up.
YubiKey device
QR code decoder, such as ZXing Decoder Online
Phone camera that works
Administrator configuration and device provisioning steps
1. If not already completed, configure a SecureAuth IdP Multi-Factor Authentication realm to generate QR codes.
2. Log on the QR code realm to register the YubiKey device in the end-user's account.
a. When the QR code appears on the page, right-click the code and download it.
b. Leave the QR code page open.
3. Access the online QR code decoder page.
a. Upload the QR code to the decoder page.
b. Decode the QR code and capture content from the raw file, as shown in the following example:
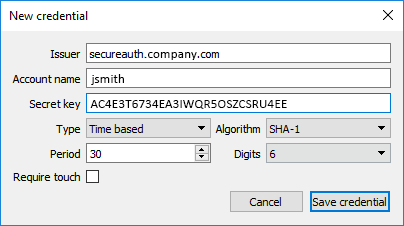
Issuer URL following "otpauth://totp/": secureauth.company.com
Account name: jsmith
Secret key: AC4E3T6734EA3IWQR5OSZCSRU4EE
Period (interval in seconds): 60
IMPORTANT: Yubico Authenticator does not support a
periodvalue greater than 99; you must configure the realm to use aperiodvalue less than 100.Digits in OTP: 6
4. Insert the YubiKey in the Windows or Mac machine.
5. Start the Yubico Authenticator, click File and select New credential.
 |
6. Make entries specified in step 3b.
Set Algorithm to SHA-1.
Ensure that Require touch is cleared.
7. Click Save credential.
 |
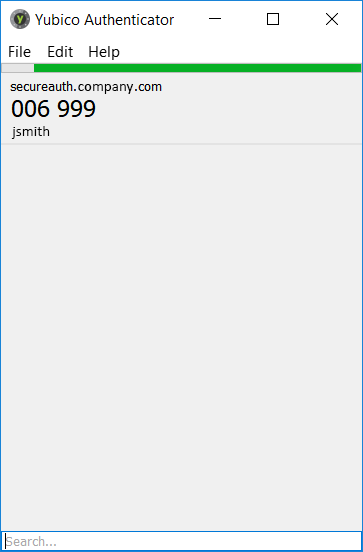
8. The Yubico Authenticator generates time-based passcodes.
 |
9. Return to the QR code page and complete the workflow by entering the QR code from the Yubico Authenticator.
This step adds the Yubico Authenticator in the end-user account.
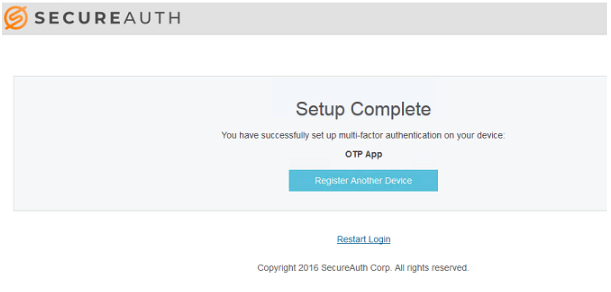
10. When Two-factor Authentication is set up, the following message is displayed.
 |
End-user usage steps
Use the provisioned YubiKey TOTP device as a Multi-Factor Authentication method and use it to log in to your company's protected area, typically a VPN.
1. Insert the YubiKey in the USB connector on your machine and start the Yubico Authenticator app.
2. After you start the Yubico Authenticator app, it generates the TOTP passcode.
 |
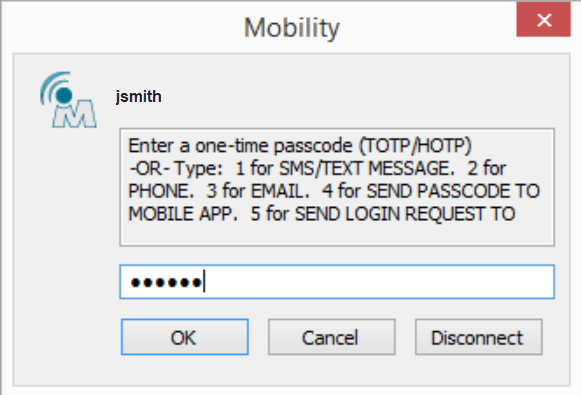
3. Enter the passcode from the Yubico Authenticator app on the VPN login page.
 |