Oracle Database Configuration Guide
Introduction
Use this guide along with the Data Tab Configuration guide to configure an Oracle Database-integrated SecureAuth IdP realm.
Prerequisites
1. Have an on-premises Oracle Database with which SecureAuth IdP can integrate
SecureAuth IdP supports versions 11.2 and 12.1, and supports with limitations versions 11.1 and 10.2
2. Create or enable an admin account that has read access (and optional write access) to the tables and stored procedures
Write access is required to update user profile information, such as creating new users and changing passwords
3. Contact SecureAuth Support to download the Oracle Data Access Components and install it onto the SecureAuth IdP appliance
More download information found here
Oracle Database Configuration Steps
Notice
The tables and stored procedures below are examples, and can be used or modified based on the existing environment
Scripts without Company / Domain
If passing only the userID and password through SecureAuth IdP, then use the tables and stored procedures below
See the next section for the tables and stored procedures that pass the company or domain name in addition to the userID and password
Scripts with Company / Domain
If passing more than just the userID and password through SecureAuth IdP (such as userID, password, and company), then use the tables and stored procedures below
See the previous section for the tables and stored procedures that do not pass the company or domain name
SecureAuth IdP Configuration Steps
Data
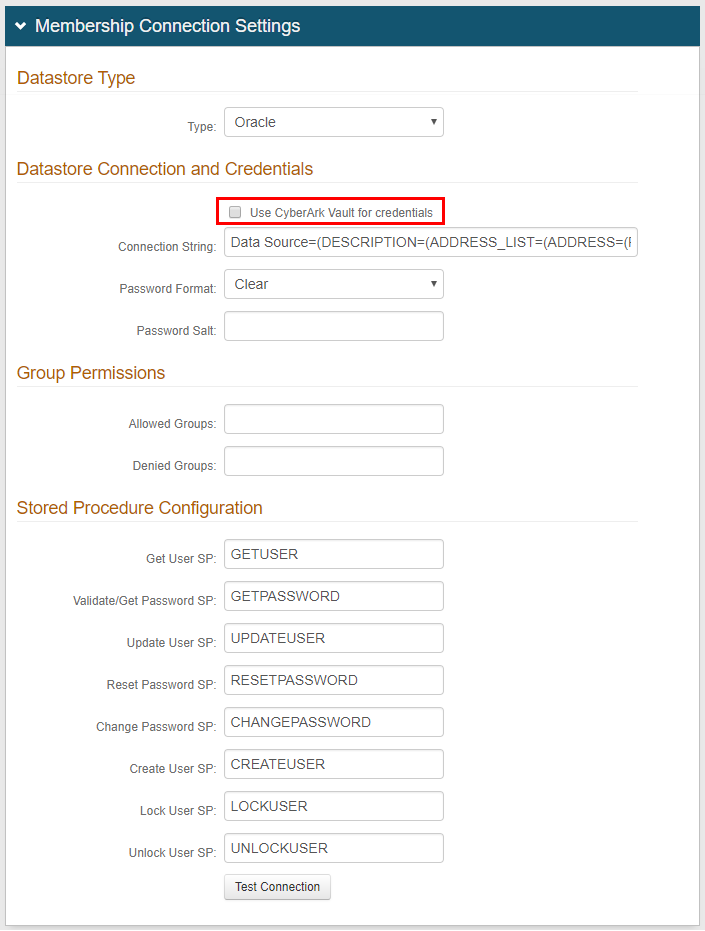 |
Datastore Type
1. Select Oracle from the Type dropdown
Datastore Connection and Credentials
Note
If using CyberArk Vault for credentials, enable Use CyberArk Vault for credentials and follow the steps in CyberArk Password Vault Server and AIM Integration with SecureAuth IdP
2. Provide or modify the given Connection String in the following format:
Data Source=(DESCRIPTION=(ADDRESS_LIST=(ADDRESS=(PROTOCOL=TCP)(HOST=localhost)(PORT=1522)))(CONNECT_DATA=(SERVER=DEDICATED)(SERVICE_NAME=[DBName]))); User Id=[username];Password=[password]
Replace localhost (after HOST) with the Server Name or IP Address of the Oracle Database if it is not on the same server
Replace 1522 with the appropriate PORT number if using a different port
Replace [DBName] with the name of the database
Replace [username] with the username of the service account
Replace [password] with the password of the service account
3. Select the Password Format from the dropdown
This setting dictates which Stored Procedure to use in the Oracle Database (Validate Password or Get Password)
4. Provide a unique string of text to append to passwords before they are hashed in the Password Salt field (not necessary for Clear Password Format)
Group Permissions
5. Provide a list of Allowed Groups and / or Denied Groups to restrict access to the realm
Stored Procedure Configuration
6. Leave the Stored Procedure names as the default, or modify them to reflect the names in the Oracle Database Stored Procedures
If using the provided names in the Stored Procedures above, then no changes are required
7. Click Test Connection to ensure that the connection is successful
Profile Provider Settings
Datastore Type
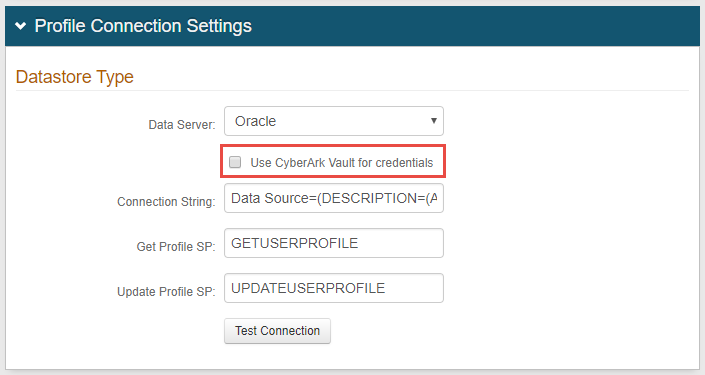 |
If using Oracle Database as the Profile Provider as well as the main directory integration, then follow these steps:
8. Select Oracle from the Data Server dropdown
Note
If using CyberArk Vault for credentials, enable Use CyberArk Vault for credentials and follow the steps in CyberArk Password Vault Server and AIM Integration with SecureAuth IdP
9. Leave the Get Profile SP and Update Profile SP fields as the default, or modify them to reflect the names in the Oracle Database Stored Procedures
If using the provided names in the Stored Procedures above, then no changes are required
Warning
Click Save once the configurations have been completed and before leaving the Data page to avoid losing changes
Notice
Refer to Data Tab Configuration to complete the configuration steps