Forgot Password page configuration
The Identity Management (IdM) tool in SecureAuth® Identity Platform (formerly SecureAuth IdP) contains the Forgot Password page for end users. As an administrator, you can configure the Forgot Password page to allow users and administrators to reset and update passwords, and unlock accounts.
There are three password reset mode methods:
Enforce mode – Useful for most Active Directory and LDAP use cases. This mode enforces password history requirements like not using a previous password or does not allow frequent password updates.
Administrative mode – Useful for SQL-type data stores, in a Help Center environment, and if your data store supports password history checks.
Administrative mode with history check – Useful for SQL-type data stores, in a Help Center environment, and if your data store does not support password history checks.
Prerequisites
Data store with service account set with write privileges to modify (needed to change user passwords)
If using Active Directory, open the following Outbound Ports for password modification:
139 – DFSN, NetBIOS Session Service, NetLogon
445 – SMB / CIFS, DFSN, LSARPC, NbtSS, NetLogonR, SamR, SrvSvc
464 – Kerberos Change / Set Password
A realm for the Forgot Password page with the following tabs configured before setting up the Post Authentication tab:
Overview
Data
Workflow
Multi-Factor Methods
(Optional) To use the Password Reset Mode: Administrative Reset with History Check, open this port for password modification: 636 - SSL Outbound Port
(Optional) Configure Google G Suite to synchronize directory passwords
Identity Platform configuration
Go to the Post Authentication tab.
In the Post Authentication section, set the following.
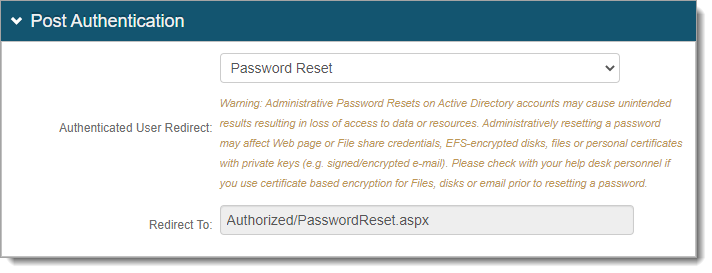
Authenticated User Redirect
Set to Password Reset.
Redirect To
This field is autopopulated with the post authentication .aspx page. This is appended to the domain name and realm number in the web address bar. For example, Authorized/PasswordReset.aspx.
Save your changes.
In the Password Reset section, click the Configure password reset page link.

In the Password Reset Functions section, set the Password Reset Mode to one of the following options:
Enforce Password Change Requirements (Enforce mode) – To enforce password history rules, it must use the current password. If the current password is not given, a random password is set, then used to change the current password.
Note: Use this option for Active Directory and LDAP directory types and must have password history checks.
Administrative Password Reset (Admin mode) – This does not enforce password history rules. The current password is not required for this rule.
Note: Use this option for SQL directory types and do not need or support password history checks.
Administrative Reset with History Check (Administrative mode with history check) – Enforces password history rules and does not require current password. This mode is not guaranteed to work with non-AD LDAP data stores. For Active Directory, you need to open SSL Outbound Port 636.
Note: This is not supported for eDirectory.
Continue with the rest of the configuration settings. The settings are the same for all password reset modes, unless otherwise specified.
Username Textbox
Set to Disabled - change own password – Do not allow username search box. User can change their own password.
Require Current Password
Set to False.
Notice
This field displays only when Password Reset Mode is set to Enforce Password Change Requirements.
Must Change Password at Next Logon
For Enforce mode, set to True to bypass any minimum password age restrictions.
For Admin modes and Admin mode with history check, set to False.
Unlock User Account
Set to Automatically.
Allow Password Change
Set to True.
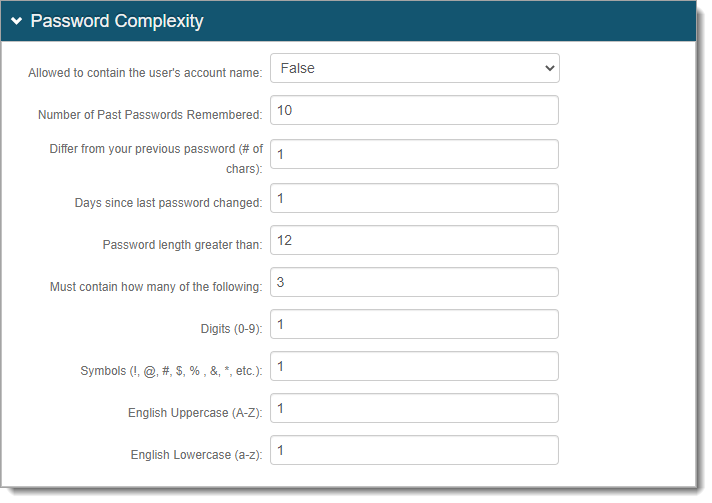
Validate Password Complexity
Set whether the Identity Platform adheres to the password complexity requirements in the data store. The rules set in the Password Complexity section should mirror what is set in the data store.
True – the Identity Platform checks with the data store to make sure the password is valid before updating the password value.
False – User can give any password value regardless of whether it meets the password rules in the data store.
Note
If the password rules in the Identity Platform are more strict than the rules in the data store, then it follows the Identity Platform password rules to allow a successful password change.
If the password rules in the Identity Platform are less strict than the data store, then it follows the data store password rules to allow a successful password change.
If the password change does not meet the data store rules, the realm errors out and does not allow a password change.
Show Password Complexity Rules
Show the password rules to the user (True / False).
This field works with the Validate Password Complexity option set to True. Configure the password rules in the Password Complexity section.
Send Email
Set whether to send an email notification of a changed password to the user.
Select the Identity Platform email profile property mapped to the email data store field like Email 1 through Email 4, or use Do not send.
Show Exception on Page
Set True to display the reason(s) why a password change is not accepted.
The error message comes from the data store, based on its password complexity rules.
Reset Complete URL (Return to)
Optionally set whether to redirect the user to a specific URL after changing their password.

In the Password Complexity section, configure the password rules that mirror the password complexity rules set in the data store.
These password rules will display on the page as guidance to the user as long as the Show Password Complexity Rules is set to True.
Notice
If the Identity Platform does not have password complexity rules turned on, the password rules from the data store takes place.
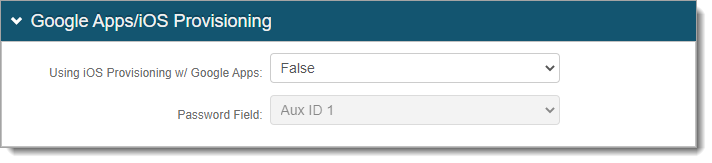
In the Google Apps / iOS Provisioning section, set whether to enable iOS provisioning with G Suite and allow synchronization of password changes.
For more information, see iOS G Suite Provision Configuration Guide.
Save your changes.
Optional configurations for token or cookie settings and SSO
In the Forms Auth/SSO Token section, you can optionally configure the token or cookie settings, and single-sign on (SSO) for this realm.
 |
To configure token or cookie settings, see Configure token or cookie settings.
To configure this realm for SSO, see SecureAuth IdP single sign-on configuration topic.
To configure this realm for Windows Desktop SSO, see Windows desktop SSO configuration topic.