F5 Big-IP VPN Integration Guide (RADIUS)
Introduction
Use this guide to enable Multi-Factor access via RADIUS to F5 Big-IP VPN using SecureAuth's OATH OTP token.
Prerequisites
1. Have F5 Big IP VPN
2. Configure the App Enrollment Realm in the SecureAuth IdP Web Admin
3. Configure and install the SecureAuth RADIUS
4. Provision end-user device(s) and / or browser to generate OATH tokens
F5 Configuration Steps
AAA Servers
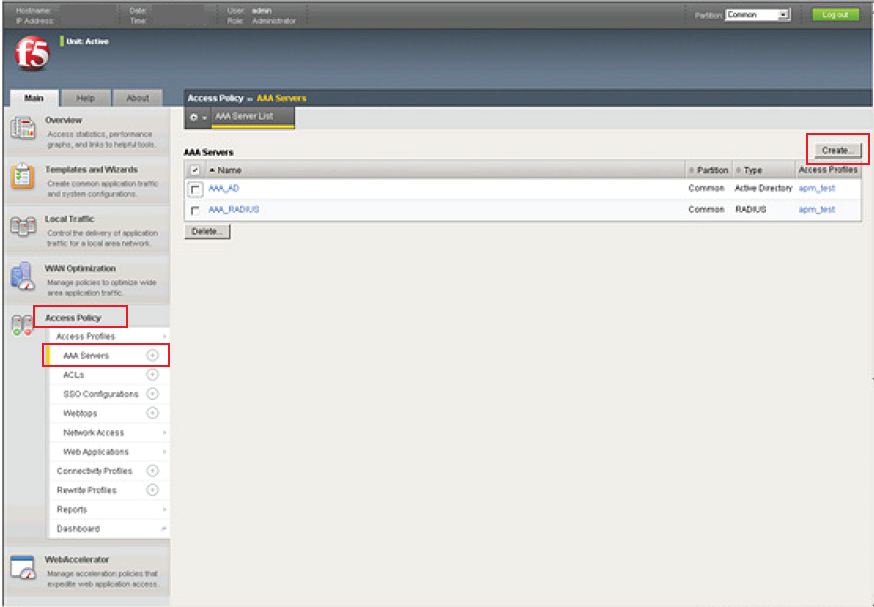 |
1. Log into the F5 VPN as an administrator
2. Select AAA Servers under Access Policy, and click Create to create a new AAA RADIUS Server
New AAA Server
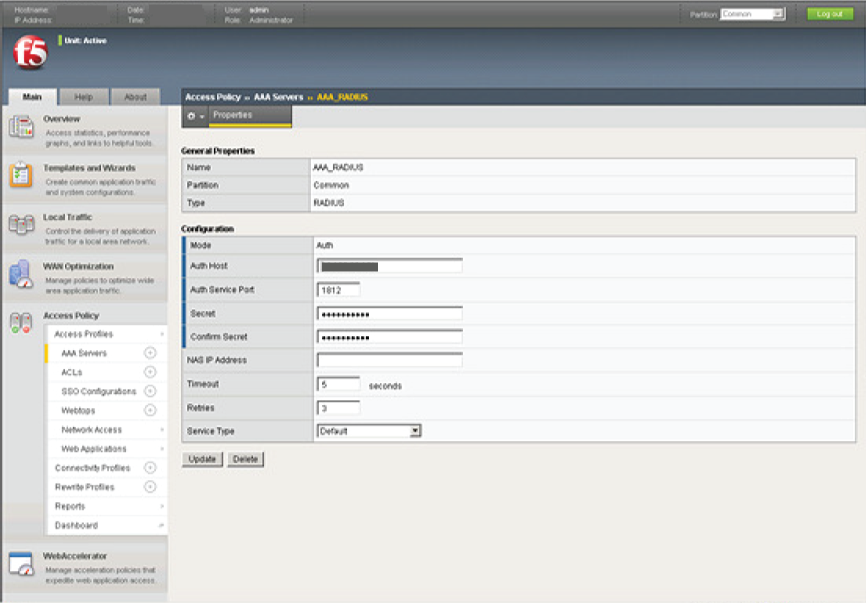 |
3. In the General Properties section, provide a Name for the AAA (Authentication, Authorization, and Accounting) Server, e.g. AAA_RADIUS
4. Select RADIUS from the Type options
5. Set the Mode to Auth
6. Set the Auth Host to the IP Address of the SecureAuth IdP Server
7. Set the Auth Service Port to 1812
8. Set the Secret to the RADIUS-SecureAuth IdP Shared Secret, and Confirm Secret
9. Set the Timeout to 60 seconds
10. Set the Retries to the number of attempts to reconnect that are permitted
11. Click Update
Access Profiles
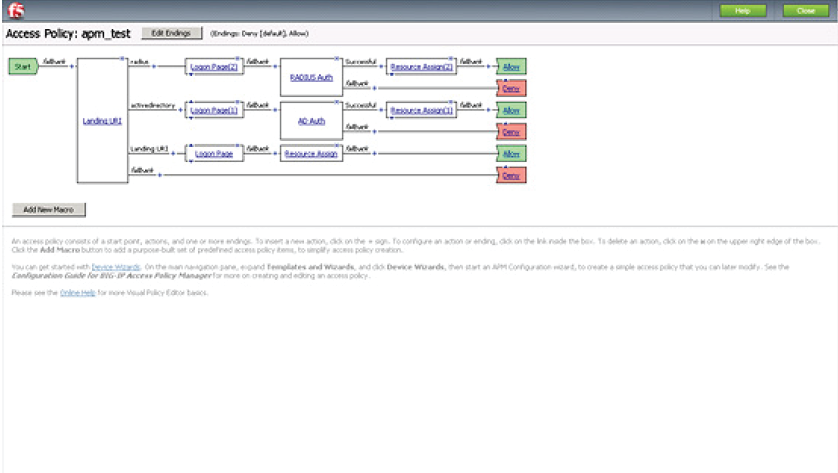 |
12. In the F5 admin console, select Access Profiles under Access Policies
13. Select the New RADIUS Server (AAA_RADIUS) from the list
14. Click Edit Access Policy for Profile to initiate the visual policy editor
15. Click the " " to add a new access policy action item
16. Under Authentication, select RADIUS, and click Add Item
17. Under Properties, select the New RADIUS Server (AAA_RADIUS) from the AAA Server List, and click Save
18. Click Activate Access Policy to save the configuration
Test F5 Integration
1. Go to the VPN URL and enter the Username and Password (or OATH OTP)
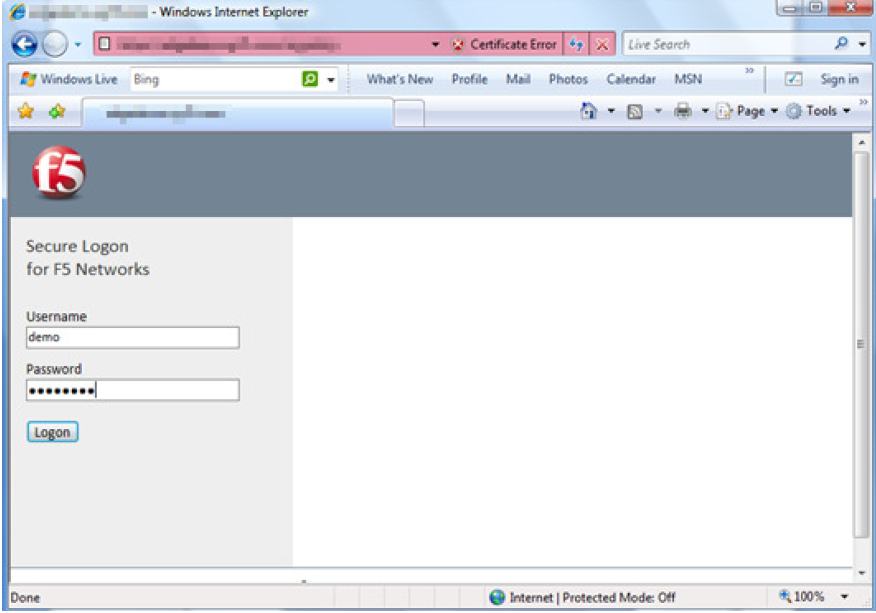 |
2. User can access VPN once authenticated
 |
Note
SecureAuth RADIUS can be configured to require Username, Password, and OATH OTP